
Critical OS Command Injection Flaw in Progress Flowmon: CVE-2024-2389
[Update] April 25, 2024: “PoC Exploit Code is Available for CVE-2024-2389 in Flowman”
Progress disclosed a highly critical vulnerability, CVE-2024-2389, that affects the Flowmon product. Exploiting this vulnerability could let attackers obtain sensitive data and network configurations, enabling additional disruptive attacks across the broader network.
Flowmon, developed by Progress, is a widely used network monitoring and security solution that gives IT teams visibility into network performance and security. Plus, users can utilize the software for effective reporting and alerting of network threats.
Flowmon’s dashboard
What is CVE-2024-2389?
The security vulnerability, identified as CVE-2024-2389, poses a critical threat with a maximum CVSS score of 10. It stems from an OS command injection issue.
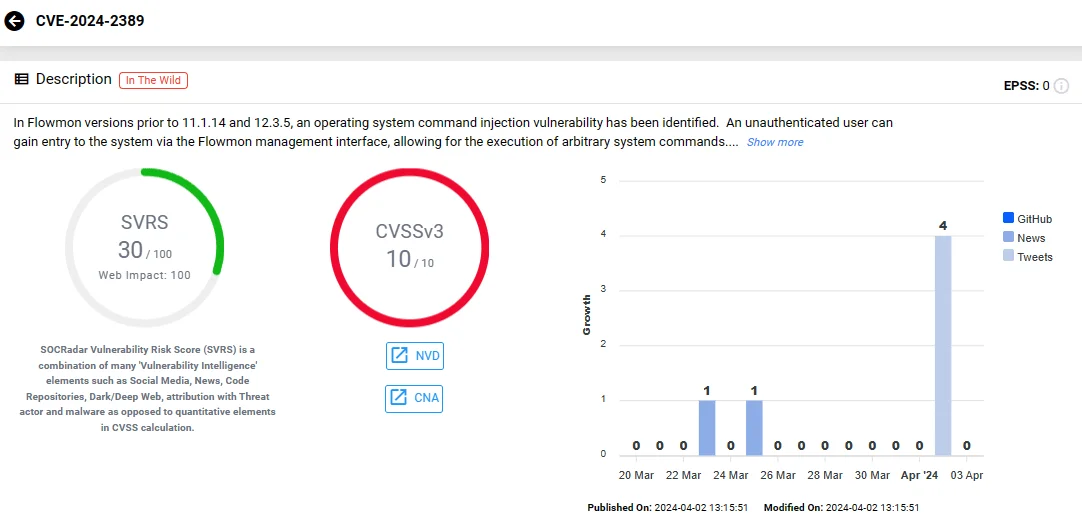
Vulnerability card of CVE-2024-2389 (SOCRadar Vulnerability Intelligence)
The vulnerability allows unauthorized access to the system via the Flowmon management interface, allowing the execution of arbitrary system commands. Exploiting this vulnerability could give attackers unrestricted access to critical network infrastructure.
Which Progress Flowmon versions are affected by CVE-2024-2389?
Progress Flowmon versions 11.x and 12.x across all platforms are susceptible to CVE-2024-2389. However, earlier versions, including 10.x and lower, remain unaffected by this vulnerability.
Despite being trusted network management tools, products like Progress Flowmon are not immune to security threats. To mitigate risks associated with vulnerabilities like CVE-2024-2389, it is vital to monitor security advisories regularly and promptly apply patches.
SOCRadar’s solutions can enhance your organization’s vulnerability management strategies. Utilizing SOCRadar’s Attack Surface Management, you can stay updated on the latest security vulnerabilities and ensure the protection of products and software.
With continuous monitoring and timely alerts, SOCRadar helps maintain the security of digital assets within an organization’s ecosystem.
SOCRadar’s Attack Surface Management
Has CVE-2024-2389 been exploited by threat actors?
Although there are not any reports of active exploitation as of yet, the CVE-2024-2389 vulnerability’s critical severity underscores the serious risk it presents.
Furthermore, a Shodan search provides up to 55 results, highlighting the scope of instances that may be vulnerable.
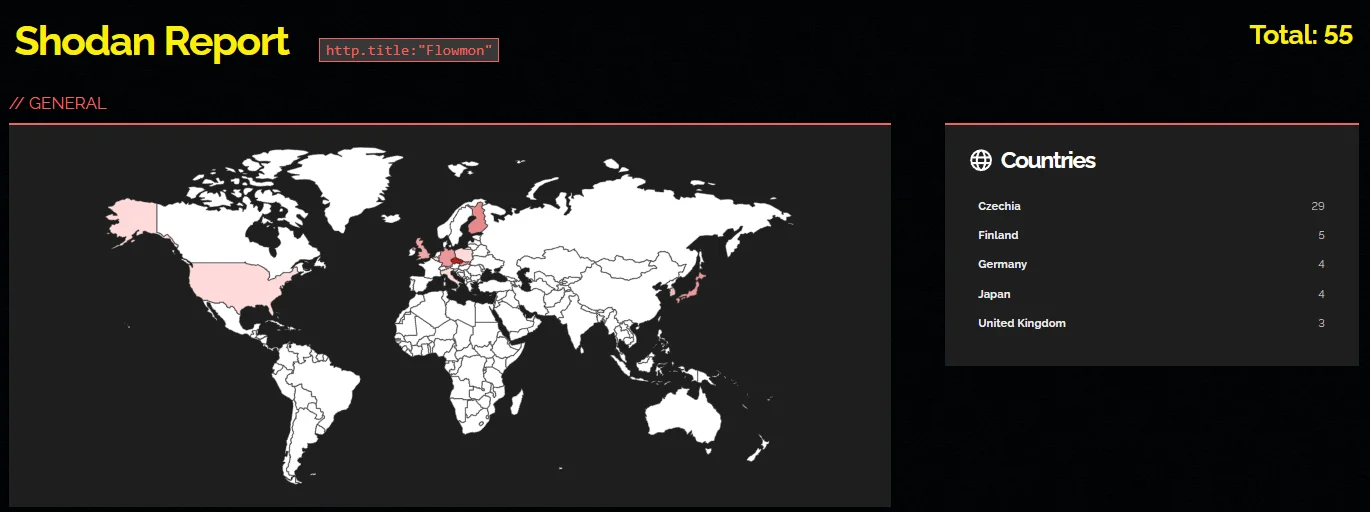
Shodan results for Flowmon instances
Apply the updates for Progress Flowmon
Flowmon versions 11.1.14 and 12.3.5 have been released with a fix for the vulnerability.
Users of versions 11.x or 12.x are advised to upgrade to version 11.1.14 or 12.3.5, respectively, to prevent the potential exploitation of CVE-2024-2389.
Download links for the patches can be found on Progress’ security advisory.
PoC Exploit Code is Available for CVE-2024-2389 in Flowman
In a concerning development, a Proof-of-Concept (PoC) exploit for CVE-2024-2389 is now publicly available. researchers documented their discovery and exploitation of the vulnerability in a recent report. They’ve released a Proof-of-Concept, emphasizing the importance of organizations addressing the vulnerability quickly.
To exploit CVE-2024-2389, the researchers created a specific API request. This would enable an attacker to gain remote, unauthenticated access to the Flowmon web interface and run arbitrary system commands.
Rhino Security Labs’ report shows how an attacker could manipulate the ‘pluginPath’ or ‘file parameters’ in Flowmon to inject malicious commands. Even though the executed command’s output remains hidden, an attacker could write a webshell to escalate privileges, underscoring the urgent need for patch implementation.
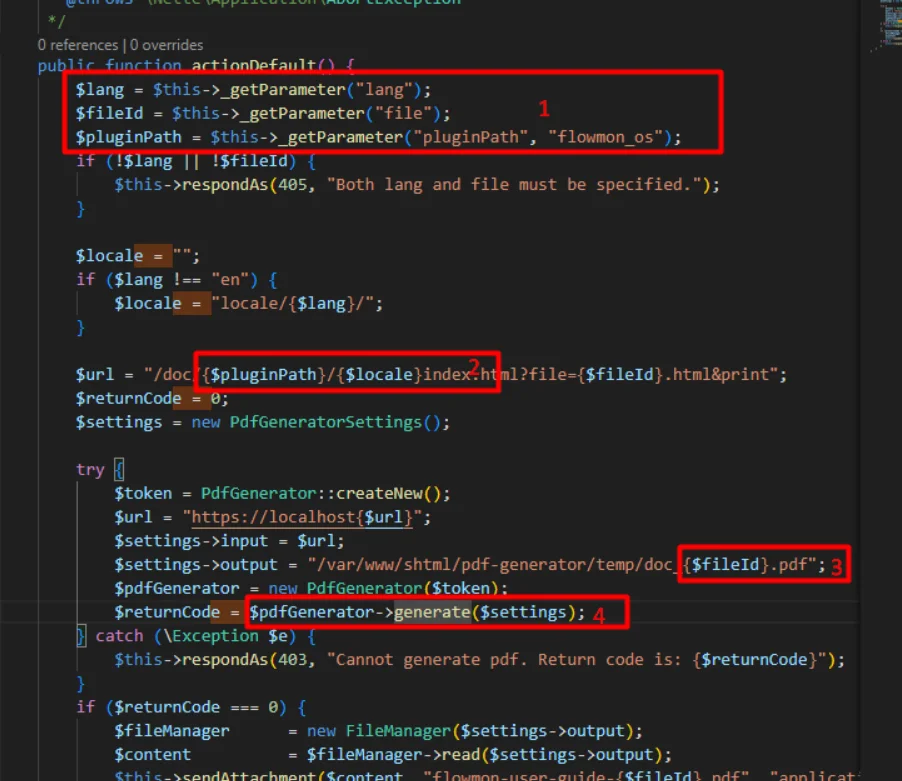
Rhino Security Labs’ report showcasing a part of the exploit code
Recent important vulnerabilities fixed by Progress and other vendors
Progress addressed two other CVSS 10 vulnerabilities in February: CVE-2024-1212 (OS Command Injection in LoadMaster) and CVE-2024-1403 (Authentication Bypass in OpenEdge Authentication Gateway).
Furthermore, another noteworthy vulnerability, CVE-2024-29834, has been discovered in Apache Pulsar, an open-source messaging and streaming platform. While not as critical as the other vulnerabilities mentioned in this blog post, CVE-2024-29834 still warrants attention with a CVSS score of 6.4, indicating medium severity.
Exploitation of CVE-2024-29834 could allow unauthorized users to manipulate sensitive data streams and system access rules, exposing organizations to security risks.
Follow CVE trends with SOCRadar’s Vulnerability Intelligence
Check SOCRadar’s Vulnerability Intelligence to effectively manage vulnerabilities and prioritize patching. With the Vulnerability Intelligence feature, you can stay updated on the latest information regarding known vulnerabilities, including exploits, repositories, and emerging hacker trends. Organizations can use such insights to proactively protect against potential threats and improve vulnerability management.
CVE trends on SOCRadar’s Vulnerability Intelligence



































