Critical BIG-IP iControl REST Vulnerability Allows Arbitrary Code Execution
A critical vulnerability discovered by F5 on May 4 allows threat actors to bypass iControl REST authentication. The flaw which coded CVE-2022-1388 has a CVSS score of 9.8. According to F5’s advisory, there is no data plane exposure; it’s just a control plane issue.

How Does the Vulnerability Affect?
The vulnerability could allow an unauthenticated attacker to gain network access to the BIG-IP system via a management port or self IP address to execute arbitrary commands, create or delete files, or disable services. In the security advisory published by F5, the vulnerability is expressed as “Missing Authentication for Critical Function” with the code CWE-306.
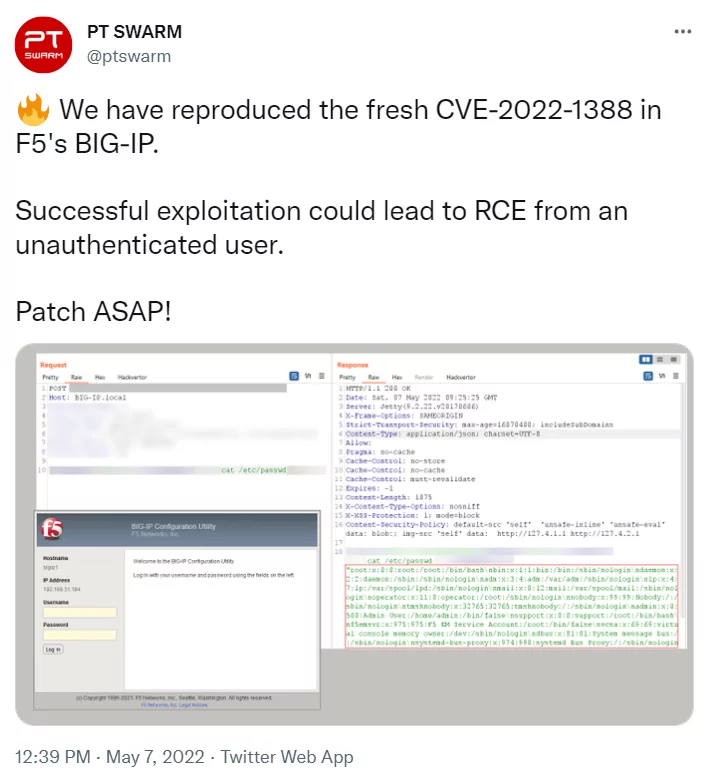
Cybersecurity researchers announced that they were able to create a remote-code-execution exploit for the F5 BIG-IP iControl REST vulnerability. In the post on Twitter, PT SWARM underlined that customers should apply the patches urgently.
Which Versions Are Affected by the Vulnerability?
According to the recommendation text of F5, the following versions of BIG-IP are vulnerable:
- 16.1.0 – 16.1.2
- 15.1.0 – 15.1.5
- 14.1.0 – 14.1.4
- 13.1.0 – 13.1.4
- 12.1.0 – 12.1.6
- 11.6.1 – 11.6.5
How to Fix the Vulnerability?
In F5’s security advisory, updates have been released for versions 17.x, 16.x, 15.x, 14.x, and 13.x. Those who use any of these versions are advised to apply the patches immediately. For versions that do not have any updates at the moment, mitigation measures need to be applied.
F5 recommends restricting access to iControl REST and granting access only to trusted networks and devices until new patches are released. These measures, which limit the attack surface, can be found in the advisory with the headings of blocking iControl REST access via self IP, blocking iControl REST access via the management interface, and changing BIG-IP httpd configuration.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.



































