
Ransomware Chronicles: Unveiling the Monthly Trends in 2023
Welcome to our “Ransomware Trends in 2023: A Live Blog of Insights and Analysis.” This live blog delves into the intricate world of ransomware, providing timely updates and valuable statistics on the prevailing trends shaping the threat landscape. As ransomware continues to wreak havoc on individuals and industries alike, it is imperative to remain vigilant and well-informed.
Our meticulous examination of ransomware attack counts, breached data, paid ransoms, victim counts, and targeted industries aims to shed light on cybercriminals’ evolving tactics and strategies. Join us as we navigate the intricate maze of ransomware in 2023, equipping you with the knowledge to fortify your defenses and protect against these ever-evolving threats.
Ransomware Statistics Since the Beginning of 2023
In 2023, ransomware attacks have reached new heights, surpassing the intensity observed in previous years. According to SOCRadar, over 1500 ransomware attacks have been recorded since the beginning of the year. While these attacks are spread across various countries, it is notable that a significant portion of them targets companies in the United States. Additionally, countries such as the United Kingdom, Canada, Germany, and France also witness a substantial number of attacks, indicating that ransomware threats predominantly affect Western and NATO-affiliated nations.
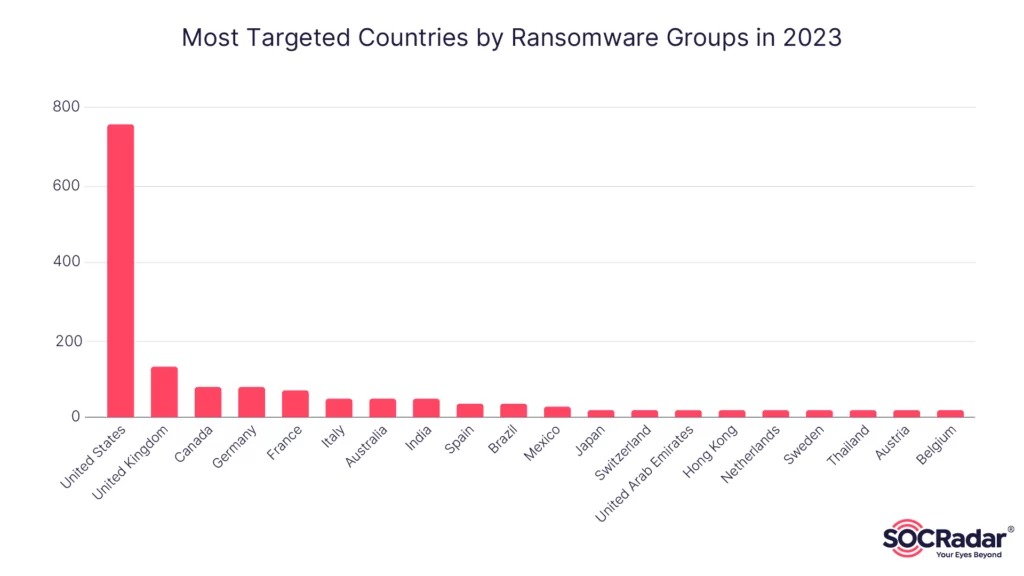
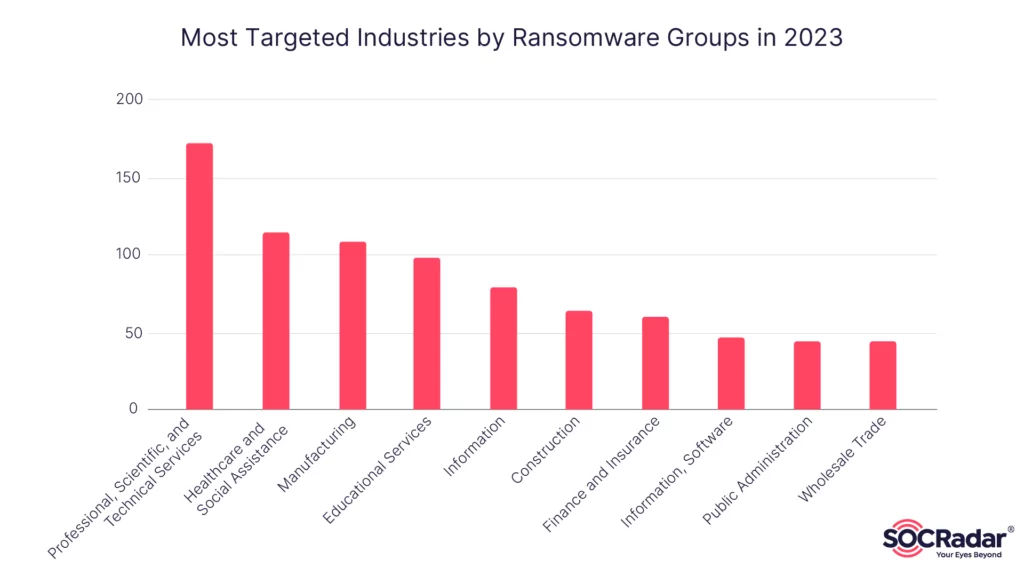
When considering the industries targeted by ransomware attacks, the Professional, Scientific, and Technical Services industry takes the lead, followed closely by Healthcare, Manufacturing, Educational services, and the Information industry. It may be surprising to see sectors like Healthcare and Education being heavily targeted, but this trend has steadily increased since 2022. These industries often possess valuable data and have sometimes been found to have vulnerabilities that make them attractive targets for cybercriminals.
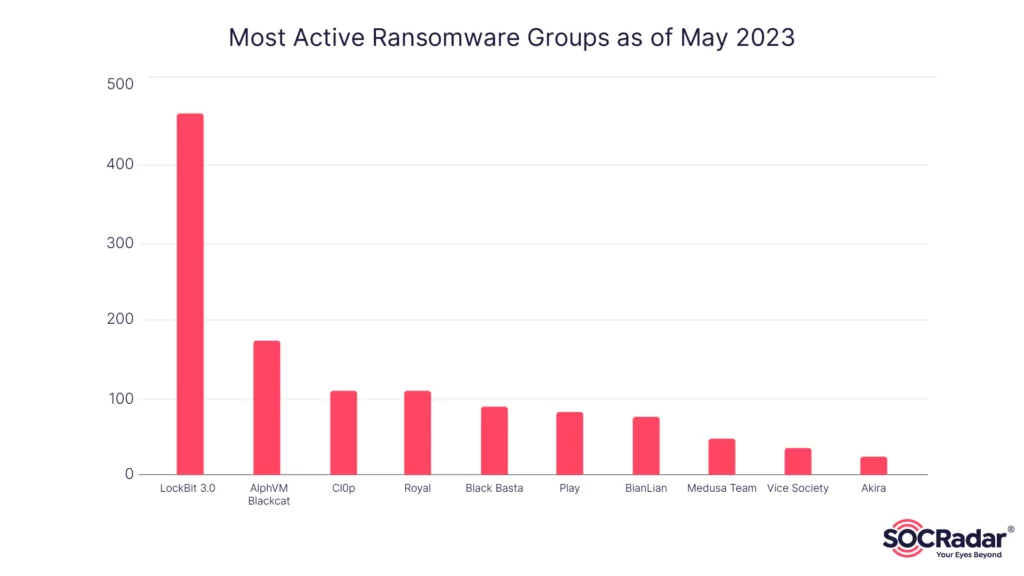
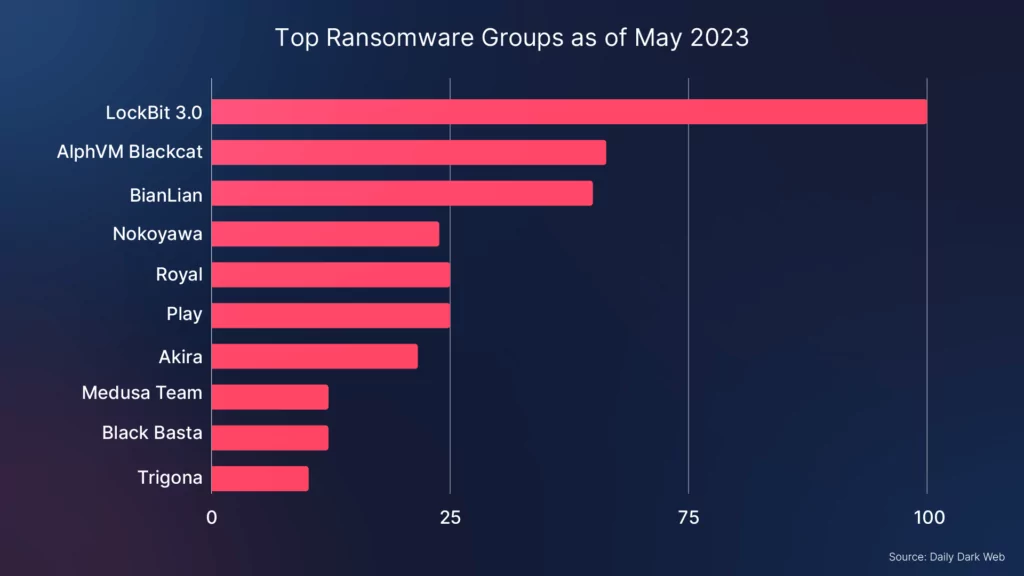
Among the ransomware groups responsible for the highest number of victims so far in 2023, the LockBit 3.0 RaaS (Ransomware-as-a-Service) group continues to prevail. LockBit has maintained its position as the most active ransomware group since the second half of 2022, consistently causing significant damage and financial losses for organizations worldwide.
Monthly Update: May 2023
May 2023 marked a significant turning point in the ransomware landscape, standing out as the month with the highest number of attacks recorded since the beginning of the year. Moreover, compared to previous years, May 2023 holds the unfortunate distinction of being the month with the highest number of ransomware attacks to date. These statistics reflect ransomware’s intensifying threat to organizations and individuals.
While the United States remains the primary target for ransomware attacks, May 2023 witnessed a notable shift in targeting preferences within specific sectors. Information-related industries, including data-centric organizations, digital service providers, and technology companies, experienced a surge in ransomware attacks. This sectoral pivot demonstrates cybercriminals’ evolving tactics, as they aim to exploit vulnerabilities and capitalize on the valuable digital assets held by information-driven entities.
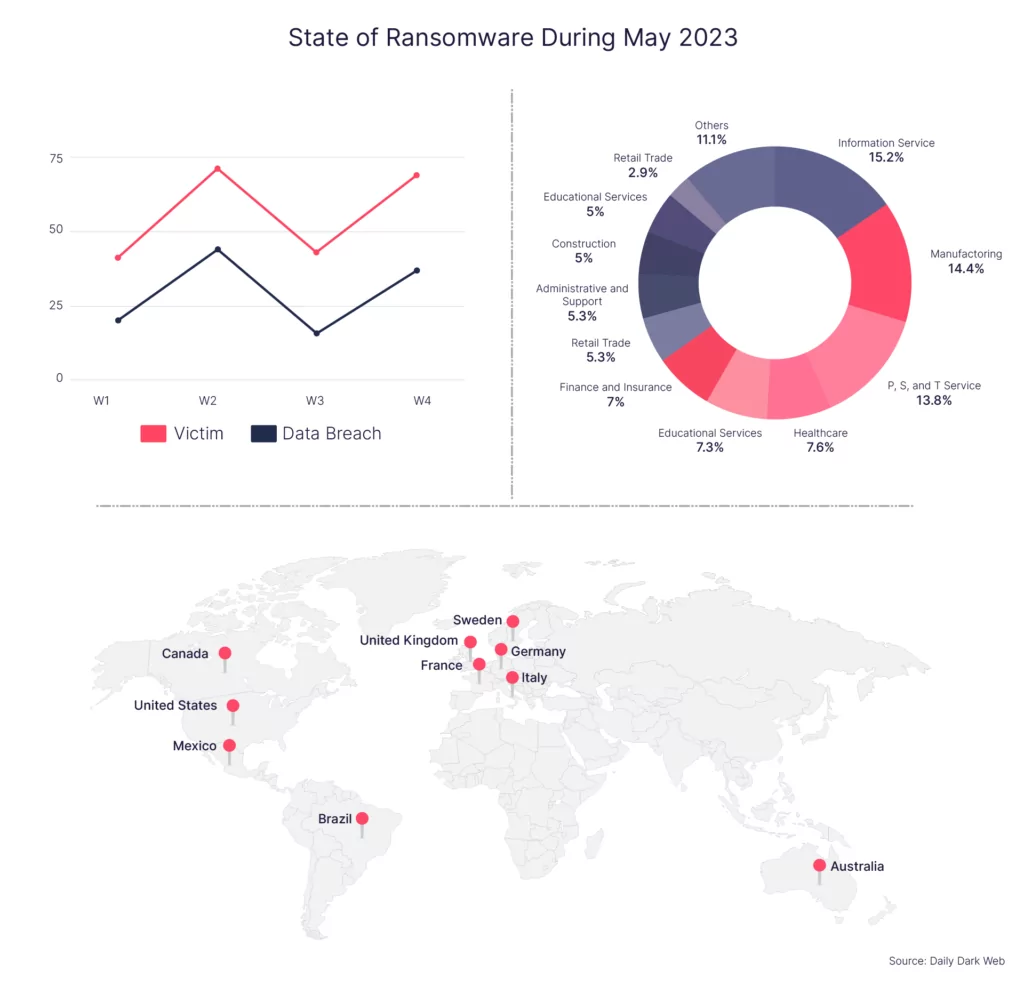
Within this challenging landscape, the LockBit 3.0 ransomware group continues to wreak havoc, maintaining its position as the most active and prolific ransomware group. LockBit 3.0 garnered widespread attention through victim announcements, demonstrating their unwavering determination to extort organizations for financial gain. This group’s relentless activities further emphasize the urgent need for heightened cybersecurity measures and collaborative efforts to combat ransomware threats effectively.
Trends and Patterns
Ransomware, a costly and adaptive threat, continues transforming alongside technological advancements. To grasp the evolving ransomware landscape in 2023, it’s crucial to identify key trends and patterns that shape its tactics. Reflecting on the trends of 2022 and looking ahead to 2023, here are six notable evolutions and three predicted trends by security researchers that shed light on the ever-changing nature of ransomware attacks.
Shifting Focus to Data Extortion: Ransomware groups have discovered success in extorting victims by posting stolen data online when their demands are not met. This tactic puts additional pressure on organizations to comply, as the potential exposure of sensitive information can lead to reputational damage and legal consequences.
Exploiting Data Monetization Opportunities: Stolen data is valuable to its rightful owners and to cyber criminals who can sell it to other malicious actors, creating an underground market. The rise of cryptocurrencies facilitates anonymous transactions, making it easier for ransomware groups to profit from their illicit activities.
Targeting Cloud Environment: With the growing adoption of cloud technology, ransomware groups are exploiting vulnerabilities in cloud resources. They use compromised instances for activities for launching ransomware attacks. Cloud environments’ decentralized and interconnected nature provides new attack vectors for cybercriminals.
Expanding Scope to Uncommon Platforms: Ransomware groups now target business-critical devices and platforms that lack readily available backups, increasing the potential impact of their attacks. Linux, Windows, macOS, FreeBSD, and non-standard processor architectures are all fair game, as demonstrated by the emergence of new ransomware families like RedAlert/N13V and LockBit.
Embracing Automation for Scaling Up: Ransomware groups leverage automation to streamline attacks, reducing costs and increasing operational efficiency. Automated tools enable attackers to propagate malware faster, target multiple platforms simultaneously, and evade detection by security systems. In addition, new ransomware strains have even increased encryption speeds enormously.
Leveraging Zero-Day Vulnerabilities: Adversaries take advantage of unknown software flaws or system vulnerabilities, enabling multiple attacks before patches or fixes are developed. This approach allows ransomware groups to exploit security gaps, making it challenging for organizations to defend against attacks effectively.
Looking ahead to 2023, three additional trends are predicted to shape the ransomware landscape:
Enhanced Functionality: Ransomware groups will continue to develop self-spreading capabilities, expanding their reach. Malware can autonomously infect vulnerable systems by incorporating worm-like features, enabling rapid proliferation and increased infection rates.
Driver Abuse: Vulnerable drivers, particularly in antivirus software, will be exploited by malicious actors. Attackers will focus on compromising device drivers to bypass security measures, rendering traditional defense mechanisms less effective and facilitating successful ransomware attacks.
Code Adoption: Ransomware groups will adopt code from other families, enhancing their capabilities and attracting more affiliates. This trend reflects the industrialization of ransomware, where malicious actors collaborate, share resources, and leverage the expertise of different groups to create more sophisticated and potent attacks.
Most Common TTPs of 2023
TTPs are also changing and varying every year in line with the trends. By examining the trends and insights from 2023, we can identify the top 5 TTPs commonly used by ransomware groups. These TTPs shed light on the evolving strategies employed by threat actors to maximize their impact and financial gains. Let’s delve into the details:
- Phishing Campaigns (T1566) Ransomware groups continue to rely on phishing campaigns to gain initial access to target networks. By sending deceptive emails or messages, they trick unsuspecting users into clicking on malicious links or downloading infected attachments. Vigilance and employee awareness training are crucial in mitigating the risks associated with these phishing attempts.
- Exploiting Remote Desktop Protocol (RDP) (T1021.001), Ransomware groups exploit weak or misconfigured Remote Desktop Protocol (RDP) connections to gain unauthorized access to systems. Once inside, they can move laterally across the network, escalating privileges and deploying ransomware payloads. Properly securing RDP by implementing strong passwords, multi-factor authentication, and limiting access can reduce the attack surface significantly.
- Software Vulnerabilities (T1203) Exploiting software vulnerabilities remains a favored TTP among ransomware groups. They target unpatched or outdated software, utilizing known vulnerabilities to gain a foothold in the target environment. Timely software updates and regular vulnerability assessments are vital for minimizing the risk of successful ransomware attacks.
- Supply Chain Attacks (T1195) Ransomware groups increasingly target supply chains, compromising trusted third-party vendors or software providers to gain access to their client’s networks. By exploiting vulnerabilities in the software supply chain, threat actors can infiltrate multiple organizations through a single entry point. Strengthening supply chain security, including conducting due diligence on vendors and assessing their security practices, is essential for mitigating this risk.
- Living-off-the-Land Techniques (T1218) Ransomware groups often employ “living-off-the-land” techniques, utilizing legitimate tools and processes already within a compromised network to carry out malicious activities. This approach allows them to bypass traditional security defenses and remain undetected for extended periods. Monitoring for suspicious behavior, employing behavioral analysis, and implementing robust endpoint detection and response (EDR) solutions can aid in detecting and stopping these stealthy attacks.
Summary
The prevalence of ransomware attacks in 2023 highlights the pressing need for organizations and individuals to prioritize robust cybersecurity measures. It is crucial to implement comprehensive security protocols, including regular software updates, strong password practices, network segmentation, and employee training on identifying phishing attempts and other common attack vectors. Additionally, organizations should consider investing in advanced threat detection and response systems to proactively identify and mitigate potential ransomware threats.
In conclusion, the alarming surge in ransomware attacks in 2023 emphasizes the critical importance of robust cybersecurity practices across organizations and individuals. By staying vigilant, implementing preventive measures, and fostering collaborative efforts, we can work towards mitigating the impact of ransomware and safeguarding our digital ecosystem.
How Can SOCRadar Help to Battle with Ransomware Threats?
SOCRadar offers comprehensive solutions to address the challenges posed by ransomware groups and their most common TTPs. Let’s explore how SOCRadar can help mitigate the risks associated with each technique:
Phishing Campaigns (T1566): SOCRadar provides robust email security capabilities that leverage machine learning algorithms and threat intelligence feeds. By using SOCRadar email analysis, SOC Analysts can analyze incoming emails, identify phishing attempts, and block malicious messages from reaching end users. Additionally, SOCRadar detects potentially fraudulent domains and websites that will enable threat actors to perform a wide range of attacks, such as wire transfer fraud, phishing, and scams against your organization and your customers.
Exploiting Remote Desktop Protocol (RDP) (T1021.001): SOCRadar’s Vulnerability Intelligence module helps organizations identify and remediate weaknesses in their RDP implementations. It continuously monitors and scans RDP services, detecting misconfigurations or weak credentials. By alerting security teams to potential vulnerabilities, SOCRadar enables them to take proactive measures such as implementing strong passwords, multi-factor authentication, and access restrictions to secure RDP connections effectively.
Software Vulnerabilities (T1203): SOCRadar’s vulnerability management module is critical in mitigating the risk of software vulnerabilities. It actively scans the environment, identifying outdated or unpatched software components. The platform correlates vulnerability data with threat intelligence, providing security teams with prioritized remediation recommendations. SOCRadar helps organizations stay ahead of threat actors exploiting known vulnerabilities by ensuring timely software updates and patch management.
Supply Chain Attacks (T1195): SOCRadar’s supply chain security module assists organizations in proactively assessing the security posture of their third-party vendors and software providers. It performs due diligence checks, evaluates vendor security practices, and assesses potential risks. With this information, organizations can make informed decisions about engaging with vendors and ensure they maintain adequate security controls throughout the supply chain.
Living-off-the-Land Techniques (T1218): SOCRadar’s advanced threat detection capabilities, including behavioral analysis and endpoint detection and response (EDR) integration, empower organizations to identify and stop living-off-the-land attacks. By continuously monitoring your external attack surface SOCRadar detects suspicious behavior and alerts security teams in real-time. This enables swift investigation and response, helping organizations minimize the dwell time of threat actors and prevent further damage.
In summary, SOCRadar offers a comprehensive suite of tools and features to address the most common TTPs of 2023. By leveraging its threat intelligence, vulnerability management, supply chain security, and advanced threat detection capabilities, organizations can strengthen their security posture and effectively defend against evolving cyber threats.




































