
Cobalt Strike Leak, Sales of Unauthorized Access and Credit Card Data
The SOCRadar Dark Web Team conducts continuous monitoring of the dark web, uncovering the latest threats that require your attention.
In this week’s update, there were reports of unauthorized access sales related to a Mexican phone credit firm, an African bank, and an Indian manufacturing company. Furthermore, a threat actor has been promoting the sale of credit card information from American companies that either do not enforce 3D security or lack verification. Simultaneously, another threat actor has leaked a cracked version of Cobalt Strike for malicious intentions.
Find out if your data has been exposed.
Unauthorized Access Sale is Detected for a Mexican Phone Credit Company
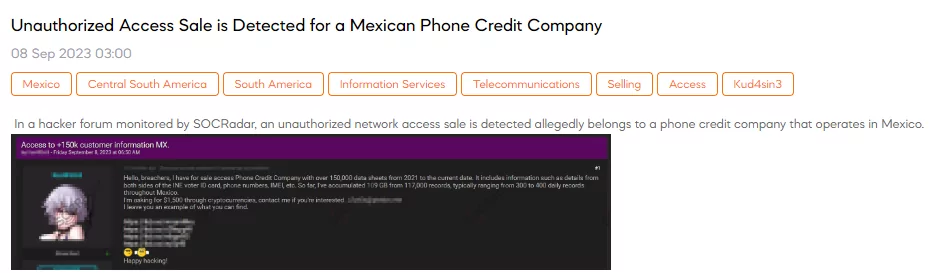
SOCRadar Dark Web Team has identified a post that a threat actor claims to be selling unauthorized access to a Mexican phone credit company’s network. The actor alleges to have over 150,000 data sheets dating from 2021 to the present, containing sensitive information like details from both sides of the National Electoral Institute (INE) voter ID card, phone numbers, IMEI numbers, and more. They mention having already accumulated 109 GB of data from 117,000 records, with a daily acquisition rate of 300 to 400 records from all over Mexico.
The threat actor is asking for $1,500 in cryptocurrencies for this illicit access and provides an example of the type of information that can be found within the data.
Unauthorized Access Sale is Detected for an African Bank
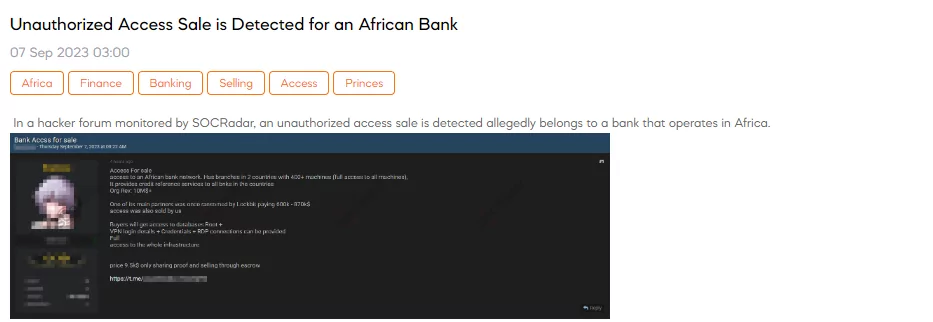
SOCRadar Dark Web researchers have detected a post in a hacker forum that a threat actor claims to have unauthorized access for sale to an African bank’s network. The bank operates in two countries, with over 400 machines, granting full access to all of them. This bank is involved in providing credit reference services to other banks in these countries, with an organizational revenue of $10 million or more.
The threat actor also mentions that one of the bank’s main partners was previously targeted by the LockBit ransomware and paid a significant ransom, and they claim to have been involved in selling access to that partner as well.
Buyers of this unauthorized access are promised access to root databases, VPN login details, credentials, and RDP (Remote Desktop Protocol) connections. The price for this access is advertised at $9,500, and the threat actor offers to use escrow services for the transaction.
Unauthorized SSH Access Sale is Detected for an Indian Manufacturing Company
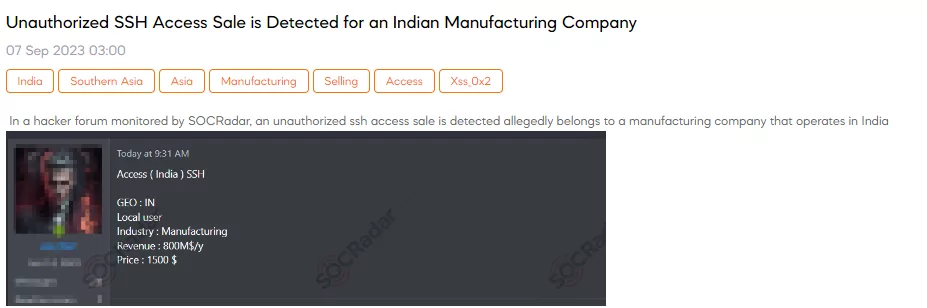
A SOCRadar Dark Web Team researcher has discovered a post on a hacker forum that a threat actor claims to be selling unauthorized SSH access allegedly belonging to a manufacturing company operating in India. This unauthorized access includes SSH access with a geographic location specified as India, local user credentials, and information regarding the industry, indicating it’s a manufacturing company with an annual revenue of $800 million. The threat actor is offering this illegal access for $1,500.
Cobalt Strike 4.8 is Leaked
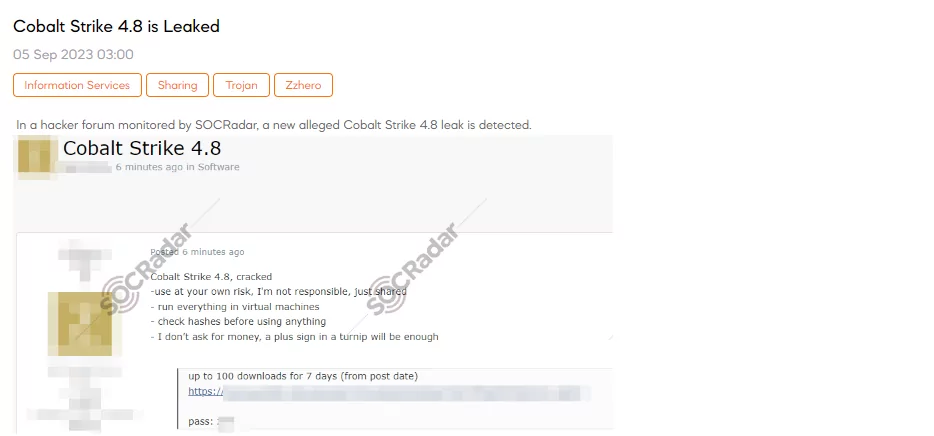
SOCRadar Dark Web Team has detected a post on a hacker forum claiming to offer a cracked version of Cobalt Strike 4.8. The post includes several disclaimers, emphasizing the use of the software at one’s own risk and recommending running it in virtual machines. It also advises users to check the file hashes before using anything. The offer appears to be limited to up to 100 downloads for seven days from the date of the post.
Credit Cards of American Companies are on Sale
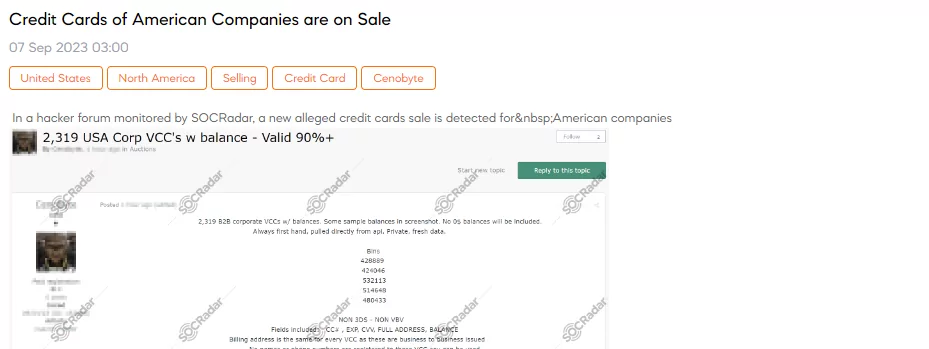
SOCRadar Dark Web Team has detected a post in a hacker forum, where a threat actor is claiming to sell 2,319 B2B corporate virtual credit cards (VCCs) with balances, specifically targeting American companies. The threat actor boasts that these VCCs are sourced directly from APIs and are private, fresh data.
According to the threat actor’s description, these VCCs fall into the category of “NON 3DS – NON VBV,” which likely means they do not require 3D Secure (3DS) or Verified by Visa (VBV) authentication. The fields included in the sale are the credit card number (CC), expiration date (EXP), card verification value (CVV), full address, and the balance on each card.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































