
Gigabyte Firmware Code Injection: Persistent Backdoor Leads to Supply Chain Risks
Researchers have expressed concerns about the UEFI firmware found in numerous motherboards by Gigabyte, a PC hardware manufacturer. They discovered that the firmware injects executable code into the Windows kernel unsafely.
The injection allows attackers to compromise systems; some APT groups have previously used similar exploits.
Vulnerable Implementation and Supply Chain Risks in Gigabyte Systems
Researchers from Eclypsium have discovered this vulnerable implementation during their investigation of behavioral patterns resembling a BIOS/UEFI rootkit. Such rootkits, known as bootkits, exist within the low-level system firmware and inject code into the operating system in each boot cycle, making them difficult to remove even if the user reinstalls the OS or replaces the hard disk drive.
The UEFI firmware acts as a mini-OS because it comprises various modules responsible for hardware initialization. It initializes hardware before transferring the boot sequence to the bootloader and the installed operating system.
Although researchers have yet to identify a specific threat actor exploiting this vulnerability, the presence of a widespread and persistent backdoor that is difficult to remove introduces supply chain risks for organizations that utilize Gigabyte systems.
Firmware Code Injection: Risks and Exploits
Previously, various functionalities were implemented by injecting firmware code into the OS memory. Absolute LoJack (previously Computrace) Windows agent, an anti-theft mechanism in certain BIOSes, is one such feature. Even after reinstalling the operating system, the BIOS agent injects an application into the system, allowing users to remotely track and wipe stolen computers.
Security researchers have long warned about the potential misuse of the LoJack agent, which can be used to connect to unauthorized servers. They found evidence in 2018 that APT28 (aka Fancy Bear) had exploited the feature.
Risks of Unsecure Download Methods in Gigabyte Update Application
The Gigabyte update application uses three URLs to search for updates: a Gigabyte download server over HTTPS, the same server over plain HTTP, and a URL to a non-qualified domain called software-nas, which could be a local network device.
Two of the download methods pose significant security risks. Unencrypted HTTP connections are vulnerable to man-in-the-middle attacks, allowing attackers to redirect the system to their own server.
The third URL is even easier to abuse since an attacker on the same network can set up a web server and mimic the computer’s name as software-nas. The HTTPS connection is also susceptible to man-in-the-middle attacks due to incorrect server certificate validation.
Furthermore, the Gigabyte tools and updates, even if digitally signed, are not verified or validated by the firmware. This lack of digital signature verification makes it easy for attackers to exploit this feature.
Mitigations
To mitigate these risks, the researchers recommend the following steps for organizations with Gigabyte systems:
- Disable the APP Center Download & Install feature in UEFI.
- Monitor connections to these URLs to identify systems that may be affected on the network.
- Stay vigilant against similar features from other manufacturers, as pre-installed applications on PCs can also introduce vulnerabilities.
Monitor Supply Chain Risks with SOCRadar
SOCRadar provides organizations with valuable insights into supply chain risks. The platform includes a Supply Chain Intelligence panel to help you stay vigilant against related threats. The Latest Hacked Companies tab displays news about hacked companies, whereas the Vendor Intelligence tab contains up-to-date information about companies that have experienced supply chain attacks.
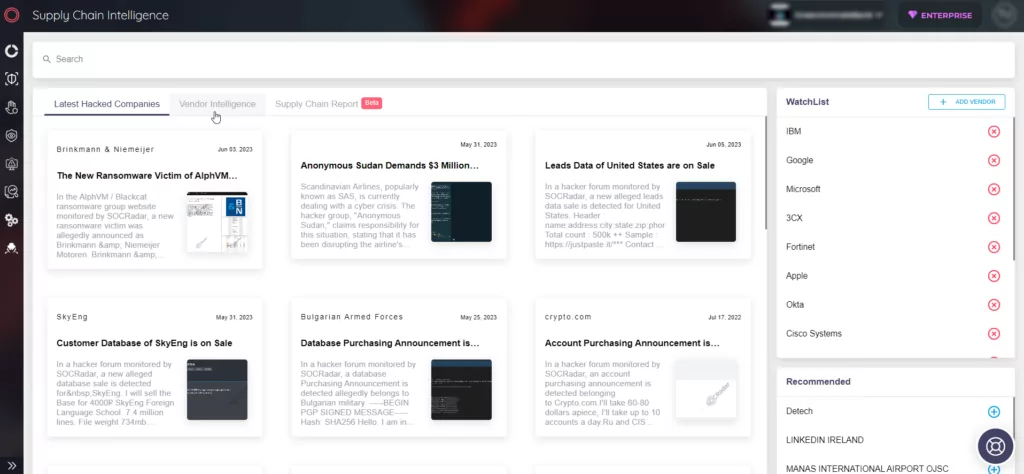
By adding vendors to the WatchList feature, you can proactively monitor any attacks that may impact your operations. Furthermore, the Supply Chain Report tab provides in-depth reports with detailed information on companies and their security posture.




































