
Critical Cisco ISE Vulnerabilities Patched: CVE-2025-20124 & CVE-2025-20125
Cisco has issued a security advisory regarding two critical vulnerabilities in its Identity Services Engine (ISE), CVE-2025-20124 and CVE-2025-20125. These vulnerabilities present significant risks, enabling attackers to execute arbitrary commands and bypass authorization controls. If exploited, they could grant unauthorized access to critical network components, potentially leading to data breaches or service disruptions.
Cisco Identity Services Engine (ISE) is an advanced security solution that enables enterprises to control user access and enforce compliance policies across their networks. By providing a platform for identity and access management, ISE helps organizations strengthen infrastructure security while improving operational efficiency.
Given the severity of these vulnerabilities, organizations utilizing Cisco ISE should promptly update their systems to the latest patched versions to mitigate potential security threats and prevent exploitation.
What You Need to Know About the Latest Cisco ISE Vulnerabilities?
Cisco recently disclosed two major vulnerabilities in its ISE platform that could allow attackers to execute unauthorized commands and gain elevated system access. These flaws pose significant security risks, making immediate remediation essential for affected organizations.
CVE-2025-20124: Insecure Java Deserialization Vulnerability (CVSS 9.9)
A serious flaw in Cisco ISE stems from insecure deserialization of Java byte streams. This vulnerability allows an authenticated remote attacker to execute arbitrary commands with root privileges, effectively gaining complete control over the affected system. The exploit is triggered when an attacker sends a maliciously crafted serialized Java object to an exposed API, bypassing security mechanisms.
Importantly, to carry out the attack, the attacker must possess valid read-only administrative credentials, which reduces but does not eliminate the risk of exploitation.
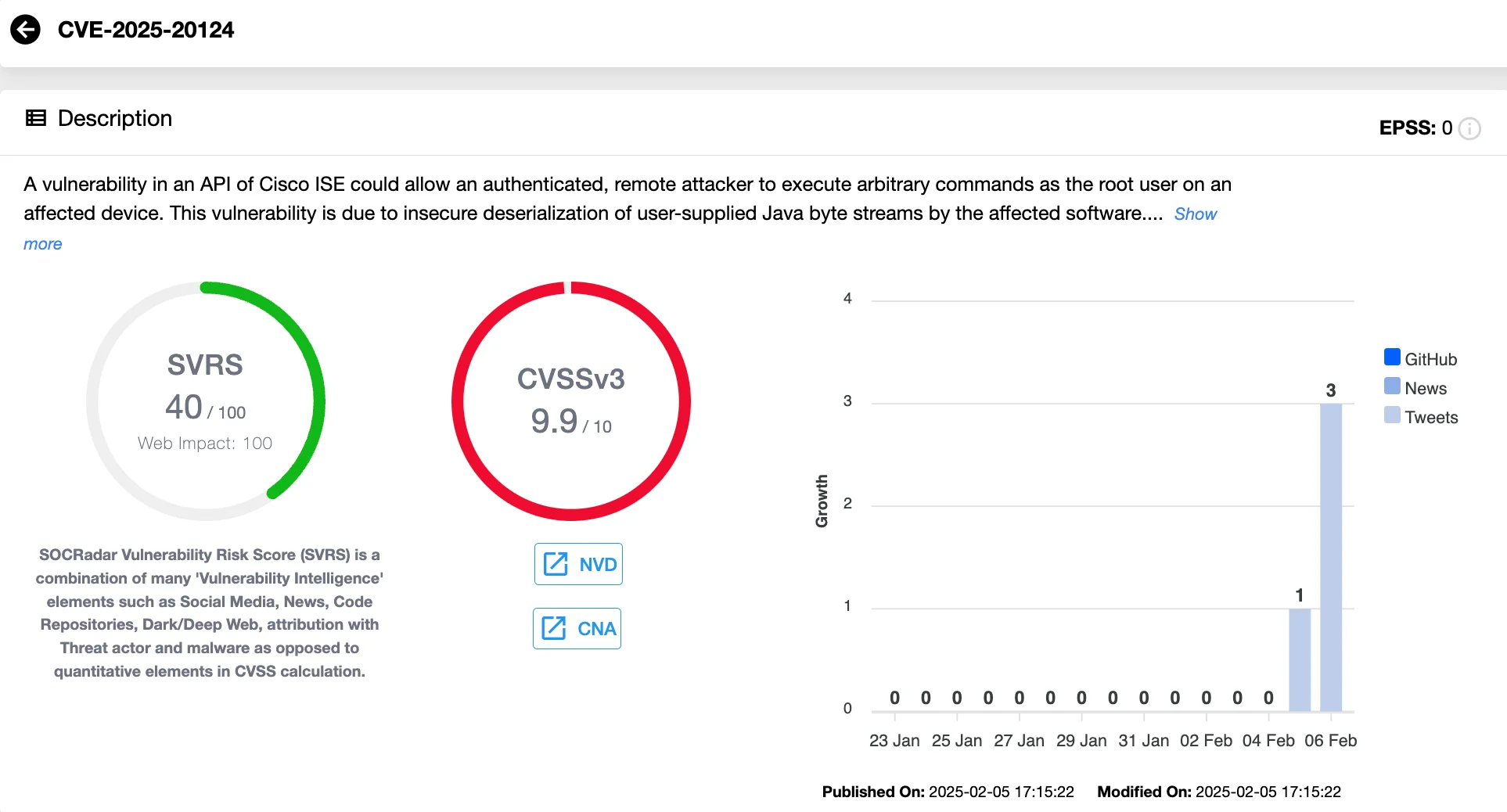
Vulnerability card of CVE-2025-20124 (SOCRadar Vulnerability Intelligence)
CVE-2025-20125: Authorization Bypass Vulnerability (CVSS 9.1)
This vulnerability arises from insufficient authorization validation in a specific API within Cisco ISE. An attacker with read-only administrative credentials can exploit this weakness by sending specially crafted HTTP requests, enabling them to access sensitive system information, modify configurations, and even restart affected nodes.
The lack of stringent access controls in this API makes it a critical security concern, as unauthorized configuration changes can disrupt network security operations and expose critical data to further threats.
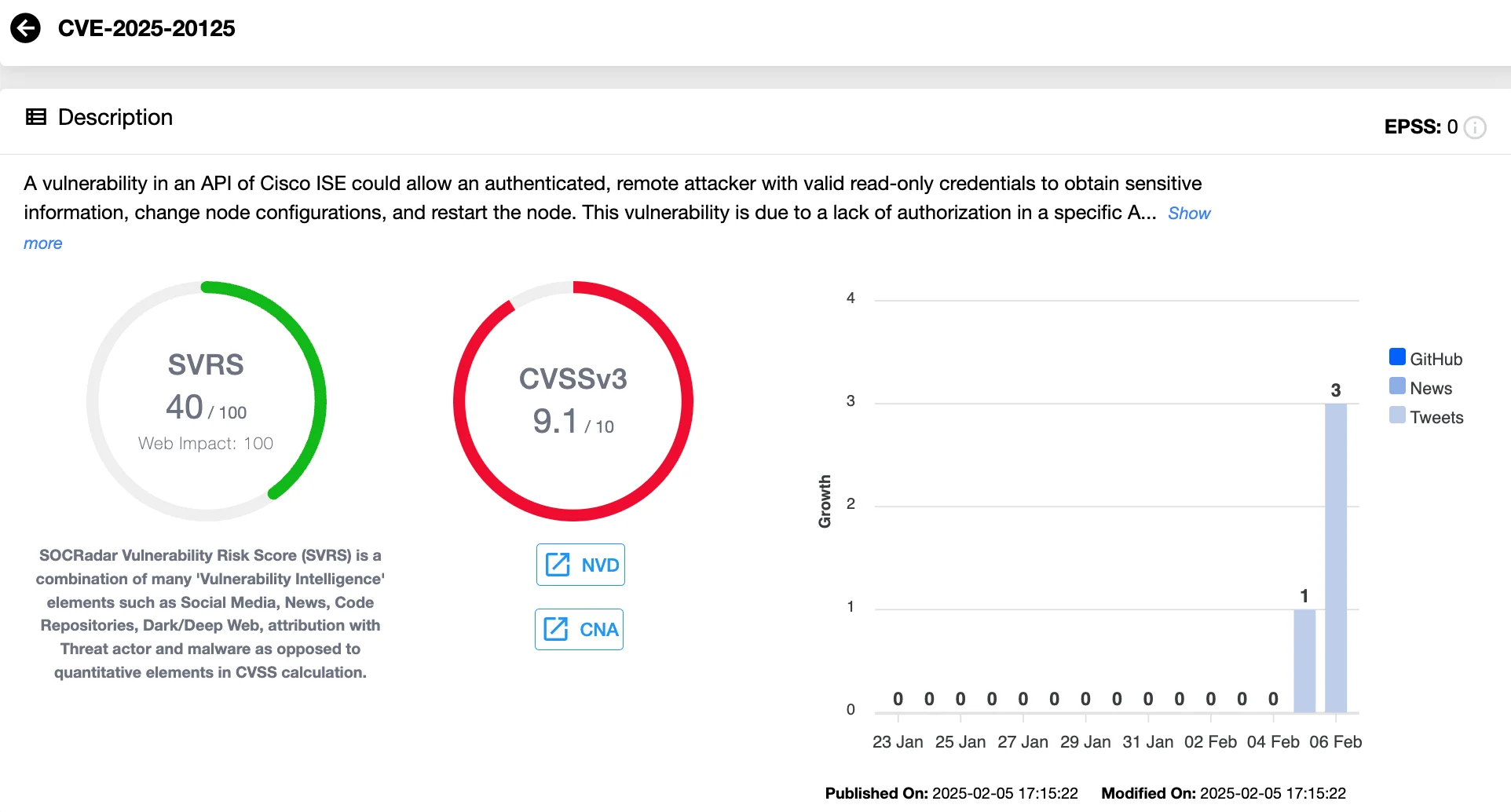
Vulnerability card of CVE-2025-20125 (SOCRadar Vulnerability Intelligence)
If your organization relies on Cisco ISE, vulnerabilities like CVE-2025-20124 and CVE-2025-20125 present a direct threat to your network’s integrity. SOCRadar’s Cyber Threat Intelligence module, with its Vulnerability Intelligence capabilities, enables you to identify, assess, and act on such critical risks in real-time. With detailed insights on exploitability and CVE lifecycle tracking, SOCRadar helps you mitigate risks before they can be weaponized, ensuring your defenses remain intact.
Which Versions Are Affected and What Are the Fixes?
The vulnerabilities impact all Cisco ISE and Cisco ISE Passive Identity Connector (ISE-PIC) configurations. Below are the affected software releases and their respective patches:
- Cisco ISE 3.1: Fixed in 3.1P10
- Cisco ISE 3.2: Fixed in 3.2P7
- Cisco ISE 3.3: Fixed in 3.3P4
It is recommended for those relying on Cisco ISE 3.0 releases to migrate to a fixed release to prevent exploitation. Additionally, Cisco ISE 3.4 releases are not vulnerable to CVE-2025-20124 or CVE-2025-20125.
No Known Exploits – Yet
At present, Cisco’s Product Security Incident Response Team (PSIRT) has not observed any active exploitation of these vulnerabilities. However, given their critical nature, adversaries may attempt to weaponize them soon. Organizations should act swiftly to safeguard their networks.
How Can Organizations Mitigate the Risks of CVE-2025-20124 and CVE-2025-20125?
Cisco has released software updates to address these vulnerabilities, and organizations should upgrade to the latest fixed release as soon as possible. Since no workarounds are available, immediate patching is the only way to mitigate these security risks effectively. Moreover, organizations should limit administrative access and implement strong authentication policies to reduce the likelihood of exploitation.
For more details, refer to Cisco’s official security advisory: Cisco Security Advisory.
Mitigating vulnerabilities like CVE-2025-20124 and CVE-2025-20125 goes beyond just patching; it’s about proactive monitoring and continuous defense. SOCRadar’s Attack Surface Management (ASM) module gives you the tools to monitor your digital assets and identify risks across your entire attack surface.
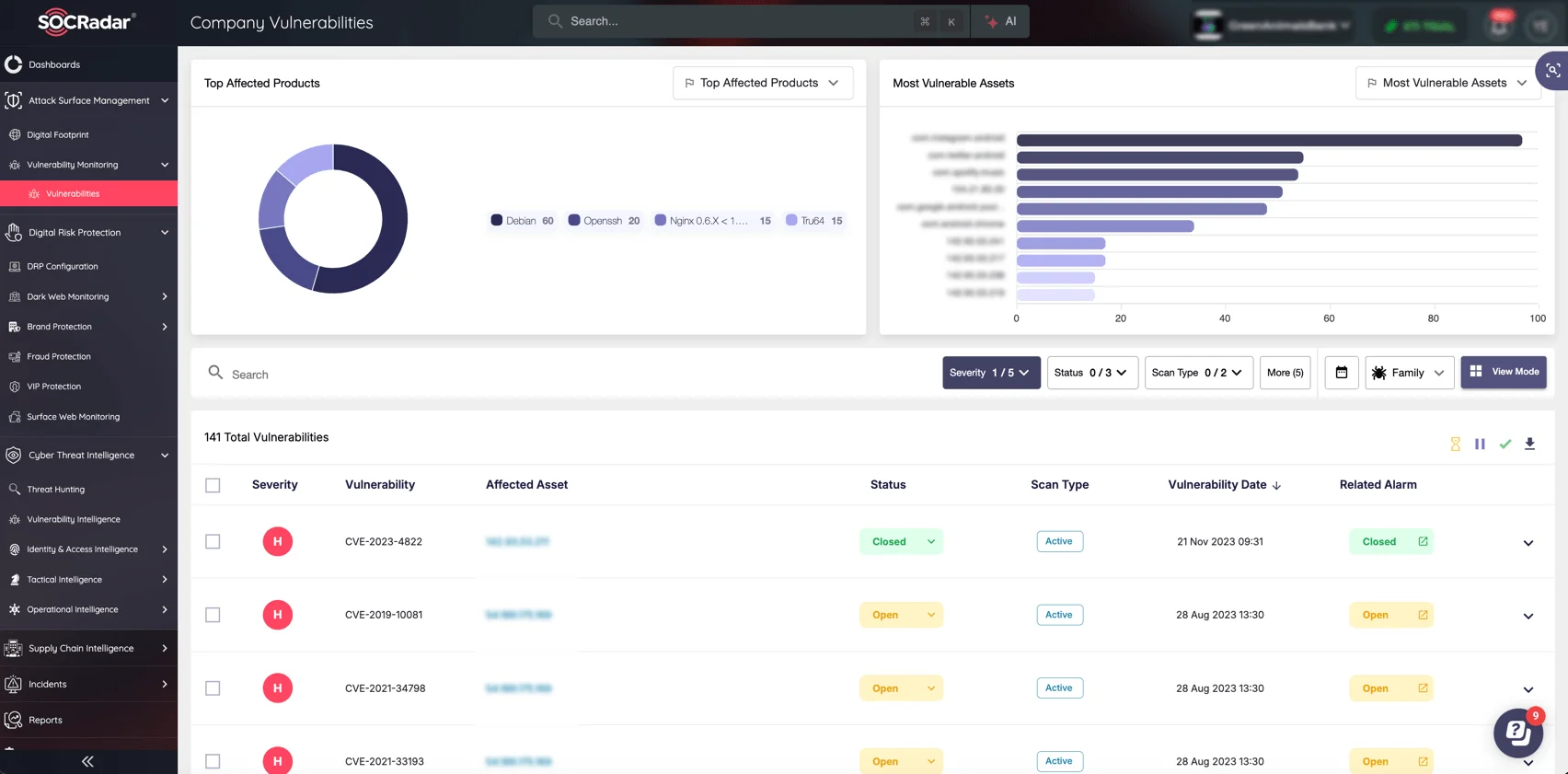
SOCRadar’s Attack Surface Management (ASM) module, Company Vulnerabilities page
By leveraging continuous visibility, intelligent tracking, and automated remediation insights, SOCRadar ASM allows you to prioritize and mitigate risks efficiently, securing your organization before vulnerabilities can be exploited.




































