
CUPS Vulnerabilities: What You Need to Know
[Update] October 9, 2024: “Automated Scanner Released for CVE-2024-47176 in CUPS”
[Update] October 4, 2024: “New Attack Vector in CUPS Exposes Over 58,000 Devices to DDoS Exploitation”
Recent reports have highlighted security vulnerabilities in the Common Unix Printing System (CUPS), a crucial component in many Unix-like systems. These vulnerabilities could allow attackers to execute commands on affected devices under specific conditions, leading to Remote Code Execution (RCE).
Discovered by researcher Simone Margaritelli (aka EvilSocket) and acknowledged by Red Hat, the vulnerabilities – CVE-2024-47176, CVE-2024-47076, CVE-2024-47175, and CVE-2024-47177 – have raised questions about their potential risks and how best to address them, becoming a booming discussion topic within the cybersecurity community in the past day.
What Are the CUPS Vulnerabilities?
The Common Unix Printing System (CUPS) is a core component in many Unix-like operating systems, enabling management of printers over networks through the Internet Printing Protocol (IPP). However, recent security findings have exposed vulnerabilities that could compromise this system:
- CVE-2024-47176: This vulnerability affects cups-browsed versions 2.0.1 and earlier. The service listens on UDP port 631, accepting packets from any source. This flaw allows attackers to send malicious IPP requests to an attacker-controlled URL.
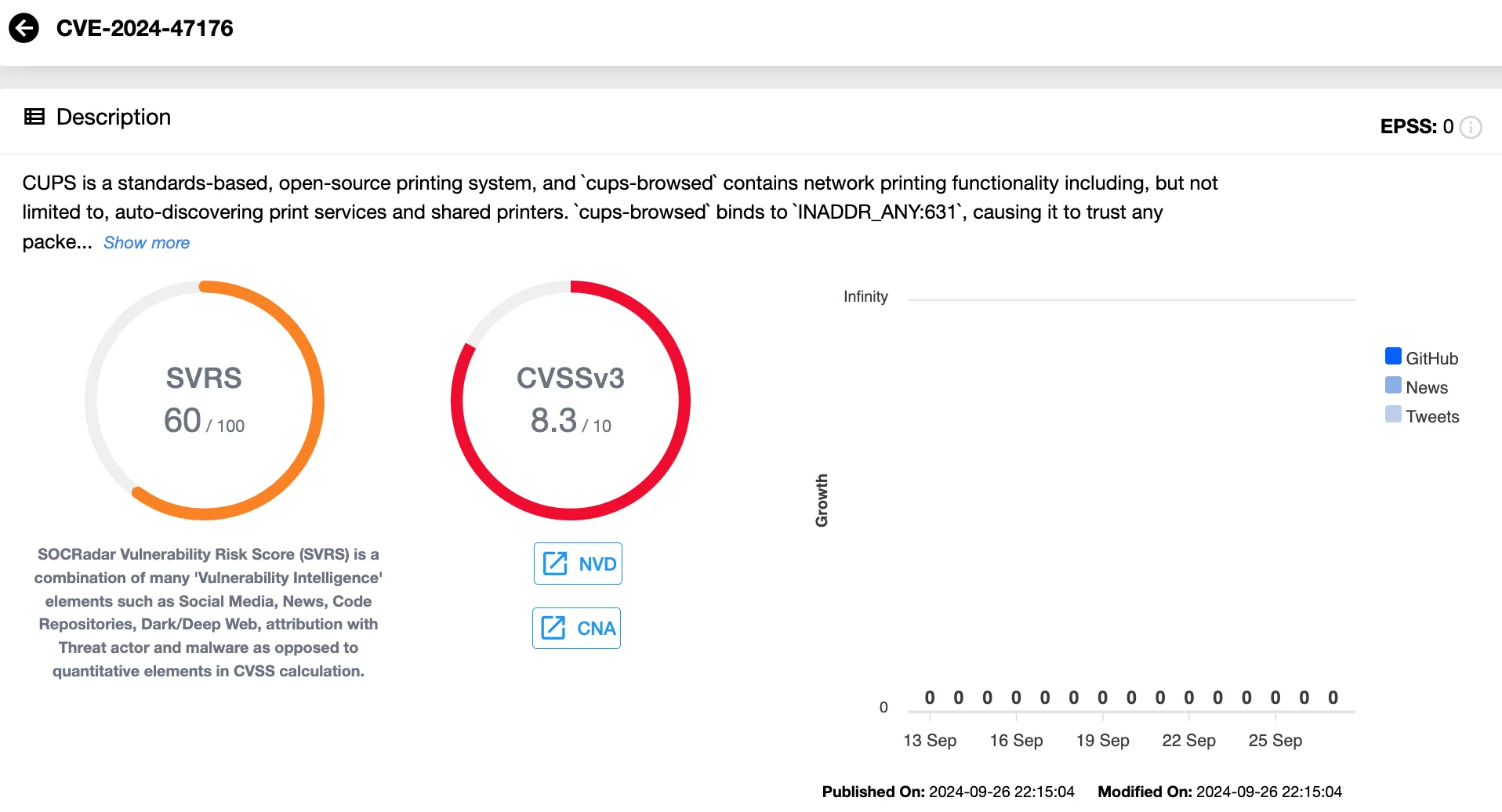
Details of CVE-2024-47176 (SOCRadar Vulnerability Intelligence)
- CVE-2024-47076: Found in libcupsfilters versions up to 2.1b1, this vulnerability stems from improper validation of IPP attributes. An attacker could inject unvalidated data into the CUPS system, which could disrupt services or lead to further exploitation.
- CVE-2024-47175: This vulnerability impacts libppd versions 2.1b1 and earlier, where temporary PPD files created during print jobs are not properly sanitized. Attackers could manipulate this process to inject harmful data.
- CVE-2024-47177: Affecting cups-filters versions 2.0.1 and earlier, this flaw enables arbitrary command execution through the FoomaticRIPCommandLine parameter.
The command execution flaw in CUPS was initially rated 9.9 in severity, causing some confusion. The researcher suggested this high rating was likely due to the ease of exploitation and widespread package use, and was an early estimation by a Red Hat engineer.
SOCRadar XTI Vulnerability Intelligence module
With SOCRadar’s Vulnerability Intelligence, you can easily track new CVEs, exploits, and updates as they emerge, ensuring your organization stays ahead of emerging threats.
Which Systems Are Affected by CUPS Vulnerabilities?
CUPS, and specifically the cups-browsed component, is included in most Unix-like systems, making it widely distributed across multiple platforms. The vulnerability primarily impacts the following distributions, as stated by the researcher:
- Most GNU/Linux distributions
- Some versions of BSD
- Potentially Google Chromium/ChromeOS
- Oracle Solaris
According to the researcher, scans of public IPv4 ranges returned connections from hundreds of thousands of devices, highlighting the potential scale of the issue. Furthermore, the fact that the CUPS package is included in many systems is alarming, with the service enabled by default in some cases.
Shodan data indicates that over 75,000 exposed CUPS daemons are visible on the internet, underscoring the potential scale of the issue. Most of these are located in Korea, followed by the United States.
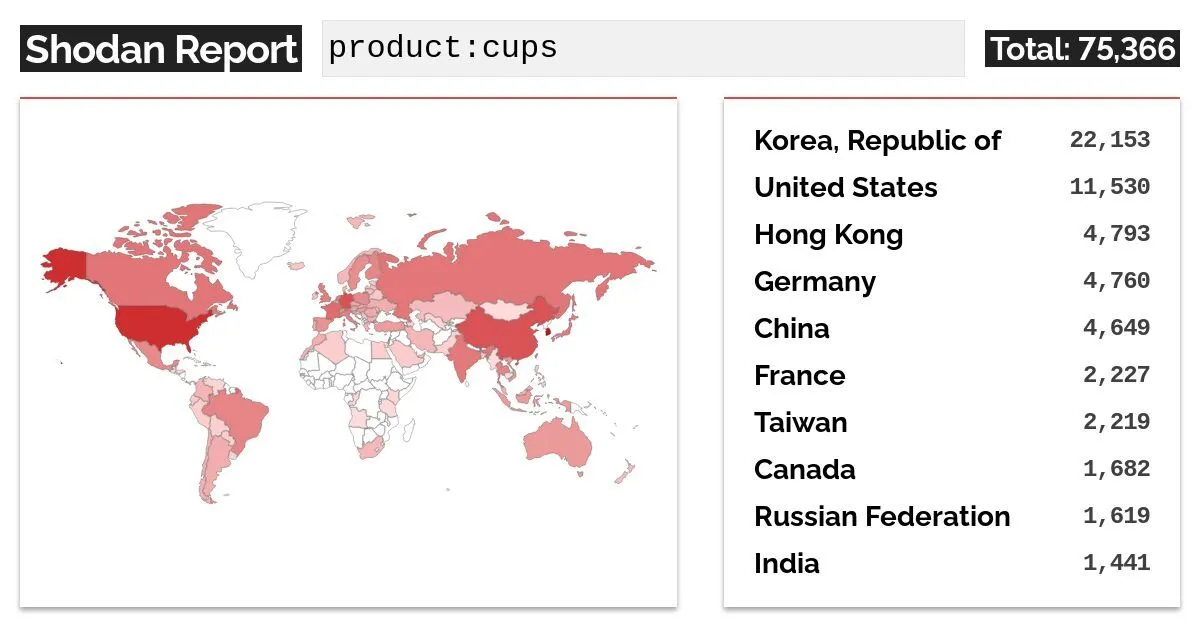
Shodan reports that there are over 75,000 CUPS daemons on the Internet (X)
Impact and Exploitability of the CUPS Vulnerabilities
The attack surface for these vulnerabilities is significant, particularly for systems where the cups-browsed service is active and exposed to public internet connections or local networks.
The researcher behind the CUPS vulnerabilities’ discovery mentions that attackers can target vulnerable systems by exploiting UDP port 631, which is commonly exposed on Linux systems.
If UDP port 631 is left exposed with the cups-browsed service enabled, attackers could gain control over print jobs and execute arbitrary commands. This could lead to security breaches, especially in environments where sensitive data is processed or printed.
Additionally, beyond public internet attacks, local network-based threats such as LAN intrusions or DNS-SD spoofing are feasible, especially in environments where internal network connections are trusted.
All in all, attackers could potentially exploit vulnerable systems through a chain of events that starts with access to an exposed CUPS instance, leading to arbitrary code execution on the victim’s machine once a malicious IPP server is advertised.
Although real-world exploitation has not been observed, it is also important to note that the researcher raised concerns about potential information leaks during the disclosure process. Specific details of the vulnerabilities, including exploit information, appeared on a Dark Web forum before the official writeup.
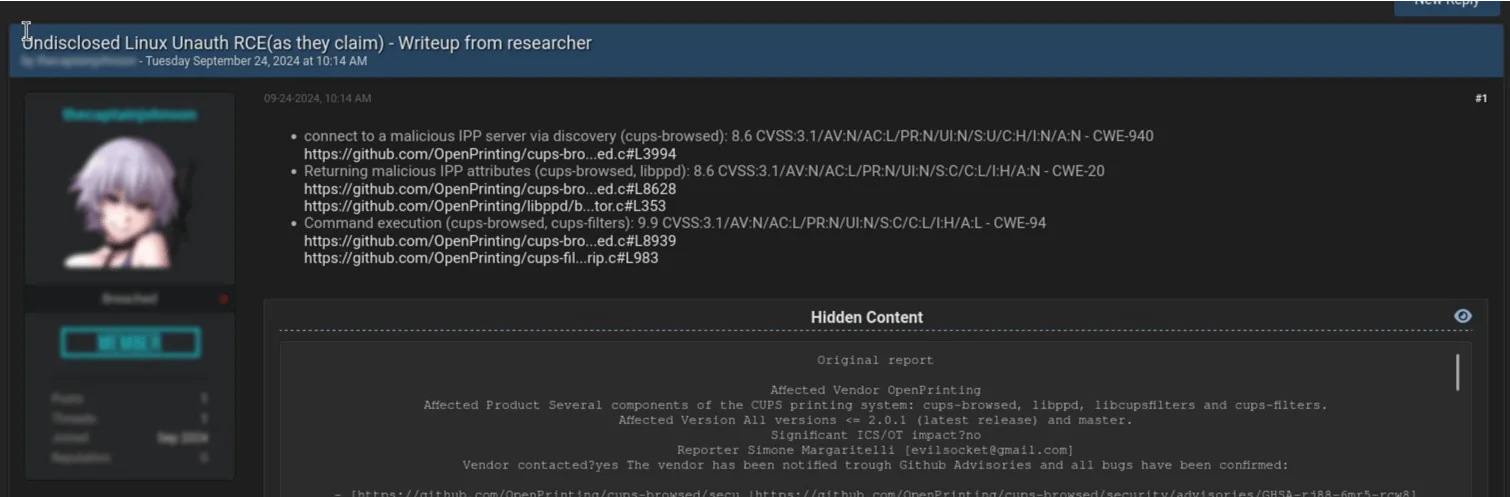
The hacker forum post about ‘Undisclosed Linux Unauth RCE’
Such events typically stir up the attention of threat actors, increasing the likelihood of future exploitation if systems remain unpatched. You can find out about sensitive information and exploits exposed on hacker channels through SOCRadar’s Dark Web Monitoring.
Red Hat’s Assessment on the Vulnerabilities’ Impact
According to Red Hat, the exploitation chain for these vulnerabilities involves manually enabling the cups-browsed service, gaining access to an exposed or trusted network, and advertising a malicious IPP server. Ultimately, when a victim tries printing from the compromised device, attackers can execute arbitrary code on the victim’s system.
Given the challenges in exploiting the CUPS vulnerabilities, researchers have classified their severity as Important (rather than Critical). While the vulnerabilities affect all versions of Red Hat Enterprise Linux (RHEL), most systems are not vulnerable in their default configurations.
How Can You Mitigate the CUPS Vulnerabilities?
In environments where printing is not essential, the easiest mitigation step is to disable the cups-browsed service. Administrators can do this using the following command:
$ sudo systemctl disable cups-browsed
For those still relying on CUPS, it’s best to wait for patches from your Linux distributor.
In the meantime, updating your CUPS package is highly recommended. If updating isn’t feasible, blocking traffic to UDP port 631 can reduce risk. Additionally, disabling DNS-SD traffic may help.
Researcher Simone Margaritelli also recommends, on a more personal level, removing CUPS and its related services entirely if printing is not a key function in your environment.
For more in-depth details and suggestions, check out EvilSocket’s full article here.
New Attack Vector in CUPS Exposes Over 58,000 Devices to DDoS Exploitation
Researchers have confirmed a new attack vector in CUPS that could be exploited for Distributed Denial-of-Service (DDoS) attacks.
Attackers can send a single crafted packet to vulnerable CUPS services, which in turn generates larger, partially attacker-controlled IPP/HTTP requests to the intended target. Not only does the target suffer, but the host running the CUPS server is also impacted, as the attack consumes its network bandwidth and CPU resources.
Akamai’s research found that more than 198,000 devices are vulnerable to CUPS flaws, with around 58,000 devices at risk of being exploited for DDoS attacks. Hundreds of these systems exhibit an “infinite loop” behavior, significantly amplifying the attack’s impact. On average, attackers can achieve a 600x amplification factor, making these systems highly attractive targets. The risk is further heightened because many of the vulnerable devices are running outdated CUPS versions, such as version 1.3 from 2007.
Additionally, researchers discovered that some CUPS servers were able to complete TLS handshakes, placing further strain on server resources due to encryption and decryption processes.
The minimal resources needed to exploit this vulnerability make it particularly dangerous, allowing attackers to launch large-scale DDoS attacks at minimal cost. As the researchers noted, “It would take an attacker mere seconds to co-opt every vulnerable CUPS service currently exposed on the internet and cost the attacker less than a single US cent on modern hyperscaler platforms.”
Automated Scanner Released for CVE-2024-47176 in CUPS
An automated scanner has been developed to help system administrators detect devices vulnerable to the CUPS RCE flaw, CVE-2024-47176. Created by researcher Marcus Hitchins (aka MalwareTech), the scanner enables rapid identification of systems running vulnerable CUPS-browsed services.
The vulnerability stems from CUPS-browsed binding its control port UDP 631 to INADDR_ANY, exposing it to local networks and potentially allowing unauthorized access. Using this, the scanner sends custom UDP packets to devices on the network, prompting vulnerable instances to respond.
The tool is available on GitHub, enabling security teams to efficiently assess exposure and take action.
Enhance Your Protection with SOCRadar
SOCRadar’s Attack Surface Management helps identify where your organization’s digital assets are exposed and vulnerable, offering full visibility into your Digital Footprint.
SOCRadar XTI Attack Surface Management (ASM) module, Digital Footprint
With continuous monitoring, SOCRadar provides real-time insights into potential risk points, such as exposed services, ports, and specific vulnerabilities affecting your systems, enabling you to take action before they can be exploited. Sign up for a Freemium to test the capabilities of SOCRadar XTI.



































