
CVE-2024-21006 in Oracle WebLogic Server – Oracle’s April 2024 Update Brings 441 New Security Patches
Oracle has released its Critical Patch Update advisory for April 2024, which addresses vulnerabilities across multiple products. This update includes 441 new security patches, including fixes for many critical vulnerabilities; one that has received attention in the media is CVE-2024-21006, a severe vulnerability in Oracle WebLogic Server.
What is CVE-2024-21006?
CVE-2024-21006 is a high-severity vulnerability in Oracle WebLogic Server, a platform for developing and deploying enterprise Java applications. The vulnerability has a CVSS score of 7.5 and has been addressed in the Oracle April 2024 Critical Patch Update.
Exploitation of CVE-2024-21006 could allow an unauthenticated attacker with network access via T3, IIOP, to compromise Oracle WebLogic Server.
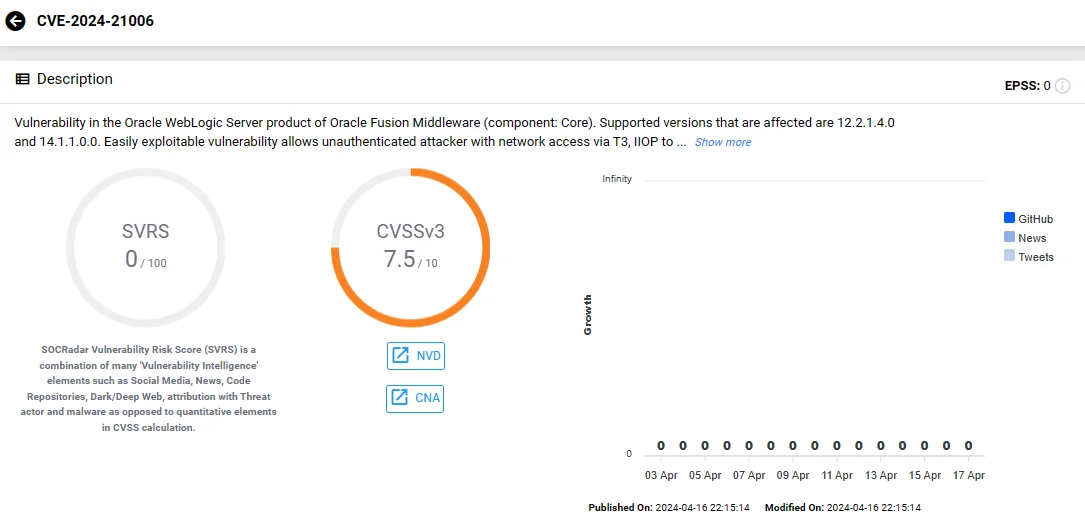
Vulnerability card of CVE-2024-21006 (SOCRadar Vulnerability Intelligence)
CVE-2024-21006 affects the supported versions 12.2.1.4.0 and 14.1.1.0.0. Its exploitation is not complex and can result in unauthorized access to data or complete access to all Oracle WebLogic Server-accessible data.
A Shodan search for exposed Oracle WebLogic Servers yields 5,370 results, indicating potentially vulnerable instances that could be targeted in attacks exploiting CVE-2024-21006.
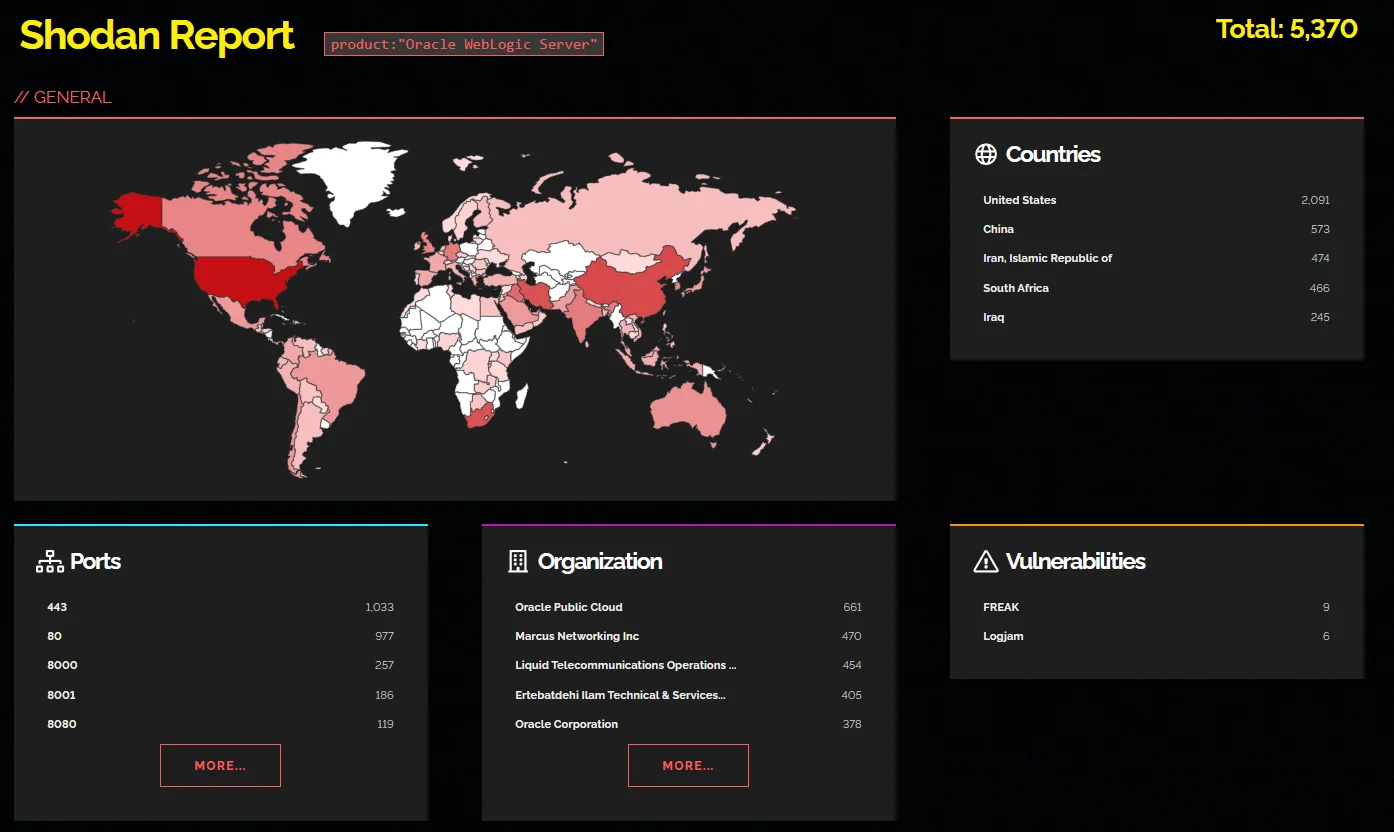
Shodan search for exposed Oracle WebLogic Server instances
What are the critical vulnerabilities in Oracle’s April 2024 Critical Patch Update?
Aside from the high-severity CVE-2024-21006 vulnerability we highlighted, multiple vulnerabilities in the Oracle April 2024 Critical Patch Update have been classified with a CVSS score greater than 9.0, demanding attention.
The following is a list of some of these critical vulnerabilities addressed in the April 2024 Critical Patch Update, along with brief descriptions, the affected Oracle products, and versions.
CVE-2022-34381 (CVSS: 9.8): The vulnerability affects Dell BSAFE SSL-J v7.0 and earlier, plus Dell BSAFE Crypto-J before 6.2.6.1, due to an outdated third-party component. Exploitation of CVE-2022-34381 by an unauthenticated remote attacker could compromise the system.
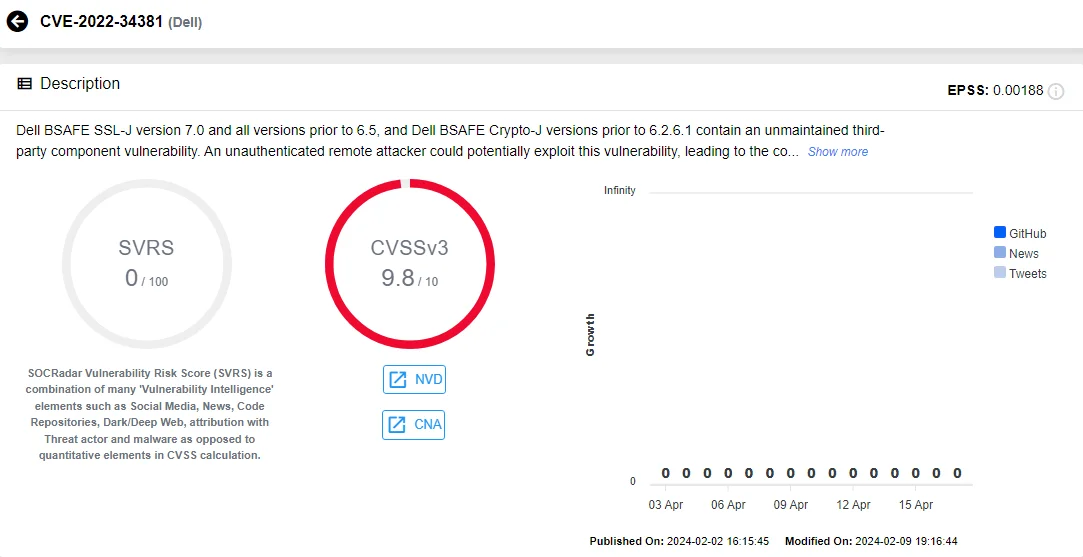
Vulnerability card of CVE-2022-34381 (SOCRadar Vulnerability Intelligence)
This vulnerability affects:
- Oracle Communications Network Integrity – 7.3.6.4
- Oracle Communications Unified Inventory Management – 7.4.0-7.4.2, 7.5.0, 7.5.1
- Oracle Application Testing Suite – 13.3.0.1
- Oracle Fusion Middleware MapViewer – 12.2.1.4.0
- Oracle Retail Integration Bus – 14.1.3.2, 15.0.3.1, 16.0.3, 19.0.1
- Oracle Retail Service Backbone – 14.1.3.2, 15.0.3.1, 16.0.3, 19.0.1
- Oracle StorageTek Tape Analytics (STA) – 2.5
CVE-2022-42920 (CVSS: 9.8): Apache Commons BCEL has APIs designed to modify specific class characteristics. However, the vulnerability allows these APIs to generate arbitrary bytecode due to an out-of-bounds writing issue. Attackers could exploit this in applications passing controlled data to these APIs, granting them unexpected control over the bytecode.
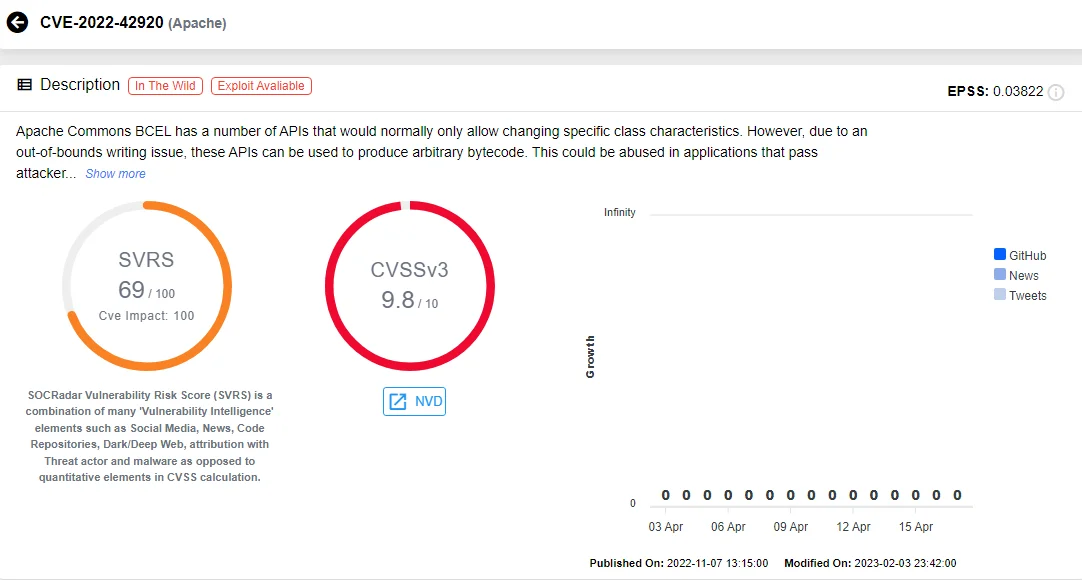
Vulnerability card of CVE-2022-42920 (SOCRadar Vulnerability Intelligence)
This vulnerability affects:
- Oracle Application Testing Suite – 13.3.0.1
- Oracle Enterprise Manager for Fusion Middleware – 13.5.0.0
- Oracle StorageTek Tape Analytics (STA) – 2.5
- Oracle Solaris Cluster – 4
- Oracle Retail Assortment Planning – 15.0.3, 16.0.3
CVE-2022-46337 (CVSS: 9.8): A crafted username could bypass LDAP authentication in Derby installations authenticated via LDAP. This may lead to disk space exhaustion by creating superfluous Derby databases and enable malware execution by the booting account. In LDAP-protected databases without SQL GRANT/REVOKE authorization, attackers could access and manipulate sensitive data, and execute database functions.
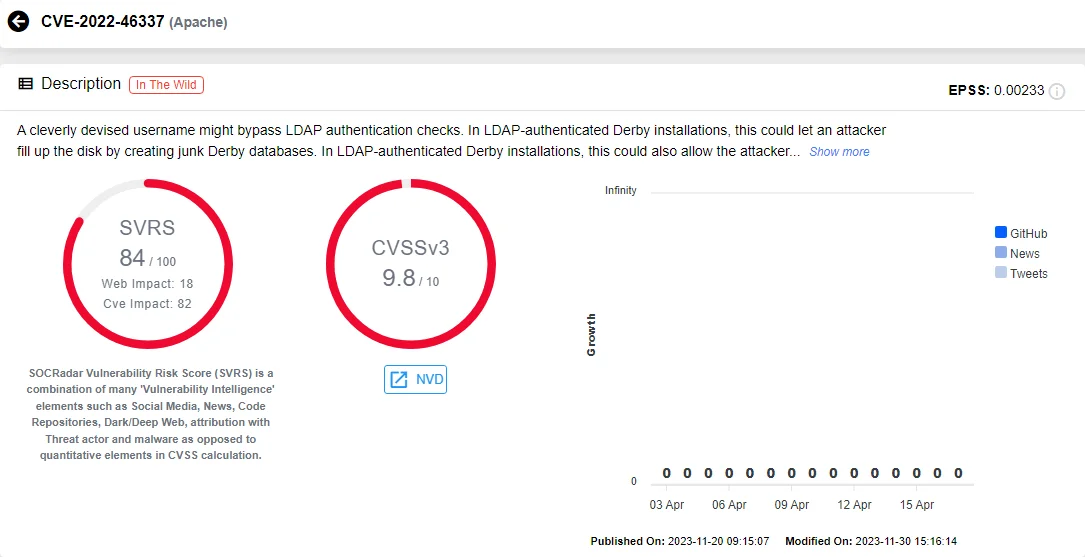
Vulnerability card of CVE-2022-46337 (SOCRadar Vulnerability Intelligence)
This vulnerability affects:
- Oracle Application Testing Suite – 13.3.0.1
- Oracle FLEXCUBE Private Banking – 12.1.0.0.0
- Oracle Enterprise Data Quality – 12.2.1.4.0
- Oracle Fusion Middleware MapViewer – 12.2.1.4.0
- Oracle Middleware Common Libraries and Tools – 12.2.1.4.0
- Oracle Documaker – 12.6, 12.7
- Oracle Retail Integration Bus – 16.0.3, 19.0.1
CVE-2019-13990 (CVSS: 9.8): The `initDocumentParser` function in `xml/XMLSchedulingDataProcessor.java` in Terracotta Quartz Scheduler up to version 2.3.0 is vulnerable to XXE (XML External Entity) attacks via a job description.
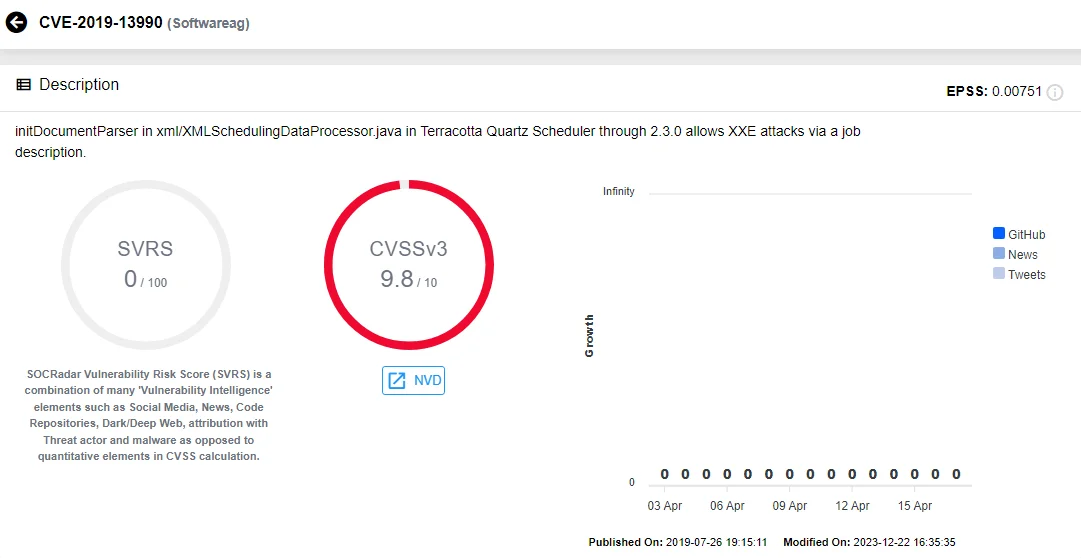
Vulnerability card of CVE-2019-13990 (SOCRadar Vulnerability Intelligence)
This vulnerability affects:
- Oracle Identity Manager – 12.2.1.4.0
- Oracle Internet Directory – 12.2.1.4.0
The following are the remainder of the critical vulnerabilities included in the Oracle April 2024 Critical Patch Update and the affected products:
- CVE-2024-1597 (CVSS: 9.8)
- Oracle Enterprise Data Quality – 12.2.1.4.0
- CVE-2022-1471 (CVSS: 9.8)
- Oracle SOA Suite – 12.2.1.4.0
- CVE-2022-45378 (CVSS: 9.8)
- Oracle Web Services Manager – 12.2.1.4.0
- CVE-2021-23369 (CVSS: 9.8)
- Oracle WebLogic Server – 12.2.1.4.0, 14.1.1.0.0
- CVE-2024-21082 (CVSS: 9.8)
- Oracle BI Publisher – 7.0.0.0.0, 12.2.1.4.0
- CVE-2023-38545 (CVSS: 9.8)
- PeopleSoft Enterprise PeopleTools – 8.59, 8.60, 8.61
- CVE-2022-46364 (CVSS: 9.8)
- Oracle Commerce Platform – 11.3.0, 11.3.1, 11.3.2
- CVE-2023-47100 (CVSS: 9.8)
- Oracle Communications Cloud Native Core Network Repository Function – 23.4.1
- CVE-2024-21071 (CVSS: 9.1)
- Oracle Workflow – 12.2.3-12.2.13
Use SOCRadar’s Vulnerability Intelligence to keep up with the latest developments and trends related to identified vulnerabilities; access comprehensive information about each identified vulnerability, including exploits and mentions.
SOCRadar’s Vulnerability Intelligence – CVE and hacker trends
Discover the capabilities of SOCRadar’s Vulnerability Intelligence with CVE Radar, a free feature available on SOCRadar Labs.
CVERadar on SOCRadar Labs
How to prevent the exploitation of vulnerabilities in Oracle WebLogic Server and other products?
It is highly recommended to review the Oracle advisory and apply the security patches issued within the April 2024 Critical Patch Update as soon as possible, while also ensuring that your systems are running actively supported Oracle products.
The Oracle April 2024 Critical Patch Update advisory provides detailed information on each vulnerability, affected products, and patch availability documents.
Proactively Monitor Your Digital Assets with SOCRadar
SOCRadar’s Attack Surface Management (ASM) module can assist you in monitoring digital assets, identifying potential vulnerabilities for your organization, and receiving critical security alerts.
SOCRadar’s Attack Surface Management, Company Vulnerabilities
Sign up for a free edition to test SOCRadar XTI’s full capabilities and take a proactive approach to a strong security posture.




































