
Dark Web Profile: Play Ransomware
[Update] July 22, 2024: “Play Ransomware Broadens Its Scope with New Linux Variant Targeting ESXi”
[Update] December 19, 2023: “Collaborative Advisory on Play Ransomware: 300 Entities Affected by October 2023.”
[Update] November 22, 2023: “Play Ransomware Shifts to RaaS Model.”
[Update] July 7, 2023: “Play Ransomware Lists 11 New Victims from Distinct Industries.”
While cyber-attacks are increasing nowadays, threat actors seek to implement different methods and techniques as well. Ransomware is one of the most common cyber-attacks that are not new but developing a cybercrime industry that threatens several sectors and governments. Today, we’ll introduce you to a new player: Play Ransomware.
Who is Play Ransomware?
On Jun 22, 2022, in the BleepingComputer forum, someone wrote that his files were encrypted with the extension “Play.” Afterward, Trend Micro published an analysis article about the new ransomware variant, Play Ransomware. The main target of Play Ransomware is the Latin American region, and Brazil is at the top of the list. Even though they seem like a new ransomware group, their identified TTPs look like Hive and Nokayawa ransomware families. One of the similar behaviors that make them look similar are they use AdFind, a command-line query tool capable of collecting information from Active Directory.
How Do They Attack?
The Play Ransomware group uses a known valid account, exposed RDP servers, and FortiOS vulnerabilities CVE-2018-13379 and CVE-2020-12812 to gain initial access to an organization’s network. After getting access, they start using “lolbins” binaries like common ransomware group use as part of their attacks.
They distribute executables in the internal network via Group Policy Objects, then run scheduled tasks, PsExec or wmic. After they gain full access to the internal network, they encrypt files with the “.play” extension.
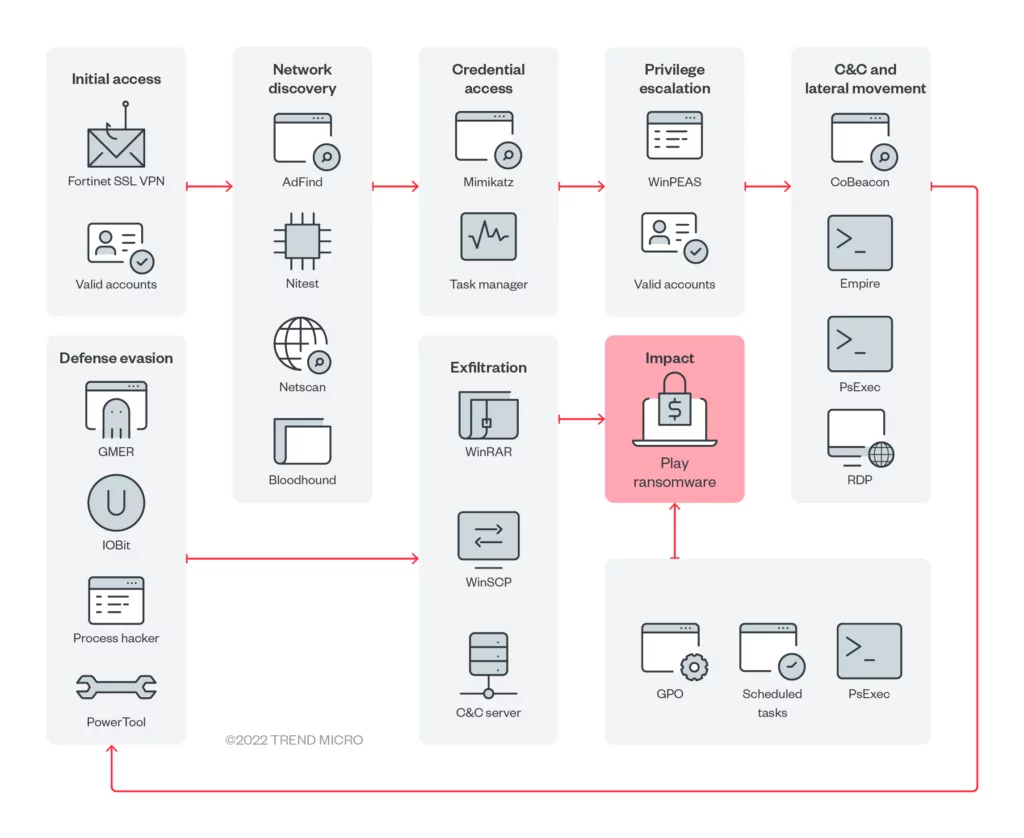
Double extortion is a popular technique in which cyber actors threaten to exfiltrate sensitive data. Play Ransomware also uses double extortion against its victims. They can archive the breached data with WinRAR and then upload it to file-sharing sites.
Unique Type of Method: Intermittent Encryption
The researchers have found that the Play Ransomware group is the first threat actor resorting to intermittent encryption. This technique provides better evasion with partial encryption on the system that uses static analysis to detect ransomware infection.
Intermittent encryption is a new technique; based on the file size, it encrypts chunks of 0x100000 bytes.
For example:
- 2 chunks if the file size is less than or equal to 0x3fffffff bytes;
- 3 chunks if the file size is less than or equal to 0x27fffffff bytes;
The researchers observed that a sample encrypted every other 0x100000 byte chunk until the end of the file. The file consisted only of null characters, making the encrypted and non-encrypted chunks visually distinguishable.

Play Ransomware Hacks Xplain: Swiss Police, Army, and Customs are Affected
Swiss authorities are investigating a cyber attack that targeted a Bernese IT firm, Xplain. The attack impacted several federal and cantonal government departments that worked with the same IT company, including the cantonal police, the Swiss army, customs, and the Federal Office of Police (Fedpol).
The Play Ransomware gang has claimed responsibility for the attack and published the stolen data from Fedpol and the Federal Office for Customs and Border Security (FOCBS) on a dark web forum.
Affected parties Fedpol and FOCBS downplayed the incident, Fedpol stating that only simulated and anonymous test data was accessed. However, the FOCBS acknowledged that exposed data included correspondence with clients.
Play Ransomware Targets IT Companies
Play Ransomware has recently added more companies to its leak site, claiming to have hacked them. After Xplain’s hack, these companies included other IT providers named Paragon Software Lanka, Soroc Technology, and a cloud hosting provider, Black Cat Networks.
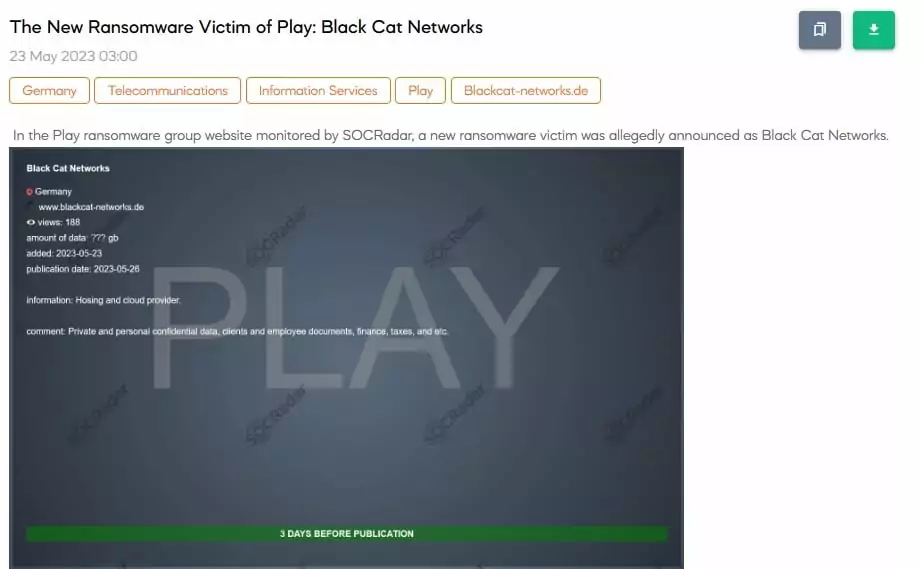
Although the ransomware group did not disclose the size of data stolen from these organizations, they explained on leak posts that they stole private and confidential data, client and employee documents, as well as certain financial information from all the victims.
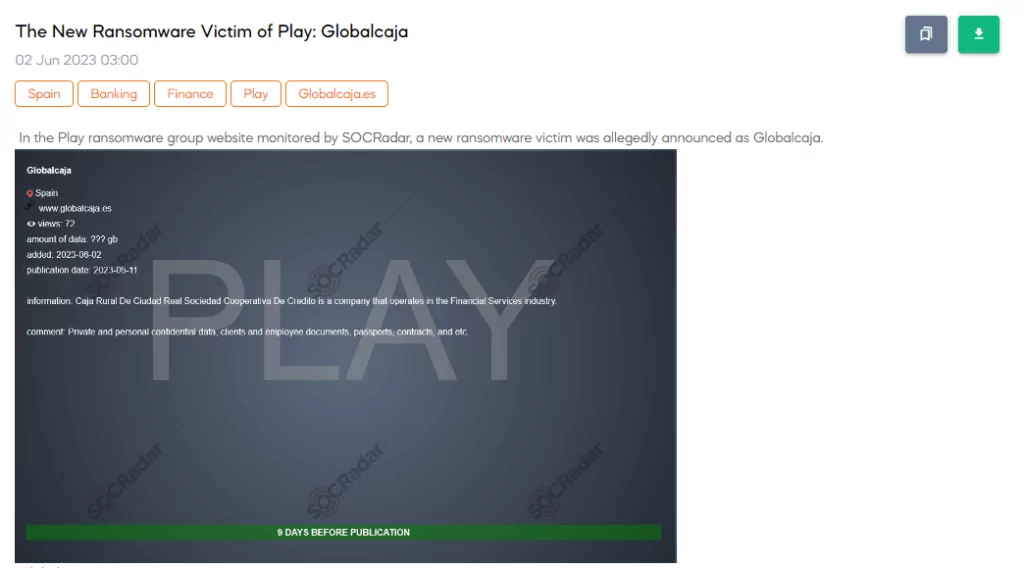
Major Spanish Bank Globalcaja Hit by Play Ransomware Attack
A major Spanish bank called Globalcaja has confirmed that it is facing a ransomware attack affecting multiple offices. The bank, located in Albacete, Spain, has over 300 branches nationwide and serves nearly 500,000 customers.
The Play ransomware group has claimed responsibility for the attack, stating that they have stolen private and confidential data, including client and employee documents, passports, and contracts.
The bank has stated that the attack has not affected customer transactions or electronic banking operations. They have activated security protocols, limited the performance of some operations, and are working to normalize the situation while prioritizing security. The bank has not commented on whether they will pay a ransom.
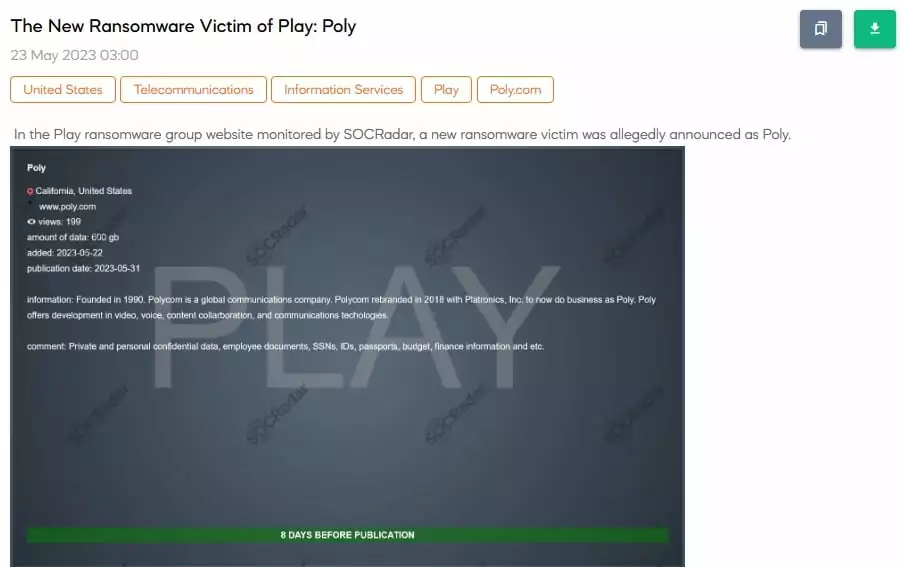
Play Ransomware Claims They Stole 600GB Data from Polycom
Another notable entry on the list is Poly (Polycom), a global communications firm based in the US. The ransomware operation posted Poly on the leak site on May 22, 2023, and claimed that they obtained 600GB of data, which included private and personal information, employee documents, social security numbers, IDs, passports, budget details, and financial information.
Play Ransomware Attack Target: Argentina’s Judiciary of Córdoba

On Aug 13, 2022, Argentina’s Judiciary of Córdoba was targeted by Play Ransomware Group. They shut down Argentina’s Judiciary of Córdoba’s IT systems, databases, and online portals. Then they encrypted their files with “.play” extensions. After that, they left a simple ReadMe.txt to contact them.
Play Ransomware Lists 11 New Victims from Distinct Industries
The Play ransomware group recently came up with an alarming update on their Dark Web leak site: they added 11 new victims to the list. The victim organizations operate in diverse industries, and while nine originate from the United States, the remaining two are from the United Kingdom and Italy.
The list includes the manufacturer Indiana Dimension, Star Island Resort and Club, towing firm Lazer Tow, traffic control company Safety Network, logistics firm Capacity LLC, retailers Betty Lou’s Inc and MUJI UK, Geneva Software, hardware manufacturer Uniquify Inc, NST Law firm in the legal field, and Lawer SpA operating in the industrial sector.
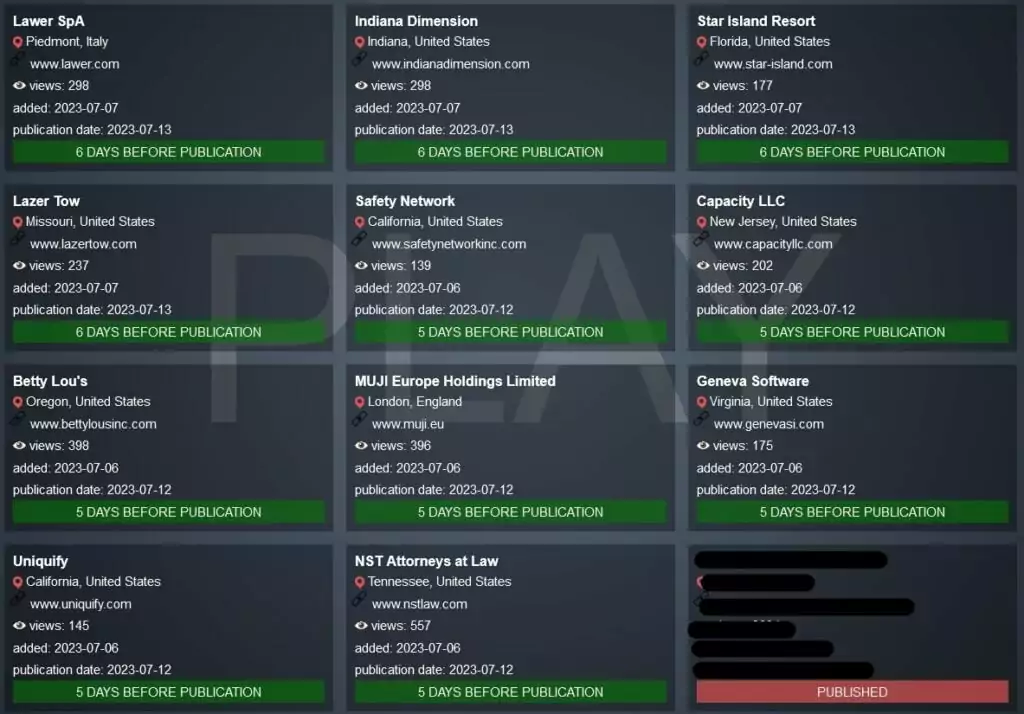
The Play ransomware group claims to have successfully hacked the systems of these organizations and threatens to expose their private and personal data if the ransom demand is not paid, including sensitive client and employee documents, contracts, as well as financial, HR, and passport information in certain cases.
Play Ransomware Shifts to RaaS Model
Researchers have uncovered a significant development, as Play Ransomware transitions to a Ransomware-as-a-Service (RaaS) model. A recent in-depth analysis, based on various Play ransomware attacks, reveals a striking uniformity in tactics and procedures across different sectors, indicating the use of predefined playbooks or instructions, possibly supplied by a RaaS kit.
In recent months, researchers have seen Play attacks with nearly identical TTPs, such as the use of the public music folder (C:…publicmusic) to hide the malicious file, the same password to create high-privilege accounts, and the same commands.
The victims who were targeted all had a similar profile. The targeting of smaller organizations with a financial capacity for ransom payments of around $1 million is particularly concerning.
For a detailed list of Indicators of Compromise, refer to the full research.
How Could This Revelation Impact the Cybersecurity Landscape?
Play Ransomware was distinct from other operations with the involvement of its developers in executing attacks. Play’s transformation into a RaaS marks a notable shift as developers are now separated from attackers, while Play also becomes an enticing option for other threat actors. Consequently, the cybersecurity landscape must anticipate a surge in incidents and strengthen defenses accordingly.
Collaborative Advisory on Play Ransomware: 300 Entities Affected by October 2023
CISA, FBI, and ASD’s ACSC have issued a collaborative advisory, #StopRansomware: Play Ransomware, to share indicators of compromise, detection methods, and TTPs used by Play ransomware with the public.
Since June 2022, the Play ransomware group, also known as Playcrypt, has impacted a diverse range of businesses and critical infrastructure across North America, South America, and Europe.
The CSA underscores that this ransomware group operates as a closed entity, aiming to ensure the confidentiality of its transactions. Unlike typical ransomware groups, instead of presenting an initial ransom demand or payment instructions, Play’s ransom notes instruct victims to reach out to the threat actors via email.
Most importantly, as of October 2023, the FBI is aware of approximately 300 entities that were exploited by the Play ransomware actors, showcasing their widespread impact.
The advisory further provides a list of tools and commands utilized by the threat actor, details characteristics, and methods employed for encryption and extortion. In addition to IoCs and TTPs, the advisory includes an extensive list of mitigation strategies.
Explore the joint cybersecurity advisory here.
Play Ransomware Broadens Its Scope with New Linux Variant Targeting ESXi
A new variant of Play Ransomware has emerged, targeting VMware ESXi virtual machines. According to researchers, this is the first time Play Ransomware has targeted ESXi environments, marking a notable shift in their attack strategy to include the Linux platform.
Researchers at Trend Micro discovered this development, noting that the new variant can verify if it is executing on an ESXi environment and avoid detection on Linux systems. After successful deployment, the Linux variant scans the affected environment, shuts down all virtual machines, and encrypts files such as VM disks, configuration, and metadata.
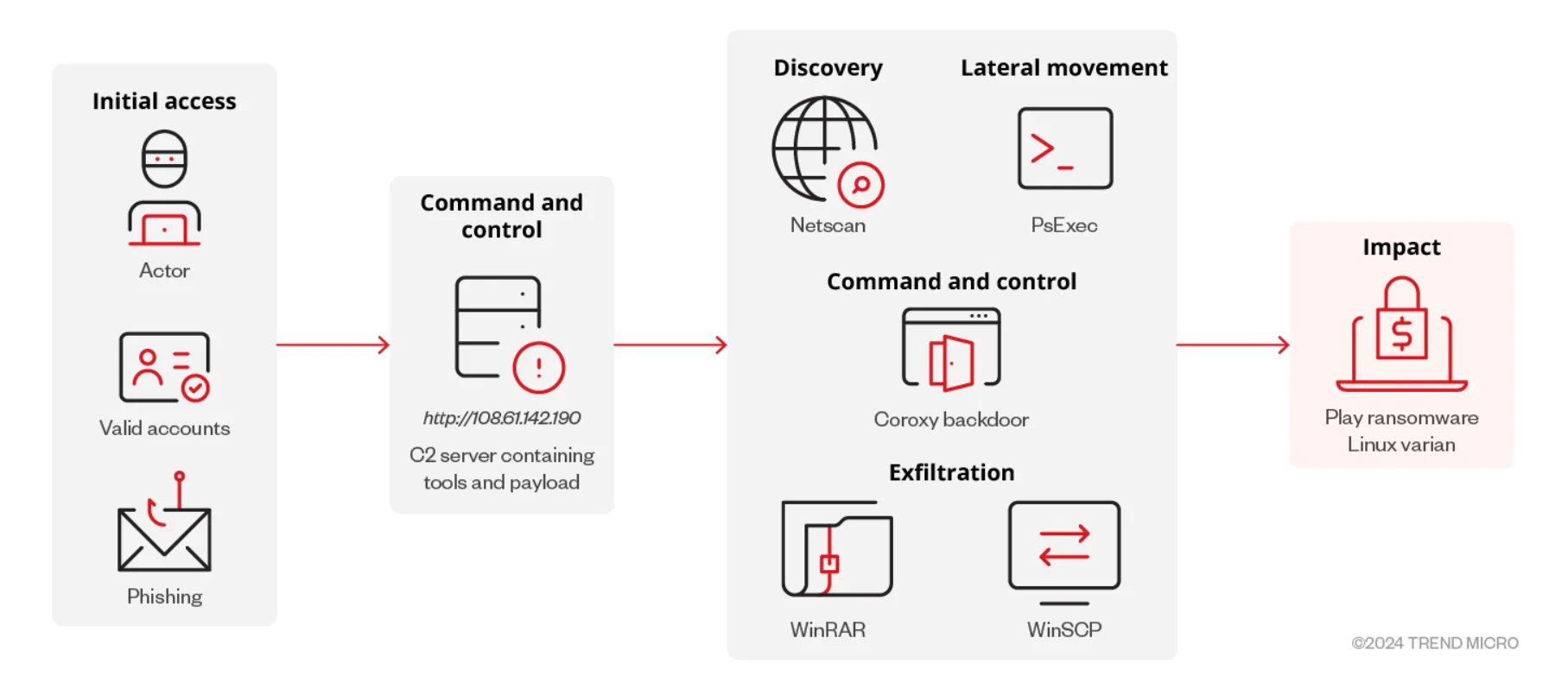
The full infection chain of Play Ransomware’s Linux variant (Trend Micro)
Encrypted files are appended with a ‘.PLAY’ extension, and a ransom note is left in the root directory of the VM, which appears in the ESXi client’s login portal and on the console post-reboot.
Among their findings, researchers have also noted that Play Ransomware uses URL-shortening services from a threat actor known as “Prolific Puma.” This threat actor, or group, is known to be active since at least January 2020.
What are the Security Recommendations?
Play Ransomware attacks emphasize the evolution of cyber threats. Recently, threat actors implement advanced evasion techniques to avoid detection by security tools. Therefore, you should deploy more security components like CTI platforms to get in intelligence about new threats from the dark web and learn about a specific threat against your company. Additionally, some curated mitigation steps are below.
- Employ MFA (multifactor authentication) for all possible services to prevent attackers’ lateral movements.
- Apply the least privilege principle, especially to critical systems and services.
- Enable logical and physical network segmentation for separation of different units’ accesses.
- Deploy attack surface management (ASM), assisting in understanding cyber assets.
- Secure domain controllers (DC) using best practices.
- Maintain offline and encrypted backups of data, especially the 3-2-1 backup rule for essential files.
- Track security patches and software/OS updates regularly.
Stay Informed with SOCRadar’s Dark Web News
Stay up to date with the latest happenings in the dark web, including the notorious Play Ransomware, through the comprehensive Dark Web News module offered by SOCRadar.
Dive into a wealth of information and stay informed about the latest updates, including Play Ransomware.
IOCs
Hashes
- fc2b98c4f03a246f6564cc778c03f1f9057510efb578ed3e9d8e8b0e5516bd49
- c316627897a78558356662a6c64621ae25c3c3893f4b363a4b3f27086246038d
- c92c158d7c37fea795114fa6491fe5f145ad2f8c08776b18ae79db811e8e36a3
- e1c75f863749a522b244bfa09fb694b0cc2ae0048b4ab72cb74fcf73d971777b
- 094d1476331d6f693f1d546b53f1c1a42863e6cde014e2ed655f3cbe63e5ecde
- e8a3e804a96c716a3e9b69195db6ffb0d33e2433af871e4d4e1eab3097237173
- d4a0fe56316a2c45b9ba9ac1005363309a3edc7acf9e4df64d326a0ff273e80f
- c88b284bac8cd639861c6f364808fac2594f0069208e756d2f66f943a23e3022
- f18bc899bcacd28aaa016d220ea8df4db540795e588f8887fe8ee9b697ef819f
- e641b622b1f180fe189e3f39b3466b16ca5040b5a1869e5d30c92cca5727d3f0
- 608e2b023dc8f7e02ae2000fc7dbfc24e47807d1e4264cbd6bb5839c81f91934
- 006ae41910887f0811a3ba2868ef9576bbd265216554850112319af878f06e55
- e4f32fe39ce7f9f293ccbfde30adfdc36caf7cfb6ccc396870527f45534b840b
- 8962de34e5d63228d5ab037c87262e5b13bb9c17e73e5db7d6be4212d66f1c22
- 5573cbe13c0dbfd3d0e467b9907f3a89c1c133c774ada906ea256e228ae885d5
- f6072ff57c1cfe74b88f521d70c524bcbbb60c561705e9febe033f51131be408
- 7d14b98cdc1b898bd0d9be80398fc59ab560e8c44e0a9dedac8ad4ece3d450b0
- dcaf62ee4637397b2aaa73dbe41cfb514c71565f1d4770944c9b678cd2545087
- f5c2391dbd7ebb28d36d7089ef04f1bd9d366a31e3902abed1755708207498c0
- 14177730443c70aefeeda3162b324fdedf9cf9e0
- 3e6317229d122073f57264d6f69ae3e145decad3666ddad8173c942e80588e69
URLs
- hxxp://84.32.190[.]37:80/ahgffxvbghgfv
- hxxp://newspraize[.]com
- hxxp://realmacnow[.]com
- 172.67.176[.]244
- 104.21.43[.]80
- hxxp://67.205.182[.]129/u2/upload[.]php





































