
Counter-Ransomware Initiative: A United Front Against Ransomware
[Update] November 9, 2023: Boeing was once again leaked on the victim site of the LockBit***
[Update] November 3, 2023: LockBit lists Boeing again, leaks data, and once again removes it from the list**
[Update] November 2, 2023: Boeing has acknowledged that they experienced an incident*
The surge in ransomware attacks has become a global concern, prompting world leaders and institutions to take a united stand. In 2021, the Biden administration established a yearly global summit aimed at tackling cybersecurity concerns, initially assembling a group of 31 countries that now expanded to more than 45 members. A significant development this year was the counter-ransomware initiative, where world leaders and the White House have made a collective decision to refuse ransomware payouts. This move is seen as a bold step towards discouraging cybercriminals and reducing the profitability of such attacks. Still, we will see over time whether it will happen, whether the promises will be kept, and whether the agreed strategies will work.
Ransomware Negotiation
Of course, there is a question that comes to mind after this development; although paying ransomware is never recommended, what should be done if data is needed?
For the sake of this question, let’s discuss a very recent incident. The LockBit ransomware group, which had previously claimed responsibility for a cyberattack on Boeing on October 27, unexpectedly removed Boeing’s name from its victim list just three days after the claim.
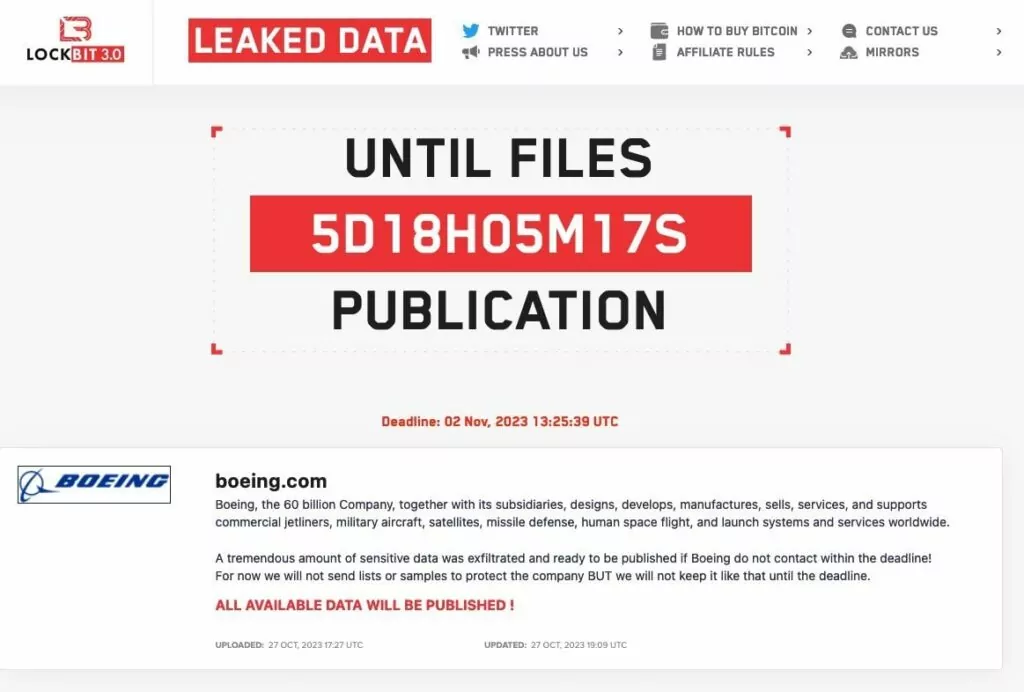
This sudden removal has raised questions regarding the authenticity of the initial attack claims. While some speculate that Boeing might have successfully negotiated a ransom with the group, the aerospace company has not confirmed any such cyberattack. Both the FBI and the Cybersecurity and Infrastructure Security Agency (CISA) have remained silent on the matter, adding to the uncertainty surrounding the alleged attack. The lack of official statements and verification has led to doubts about the legitimacy of the purported attack.
*Boeing has made a statement acknowledging that they experienced an incident; as of today, no further comment has been made. Another claim is that in a tweet by vx-underground, LockBit removed the listing because the negotiation process had started.
**As of today, on November 3, LockBit listed Boeing again, leaked a portion of the alleged data and said that more would follow in the coming days, but later removed Boeing from the list again.
***Most recent development, Boeing was once again leaked on the victim site of the LockBit, allegedly “negotiations” failed.
When we look at other incidents, before contacting cybercriminals, victims typically explore legitimate avenues to recover their data. Often, the reluctance to approach these gangs isn’t just due to legal issues but also the hefty ransoms involved. Thus, our recent article discusses that a reputed data recovery firm might have collaborated with North Korean hackers during the data recovery process. In this context, things can get very confusing.
However, as Verizon’s DBIR report points out, paying off the ransom is often the more costly option.
The Counter-Ransomware Initiative Introduces the Blacklist Strategy
The White House, in collaboration with partner countries, has taken the counter-ransomware initiative a step further by introducing a series of measures to combat the ransomware menace. One notable measure is the sharing of a “blacklist” through the US Department of the Treasury. This list contains information on cryptocurrency wallets that are known to be involved in transferring ransoms. The idea behind this is to track and potentially block transactions from these flagged wallets, thereby crippling the financial backbone of ransomware operations.
A question arises again: Is tracking and blocking cryptocurrency wallets a viable solution? Cryptocurrencies, by their very nature, offer a degree of anonymity and flexibility. Wallet addresses can be changed, and transactions can be masked, especially with privacy-centric cryptocurrencies like Monero. Moreover, a representative from Europol’s Cybercrime Unit, Jerej Jakubcek, stated in a webinar that they cannot trace Monero (XMR) transactions. Speaking as a guest of the Blockchain Alliance in a webinar, Jakubcek admitted that when TOR and Monero are used together, investigations often hit a dead end, and they are unable to track the criminals.
This raises concerns about the effectiveness of the blacklist approach, as cybercriminals could potentially switch to more private cryptocurrencies or frequently change their wallet addresses to evade detection.
So, What is The Solution?
While the initiative to blacklist suspicious wallets is commendable, it is essential to understand that the world of cyber crime is vast and ever-evolving. Relying solely on specific methods might not be sufficient. A multi-pronged approach involving technological advancements, international cooperation, public awareness campaigns and intelligence would be more effective in the fight against cyber crime. Of course, this summit creates a suitable environment for these.
In conclusion, the global counter-ransomware initiative is a significant step in the right direction. However, the dynamic nature of cyber crime and the adaptability of cybercriminals necessitate continuous evolution in strategies and methods. Only through collective effort, innovation and proactive approach can we hope to curb the ransomware threat effectively. Of course, the most important thing is to take the necessary precautions before falling into a dire situation such as ransomware negotiation.
SOCRadar continuously monitors your perimeter from an external perspective to spot critical internet-facing vulnerabilities to be exploited. You can ensure your security by tracking ransomware groups and the vulnerabilities they exploit with our Ransomware Check feature within Attack Surface Management.




































