
Impact of CL0P Ransomware on the Cyber Threat Landscape in 2023: An Analysis of Cyber Tactics and Threat Evolution Over the Year
In the intricate web of cybersecurity threats, the CL0P ransomware group carved out a reputation for its sophisticated and strategic operations last year. This article aims to unpack the unique modus operandi of CL0P, contrasting it with other formidable players in the ransomware arena. Leveraging SOCRadar Cyber Intelligence’s rich data repository, we reveal a year’s worth of tactics, targets, and trends that set CL0P apart.
Dissecting the Sophisticated Threat Landscape Shaped by CL0P
SOCRadar’s vigilant monitoring and analytical prowess have investigated CL0P’s nuanced attack patterns, including its selective exploitation of critical 0-day vulnerabilities and its psychological leverage over victims. We’ll delve into the group’s unpredictable attack schedule, its strategic communication choices, and its targeted geographic and industry preferences, all underpinned by data collected from dark web forums, leak sites, and ransomware group blogs.
Through meticulous documentation and extensive tagging, SOCRadar has captured over 4,070 cyber events, providing us with a robust foundation to analyze and understand CL0P’s approach within the broader context of global cyber threats. As we dissect these findings, we aim not only to inform but also to empower organizations with actionable intelligence for bolstering their cybersecurity defenses.
Analyzing the Distinctiveness of CL0P: A Comparative Study
To understand the unique characteristics of the CL0P ransomware group, it is essential to compare its activities with other leading groups. This section provides a comparative analysis, juxtaposing CL0P with three of the most active ransomware groups: LockBit 3.0, AlphV (also known as BlackCat), and Play.
Comparative Analysis of Ransomware Group Activities
| Ransomware Group | Number of Documented Incidents |
|---|---|
| LockBit 3.0 | 940 |
| CL0P | 387 |
| AlphV (BlackCat) | 382 |
| Play | 273 |
The table above illustrates the activity levels of the top ransomware groups, based on the number of incidents documented on the SOCRadar platform from January to November 2023. The data highlights the contrasting operational scales and approaches of these groups, with a specific focus on the CL0P ransomware group.
This comparative analysis serves as a foundation to unravel how CL0P’s modus operandi diverges from these groups. The data not only reflects the frequency of attacks by each group but also sets the stage for a deeper dive into their operational tactics, targets, and impacts.
Despite CL0P’s attack volume being only a third of LockBit 3.0’s, they achieved this without relying on the Ransomware as a Service model utilized by LockBit. Furthermore, their strategy of conducting attacks over a relatively brief period shook the ransomware landscape unexpectedly during the summer months. This landscape had been steadily evolving throughout the year, and their targets primarily consisted of prominent corporate entities.
Monthly Ransomware Attack Trends of 2023
The cybersecurity landscape is often illuminated by the patterns and frequencies of attacks by various threat actors. In 2023, a significant disparity in the operational rhythm among different ransomware groups emerged, as illustrated by the monthly distribution of their attacks.
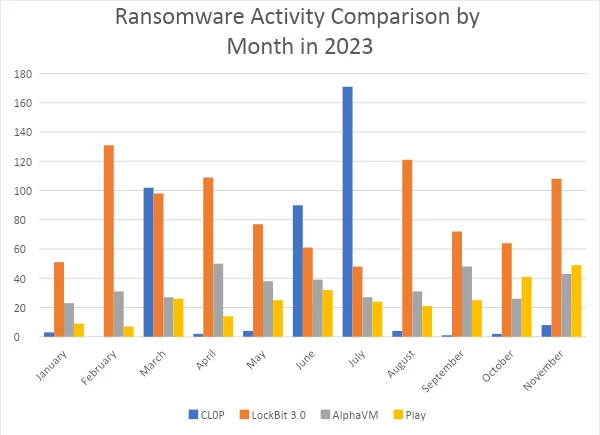
The chart provides a visual representation of the monthly attack frequency for the ransomware groups CL0P, LockBit 3.0, AlphaVM, and Play throughout 2023.
The data showcased in the accompanying graph paints a compelling narrative of the ransomware threat landscape. CL0P’s activities, in particular, exhibit a strikingly erratic pattern, with peaks and troughs that defy the more uniform trends of its counterparts. This irregularity may suggest strategic planning behind CL0P’s operations, possibly indicating a focus on larger, more lucrative targets, or periods of dormancy for development.
In contrast, other groups like LockBit 3.0 and AlphaVM maintain a steadier cadence of attacks, hinting at a different operational approach, perhaps one that is less selective and more opportunistic. This consistent level of threat underscores the persistent nature of the ransomware problem and the need for continuous vigilance in the cybersecurity community.
Strategic Posturing: CL0P’s Approach to Ransomware Announcements
Ransomware groups often utilize public announcements as part of their strategy to pressure victims into meeting their demands. However, the frequency and nature of these announcements can vary greatly between groups, reflecting their individual tactics and intentions.
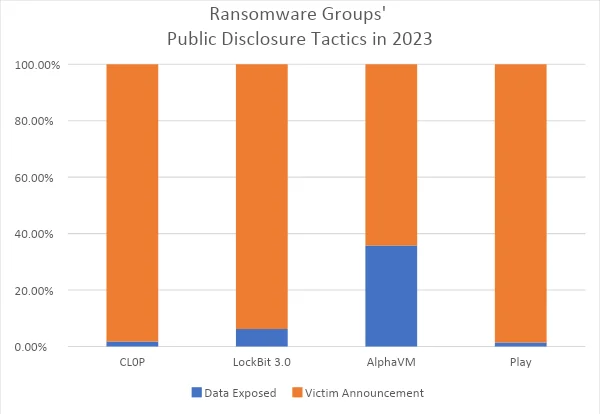
This chart compares the percentage of data exposure events versus victim announcements made by ransomware groups CL0P, LockBit 3.0, AlphaVM, and Play throughout 2023. It normalizes the intent behind their public shares relative to their total number of attacks, showcasing strategic differences in their operational styles.
In 2023, the CL0P ransomware group demonstrated a significant propensity for announcing their victims rather than exposing data, with a staggering 98.19% of their communications dedicated to victim announcements. This starkly contrasts with AlphaVM, which has a more balanced approach, with 35.77% of their shares revealing exposed data.
The data suggests that CL0P favors a strategy that could be interpreted as ‘psychological warfare,’ relying heavily on the threat of exposure to coerce victims into complying with their demands. This approach minimizes actual data leakage, potentially indicating a preference for maintaining leverage over victims.
On the other hand, groups like AlphaVM seem to employ a more aggressive tactic of data exposure, possibly to underscore the consequences of non-compliance. LockBit 3.0 and Play, similar to CL0P, also show a greater inclination towards victim announcements, suggesting that the threat of exposure remains a preferred method of intimidation among these ransomware groups.
Geographic Focus: The Predominant Targeting of US Organizations by CL0P
Geographic targeting in cyber attacks reveals much about the objectives and strategic preferences of ransomware groups. In 2023, a clear pattern emerged that highlights how often these groups target organizations within the United States.
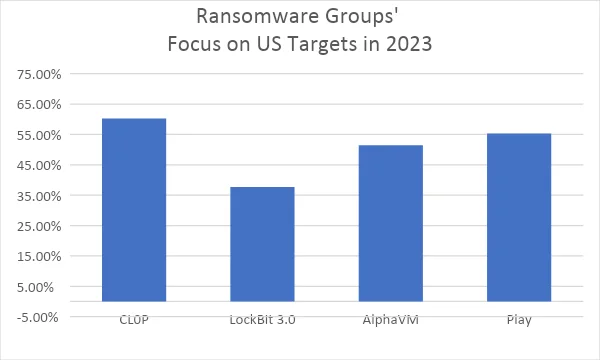
The graph illustrates the proportion of each ransomware group’s attacks that were directed at U.S. organizations in 2023, normalized by their total number of incidents.
In this year’s cyber threat arena, CL0P has significantly focused its efforts on American targets, with over 60% of its actions aimed at U.S. organizations. This emphasis underscores the group’s strategic decision to concentrate on what is arguably the world’s most lucrative cyber market.
Comparatively, LockBit 3.0 shows a more moderate inclination towards U.S. targets, while AlphaVM and Play demonstrate a similar pattern of engagement, with just over half of their attacks affecting U.S. entities. These statistics not only reflect each group’s tactical choices but also indicate the high value they place on U.S. targets, known for their potential for higher ransom payouts and valuable data.
The distinct approach of CL0P in focusing predominantly on U.S. organizations suggests a deliberate targeting strategy, potentially reflecting a calculated assessment of risk versus reward in the choice of victims. Understanding these geographic trends is crucial for U.S. entities to anticipate potential threats and strengthen their defenses accordingly.
Industry-Specific Targeting: A Comparative Analysis of Ransomware Focus in 2023
The selection of industries targeted by ransomware groups often provides key insights into their strategic motivations and preferred attack vectors. In 2023, distinct patterns emerged that highlight each group’s targeting preferences across different sectors.
Predominant Industry Targets of Ransomware Groups in 2023
| CL0P | LockBit 3.0 | ||
| Information and Telecom Tech | 19.90% | Manufacturing | 21.28% |
| Finance and Insurance | 19.64% | Professional, Scientific, and Technical Services | 13.51% |
| Manufacturing | 14.21% | Public Administration | 7.98% |
| AlphaVM | Play | ||
| Manufacturing | 19.84% | Manufacturing | 18.32% |
| Professional, Scientific, and Technical Services | 15.67% | Professional, Scientific, and Technical Services | 14.29% |
| Information and Telecom Tech | 9.40% | Information and Telecom Tech | 12.45% |
The table ranks the top three industries targeted by the ransomware groups CL0P, LockBit 3.0, AlphaVM, and Play in 2023, showing the percentage of each group’s total attacks that these industries represent.
When examining the industries under siege, CL0P’s focus is notably diversified, with Information and Telecom Technologies, and Finance and Insurance industries being almost equally targeted, reflecting the group’s recognition of the high value and impact of disrupting these vital sectors. The group’s attention to the Manufacturing sector is also significant, though less pronounced.
LockBit 3.0, on the other hand, shows a strong preference for Manufacturing, while also extending its operations into Professional, Scientific, and Technical Services, and less so into Public Administration. This indicates a strategic exploitation of industrial control systems and intellectual property, which are prevalent in these sectors.
AlphaVM and Play display a similar pattern, both favoring manufacturing, which is indicative of a trend where the disruption of production lines and supply chains presents a lucrative opportunity for ransom demands. However, AlphaVM shows a stronger engagement with Professional, Scientific, and Technical Services compared to Play, which may suggest different operational capabilities or access within this field.
Strategic Patterns and Impact: CL0P’s Ransomware Operations in 2023
Drawing upon the comprehensive data from SOCRadar’s extensive monitoring and the subsequent analysis of the ransomware landscape throughout 2023, several key conclusions about the CL0P ransomware group can be distilled:
- Operational Unpredictability: The monthly distribution of CL0P’s attacks shows a high level of unpredictability. Notably, there were significant spikes that corresponded with the exploitation of 0-day vulnerabilities in GoAnywhere and MOVEit, indicating a strategic approach to leveraging critical vulnerabilities at opportune moments.
- Strategic Communication: CL0P’s communication strategy is primarily focused on victim announcements rather than data exposure. This suggests a psychological tactic, possibly to maintain leverage by threatening data release while minimizing the risks associated with actual data leaks.
- Geographic Preference: CL0P has a distinct preference for targeting U.S. organizations, with over 60% of its activities aimed at American entities. This could be indicative of the group’s assessment of the U.S. as a high-value target with the potential for substantial ransoms.
- Industry-Specific Targeting: CL0P has shown a nearly equal focus on the Information and Telecom Tech and Finance and Insurance industries, sectors known for their critical infrastructure and sensitive data. This approach may reflect the group’s interest in causing impactful disruptions and accessing high-value information.
- Sophisticated Exploitation: The utilization of 0-day vulnerabilities reveals CL0P’s sophisticated capabilities in identifying and exploiting the most critical and less-anticipated security gaps within target organizations.
- Comparative Modus Operandi: When compared to other ransomware groups such as LockBit 3.0, AlphaVM, and Play, CL0P’s approach is less about the volume of attacks and more about precision and impact. This is in contrast to the more consistent attack patterns and broader targeting strategies observed in other groups.
- Adaptation and Evolution: The adaptability of CL0P to exploit emergent vulnerabilities and to adjust its targeting strategy suggests a highly dynamic nature, capable of evolving its tactics to meet its objectives effectively.
In light of these findings, it becomes imperative for organizations, especially in the U.S. and within CL0P’s preferred industries, to prioritize cybersecurity. This includes staying abreast of emerging vulnerabilities, enhancing detection capabilities, and developing robust incident response strategies. A tailored approach to defense, informed by threat intelligence such as that provided by SOCRadar, is essential to counter the sophisticated and evolving threats posed by ransomware groups like CL0P.

Threat Actor Card of Cl0p Ransomware
Harnessing SOCRadar’s Intelligence to Fortify Against Ransomware
As we reflect on the patterns and tactics of the CL0P ransomware group, it’s clear that their operations are both sophisticated and menacingly targeted. SOCRadar’s in-depth analysis throughout 2023 has provided crucial insights into CL0P’s attack vectors, preferred industries, and geographical focuses, alongside their strategic exploitation of 0-day vulnerabilities.
SOCRadar Cyber Intelligence offers a comprehensive suite of tools and services designed to equip organizations with the necessary foresight and intelligence. With Extended Threat Intelligence (XTI), SOCRadar enhances the visibility of an organization’s attack surface, delivering early warnings and actionable insights to pre-empt cyber attacks. The integration of External Attack Surface Management, Digital Risk Protection, and Cyber Threat Intelligence into a unified platform ensures that SOCRadar’s clients are not just reactive but proactive in their cybersecurity measures.
By understanding the threat actors’ communication strategies and the potential implications of their victim announcements, SOCRadar provides a unique advantage. Our platform’s capabilities in crawling and analyzing the dark web and other communication channels of these groups translate into tailored defense strategies, enabling clients to stay one step ahead.
The geographic and industry-specific intelligence gathered by SOCRadar is not merely data—it’s a strategic asset that empowers C-level executives and SOC teams to prioritize defenses and allocate resources effectively, ensuring that the organization’s cybersecurity posture is robust and resilient.




































