
Critical Update for Spring Framework: CVE-2024-22259 Exposes Applications to Open Redirect, SSRF Attacks
Spring Framework faces a critical security challenge with the emergence of CVE-2024-22259. This vulnerability poses significant risks to systems utilizing the Spring Framework, potentially exposing them to open redirect and Server-Side Request Forgery (SSRF) attacks.
Spring Framework is a lightweight application framework for creating enterprise applications. It consists of several sub-frameworks, including Spring AOP, Spring ORM, Spring Web Flow, and Spring MVC. It is commonly used to write high-performance, testable, and reusable code for Java-based applications.
What Is the CVE-2024-22259 Vulnerability in Spring Framework About?
The CVE-2024-22259 vulnerability primarily affects applications employing Spring Framework’s UriComponentsBuilder to parse externally provided URLs while also conducting validation checks on the URL host. Unfortunately, this combination creates a loophole that malicious actors can exploit.
Attackers can leverage this vulnerability to orchestrate open redirect attacks, particularly in phishing scenarios. By crafting URLs that pass host validation and then redirect users to untrusted websites, attackers can deceive users into divulging sensitive information.
Moreover, the vulnerability opens the door to SSRF attacks, enabling attackers to coerce vulnerable applications into making unauthorized requests to internal systems or external networks. This poses a grave risk of data leakage and compromise of infrastructure.
Which Spring Framework Versions Are Vulnerable to CVE-2024-22259?
Several versions of the Spring Framework are susceptible to CVE-2024-22259:
- 6.1.0 to 6.1.4
- 6.0.0 to 6.0.17
- 5.3.0 to 5.3.32
Older, unsupported versions are also affected by the vulnerability.
Monitoring the Latest Vulnerability Trends with SOCRadar
Use SOCRadar’s Vulnerability Intelligence for real-time monitoring of CVE and exploitation trends. Benefit from its comprehensive database and advanced analytics to track updates, identify exploits, and receive actionable insights for proactive vulnerability management.
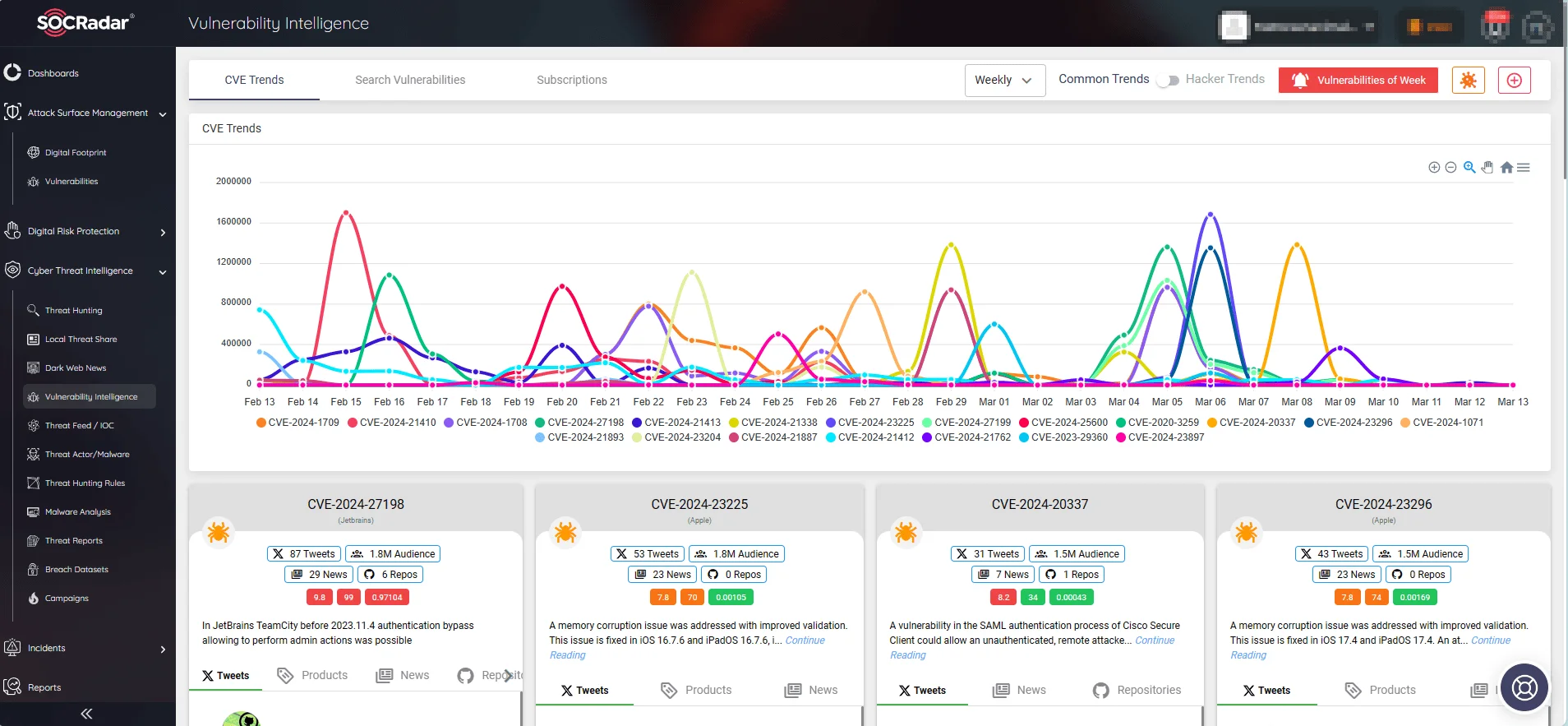
SOCRadar’s Vulnerability Intelligence
How to Fix CVE-2024-22259?
To mitigate the risks associated with CVE-2024-22259, it is important to promptly update Spring Framework dependencies to the following versions:
- For users of 6.1.x: Upgrade to version 6.1.5
- For users of 6.0.x: Upgrade to version 6.0.18
- For users of 5.3.x: Upgrade to version 5.3.33
By adopting these updated versions, organizations can fortify their applications against potential exploitation of the vulnerability.
How Can Attackers Exploit CVE-2024-22259?
The discovery of CVE-2024-22259 was credited to “threedr3am,” who highlighted its similarity to a previously patched vulnerability, CVE-2024-22243 (CVSS: 8.1), reported in February 2024. Despite the commonality in exploitation scenarios, the difference lies in the input used.
The researcher showcased the exploitation method on GitHub, and also posted about it on X. Notably, the exploitation technique involves a regular group escape achieved by adding “@” in front of the host.
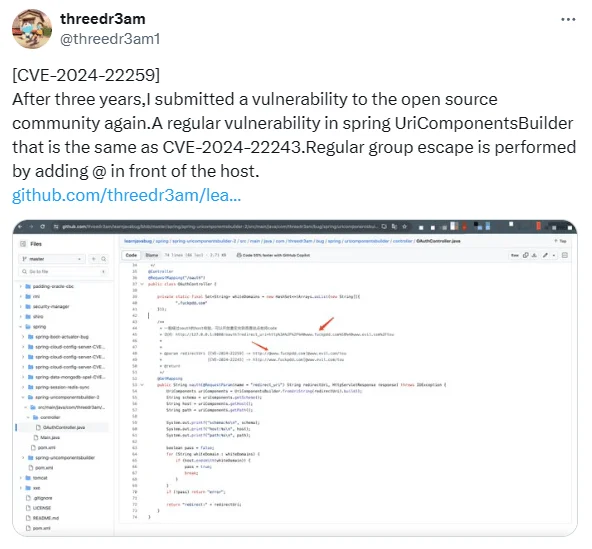
Researcher’s tweet about the new CVE-2024-22259 vulnerability in Spring Framework and its exploitation method (X)
Given the serious security risks associated with CVE-2024-22259, organizations must swiftly update their Spring Framework installations to the patched versions to protect their applications and data.
You can easily defend against threats like CVE-2024-22259 with SOCRadar’s Attack Surface Management (ASM) module. With its robust monitoring capabilities, SOCRadar proactively identifies vulnerabilities in digital assets, providing insights and allowing for quick action to strengthen patching strategies and effectively mitigate risks.
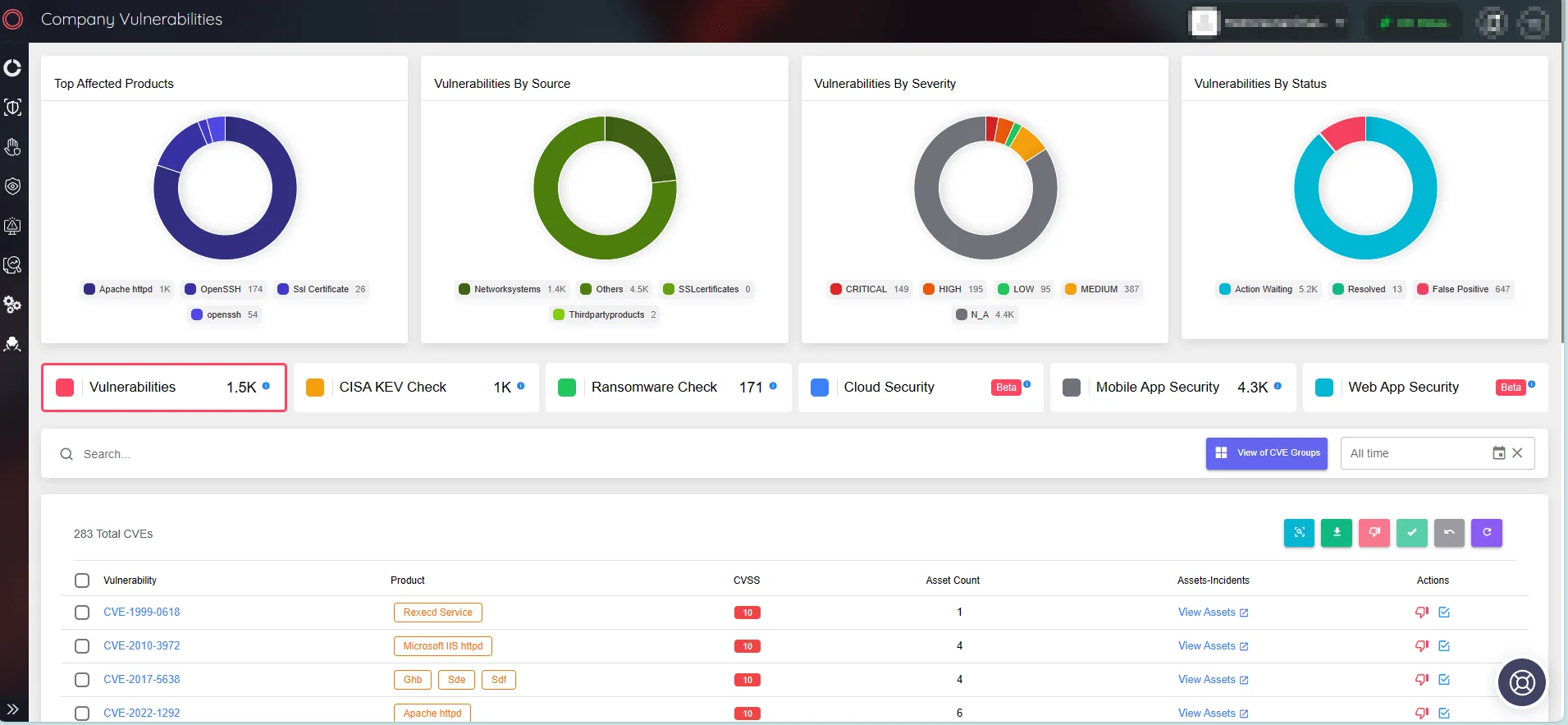
Monitor assets and manage Company Vulnerabilities on the SOCRadar platform




































