
Critical RCEs: Ivanti Standalone Sentry (CVE-2023-41724), Neurons for ITSM (CVE-2023-46808), Telerik Report Server (CVE-2024-1800)
[Update] March 22, 2024: “CISA Warns for the Vulnerabilities in Ivanti Standalone Sentry and Neurons for ITSM”
Ivanti has fixed critical vulnerabilities that could lead to code execution, including one in Ivanti Standalone Sentry that was reported by NATO Cyber Security Centre researchers.
At the time of disclosure, Ivanti stated there are no known instances of these vulnerabilities being exploited in the wild. However, recent incidents – such as Magnet Goblin‘s exploitation of Ivanti CVEs like CVE-2024-21888, CVE-2024-21893, CVE-2023-46805, and CVE-2024-21887 – have underscored the consistent targeting of Ivanti vulnerabilities by various threat actors.
The appearance of new and critical vulnerabilities within Ivanti products ignites concerns about cybersecurity once more.
How Does CVE-2023-41724 Affect Ivanti Standalone Sentry?
Tracked as CVE-2023-41724 (CVSS: 9.6), the security vulnerability in Standalone Sentry enables unauthenticated threat actors within the same network to execute arbitrary commands on the appliance’s operating system.
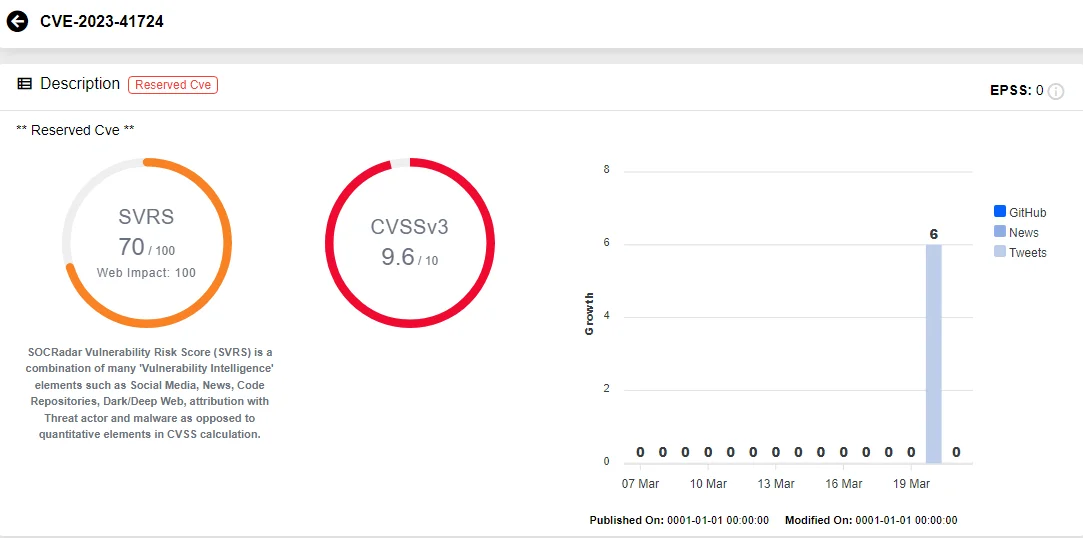
Vulnerability card of CVE-2023-41724 (SOCRadar Vulnerability Intelligence)
Ivanti Standalone Sentry, a key part of Ivanti UEM (Unified Endpoint Management), serves as a gateway between devices and ActiveSync-enabled email servers or backend resources, ensuring secure access and data export/import functionalities. Additionally, it functions as a Kerberos Key Distribution Center Proxy (KKDCP) server.
While the vulnerability is exploitable in low-complexity attacks, Ivanti claims that threat actors without a valid TLS client certificate obtained through EPMM cannot directly exploit it on the Internet.
Through SOCRadar’s Vulnerability Intelligence, you can access comprehensive details on identified vulnerabilities, including the latest updates, available exploits, and vulnerability lifecycles.
With Vulnerability Intelligence, organizations can proactively track and prioritize vulnerabilities, know when attackers begin targeting them, and quickly implement targeted mitigation strategies to reduce their exposure.
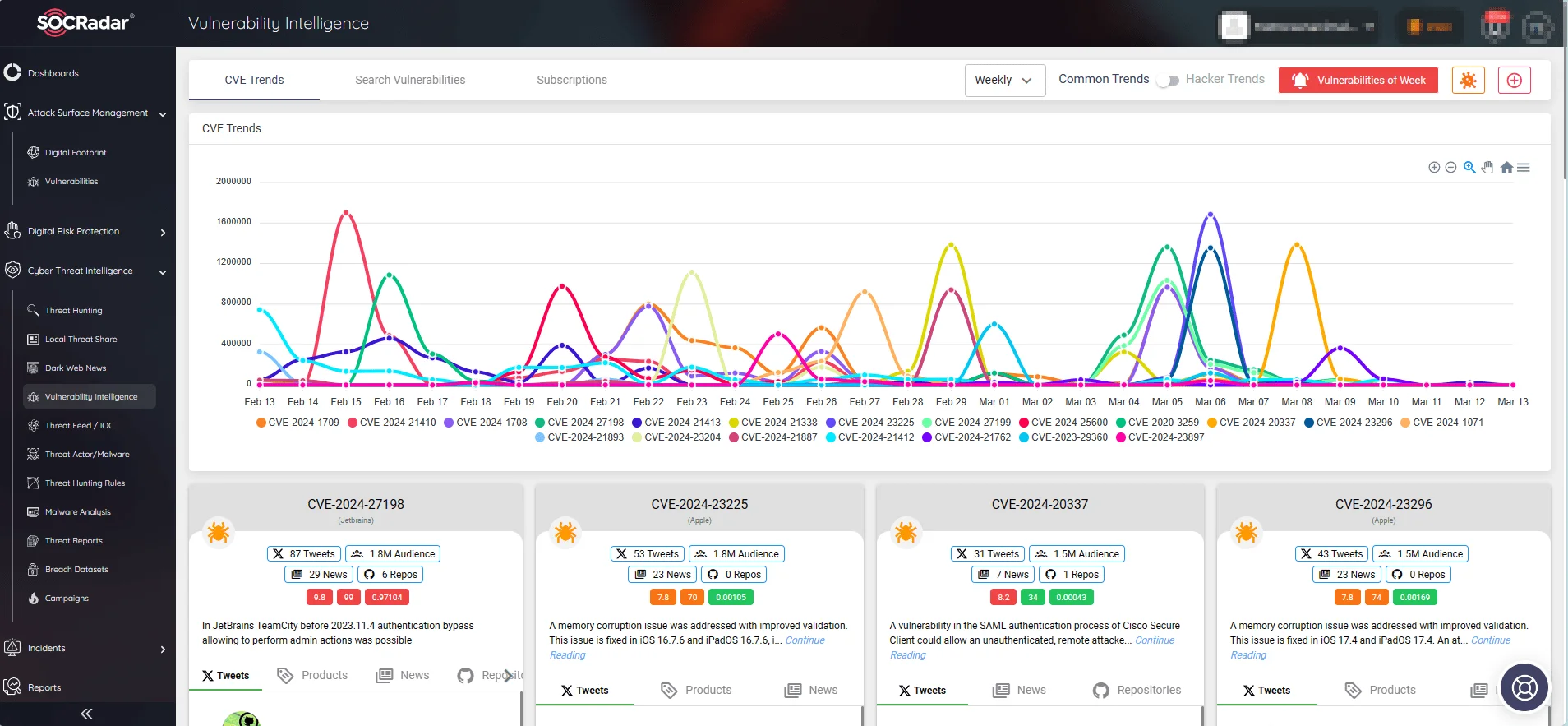
Follow CVE and exploitation trends via SOCRadar’s Vulnerability Intelligence
Which Ivanti Standalone Sentry Versions Are Vulnerable to CVE-2023-41724?
CVE-2023-41724 impacts all supported Ivanti Standalone Sentry versions (9.17.0, 9.18.0, and 9.19.0).
Ivanti urges all users to apply the patches, recommending that those on versions predating 9.17.0 upgrade to a supported version for enhanced security.
What is the CVE-2023-46808 Vulnerability Affecting Ivanti Neurons for ITSM?
Concurrently with CVE-2023-41724, Ivanti fixed another critical vulnerability, affecting its Neurons for ITSM – an IT service management software.
Tracked as CVE-2023-46808 (CVSS: 9.9), this second vulnerability allows remote, authenticated threat actors to write files to sensitive directories, thereby enabling them to execute commands within the context of the web application’s user.
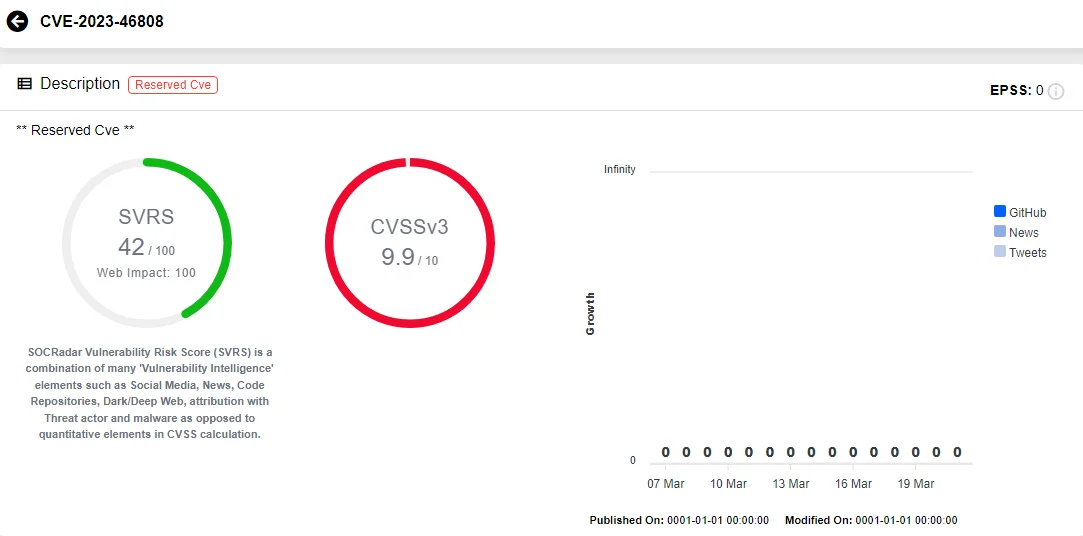
Vulnerability card of CVE-2023-46808 (SOCRadar Vulnerability Intelligence)
What Steps Should You Take to Secure Ivanti Neurons for ITSM?
Ivanti reassured in the advisory that the patch has been applied to all Ivanti Neurons for ITSM Cloud landscapes. Customers are advised to promptly update their on-premise installations to a version that includes the fix – either v2023.3, 2023.2, or 2023.1.
The patches are accessible via the standard download portal, and Ivanti strongly encourages customers to take immediate action to ensure comprehensive protection.
CISA Warns for the Vulnerabilities in Ivanti Standalone Sentry and Neurons for ITSM
The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has issued an alert, urging users and administrators to patch critical RCE vulnerabilities in Ivanti Standalone Sentry and Neurons for ITSM.
CISA indicated the potential for threat actors to exploit these vulnerabilities and gain control of affected systems, stressing the urgency of the situation and the need for vigilance.
Critical RCE in Progress Telerik Report Server, CVE-2024-1800
Another critical vulnerability has recently surfaced in Progress Software’s Telerik Report Server, an enterprise-level reporting solution for storing, creating, managing, and viewing reports.
Designated as CVE-2024-1800 and carrying a critical CVSS score of 9.9, this vulnerability allows Remote Code Execution (RCE) attacks on affected systems, potentially granting attackers complete control over the server and facilitating data theft, malware infection, and more actions.
How to Fix the CVE-2024-1800 Vulnerability in Progress Telerik Report Server?
All versions of the Progress Telerik Report Server released before 2024 Q1 (10.0.24.130) are vulnerable to CVE-2024-1800. There are no workarounds; the advisory states that the only way to resolve the vulnerability is to update to version 2024 Q1 (10.0.24.305) or later.
For guidance on patching the CVE-2024-1800 vulnerability, refer to Progress’ Telerik Report Server upgrading documentation.
Unlock the power of advanced monitoring with SOCRadar’s Attack Surface Management (ASM) module. The platform scans digital assets in real-time, quickly identifying potential vulnerabilities and security incidents. Furthermore, it goes beyond detection by issuing critical alerts in a prompt manner, guaranteeing security teams are notified of any emerging threats.
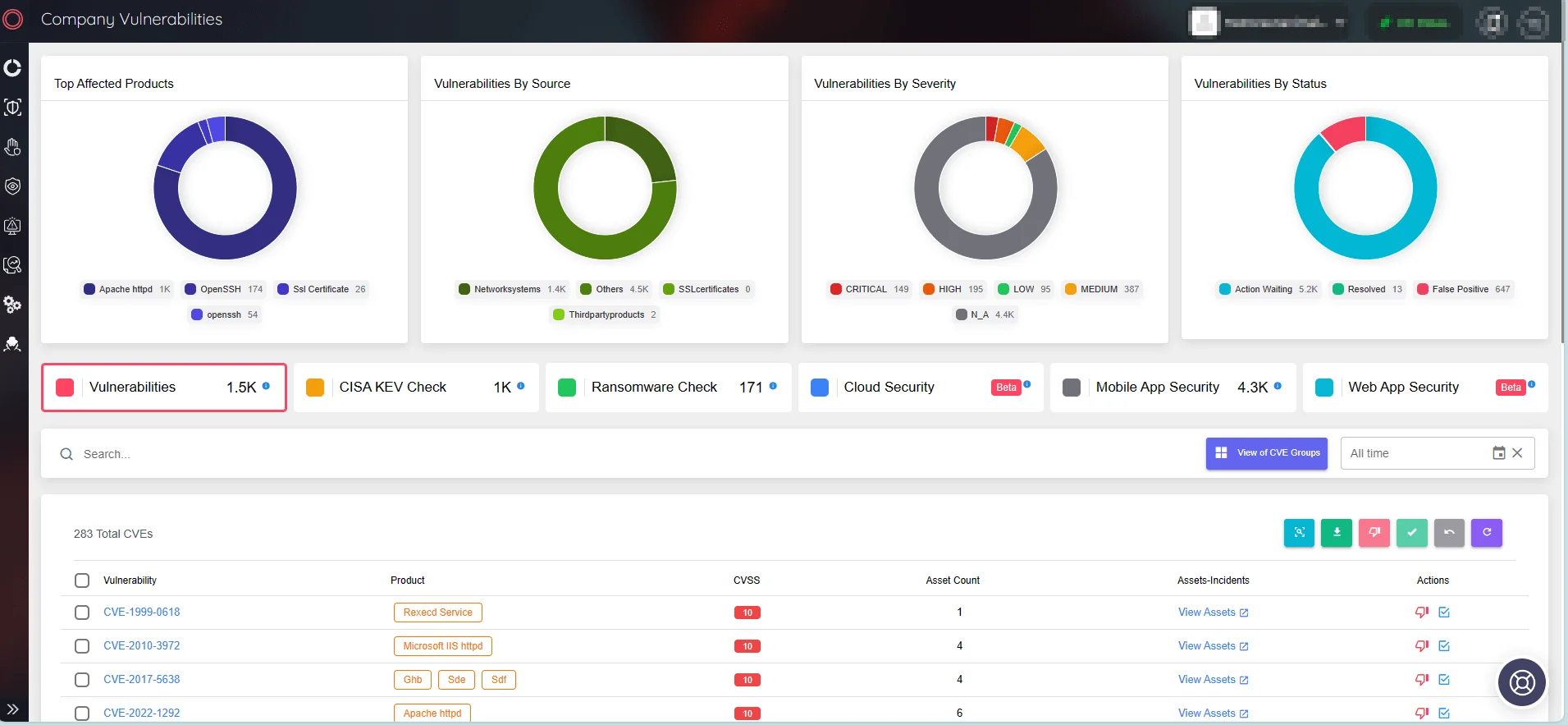
Monitor vulnerabilities throughout your assets with SOCRadar’s ASM



































