
Compliance Through Vigilance; SOCRadar XTI for Compliant Organizations
We are all aware that reactive measures are insufficient in this age of cyber threats; businesses must take proactive steps to effectively protect digital assets from imminent cyber threats. This entails adhering to cybersecurity regulations and frameworks, not only to improve cybersecurity but also to meet compliance obligations.
Simply put, organizations can manage vulnerabilities and implement necessary patches more efficiently by following specific standards and cybersecurity regulations.
Regardless of how challenging managing regulatory compliance can be, failure to do so not only exposes organizations to severe legal penalties, but also results in significant financial losses and irreparable reputational damage. In such a high-stakes environment, having the right tools and solutions in grasp is critical.
This is where SOCRadar steps in as a cybersecurity solution designed to assist organizations in meeting regulatory compliance requirements. By offering features such as vulnerability management, threat intelligence, and data breach monitoring, SOCRadar allows organizations to stay ahead of potential threats and maintain compliance with various regulations.
Through this article, we will examine some of the key regulations and explore how SOCRadar’s solutions can assist organizations in achieving and maintaining compliance with them in today’s dynamic cybersecurity environment.
What Are Regulatory Requirements? Why Are They So Important?
Organizations must comply with numerous cybersecurity regulations, each outlining specific requirements. Understanding these requirements is vital to ensure compliance and avoid severe consequences for non-compliance.
These regulations dictate that organizations must adhere to precise measures to protect their digital assets and sensitive information. Regulatory bodies responsible for overseeing cybersecurity compliance possess the authority to enforce these regulations through various means, including audits and inspections.
Failure to comply with regulations results in fines, sanctions, or legal actions imposed by regulatory bodies. Moreover, regulations are often tailored to specific industries, taking into account the distinct risks and challenges faced by each sector. For instance, financial institutions are governed by the Payment Card Industry Data Security Standard (PCI DSS), while healthcare organizations must follow the Health Insurance Portability and Accountability Act (HIPAA).
Despite the seeming complexity, these regulations offer valuable guidelines and standards that can significantly benefit organizations. Adhering to regulations not only helps organizations avoid legal consequences and the costs associated with cyber breaches but also enhances their overall security posture.
Fundamentally, regulations serve as official guidelines for ensuring organizational security, with legal repercussions for non-compliance. And, for organizations, it is absolutely preferable for regulatory bodies to enforce these rules rather than dealing with the aftermath of cyber threats.
In the following sections, we will use examples of well-known regulations to explore how SOCRadar’s solutions can help organizations meet regulatory requirements and maintain compliance in today’s dynamic cybersecurity landscape.
Overview of Key Cybersecurity Regulations
Cybersecurity regulations have an important influence on the security practices of organizations across industries, ensuring the protection of sensitive data and mitigating cyber threats.
Here, we provide a brief overview of three key regulations: GDPR, HIPAA, and PCI DSS, along with their industry-specific requirements.
General Data Protection Regulation (GDPR)
The General Data Protection Regulation (GDPR) requires businesses to employ both technical and organizational safeguards to protect personal data. This includes regular vulnerability assessments and the prompt application of necessary patches to protect personal data from breaches.

GDPR is a global regulation that applies to all organizations that handle the personal data of individuals who reside in Europe.
GDPR outlines several fundamental principles, including the lawful processing of personal data, minimizing data collection, and respecting data subject rights. It mandates that organizations notify the relevant supervisory authority and, in certain instances, the affected individuals, in the event of a data breach.
SOCRadar assists organizations in complying with GDPR by:
- Monitoring for data breaches for promptly notifying relevant authorities.
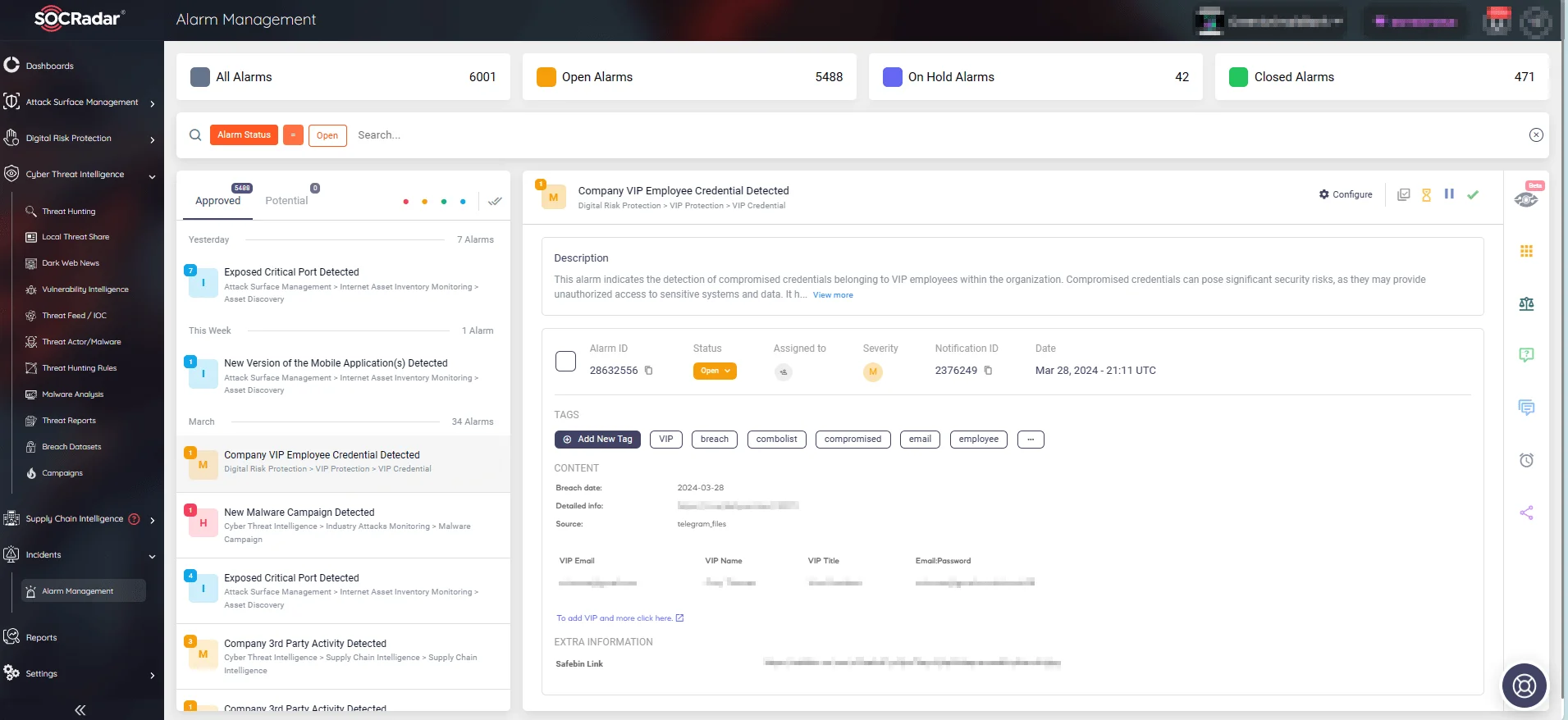
Receive real-time alerts on security incidents, including data breaches (SOCRadar’s Alarm Management)
- Providing continuous vulnerability management to ensure that organizations stay on top of potential security risks and comply with GDPR’s requirement for regular vulnerability assessments and patching.
- Offering robust threat intelligence capabilities to enhance data security and protection measures.
Health Insurance Portability and Accountability Act (HIPAA)
Health Insurance Portability and Accountability Act (HIPAA) requires that patient health information be protected through administrative, physical, and technical means.
Organizations must conduct regular security assessments and address any vulnerabilities with appropriate security measures in order to comply with the HIPAA regulations, and limit the exposure of Protected Health Information (PHI) data that they handle.
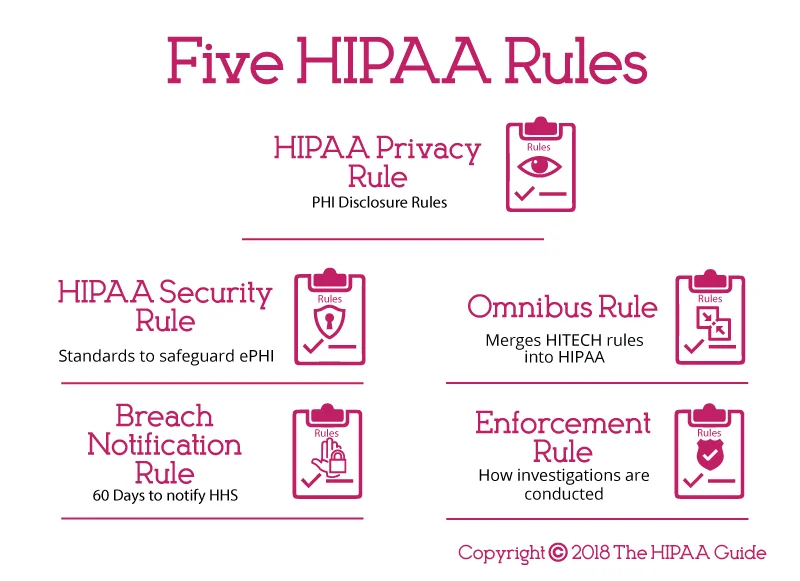
Five HIPAA Rules (The HIPAA Guide)
This regulation encompasses key rules such as the Privacy Rule, governing PHI use and disclosure, and the Security Rule, which dictates security measures for electronic PHI (ePHI).
HIPAA also requires healthcare organizations to report breaches to HHS (Department of Health and Human Services), individuals, and occasionally the media.
SOCRadar aids healthcare organizations in complying with HIPAA by:
- Providing comprehensive vulnerability management solutions tailored to the specific needs of healthcare environments.
- Offering continuous monitoring and threat detection capabilities to safeguard electronic protected health information (ePHI) and ensure compliance with HIPAA’s security requirements.
- Assisting in breach detection and response, helping organizations meet HIPAA’s breach notification obligations.
Payment Card Industry Data Security Standard (PCI DSS)
The Payment Card Industry Data Security Standard (PCI DSS) requires entities that handle credit card information to perform periodic threat assessments and set up effective safety measures.

PCI DSS mandates data encryption, regular audits, and network security measures to protect cardholder data from unauthorized access and breaches.
SOCRadar supports organizations in adhering to PCI DSS requirements by:
- Offering advanced vulnerability management capabilities to help organizations conduct regular vulnerability assessments and maintain a robust patch management program.
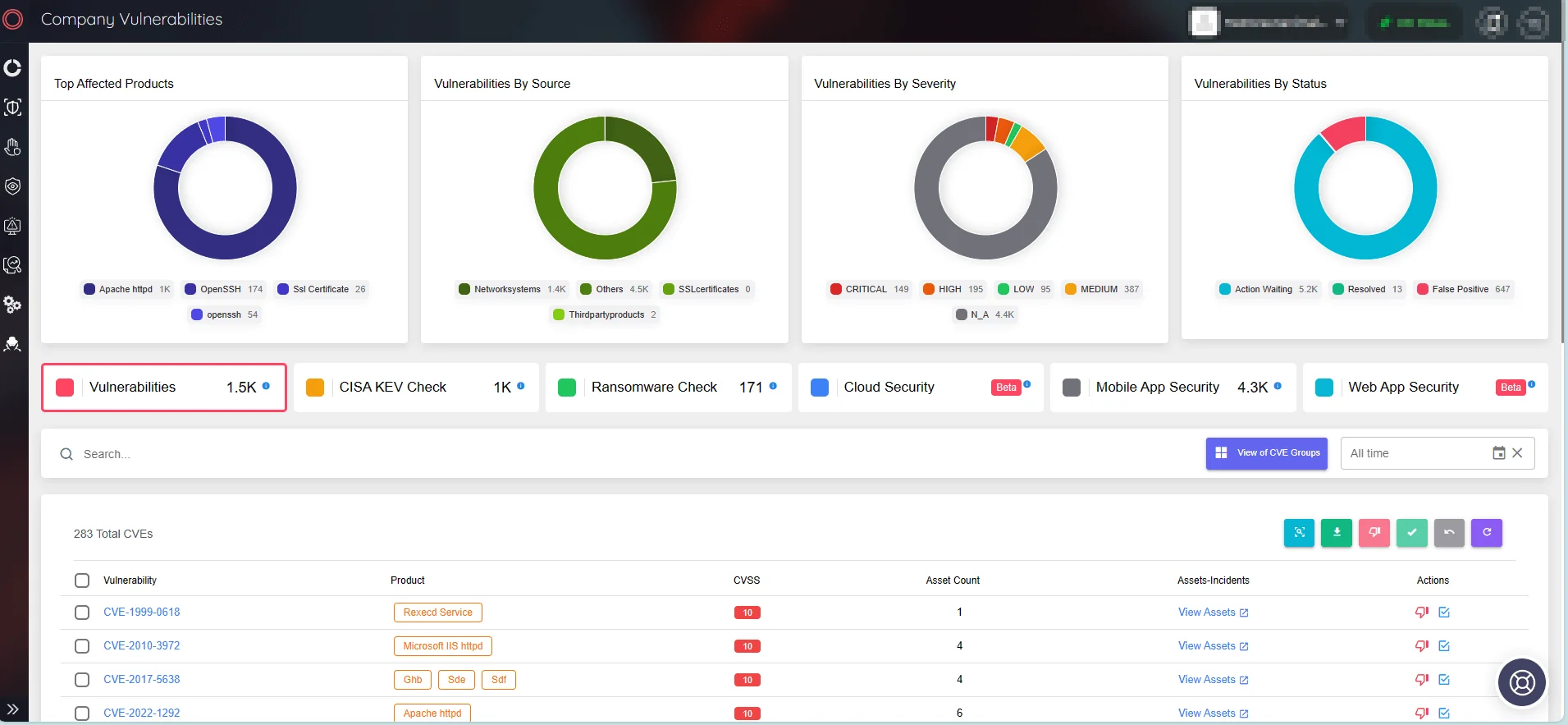
Monitor company vulnerabilities and take quick actions to initiate patches through SOCRadar’s Attack Surface Management module.
- Providing visibility into network security and facilitating compliance with PCI DSS’s guidelines for securing network infrastructure.
- Enhancing data protection measures through continuous monitoring and threat intelligence, thereby helping organizations safeguard cardholder data and maintain compliance with PCI DSS.
In summary, SOCRadar serves as a valuable ally for organizations striving to meet regulatory requirements and maintain robust cybersecurity practices across various industries. By offering comprehensive solutions for vulnerability management, threat intelligence, and data breach monitoring, SOCRadar enables organizations to navigate the complex landscape of cybersecurity regulations effectively while enhancing their overall security posture.
Cybersecurity Frameworks & Reminding SEC’s New Rules
Cybersecurity regulations are legally enforceable rules established by government authorities or regulatory bodies. These regulations, such as HIPAA, PCI DSS, and GDPR, impose specific cybersecurity standards and practices tailored to each industry. Non-compliance with these regulations can lead to penalties, fines, or legal action.
Conversely, cybersecurity frameworks are voluntary guidelines and best practices developed by cybersecurity experts to aid organizations in bolstering their security defenses, and even help in pursuit of achieving compliance with regulations. Examples include the NIST Cybersecurity Framework, CIS Controls, and ISO/IEC 27001 standard.
- NIST Cybersecurity Framework (CSF): Developed by the National Institute of Standards and Technology (NIST), the CSF is a framework designed to be applicable to organizations of any size and level of cybersecurity sophistication.
It expands its scope beyond critical infrastructure to include all sectors, emphasizing governance and recognizing cybersecurity as a significant enterprise risk. The updated framework, in version 2.0, introduces a new function, ‘Govern,’ to its core, which now comprises six key functions: Identify, Protect, Detect, Respond, Recover, and Govern, providing a comprehensive approach to managing cybersecurity risk.
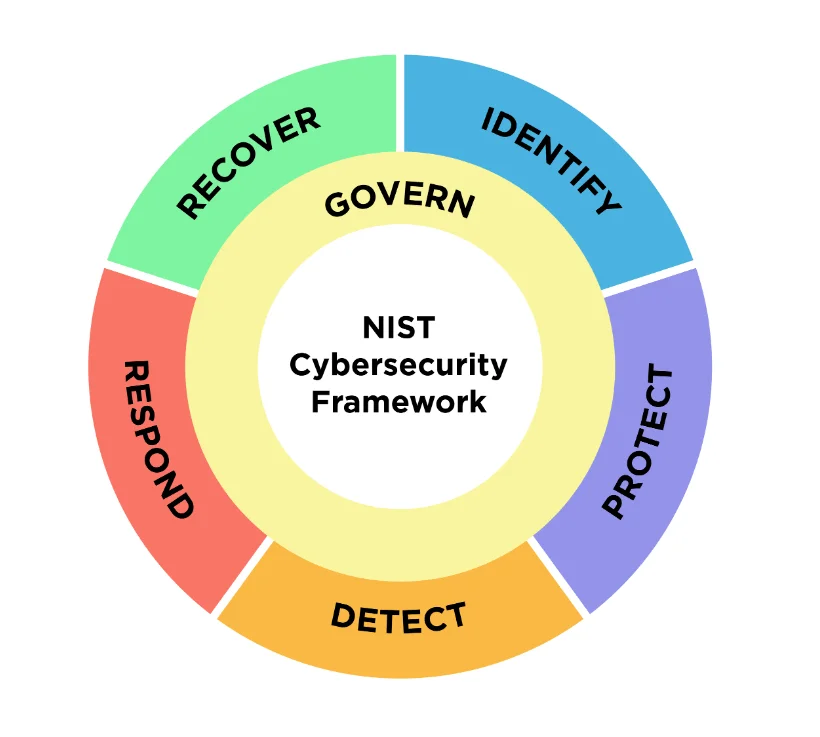
NIST CSF 2.0
- CIS Controls: The Center for Internet Security (CIS) Controls are a set of 18 prioritized, prescriptive, and simplified cybersecurity best practices designed to provide organizations with a clear roadmap for enhancing their security posture.
These controls are structured to defend against prevalent cyber threats and are adaptable to a variety of industries, providing a foundation for compliance with regulations like PCI DSS, HIPAA, and GDPR.
The latest version, CIS Controls v8, addresses the security challenges of modern, hybrid cloud environments and emphasizes supply chain security while offering resources and guidance to facilitate implementation and migration from previous versions.
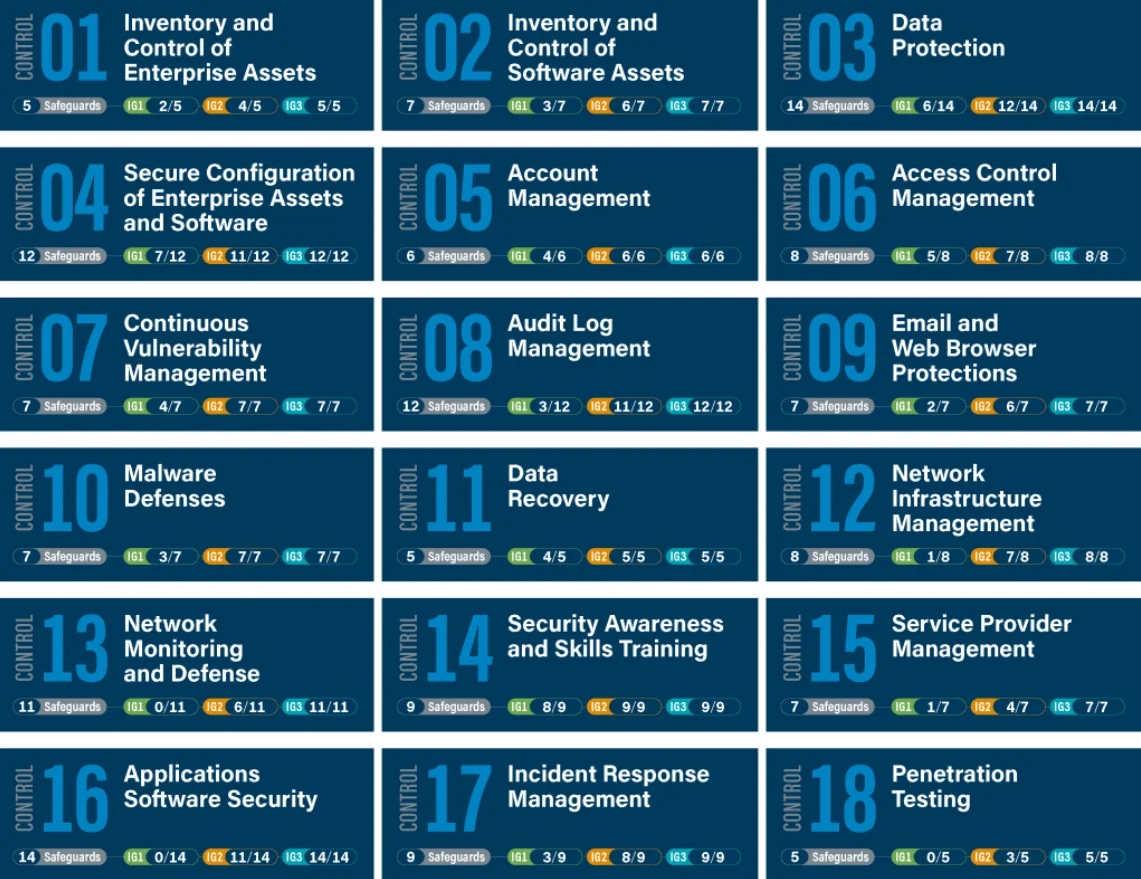
The 18 best practices in CIS Controls (Incident Response Solutions)
- ISO/IEC 27001 Standard: ISO/IEC 27001 is an international standard for Information Security Management Systems (ISMS). It outlines requirements for establishing, implementing, maintaining, and continually improving an ISMS.
It is designed to be applicable to any organization, regardless of its size, type, or nature, and emphasizes the protection of the confidentiality, integrity, and availability of information assets.
ISO/IEC 27001:2022, the latest version, includes a set of requirements and controls that organizations can be certified against, demonstrating their commitment to information security.
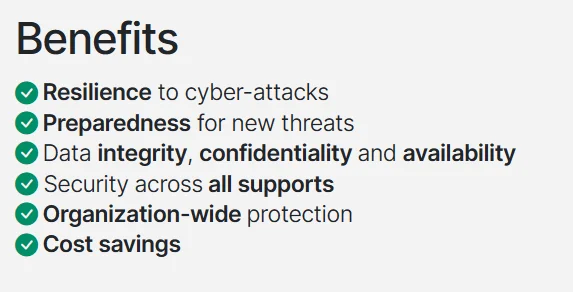
Benefits of ISO/IEC 27001 (ISO)
Many organizations voluntarily adopt such frameworks to demonstrate their commitment to cybersecurity and enhance their security measures.
Moreover, the U.S. Securities and Exchange Commission (SEC) introduced new rules concerning the disclosure of cybersecurity incidents in the past year. These regulations enforce key requirements that we have previously emphasized as critical aspects of regulations.
Understanding and adhering to these rules will greatly assist organizations in achieving compliance and serve as an important guidepost, much like the cybersecurity frameworks.
What Are the Rules of SEC?
Briefly summarized, the SEC rules necessitate organizations to promptly disclose material cybersecurity incidents within four business days via Form 8-K. There is also an emphasis on enhancing disclosures regarding companies’ cybersecurity risk management and governance in annual reports filed on Form 10-K and Form 20-F. Furthermore, companies are required to specify board oversight of cybersecurity risks and delineate management’s role in addressing significant cyber threats.
The SEC’s focus on the new rules also underscores the critical need to secure not just internal systems, but also the entire supply chain. This serves as a reminder that compliance is essential for safeguarding our collective attack surface.
Vulnerabilities in third-party systems can trigger ripple effects, emphasizing the necessity for robust threat intelligence solutions like SOCRadar. With its Supply Chain Intelligence module, SOCRadar offers valuable insights into third-party risks, empowering organizations to efficiently monitor their entire ecosystem.
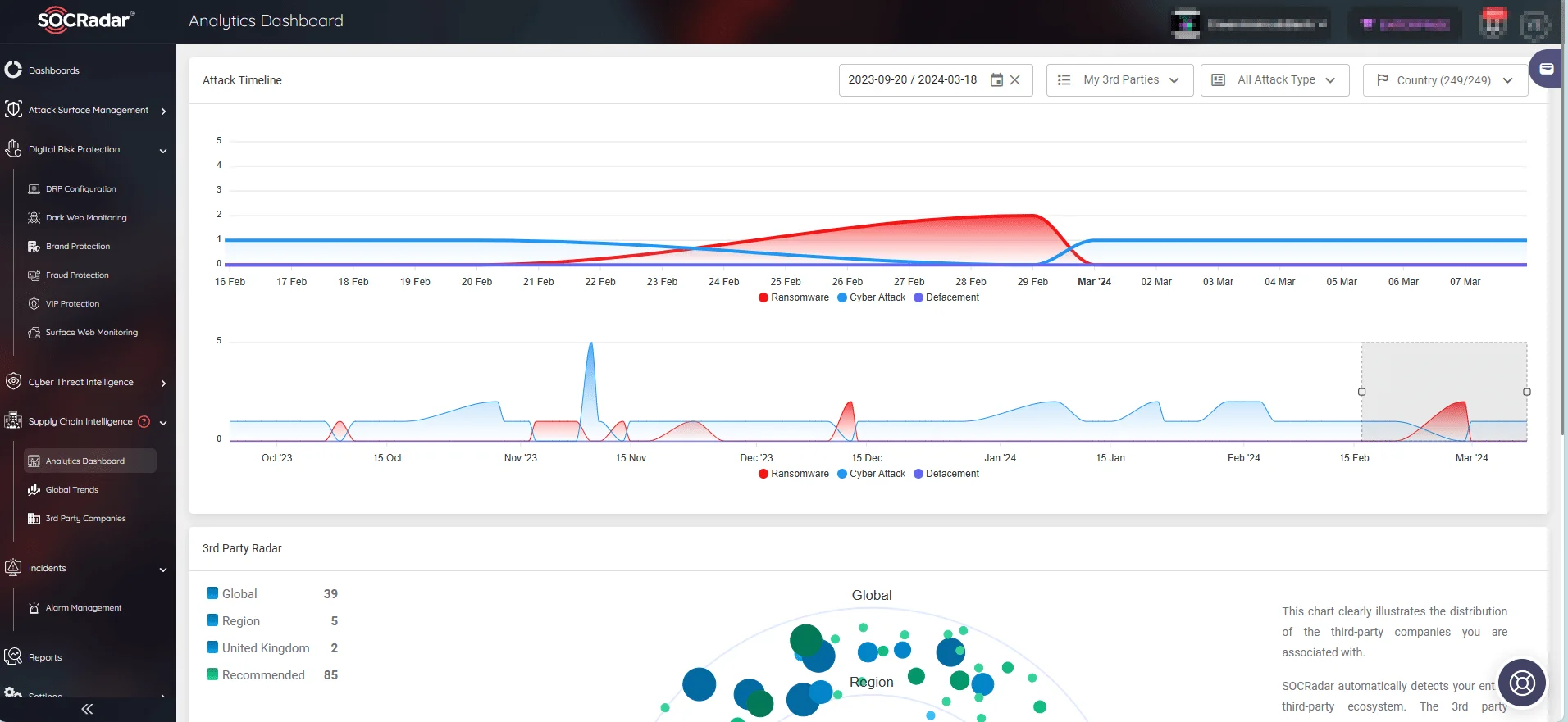
Track all security incidents surrounding your supply chain. (SOCRadar)
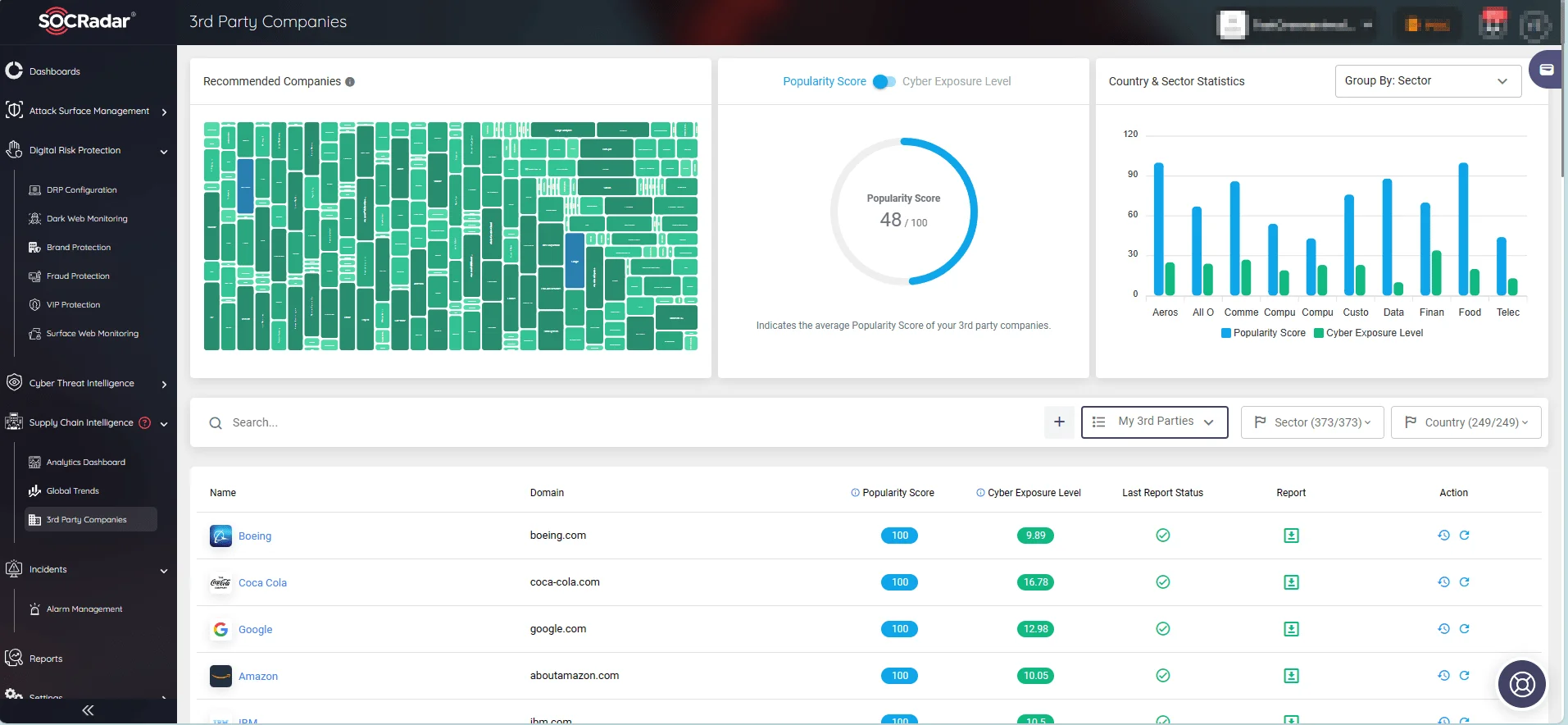
Monitor 3rd party companies and their cyber exposure level. (SOCRadar)
Conclusion; SOCRadar’s Role in Compliance
In today’s digital landscape, regulatory compliance is not just a legal obligation but a crucial component of a robust cybersecurity strategy. Adhering to cybersecurity regulations such as GDPR, HIPAA, and PCI DSS is essential for organizations across all industries to protect sensitive data, mitigate cyber threats, and safeguard their reputation and financial standing.
SOCRadar emerges as a vital ally in this journey towards compliance and enhanced cybersecurity. By offering a suite of advanced features and capabilities, SOCRadar empowers organizations to meet regulatory requirements effectively and proactively address cyber threats.
- Real-time Alerts: SOCRadar provides real-time alerts for potential security threats, enabling organizations to respond promptly and mitigate risks before they escalate.
- Risk Assessment Tools: SOCRadar’s solutions help organizations identify vulnerabilities, prioritize security measures, and assess their overall cybersecurity posture in alignment with regulatory standards.
As cyber threats continue to evolve in complexity and frequency, taking proactive steps in vulnerability management and compliance is imperative. Organizations must invest in robust cybersecurity solutions like SOCRadar to stay ahead of emerging threats, protect their assets, and maintain regulatory compliance.
In conclusion, compliance with cybersecurity regulations is not merely a box to check—it is a continuous journey toward fortifying organizational resilience against cyber threats. By leveraging SOCRadar’s innovative solutions and embracing a proactive approach to compliance, organizations can navigate the ever-changing cybersecurity landscape with confidence and resilience. It’s time to prioritize compliance, enhance cybersecurity practices, and safeguard the future of your organization.



































