
Critical Ivanti vTM Vulnerability Exploited (CVE-2024-7593); pgAdmin Flaw Could Expose Data (CVE-2024-9014)
Critical vulnerabilities in Ivanti vTM and PostgreSQL’s pgAdmin tool have recently come under the spotlight, raising serious concerns for organizations relying on them.
A flaw in Ivanti’s Virtual Traffic Manager (vTM), initially patched last month, has now been added to CISA’s Known Exploited Vulnerabilities (KEV) Catalog, signaling active exploitation and the need for immediate patching.
Also recently, pgAdmin has issued an urgent update to address a critical vulnerability that could allow unauthorized access to sensitive information.
Critical Ivanti vTM Vulnerability (CVE-2024-7593) Added to CISA’s KEV Catalog
The vulnerability in Ivanti’s Virtual Traffic Manager (vTM), first addressed in a mid-August advisory by the company, has now been flagged by CISA as actively exploited and added to the Known Exploited Vulnerabilities (KEV) Catalog.
Ivanti vTM is a software-based Application Delivery Controller (ADC) that enhances user experiences across public websites and enterprise applications in various environments.
Identified as CVE-2024-7593 (CVSS score: 9.8), the flaw is an authentication bypass vulnerability caused by a flawed implementation in the authentication process, putting systems using Ivanti vTM at risk.
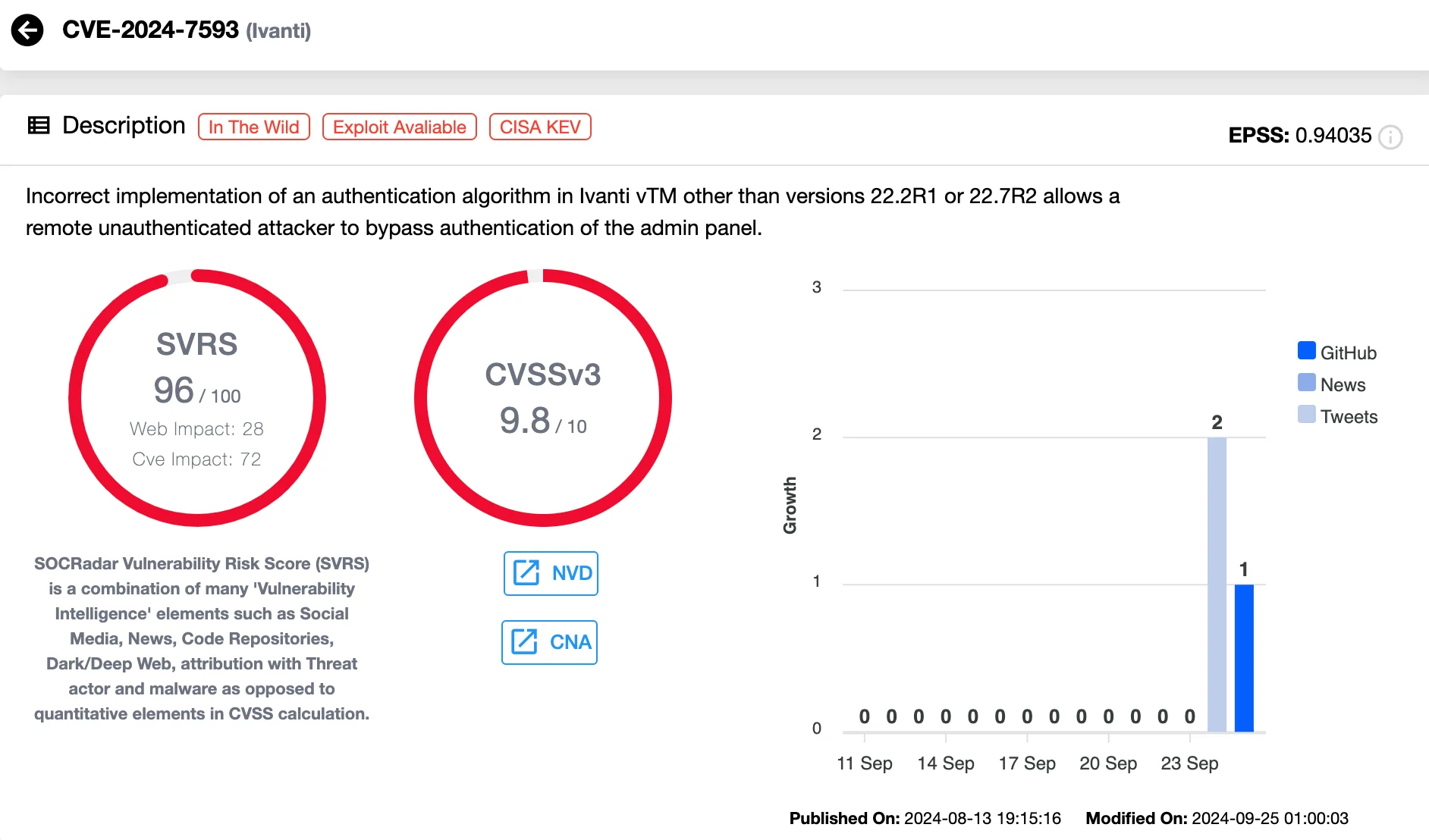
Details of CVE-2024-7593 in Ivanti vTM (SOCRadar Vulnerability Intelligence)
If exploited, remote attackers can bypass the authentication on publicly exposed vTM admin panels, potentially creating unauthorized administrator accounts.
While first announcing the vulnerability’s fix, the Ivanti advisory further warned that a publicly available Proof-of-Concept (PoC) exploit exists, making this vulnerability especially dangerous. Now that the vulnerability is under exploitation, patching it has become more urgent.
SOCRadar’s Vulnerability Intelligence provides detailed insights into emerging vulnerabilities, including updates and exploit activity, helping you mitigate risks before they escalate. With real-time data, you can receive detailed information on CVEs, track which vulnerabilities are being actively exploited, and prioritize patching.
Find CVE trends on SOCRadar’s Vulnerability Intelligence
Affected Versions of Ivanti vTM and Potential Exposure
The Ivanti vTM (Virtual Traffic Manager) versions impacted by this vulnerability include versions 22.2, 22.3, 22.3R2, 22.5R1, 22.6R1, and 22.7R1, with versions 22.2R1 and 22.7R2 being the only non-vulnerable versions.
A quick search through FOFA reveals over 460 instances of public-facing Ivanti vTM systems, underscoring the potential exposure to attackers who may target these appliances.
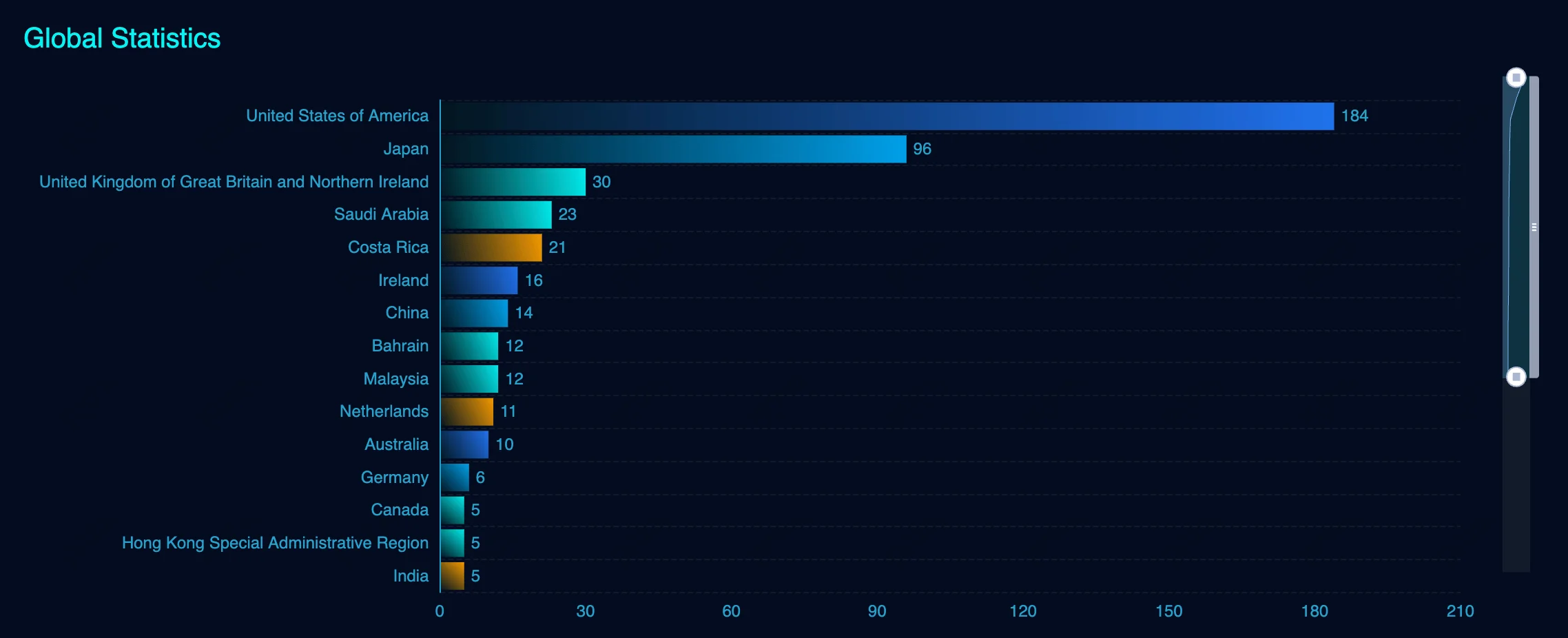
Ivanti vTM instances (FOFA)
Ivanti’s advisory emphasized the importance of patching and securing these instances to avoid unauthorized access; and most recently, CISA issued an alert confirming the addition of CVE-2024-7593 to the KEV Catalog, with a deadline of October 15, 2024 for federal agencies to address this critical vulnerability.
Is There a Workaround to Mitigate Ivanti vTM Exploitation?
In the Ivanti advisory, it is noted that CVE-2024-7593 is exploitable through the vTM’s management interface. Thereby, limiting access to this interface can mitigate exploitation attempts, where updating is not feasible.
Ivanti advises to restrict admin access to internal network environments only, minimizing exposure to the internet. Optionally, you can restrict access further by configuring the “bindip” setting to only allow trusted IP addresses. This provides an additional layer of security by ensuring that only authorized users can access the management interface.
For more information, check out the official Ivanti advisory.
How to Detect Compromise of Ivanti vTM
To check for compromise in your Ivanti vTM, review the ‘Audit Logs Output’ for any unauthorized admin user additions, as advised by Ivanti.
A legitimate log would look like:
[08/Aug/2024:21:53:12 +0530] USER=admin GROUP=admin AUTH=local IP=XX.XX.XX.XXX OPERATION=adduser MODUSER=user1 MODGROUP=admin
An exploit-based user creation will have missing or incorrect details:
[08/Aug/2024:21:54:22 +0530] USER=!!ABSENT!! GROUP=!!ABSENT!! AUTH=!!ABSENT!! IP=!!ABSENT!! OPERATION=adduser MODUSER=user2 MODGROUP=admin
Critical OAuth2 Flaw in pgAdmin Could Expose Sensitive Data: CVE-2024-9014
A critical vulnerability, CVE-2024-9014 (CVSS: 9.9), has been discovered in pgAdmin’s OAuth2 authentication system, potentially allowing attackers to compromise sensitive user data.
The vulnerability poses a serious risk to those relying on pgAdmin for managing PostgreSQL databases, necessitating an immediate update.
pgAdmin is a popular open-source management tool for PostgreSQL, an advanced and widely-used open-source relational database system. It is designed to provide an intuitive interface for managing databases, running queries, and overseeing database operations.
CVE-2024-9014 resides in pgAdmin’s implementation of OAuth2 authentication, a protocol used to securely access systems without exposing sensitive credentials. The vulnerability allows attackers to gain unauthorized access to client IDs and secrets, enabling potential exploitation of user data and compromise of system integrity.
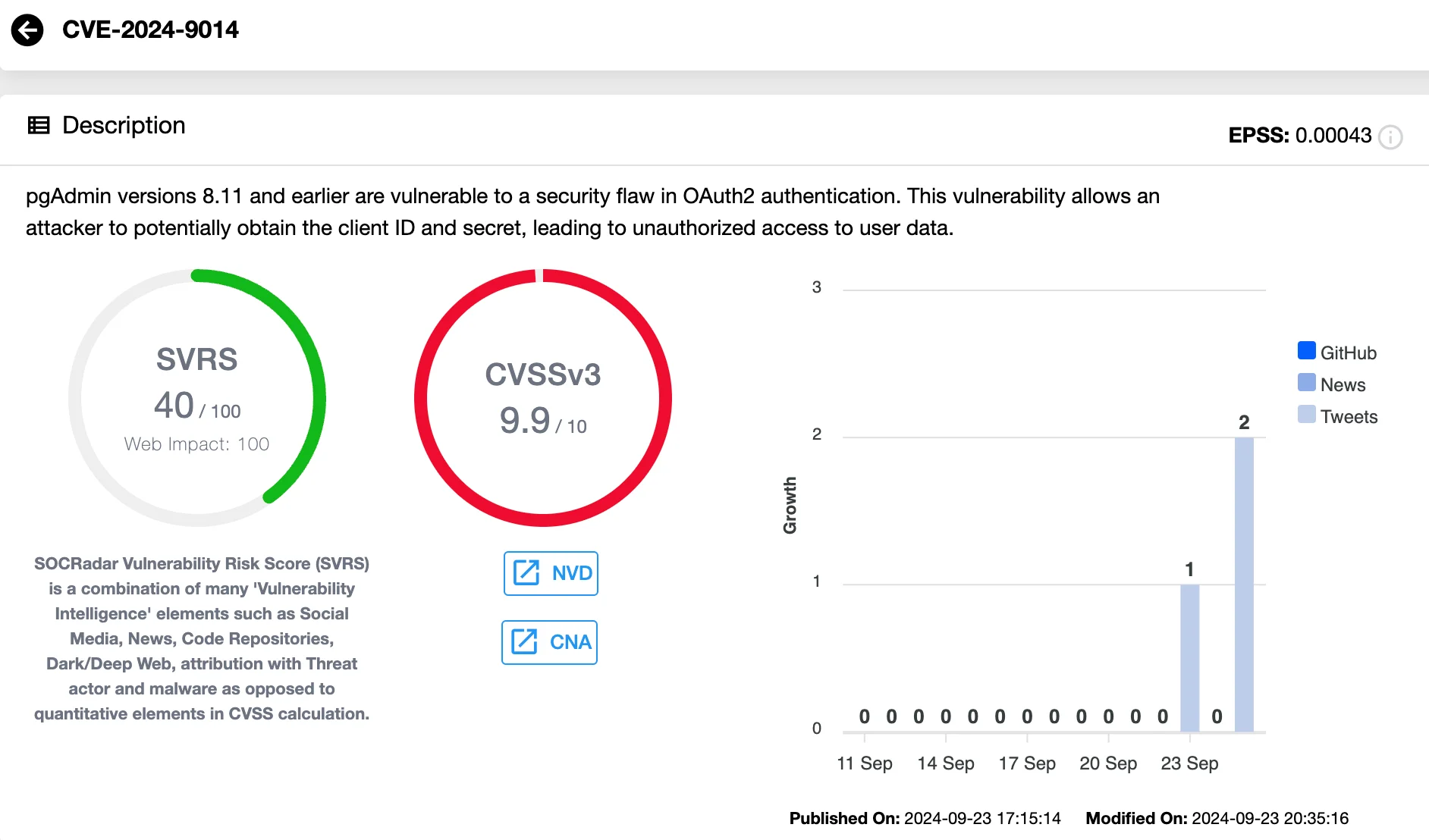
Details of CVE-2024-9014 in pgAdmin (SOCRadar Vulnerability Intelligence)
The flaw impacts pgAdmin versions 8.11 and earlier, and users are strongly urged to upgrade to pgAdmin 4 version 8.12 to protect against exploitation. For more details, see the pgAdmin 4 version 8.12 release notes.
To maintain continuous protection of your digital assets and mitigate the risk of exploitation, implementing proactive monitoring and effective patch management is necessary. Supporting this effort, SOCRadar’s Attack Surface Management (ASM) offers real-time visibility into your organization’s entire digital footprint, helping identify exposed assets, hidden vulnerabilities, and potential entry points for attackers.
SOCRadar’s Attack Surface Management (ASM) module
Monitor assets and company vulnerabilities with the SOCRadar ASM module. ASM also features a CISA KEV Check, cross-checking vulnerabilities with the Known Exploited Vulnerabilities catalog to help your organization ensure compliance.




































