
Top 10 Vulnerabilities on the Dark Web in 2023
In the Dark Web, where cybercriminals and hackers converge to trade secrets and illicit goods, vulnerabilities can easily become weapons for many, and the consequences can be catastrophic.
The rapid emergence of operational exploits on Dark Web forums is a chilling testament to the relentless ingenuity of cybercriminals. Their activities extend beyond disclosed vulnerabilities, thriving in a marketplace for zero-day exploits, the holy grail of hacking.
In early 2023, an exploit for CVE-2022-24086, a Remote Code Execution (RCE) in Adobe Commerce, was listed for sale at a staggering $30,000. This price serves as a testament to the value of such exploits and offers a glimpse into the potentially devastating effects they can have in the hands of a malicious actor.
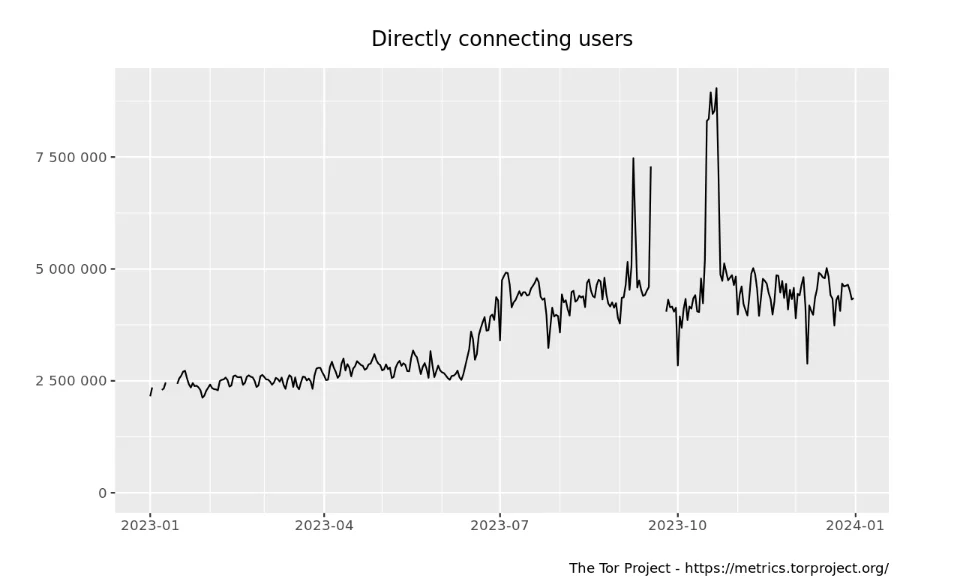
Estimated number of users for the year of 2023 on Tor Metrics
According to Tor Metrics, the dark web witnessed a significant surge in activity throughout 2023. Daily visitors escalated from over 2.5 million at the beginning of the year to a staggering 5 million by year-end. The apex occurred in mid-October 2023, peaking at over 8.5 million daily visitors.
Among these users, a substantial portion likely comprised threat actors engaged in illicit activities or seeking sensitive information and exploits to breach target organizations. This escalating trend demands our immediate attention.
In this article, we journey through the Dark Web to explore the top 10 vulnerabilities that plagued the digital landscape in 2023. From zero-day exploits to the aftermath of vendor disclosures, we explore the threats chattered across the Dark Web.
1. JetBrains TeamCity Authentication Bypass Vulnerability, CVE-2023-42793
A critical authentication bypass vulnerability in JetBrains’ TeamCity, a vital tool for continuous integration and deployment (CI/CD), became a focal point among cyber threat actors.
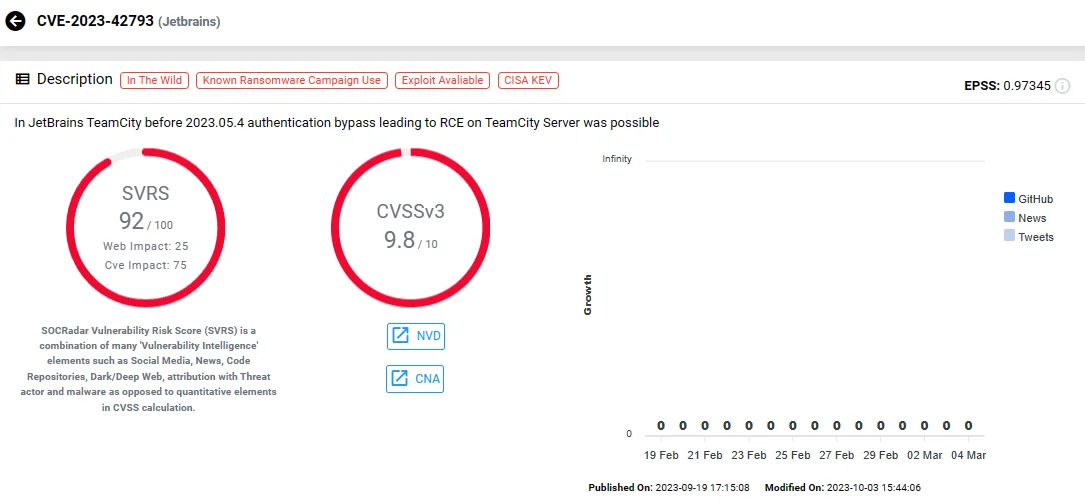
CVE-2023-42793 (SOCRadar)
Within just two weeks of its disclosure, an exploit surfaced in a Russian Telegram channel known for sharing posts related to penetration testing and PoCs for documented vulnerabilities.
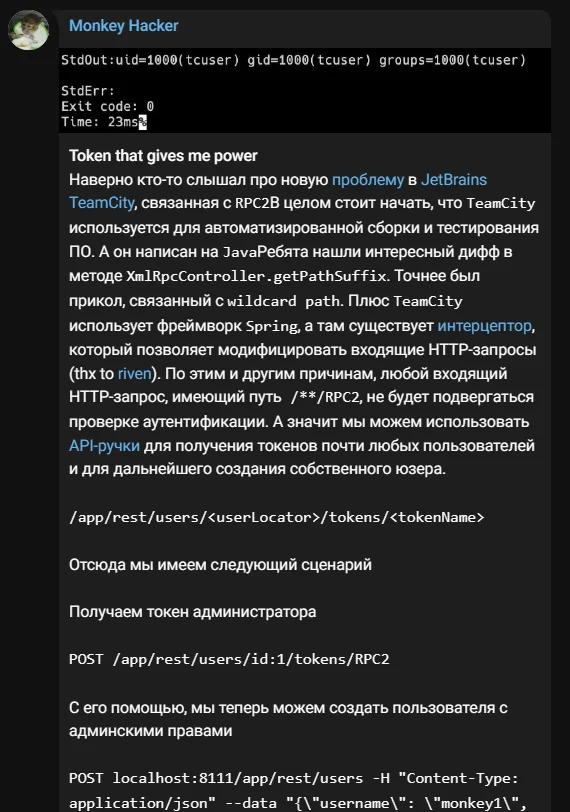
PoC exploit for the TeamCity vulnerability, CVE-2023-42793
The exploit quickly made its way onto hacker forums, enabling other threat actors to attempt its exploitation. Notably, the APT29 group, associated with Russia’s Foreign Intelligence Service (SVR), actively exploited CVE-2023-42793. They targeted the networks of software developers, leveraging initial access to escalate privileges and move laterally within the network while deploying additional backdoors.
Moreover, in October 2023, Microsoft revealed that Lazarus and Andariel, North Korean state-backed hacking groups, were using CVE-2023-42793 to backdoor victims’ networks.
2. Progress MOVEit Transfer SQL Injection Vulnerability, CVE-2023-34362
On May 31, 2023, Progress Software detected and issued an advisory for the critical vulnerability plaguing MOVEit, a widely utilized file transfer solution.
MOVEit finds extensive use across the globe, catering to government agencies, financial institutions, and various public and private sector organizations.
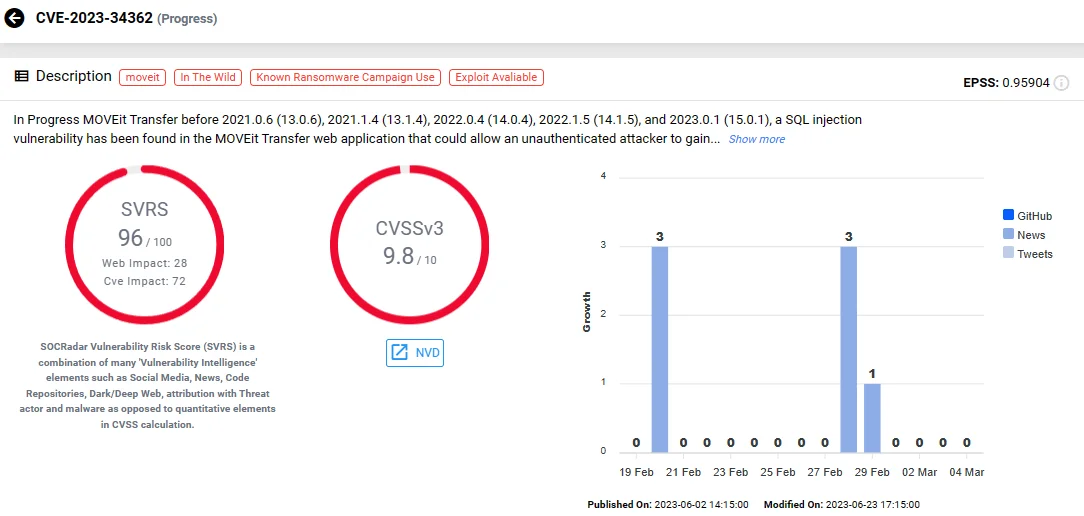
CVE-2023-34362 (SOCRadar)
Exploiting this vulnerability, the Cl0p ransomware group gained unauthorized access, wreaking havoc throughout the year of 2023. Their operations breached over 2,500 organizations worldwide, impacting more than 77 million individuals due to unpatched MOVEit instances.
Despite Cl0p’s notoriety in exploiting CVE-2023-34362, other threat actors also shared exploits related to the vulnerability on dark web forums.
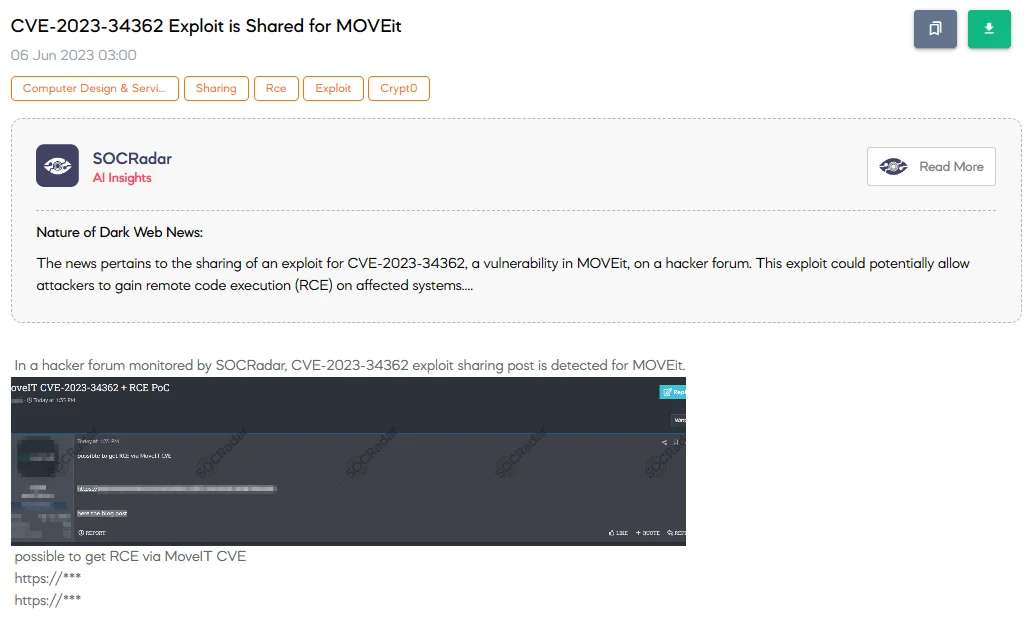
CVE-2023-34362 exploit is shared for MOVEit (SOCRadar Dark Web News)
3. Citrix NetScaler ADC/Gateway Code Injection Vulnerability, CVE-2023-3519
CVE-2023-3519, impacting Citrix NetScaler ADC and Gateway instances, permits unauthenticated remote code execution, granting attackers the ability to execute arbitrary code on the affected system without requiring any privilege or user interaction.
Upon its disclosure, researchers observed several attempted exploitations, evidenced by related IP addresses.
Within two weeks of the CVE code being reserved for the vulnerability, the first Proof-of-Concept (PoC) exploits began to surface. Notably, SOCRadar detected an RCE exploit for this vulnerability being offered for sale on a dark web forum, citing it as a zero-day, even before the vendor disclosed the vulnerability.
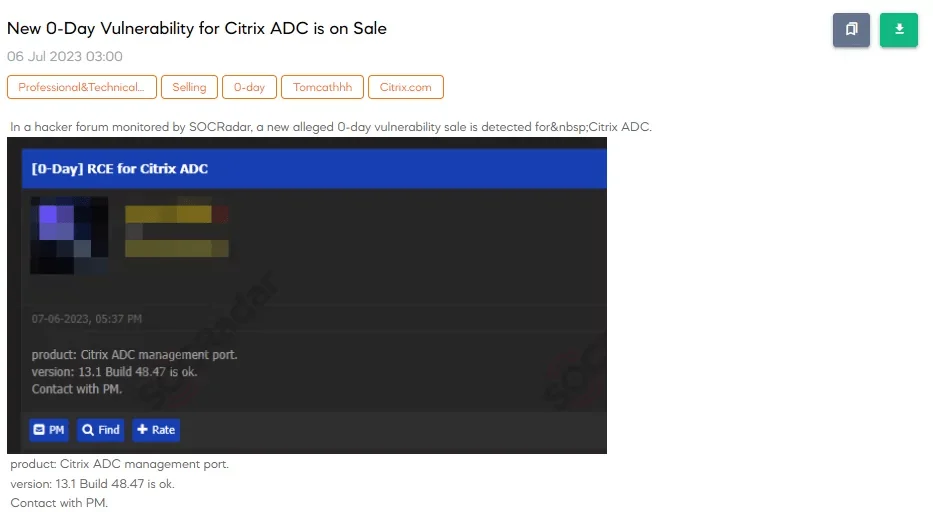
New 0-day vulnerability for Citrix ADC is on sale (SOCRadar Dark Web News)
4. PaperCut MF/NG Improper Access Control Vulnerability, CVE-2023-27350
In mid-April, 2023, PaperCut detected suspicious activity on a customer server, signaling that unpatched servers are being exploited in the wild due to the CVE-2023-27350 vulnerability, allowing RCE attacks. Initial investigations indicated the involvement of the TrueBot malware, associated with Russian hackers known as “Silence.”
Moreover, attackers leveraged CVE-2023-27351, another vulnerability affecting PaperCut, to extract sensitive information from vulnerable PaperCut NG or MF instances.
In May, researchers developed several PoC exploits for the critical vulnerability, which subsequently became the focus of numerous threat actors. These actors exploited the vulnerability to deploy ransomware such as Cl0p, LockBit, and Bl00dy.
Microsoft also reported that state-sponsored threat actors named Mint Sandstorm and Mango Sandstorm exploited the vulnerability to target unpatched PaperCut instances, highlighting the widespread impact and severity of the issue.
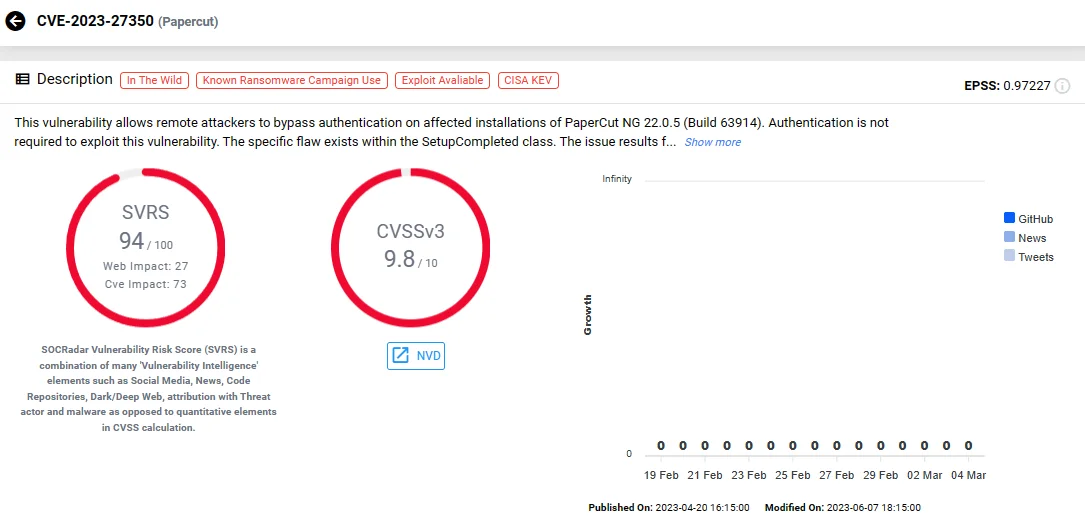
CVE-2023-27350 (SOCRadar)
A Future Demanding Actionable Intelligence and Rapid Response
In an era where threat actors are increasingly drawn to the dark web for lucrative opportunities, organizations face mounting risks from breaches and exploits. Further concerning, the specter of ransomware looms large, threatening organizations’ financial stability and reputation.
The dark web’s role in disseminating vulnerabilities and known CVEs exacerbates the situation, providing a fertile ground for threat actors worldwide. This widespread availability of exploits fuels a sense of foreboding, leaving organizations on edge, uncertain of when they might fall victim.
To counter this threat, proactive measures are essential. Harnessing actionable threat intelligence becomes vital, enabling organizations to swiftly identify and address vulnerabilities demanding immediate attention. With SOCRadar XTI’s Vulnerability Intelligence, organizations gain invaluable insights into hacker trends and comprehensive details on vulnerabilities, including their lifecycle and exploit availability.
Moreover, with the Attack Surface Management module, organizations can receive timely alarms that warn them of security issues before an exploit can take place, ensuring a proactive approach to security and enhancing overall resilience against cyber threats.
By leveraging this intelligence, organizations can streamline their vulnerability management efforts, making informed decisions to safeguard their systems and data from malicious actors.
View CVE trends through SOCRadar’s Vulnerability Intelligence.
5. RARLAB WinRAR Code Execution Vulnerability, CVE-2023-38831
Google’s Threat Analysis Group (TAG) has discovered government-backed hacking groups exploiting CVE-2023-38831, a flaw that triggered unintended file expansion in WinRAR when handling specific archives. The vulnerability enabled attackers to execute arbitrary code by tricking users into opening seemingly harmless files within ZIP archives.
This critical vulnerability has been leveraged as a zero-day exploit to execute arbitrary code and deliver malware to compromised systems.
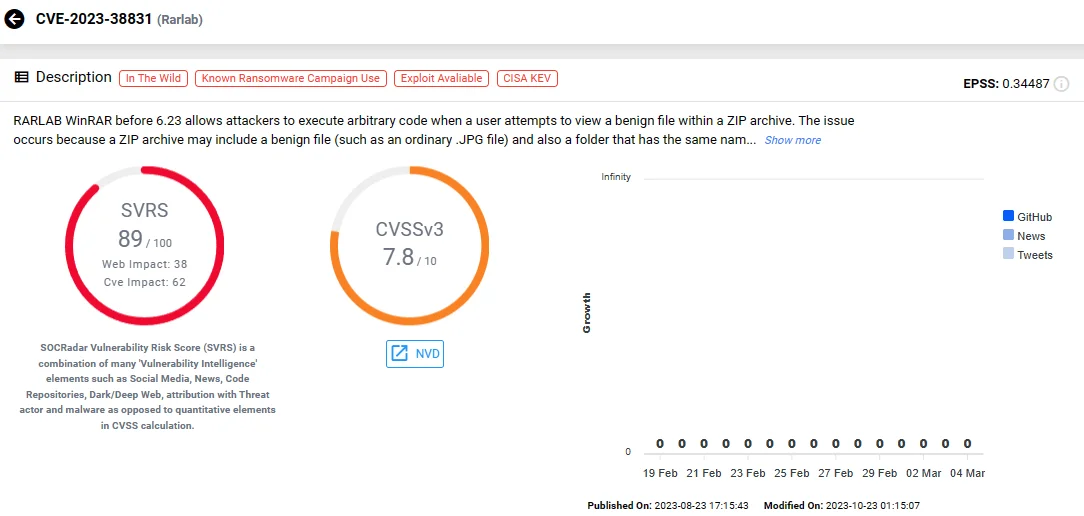
CVE-2023-38831 (SOCRadar)
Google’s findings reveal that threat actors have been exploiting the vulnerability since at least April 2023, targeting financial traders and distributing various malware. Post-disclosure, PoC exploits and exploit generators quickly proliferated on GitHub and hacker forums.
Financially motivated and APT actors were also observed attempting to exploit CVE-2023-38831.

CVE-2023-38831 exploit is shared for WinRAR (SOCRadar Dark Web News)
Listed below are the campaigns that exploited CVE-2023-38831:
- SANDWORM, associated with the Russian GRU, impersonated a Ukrainian drone warfare school. They used a phishing email with a benign PDF alongside a malicious ZIP file containing the exploit, deploying Rhadamanthys infostealer.
- APT28, also linked to the Russian GRU, spear-phished Ukrainian government organizations. They used a free hosting provider to serve the exploit, disguising it as a document from Razumkov Centre, and executed an IRONJAW script through PowerShell.
- APT40, attributed to China, targeted Papua New Guinea. Phishing emails included a Dropbox link to a ZIP archive with the exploit, a password-protected decoy PDF, and an LNK file.
- APT29 exploited CVE-2023-38831 in attacks on European embassies. The campaign, starting in September 2023, targeted diplomatic entities in Azerbaijan, Greece, Romania, and Italy, per the National Security and Defense Council of Ukraine.
6. Microsoft Streaming Service Proxy Privilege Escalation Vulnerability, CVE-2023-36802
CVE-2023-36802, impacting Microsoft Streaming Service Proxy, emerged as a zero-day exploit, as disclosed by Microsoft during the September 2023 Patch Tuesday. Exploiting this vulnerability grants an attacker SYSTEM privileges.
Despite the vulnerability’s disclosure in September 2023, its exploit was already circulating for purchase on dark web forums as early as February 2023. Reports indicate active sales on dark forums for seven months preceding Microsoft and CISA’s advisory on its exploitation.
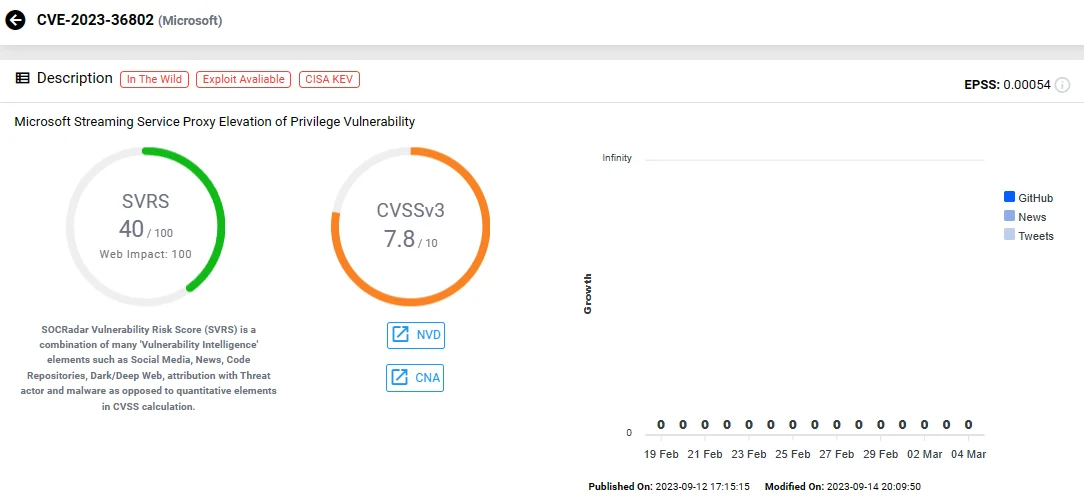
CVE-2023-36802 (SOCRadar)
7. Microsoft Windows Common Log File System (CLFS) Driver Privilege Escalation Vulnerability, CVE-2023-28252
Microsoft has addressed CVE-2023-28252 in its April 2023 Patch Tuesday release, closing a zero-day vulnerability actively exploited by attackers to distribute Nokoyawa ransomware.
This vulnerability resides in the Windows Common Log File System (CLFS) driver, presenting a pathway for privilege escalation. Exploiting CVE-2023-28252 empowers attackers to attain SYSTEM privileges.
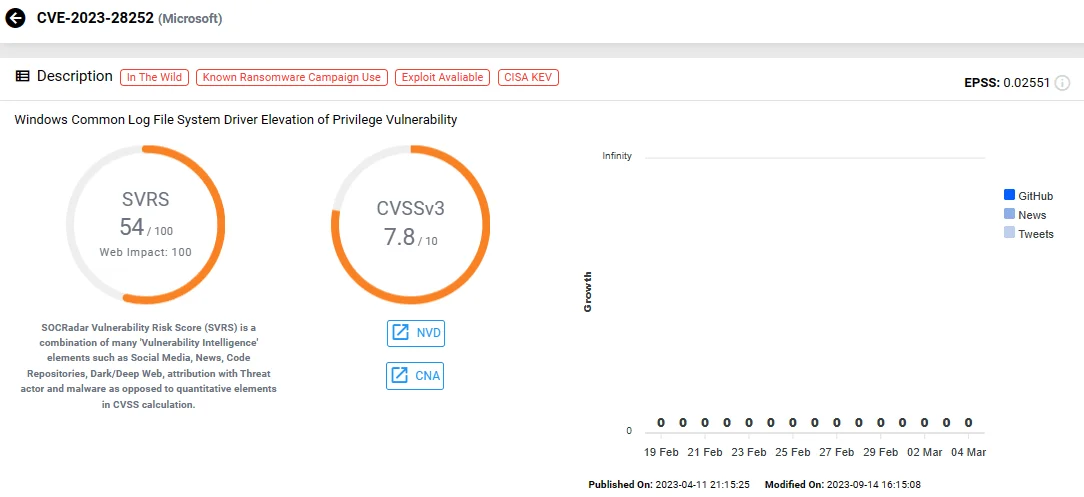
CVE-2023-28252 (SOCRadar)
Since its inception in early 2022, the Nokoyawa ransomware group employed over five other CLFS exploits to target a wide array of industries, including retail, manufacturing, and healthcare, starting from June 2022.
Along with exploit shares for the CLFS vulnerability on dark web forums, certain actors have taken the initiative to disseminate PoC materials for this vulnerability within their Telegram communities.
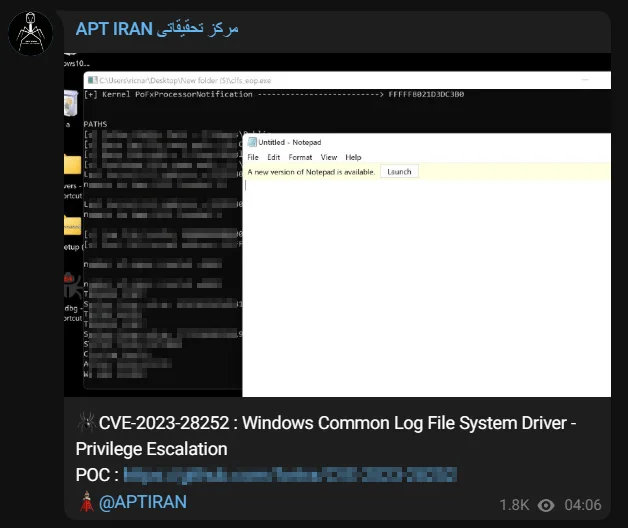
Telegram channel post with PoC exploit for CVE-2023-28252
8. Citrix ShareFile Improper Access Control Vulnerability, CVE-2023-24489
CVE-2023-24489, impacting Citrix ShareFile, a cloud-based file sharing application, enables unauthenticated arbitrary file upload and RCE.
Researchers devised exploits for the vulnerability soon after its disclosure, prompting threat actors’ interest, and subsequently, exploitation attempts.
Importantly, in June, researchers noted a threat actor actively seeking to purchase an exploit for the ShareFile vulnerability, offering a substantial sum of $25,000.
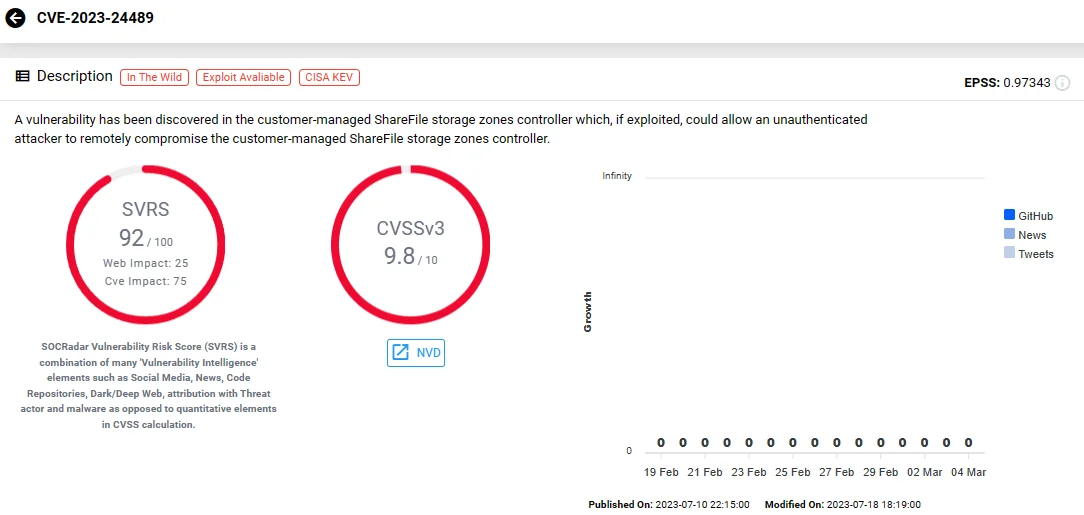
CVE-2023-24489 (SOCRadar)
9. Fortra GoAnywhere MFT Remote Code Execution Vulnerability, CVE-2023-0669
Initial signs of suspicious activity linked to this zero-day RCE vulnerability were detected on January 18, 2023, while it was officially disclosed by Fortra on February 1, 2023.
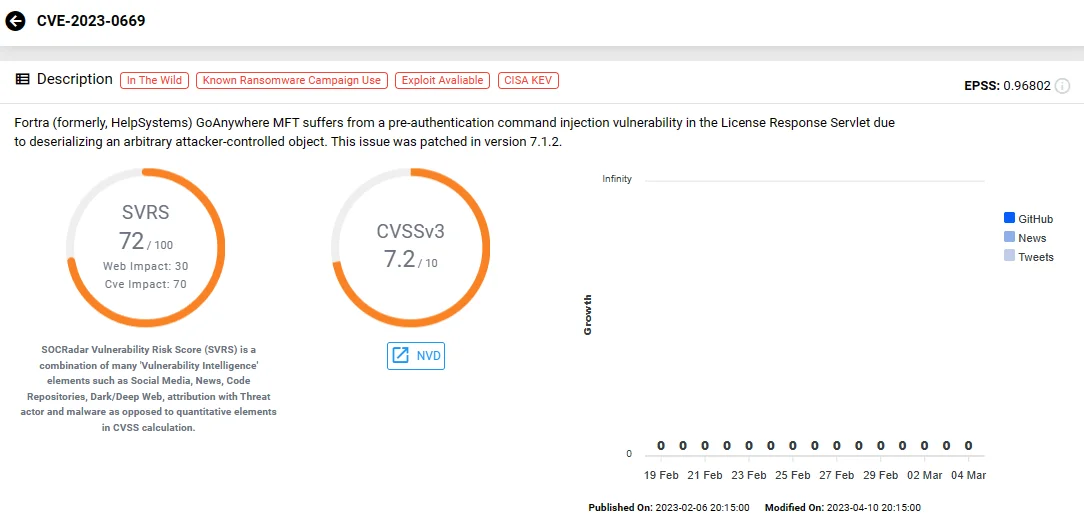
CVE-2023-0669 (SOCRadar)
After the disclosure of this zero-day RCE vulnerability, threat actors actively attempted to exploit it, or sought for access to attempt its exploitation.
It is important to note that products like GoAnywhere MFT and MOVEit Transfer attract the interest of threat actors due to the sensitive nature of their operations and their widespread use in business environments. Consequently, potential threat actors actively seek exploits for such vulnerabilities.
The GoAnywhere MFT RCE vulnerability has been exploited by notorious ransomware groups such as LockBit, Cl0p, and BlackCat (ALPHV), leading to a 91% increase in ransomware attacks within a month of its disclosure.
10. Citrix NetScaler ADC/Gateway Buffer Overflow Vulnerability, CVE-2023-4966 (Citrix Bleed)
In October 2023, researchers found that CVE-2023-4966 had been actively exploited in the wild since August as a zero-day vulnerability.
Dubbed “Citrix Bleed,” this high-severity vulnerability exposes sensitive information, raising concerns about unauthorized data disclosure. The risk amplifies based on the permissions and access levels granted to the compromised identity or session. The vulnerability has been leveraged in targeted exploits and session hijacking attacks.
Significantly, organizations like Xfinity and Boeing fell victim to the Citrix Bleed vulnerability. CISA issued an advisory about LockBit ransomware targeting Boeing Distribution Inc. by exploiting this vulnerability.
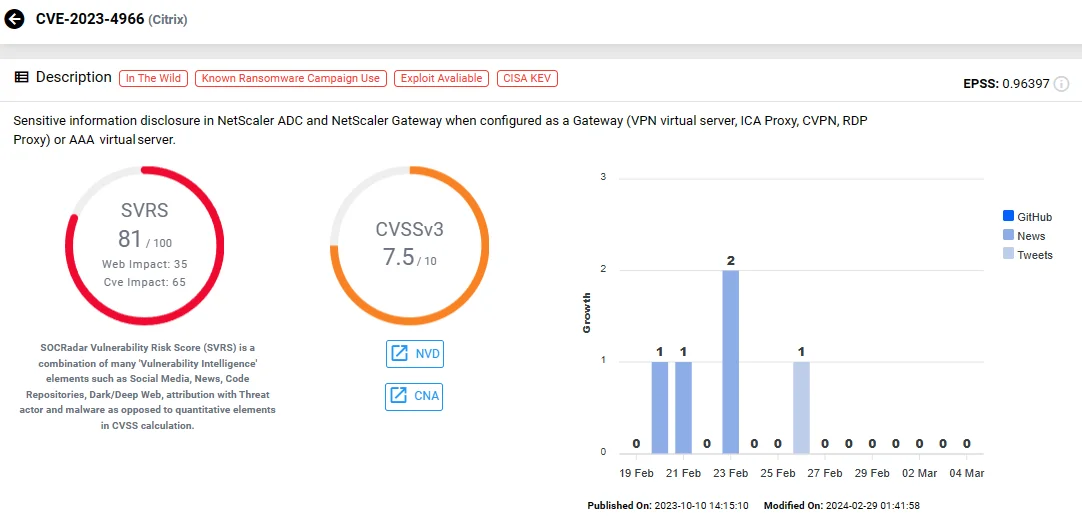
CVE-2023-4966 (SOCRadar)
The impact of CVE-2023-4966 reverberated across the cybersecurity landscape, prompting cyber threat actors to share exploits on dark web forums. Even in January 2024, a guide for the exploit surfaced, indicating ongoing interest and exploitation attempts.
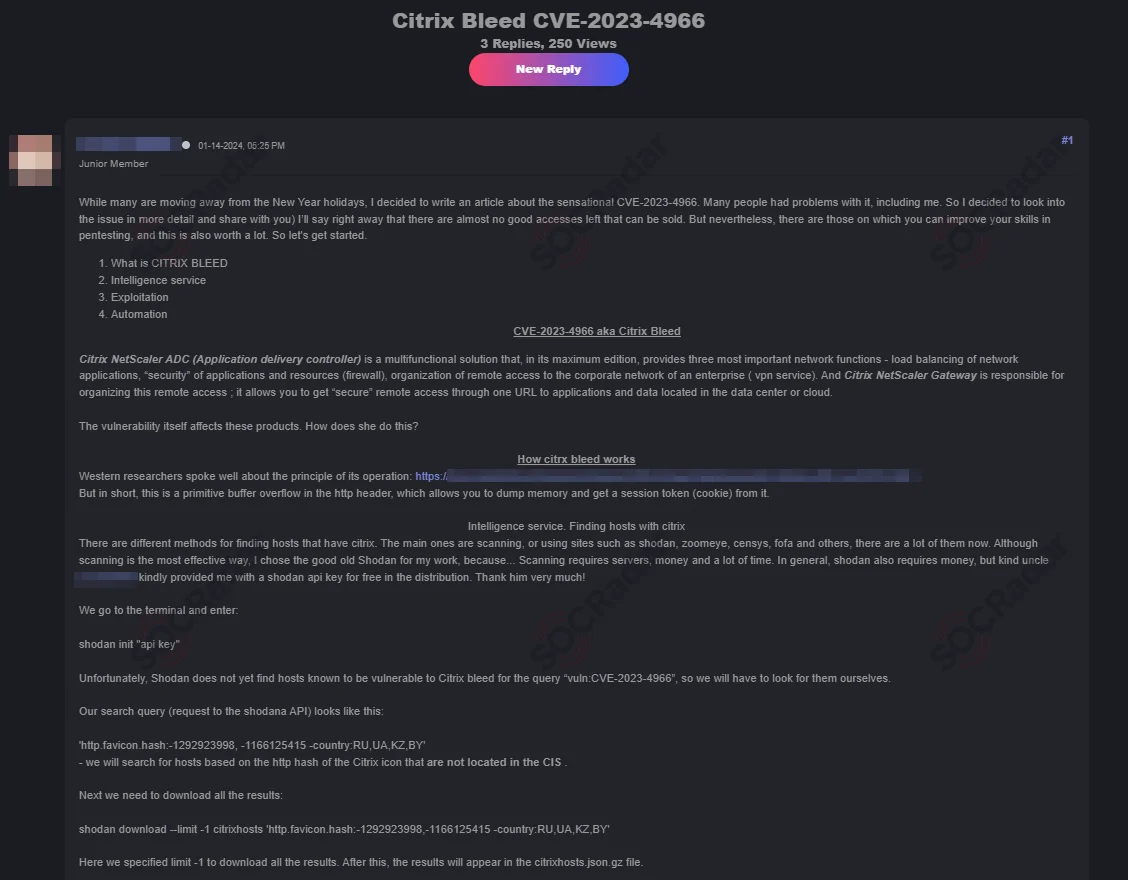
CVE-2023-4966 exploit is shared for Citrix systems (SOCRadar Dark Web News)
Conclusion: Watch Out for Exploits in the Dark Web
Cybersecurity is critical to the success and security of both organizations and individuals. With cyber threats growing at a rapid pace, it is highly important to implement reliable cybersecurity measures to proactively discover vulnerabilities and start remediating vulnerabilities before exploitation occurs. In other words, in terms of security, proactivity triumphs over reactivity.
To remain on top of the unpredictable threat landscape, ongoing monitoring and proactive protection systems are required. By keeping attentive and leveraging the power of threat intelligence, organizations can protect their digital assets and maintain their integrity.
In this rapidly changing digital landscape, SOCRadar emerges as a key source of protection. Its powerful threat intelligence platform enables customers to actively monitor hacker activity and keep ahead of emerging threats lurking in dark web forums.
With SOCRadar’s Dark Web Monitoring, you can easily monitor the Dark Web for data exposures.
For a deeper understanding of the operations of the top illicit markets for cyber threat actors and insights into the threats they pose, explore our “Top 10 Deep Web and Dark Web Forums” blog post.



































