
Critical RCE in Ivanti Endpoint Manager, Citrix Virtual Apps & Desktops Flaws – Patch Now
[Update] November 19, 2024: “Exploitation of CVE-2024-8068 and CVE-2024-8069 Confirmed”
Two recent vulnerability disclosures demand swift attention from organizations using Ivanti Endpoint Manager and Citrix Virtual Apps & Desktops.
Ivanti’s latest security update addresses a critical vulnerability (CVE-2024-50330) that could allow Remote Code Execution (RCE) through SQL injection, making immediate patching essential. Meanwhile, a medium-severity vulnerability in Citrix Virtual Apps & Desktops has been disclosed, potentially leading to authenticated RCE via a misconfigured MSMQ instance. Though of differing severity levels, vulnerabilities highlight risks that should be addressed promptly.
What’s the Critical Vulnerability in Ivanti Endpoint Manager (CVE-2024-50330)?
Ivanti has rolled out urgent patches to address several security flaws in its Endpoint Manager platform. The most critical of these—CVE-2024-50330—has been assigned a CVSS score of 9.8 and can lead to remote code execution through SQL injection. Attackers exploiting this flaw could gain unauthorized access, with the potential to disrupt operations and compromise sensitive data.
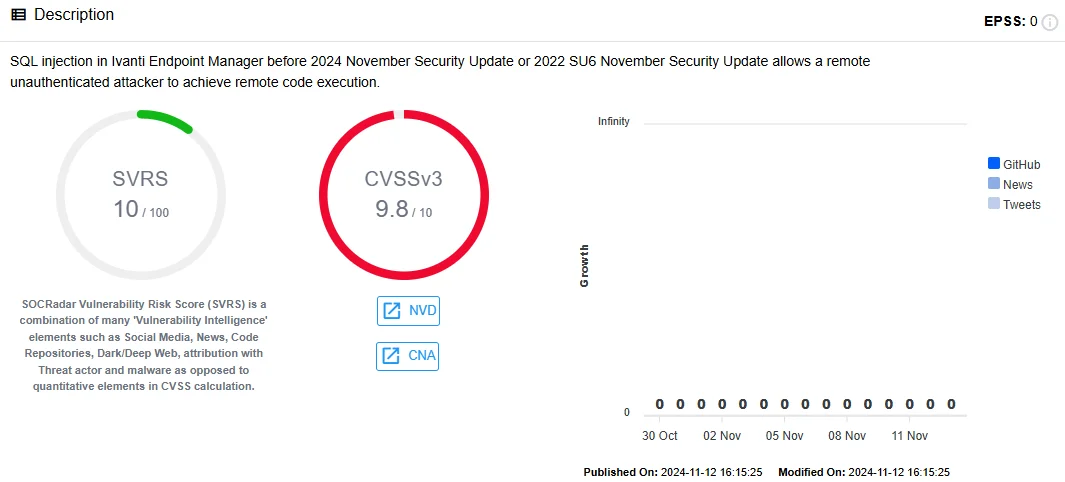
CVE-2024-50330 in SOCRadar Vulnerability Intelligence
Key Vulnerabilities:
- CVE-2024-50330 (CVSS 9.8): Critical SQL injection vulnerability allowing unauthenticated RCE.
- Path Traversal Vulnerabilities (CVSS 7.8): CVE-2024-50323, CVE-2024-34787, and CVE-2024-50322 enable code execution for local unauthenticated attackers under specific conditions.
- SQL Injection Vulnerabilities (CVSS 7.2): Multiple flaws, such as CVE-2024-32839 and CVE-2024-32844, allow authenticated attackers with admin privileges to achieve RCE.
Ivanti has resolved these vulnerabilities in the November Security Update for both the 2024 and 2022 SU6 versions of Endpoint Manager. No active exploitation of these vulnerabilities has been reported, but their high severity still makes immediate patching imperative.
What’s the Medium-Severity Vulnerability in Citrix Virtual Apps & Desktops?
Researchers have uncovered a medium-severity security flaw in Citrix Virtual Apps & Desktops’ Session Recording component, a tool used by system administrators to monitor user sessions. The vulnerability is associated with a misconfigured MSMQ instance combined with the BinaryFormatter deserialization method, which could allow authenticated remote code execution under certain conditions.
Key Vulnerabilities:
- CVE-2024-8068 and CVE-2024-8069 (CVSS 5.1): These vulnerabilities allow privilege escalation and authenticated RCE with NetworkService account access. Attackers need to be authenticated users within the same Active Directory domain and intranet as the session recording server.
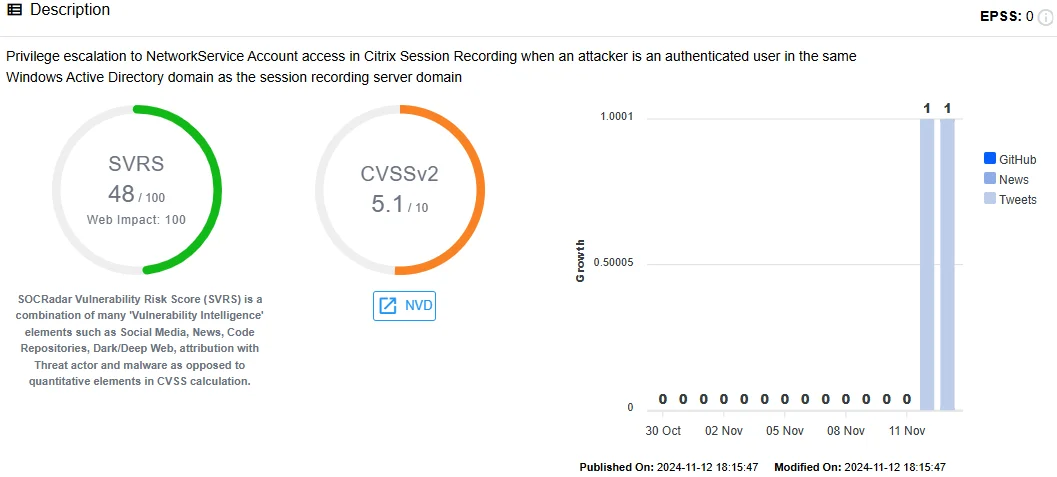
CVE-2024-8068 in SOCRadar Vulnerability Intelligence
BinaryFormatter Security Risks: The issue arises from the Session Recording Storage Manager, which deserializes data received via MSMQ using BinaryFormatter. This deserialization method, flagged by Microsoft as unsafe with untrusted input, allows specially crafted messages to potentially trigger the vulnerability.
Citrix has released patches for affected versions, including:
- Citrix Virtual Apps and Desktops 2407: Hotfix 24.5.200.8.
- Citrix Virtual Apps and Desktops 1912 LTSR: Hotfix 19.12.9100.6.
- Citrix Virtual Apps and Desktops 2203 LTSR: Hotfix 22.03.5100.11.
- Citrix Virtual Apps and Desktops 2402 LTSR: Hotfix 24.02.1200.16.
How Serious Is the Citrix Vulnerability?
According to THN, while Citrix assesses these vulnerabilities as medium in severity, researchers from watchTowr argue that they represent a potential takeover risk under certain conditions. The Shadowserver Foundation has observed initial scanning attempts that suggest active interest from attackers. Organizations using affected Citrix products should prioritize patching to mitigate any potential threat.
What Are SOCRadar’s Recommendations?
- Patch Immediately: Organizations using Ivanti Endpoint Manager should apply the latest security updates to mitigate the risk of RCE. For Citrix users, especially those with high compliance or security needs, patching the Session Recording component is strongly advised despite the medium rating.
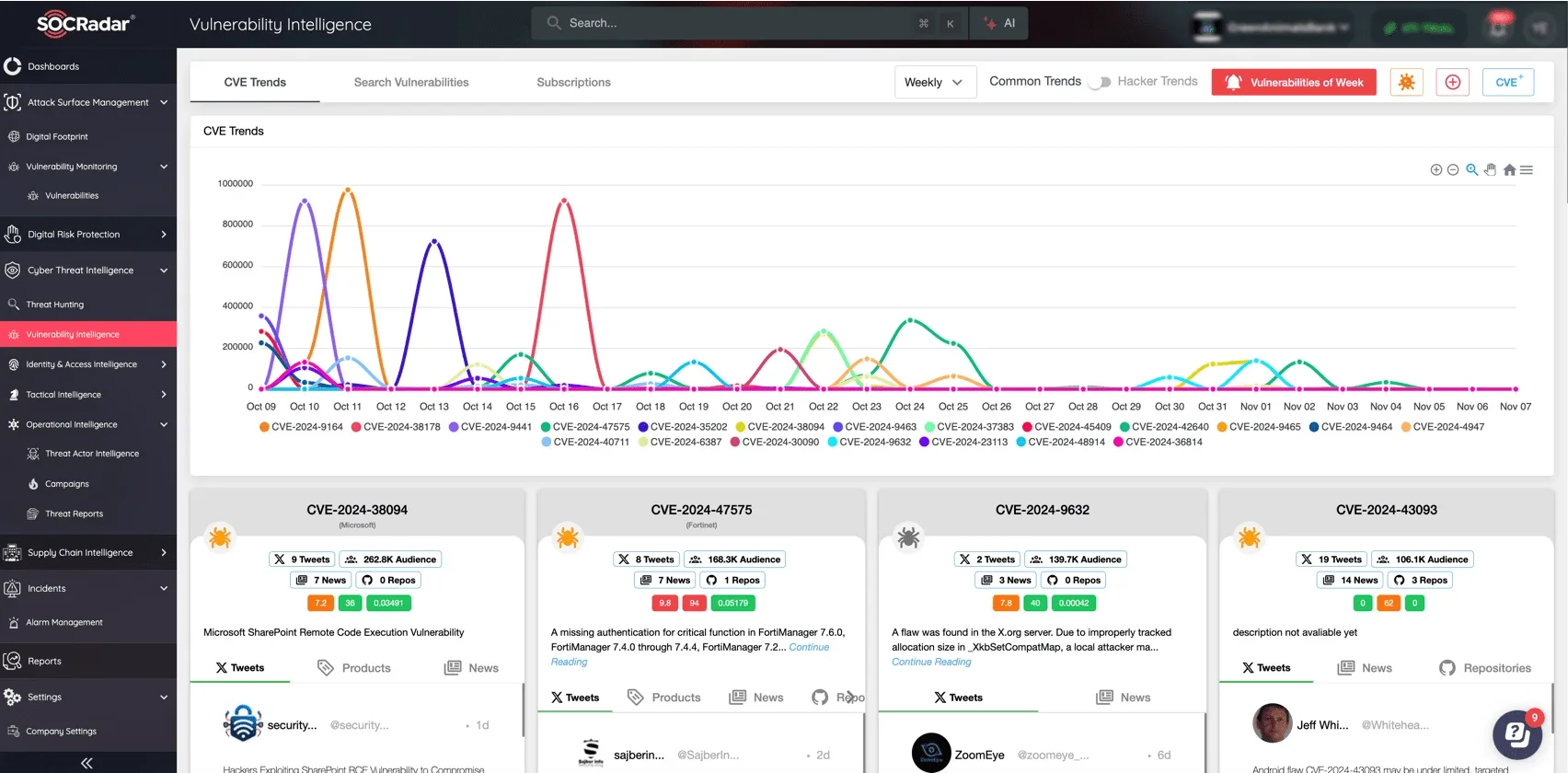
Track CVE trends and search vulnerability information via SOCRadar’s Vulnerability Intelligence
- Monitor for Unusual Activity: For both Ivanti and Citrix environments, monitor for signs of unauthorized access or unusual behavior that could indicate exploitation attempts.
While the Ivanti vulnerability is rated critical, the medium-severity Citrix issue underscores that even moderately severe flaws can create substantial security risks. Both vulnerabilities reveal the need for organizations to maintain a proactive patch management strategy to safeguard against evolving threats.
Exploitation of CVE-2024-8068 and CVE-2024-8069 Confirmed
New reports confirm active exploitation of the Citrix Virtual Apps and Desktops vulnerabilities, CVE-2024-8068 and CVE-2024-8069. Attackers are leveraging exposed Microsoft Message Queuing (MSMQ) services and insecure deserialization in the Citrix software stack to execute arbitrary code, gaining significant control over affected systems.
Attackers have started using Proof-of-Concept (PoC) exploits, with observed exploitation attempts began on November 13, 2024, as noted by Shadowserver on X. Malicious payloads have reportedly been delivered via command-and-control servers, adding urgency to the need for patching.
How Can SOCRadar Help?
Your organization’s digital footprint expands daily, increasing your attack surface and exposing potential entry points for attackers. Are you aware of every asset that could be a gateway to risk? To help you address any vulnerabilities that arise, SOCRadar’s Attack Surface Management (ASM) continuously monitors your external digital footprint, identifying exposed assets and potential security gaps.
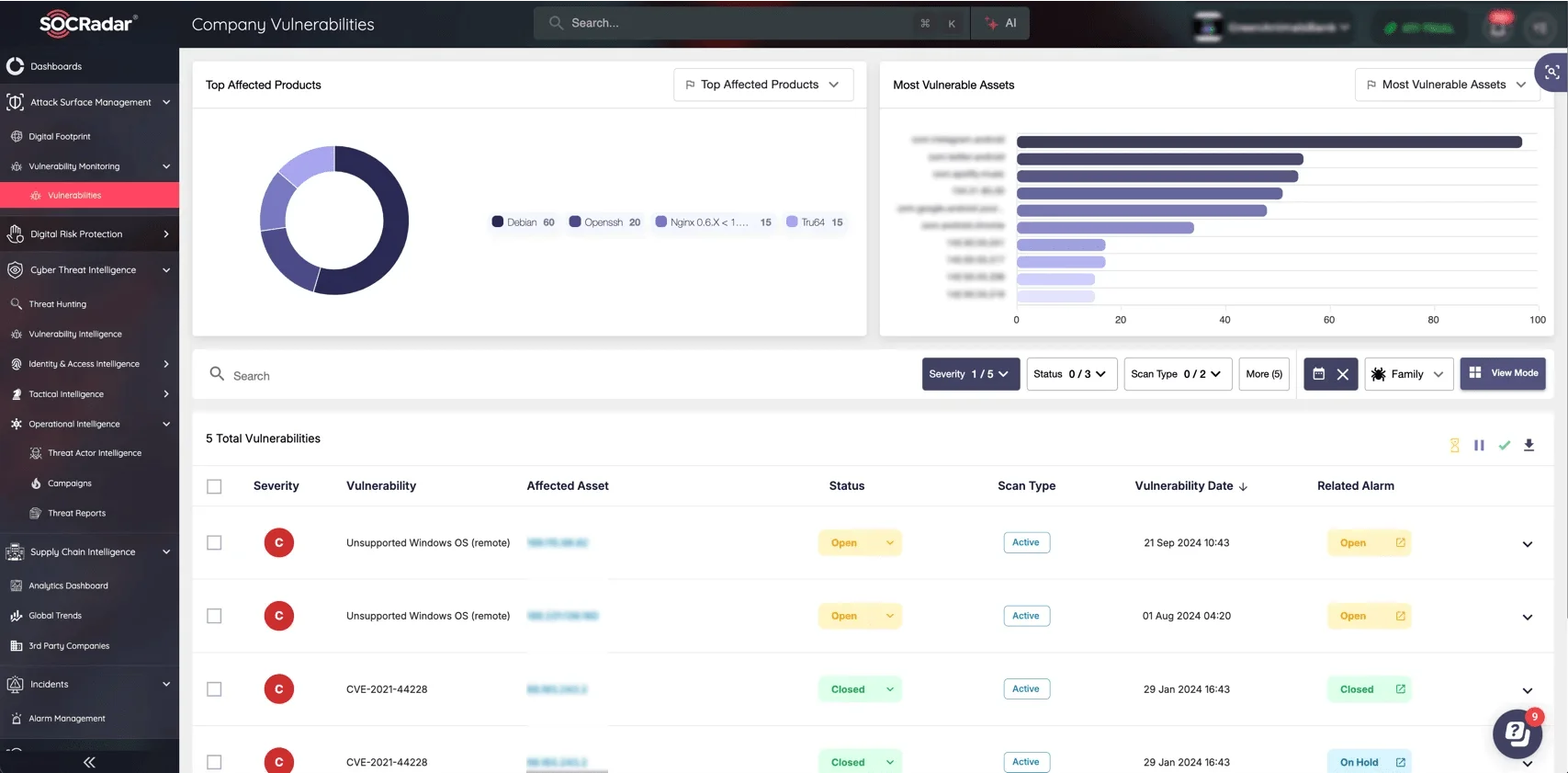
Monitor your Company Vulnerabilities easily with SOCRadar’s ASM module
By using SOCRadar’s ASM, you gain 24/7 monitoring and visibility, automated alerts, and insights into the state of your assets—empowering your team to proactively secure and manage your attack surface.


































