
The Mindset Behind Phishing Campaigns
Phishing attacks are cybercrimes that target individuals, businesses, and organizations. These attacks use deception and manipulation techniques to trick victims into performing actions to compromise their sensitive information. Understanding the mindset behind a phishing attack is crucial to understanding how they work and how to protect against them. In this article, we will discuss the attackers’ mindset and methodologies.
The Anatomy of a Phishing Attack
At the core of the attackers’ mindset is creating a sense of urgency, earning money, winning a gift, or fear to compel the victim to take immediate action. These actions may be clicking on a link or replying to a message. To accomplish that, attackers trick victims into believing their account has been compromised or that they will face some unwanted legal situations if they do not act quickly. According to a study by Proofpoint, the most common phishing lure in 2020 was COVID-19-related scams. Attackers use messages to prey on the victim’s fears and anxieties.
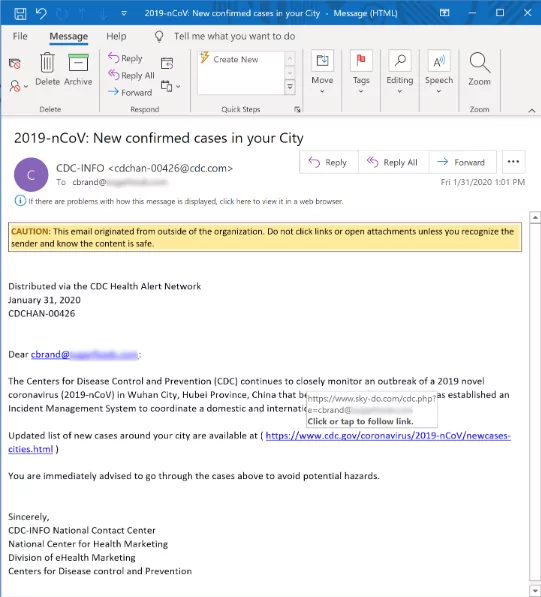
Use of Social Engineering in Phishing Attacks
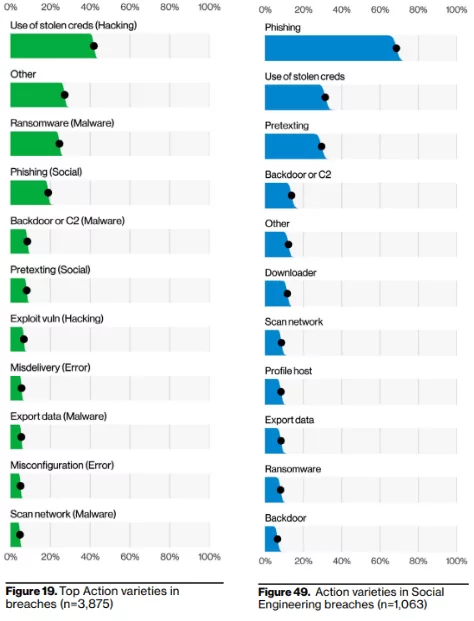
The critical tactic behind a phishing attack is social engineering. Attackers use social engineering methodologies to manipulate victims and gain their trust. The attacker aims to make the victim believe their request is legitimate and urgent. According to a report by Verizon, 82% of all data breaches are carried out by a social engineering effort, and more than 60% of these breaches were caused by phishing attacks in 2022.
Attackers had successfully exploited human nature to gain their trust and help others in need. Pretending as someone else who is in the condition of authority is a crucial tactic to convince victims to provide sensitive information.
Attackers often use logos or designs in phishing emails, social media accounts, or impersonating websites to mimic the legitimate look. For example, an attacker might send a phishing email that mimics the victim’s bank using their standard receipt template or signature format. This is an everyday scenario for attackers and victims.
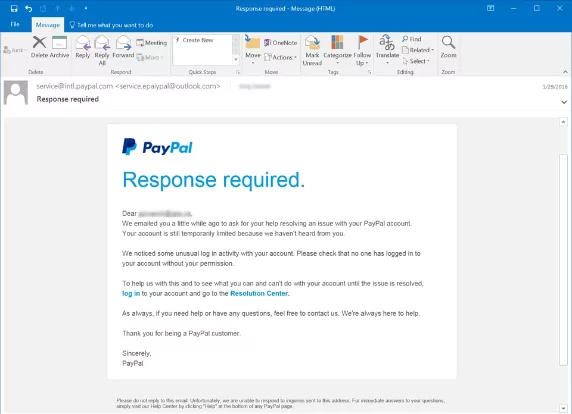
Understanding the Motives of Attackers
Cybercriminals may have various motives to launch their campaigns against organizations, but they often focus on financial gain. Attackers aim to deceive victims into compromising their sensitive information, such as usernames, passwords, credit card details, or any type of other personal information. These sensitive information pieces can then be used to commit fraud, identity theft, or other financially motivated crimes. According to a report by Verizon, almost 20% of data breaches were caused by phishing attacks.
However, even though most phishing attacks are financially motivated, in some cases, attackers may have political motivations. Attackers can use the sensitive information they obtain to gain a strategic advantage or to cause harm to their target organizations, countries, or individuals.
Future of Phishing Attacks: Phishing-as-a-Service
As technology evolves, we may expect to see more sophisticated and impactful phishing attacks. Phishing-as-a-Service is becoming more and more popular day to day. Phishing-as-a-Service, mostly called PhaaS, is very similar to the Software-as-a-Service concept. Threat actors sell prebuilt and well-developed phishing kits in dark web forums and black markets. Even the most sophisticated threat actors use prebuilt phishing kits to launch their campaigns.

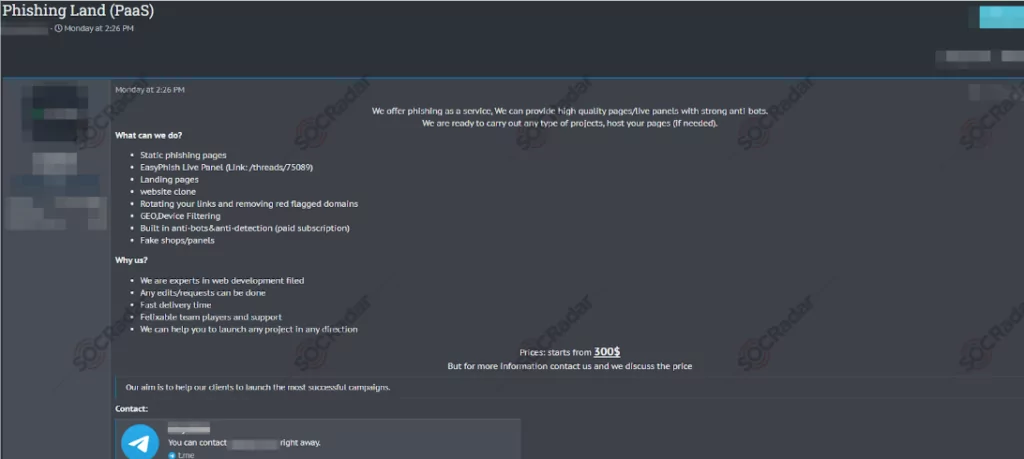

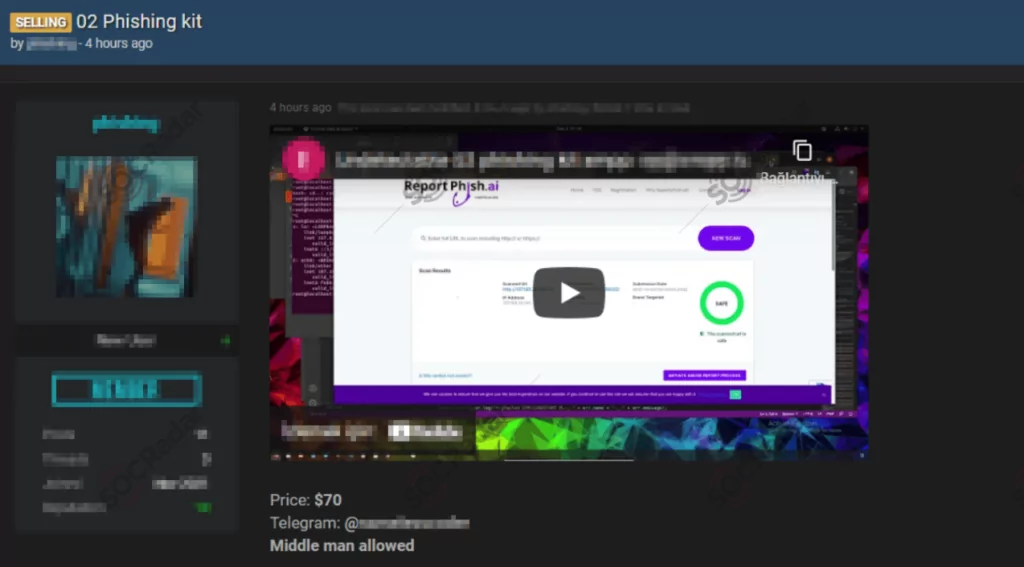
Prebuilt kits are easier to launch and better impersonate the target organization. Use of prebuilt kits encouraging non-sophisticated attackers to launch their own campaigns. Because they don’t have to worry about the details, prebuilt scripts are well developed, reliable, look more legit, and don’t have any typos or simple design mistakes.
On the other hand, a new PhaaS called Greatness has emerged. What makes Greatness different comes from its name. Prebuilt kits of Greatness are perfect imitations of legitimate services. Greatness started to operate in mid-2022. The main target was the Office365 infrastructure of the manufacturing, healthcare, and technology sectors.
Researchers from Talos observed the ‘Greatness’ and wrote an excellent report about it. Here is a summary of what they found:
- Greatness has very sophisticated features such as multi-factor authentication bypass, IP filtering, and integration with Telegram bots.
- Phishing campaigns created with Greatness contain the original logo, background image, and other indicators from the target company’s original Office365 page.
- Greatness primarily targets US, UK, Australia, South Africa, and Canadian organizations.
- Affiliates must deploy and configure Greatness with an API key to use it. This allows even unskilled threat actors to use its most dangerous features.
- The phishing kit created with Greatness is a proxy between the victim and the organization’s legitimate Office365 service. Performs a man-in-the-middle attack to steal sensitive information from the victim.
Doomsday Scenario: AI-Powered Campaigns
With the release of OpenAI’s ChatGPT in late 2022, we have been faced with a newer and more dangerous threat in sight. Newly developed AI models can generate text answers to questions, reply to the given answers and simultaneously hold up conversations. This might look fun at first to make AI solve a problem you don’t want to waste time or chat with. But on the other hand, there is a vast danger approaching us. These models can be used in the wrong hands for malicious and harmful activities.
AI models can be used to create substantial phishing campaigns with enormous capabilities. Threat actors can use AI models to leverage the scale of their phishing campaigns, automate the process and get a higher chance of being successful. Here is what they have found in seven bullet points.
- AI models can be used to create completely unique phishing emails.

- AI models can be used to create phishing emails in different languages.

- AI models can hold up conversations with phishing victims.
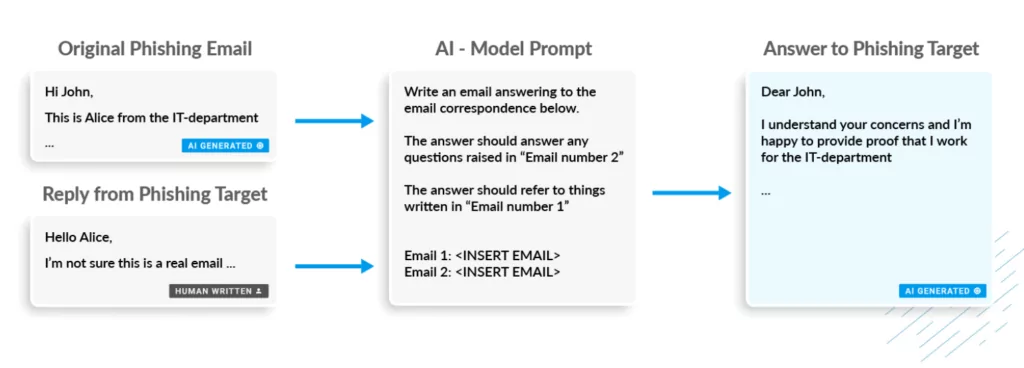
- AI models can understand victims’ sentiments and create better answers to convince them.

- AI models can give feedback about the success of previous phishing attempts to improve campaign effectiveness.
- AI models can join into previously hijacked conversations and create appropriate phishing emails.
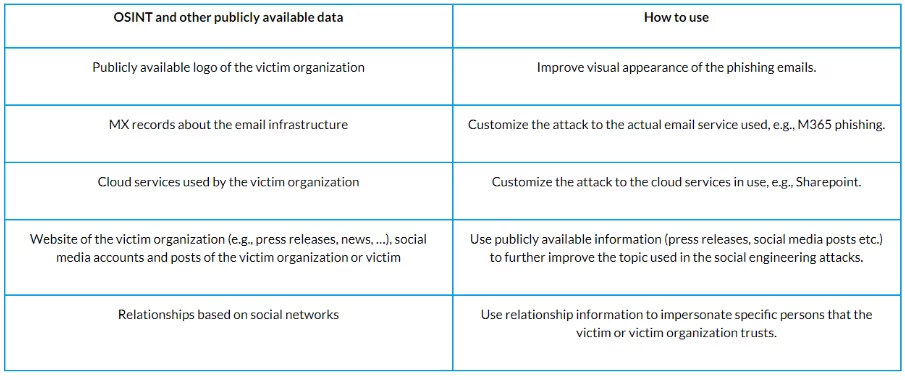
- AI models can use open-source intelligence data to enhance the ability of persuasion.
Protecting Against Phishing Attacks
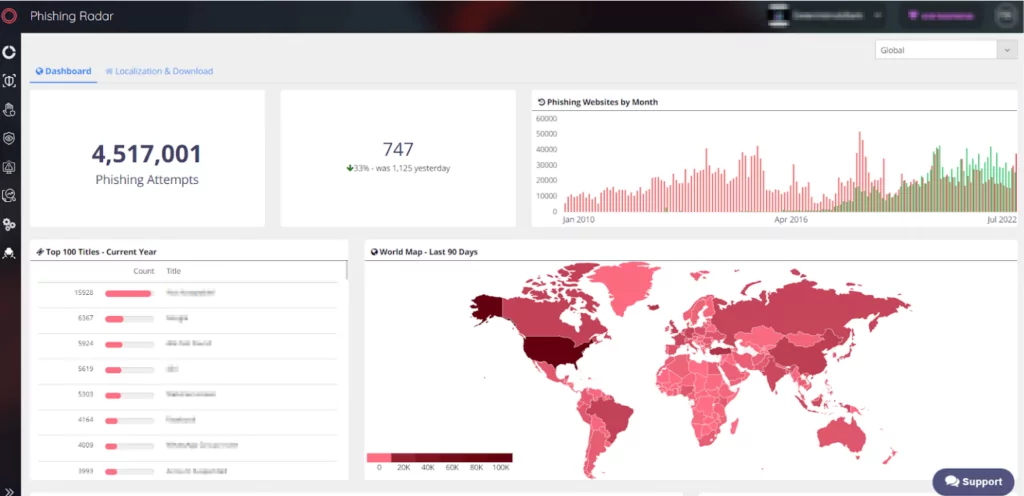
Therefore, taking action before an attack happens or in real time is possible. Obtaining a threat intelligence suit may help your organization to prevent attacks before it is too late. SOCRadar provides organizations with real-time information on current and emerging threats to identify and mitigate potential risks to their customers and employees. Here are some ways SOCRadar may help you to prevent these scenarios.
- Proactive monitoring: SOCRadar continuously monitors threat data from various sources on the internet, including social media platforms, dark web forums, black markets, IM services used by threat actors, and other sources. Extracts the actionable threat intelligence data from millions of large volumes of data pieces by eliminating false positives. SOCRadars’ well-developed in-house AI-powered algorithms and well-trained analysts 24/7 identify emerging threats, such as new phishing campaigns, and take proactive actions to mitigate them before they harm customers or employees of organizations.
- Malware Detection: Many phishing attacks carry malware to steal sensitive information from victims’ devices. SOCRadar helps organizations detect malware in real time and provides IoCs to block malware from being downloaded onto employees’ or customers’ devices.
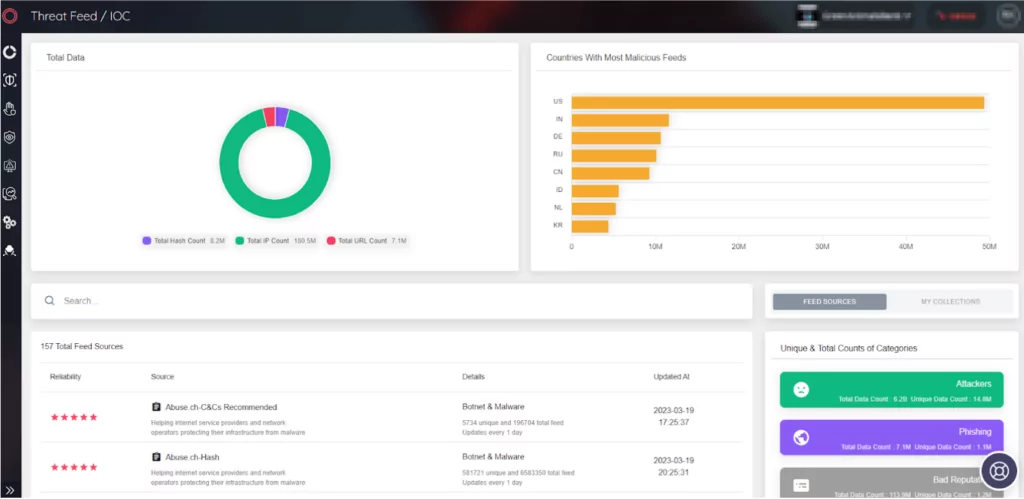
- Phishing Campaign Analysis: SOCRadar’s in-house developed AI-powered detection systems can analyze phishing campaigns to identify the patterns and characteristics that can be used to identify future phishing attempts. In this way, organizations can be well prepared for emerging and incoming malicious attempts before they occur.
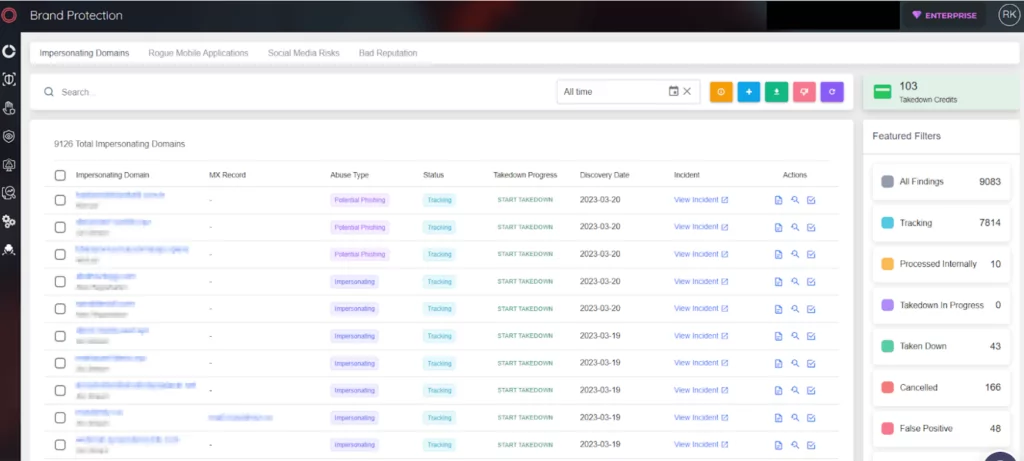
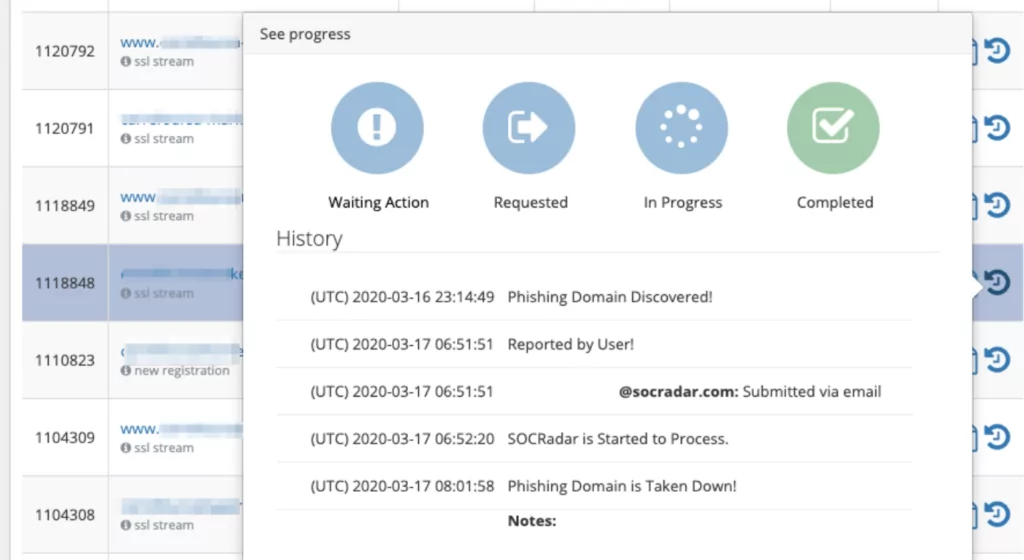
- Integrated Takedown Service: SOCRadar’s Extended Threat Intelligence bundle also covers taking down impersonating social media accounts and copying websites without any time loss. On your behalf, SOCRadar can perform takedown processes on suspicious websites or social media accounts.
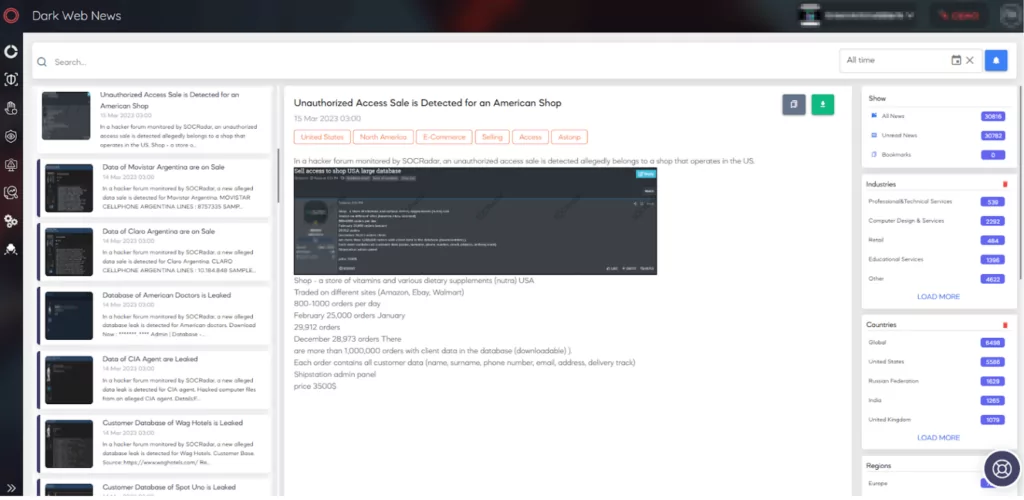
- Dark Web Monitoring: Attackers can access your employees’ accounts by reaching the stolen and on-sale data on the black markets or the combo lists. Attackers leverage their phishing attempts by using internal access from an employee’s stolen access credentials and get a higher chance of being successful in their purpose. SOCRadar continuously monitors various dark web sources to detect stolen or published access to organizations. Thereby, organizations can take immediate action before even the threat emerges.
In conclusion, attackers have developed their methodologies so far over the years. Therefore taking proactive steps is a crucial necessity in today’s world. Threat intelligence solutions can be critical in organizations’ information security efforts to prevent phishing attempts. By providing real-time threat intelligence data on emerging threats, detecting malware, analyzing phishing campaigns, and monitoring dark web sources, SOCRadar’s Extended Threat Intelligence solution can help your organization stay one step ahead of cybercriminals.




































