
CSP Bypass Unveiled: The Hidden Threat of Bookmarklets
A bookmarklet is a primitive version of browser extensions commonly used today. It consists of a bookmark that contains JavaScript code. These bookmarklets have been employed since the early days of JavaScript for various purposes. They provide users with a convenient one-click solution, enabling them to bypass paywalls on news websites, accelerate YouTube videos, control audio on web pages, and perform other functions.
The term “bookmarklet” was coined by Steve Kangas, the founder of bookmarklets.com. Another term used interchangeably with bookmarklets is “favelets,” invented by Tantek Celik, a Turkish-American computer scientist.
Brendan Eich, the inventor of JavaScript, introduced the javascript: protocol to facilitate the easy utilization of bookmarklets.
Users can add bookmarklets to their browsers by either creating a new bookmark and pasting the bookmarklet’s code as the URL or by simply dragging and dropping the bookmarklet’s link onto the bookmark toolbar, as offered on the web pages.
Between 1994 and 2014, bookmarklets were widely utilized by individuals. However, the implementation of the Content-Security-Policy (CSP), a browser security mechanism, led many to believe that bookmarklets became obsolete. Numerous “Rest in Peace” (RIP) messages were seen as a result.
While the RFC (Request for Comments) of the Content Security Policy suggests that extensions and bookmarklets should not interfere with a user’s preference and that the configuration of the website owner should take precedence, many people have lamented the apparent uselessness of bookmarklets due to the CSP.
A newly developed method for enticing victims involves the addition of bookmarklets and enticing them to click on specific websites. This technique has revealed that despite implementing Content-Security-Policy on targeted websites, bookmarklets can still be executed within the context of the targeted domain.
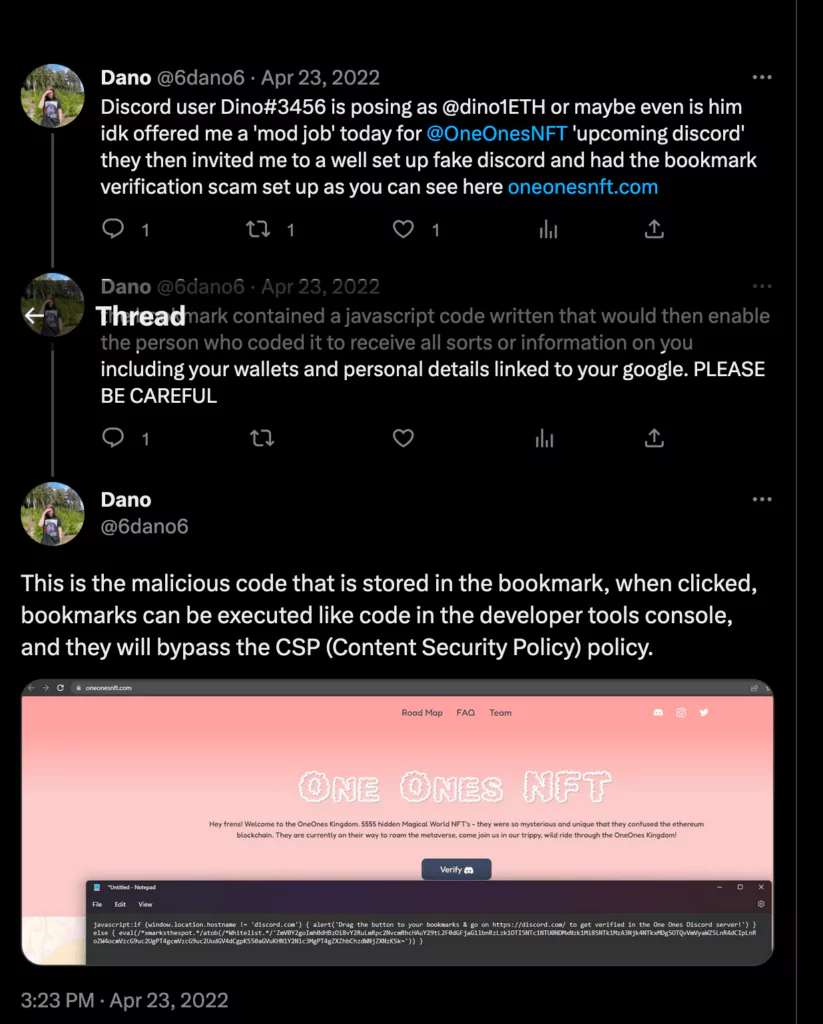
This allows them to access the Document Object Model (DOM) of the page, potentially leading to the extraction of sensitive data, which can then be sent to servers controlled by the attacker.
The Discord Attacks: Revealing the Strategies
Incidents targeting Discord communities focused on cryptocurrency have recently shed light on the malevolent capabilities of bookmarklets. In these attacks, attackers assumed the guise of reporters affiliated with cryptocurrency-oriented news platforms and engaged in conversations with community administrators, gradually earning their trust. Subsequently, the attackers shared a link to a Discord server, deceitfully presenting it as the official server of the news outlet. To verify their identity, the administrators were instructed to drag a button to their bookmarks bar, unaware that it contained JavaScript code with malicious intent.
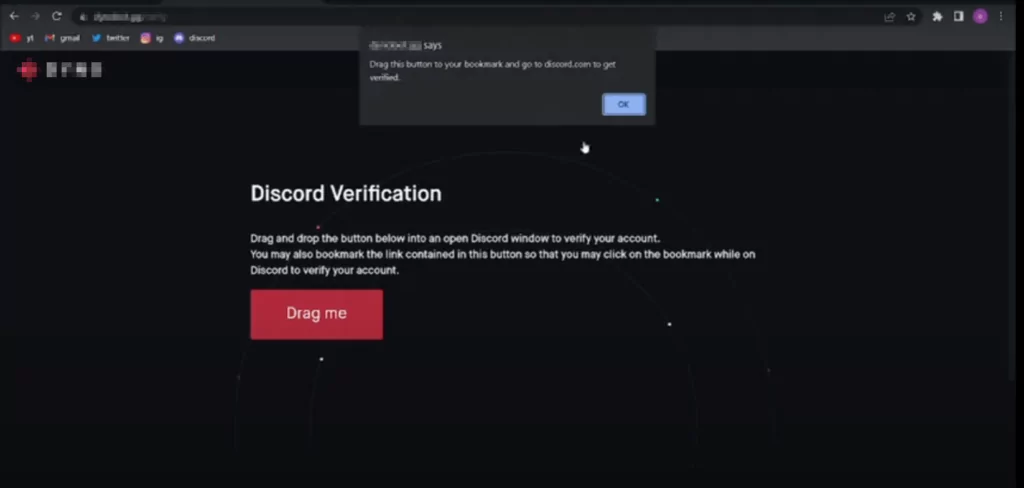
Without the administrators’ knowledge, the bookmarklet discreetly retrieved their Discord token when it was dragged, subsequently transmitting it to the attacker’s website. Armed with the pilfered token, the attackers achieved unauthorized access to the administrators’ accounts. Taking advantage of the late-night hours when the administrators were less active, the assailants proceeded to disseminate deceitful announcements regarding exclusive cryptocurrency prospects. These announcements were specifically crafted to entice community members into clicking on the provided links.
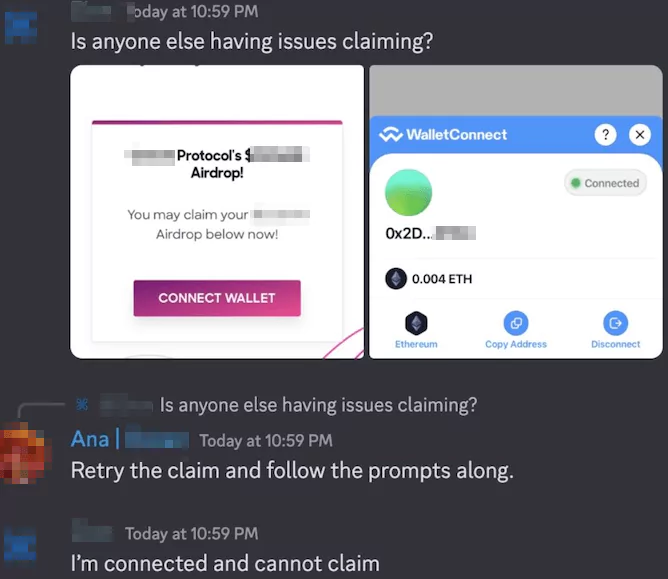
Upon clicking the links, community members were redirected to the scammer’s website, where they were prompted to connect their cryptocurrency wallets. Regrettably, this action inadvertently allowed the attackers to siphon funds from these valuable accounts by requesting unrestricted spending approvals. Moreover, individuals who recognized the fraudulent scheme and endeavored to caution others faced immediate expulsion from the compromised Discord channel. The attackers utilized these measures to retain control and evade detection, thus perpetuating their illicit activities.
Expanding the Realm of Possibilities with Cosmetic Attacks
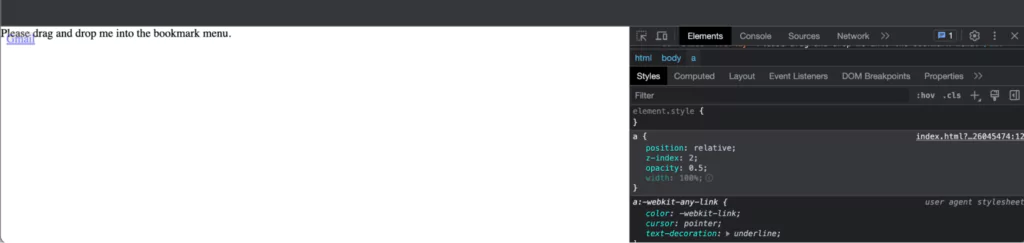
Despite the Discord attackers employing a technique that drew vigilant individuals’ attention, there is even greater potential for leveraging UI redressing or cosmetic attacks.
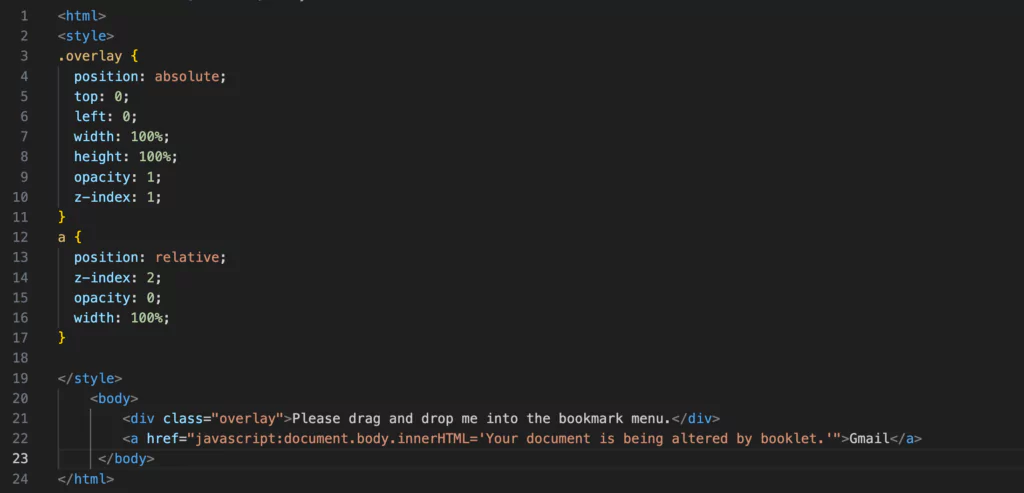
One such example involves overlaying an innocuous DIV element with an overlaid anchor element. Through this approach, the attackers can manipulate the purpose of the attack, presenting an apparently legitimate link within the bookmark menu.
The assailant effectively circumvents the security provided by Content Security Policy (CSP) by employing a bookmarklet attack. Consequently, the attacker gains access to the targeted website’s Document Object Model (DOM), including the page content and potentially even cookies (unless marked with the httpOnly flag). This breach of CSP protection widens the attacker’s scope and amplifies their ability to exploit sensitive information.
In addition to the aforementioned techniques, an attacker can further compromise the targeted page by incorporating a download link for malicious executables. This method enables the dissemination of harmful software, allowing the attacker to exploit vulnerabilities and potentially gain unauthorized access or execute malicious actions on the victim’s system. By adding such download links, the attacker expands their arsenal of attack vectors and intensifies the threat posed to unsuspecting users.
A Greater Threat than Malicious Extensions: The Dangers of Bookmarklets
Browser extensions possess a wide range of capabilities, including intercepting HTTP requests and responses, reading cookies, and accessing browsing history. Recognizing the potential risks associated with these capabilities, browser vendors have implemented measures to mitigate them in newer versions of browser extensions. Extension marketplaces diligently examine browser extensions for any malicious activities or permissions, ensuring they align with user consent.
While content scripts in the most capable version of browser extensions (previous version, manifest v2) have limited access to the DOM of injected pages, bookmarklets appear to be exempt from such limitations. This unrestricted access raises questions and concerns, particularly when considering the farewell to bookmarklets due to the emergence of CSP.
The bypass capabilities exhibited by bookmarklets in the face of CSP raise valid concerns regarding their usage and potential consequences, making them a more formidable threat compared to malicious extensions while thinking that convincing someone to drag and drop a text to the bookmark toolbar is easier than convincing them to install a malicious extension.
Protecting Against Bookmarklet Attacks
Safeguarding against bookmarklet attacks and similar threats requires adopting a proactive cybersecurity approach. Consider the following recommended practices to enhance your protection:
- Regularly Review and Update Bookmarks: Regularly review your bookmarks to eliminate outdated or unnecessary entries. Keep your bookmarks up to date to ensure they lead to secure and correct URLs.
- Enable Browser Security Features: Keep your web browser and its security features up to date. Enable functionalities like phishing and malware protection to minimize exposure to malicious websites.
- It is crucial to acknowledge that, despite their innocuous naming, bookmarks can store JavaScript code, which is executed within the context of the visited page. To safeguard against potential vulnerabilities arising from malicious bookmarklets and minimize access to the Document Object Model (DOM) context of pages, it is advisable to click on bookmarks within a newly created tab, such as “about:blank.” By employing this approach, the risk of unwanted DOM access is effectively eliminated.
Moreover, the “Open in a New Tab” option available in the context menu of bookmark items provides a convenient means to access bookmarked links while maintaining a secure browsing environment. By utilizing this option, users can ensure a safer browsing experience without compromising the integrity of their browsing sessions.
While bookmarks and bookmarklets provide convenience and enhance productivity, it is crucial to approach them with the utmost caution in terms of cybersecurity. Recent attacks on Discord communities have highlighted the potential risks associated with these browser features. By exercising vigilance, staying well-informed, and adopting best security practices, users can effectively minimize risks and ensure a safer online experience. Remember, staying proactive and alert in the face of evolving cyber threats is key to protecting oneself.




































