CVSS v4.0 on the Horizon
[Update] November 2, 2023: See the subheading “FIRST Has Released CVSS v4.0: The Next Generation of Vulnerability Scoring”
The Common Vulnerability Scoring System (CVSS) is a widely used method for assessing security vulnerabilities in digital systems. Created by the U.S. National Infrastructure Advisory Council (NIAC) in 2005 and maintained by the Forum of Incident Response and Security Teams (FIRST). It provides a consistent approach for security professionals to prioritize risks. The current version CVSS v3.1 released in June 2019. It clarified and improved version 3.0 without introducing new metrics or values. It improved upon the clarity of concepts to improve the overall ease of use of the standard. It added the CVSS Extensions Framework and updated the Glossary of Terms.
Despite the tunings, CVSS v3.1 has faced criticism due to its complexity and lack of flexibility. In response, FIRST introduced CVSS v4.0 as a significant revision, aiming to simplify the scoring process and enhance accuracy. CVSS v4.0 is a significant revision that aims to simplify scoring, improve accuracy, and help organizations prioritize vulnerabilities effectively. We will cover its key features, improvements, comparison with CVSS v3.1, benefits, and adoption process.
The CVSS v4.0 Public Preview comment period commenced on June 8, 2023, and will continue until July 31, 2023. During this time, feedback from the community will be collected and thoroughly reviewed. By August 31, 2023, all received comments, questions, concerns, and other feedback will be carefully addressed. The target official publication date for CVSS v4.0 is set for October 1, 2023.
How Does CVSS v3.1 Work?
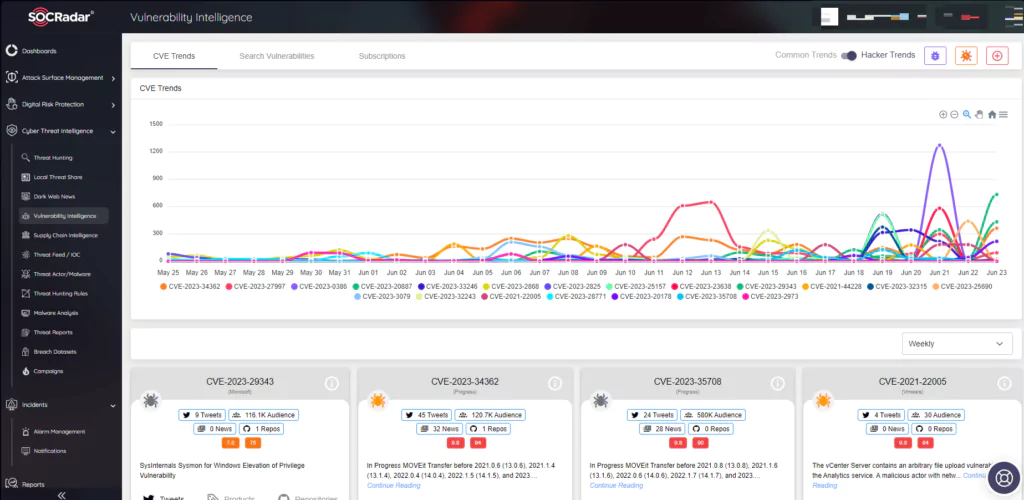
The CVSS scoring system utilizes three metric groups: base, temporal, and environmental metrics, to evaluate the severity of vulnerabilities and their impact on organizations.
Base Metrics: These metrics assess the nature of the vulnerability without considering temporal or environmental factors. They consist of exploitability metrics (Attack Vector, Attack Complexity, Privileges Required, and User Interaction) and impact metrics (Confidentiality Impact, Integrity Impact, and Availability Impact). The Scope metric assesses whether a vulnerability in one component can have an impact on resources outside its defined security scope.
Temporal Metrics: These metrics account for time-related factors that can influence vulnerability severity, such as the availability of patches or working exploits. They include Exploit Code Maturity, Remediation Level, and Report Confidence.
Environmental Metrics: Environmental Metrics in the CVSS allow analysts to tailor the CVSS score based on the significance of the affected IT asset to the organization. These metrics consider factors such as the presence of complementary or alternative security controls, as well as the importance of Confidentiality, Integrity, and Availability of the asset.
To calculate a CVSS score, the base, temporal, and environmental metrics are combined using a specific formula. The resulting score falls on a scale of 0 to 10, with higher scores indicating more severe vulnerabilities. The scores are categorized into four severity levels: Low (0-3.9), Medium (4-6.9), High (7-8.9), and Critical (9-10).
What are the Downsides of CVSS v3.1?
CVSS Base Score as the primary input to risk analysis: One of the drawbacks of CVSS v3.1 is the heavy reliance on the CVSS Base Score as the primary input for risk analysis. This score alone may not provide a comprehensive understanding of the actual risk associated with a vulnerability, as it lacks real-time threat intelligence and contextual details.
Prevalence of high scores: Scores published by vendors often tend to be in the High or Critical range (7.0+), potentially leading to an inflated perception of risk. This may not accurately reflect the true severity of vulnerabilities.
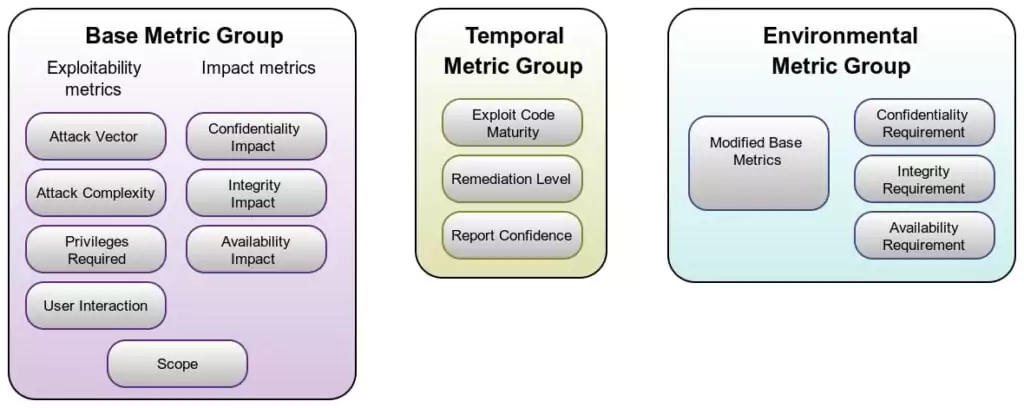
SOCRadar Extended Threat Intelligence has already addressed these issues mentioned above with its SOCRadar Vulnerability Risk Scoring (SVRS). You can use SVRS to prioritize higher-risk vulnerabilities. SVRS is a unique scoring system developed by SOCRadar that takes into account a combination of qualitative elements from various sources, such as social media, news, code repositories, dark web, and attribution with threat actors and malware. This differs from the traditional quantitative approach used in the Common Vulnerability Scoring System (CVSS) calculation.
Limited representation of non-I.T. systems: CVSS v3.1 is primarily designed for assessing vulnerabilities in I.T. systems. As a result, it may not adequately represent the unique considerations of other domains, such as health, human safety, and industrial control systems.
Insufficient granularity: CVSS v3.1 lacks fine granularity, as there are fewer than 99 discrete CVSS scores in practice. This limited granularity may not effectively differentiate between vulnerabilities with nuanced differences in severity.
Limited impact of Temporal Metrics: The Temporal Metrics in CVSS v3.1 do not have a significant impact on the final CVSS score. This limitation diminishes the ability to account for time-related factors, such as the availability of patches or the maturity of exploit code.
The complexity of the scoring formula: The formula used to calculate CVSS scores in v3.1 can be perceived as overly complicated and counterintuitive. This complexity may impede effective communication and decision-making surrounding vulnerability severity.
How Will CVSS v4.0 Address These Downsides?
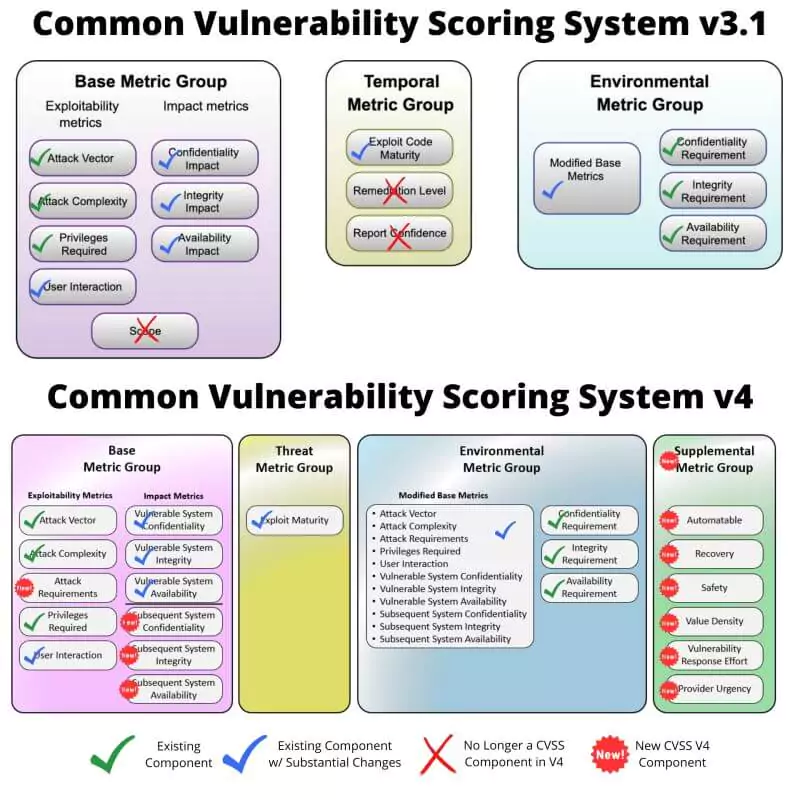
Addressing the limitations required drastic changes. The revised CVSS framework underwent significant changes by modifying existing components, removing certain components, and introducing new components.
The Base Metric Group in the new version of CVSS represents the inherent characteristics of a vulnerability that remain constant over time and across user environments. It consists of two sets of metrics: Exploitability Metrics and Impact Metrics. Exploitability Metrics assess the ease and technical means of exploiting the vulnerability, while Impact Metrics evaluate the direct consequences of a successful exploit. The vulnerable system refers to the entity susceptible to the vulnerability, while subsequent systems are those affected by the exploit. CVSS v3.0 introduced the ability to measure impacts beyond the vulnerable system called “Scope.” However, it has been retired and expanded into two sets, which will be discussed later on.
The Threat Metric Group captures vulnerability characteristics related to a threat, which may change over time.
The Environmental Metric Group considers the specific environment of a user, including security controls and the relative importance of the vulnerable system.
The Supplemental Metric Group provides additional contextual information and attributes of a vulnerability. These metrics do not directly impact the final CVSS score, allowing organizations to assign importance and evaluate the impact of each metric based on their system.
We briefly went over each metric group, but there are more detailed changes regarding the framework.
Shift in Nomenclature
To emphasize that CVSS is not solely based on the Base Score, CVSS v4.0 has undergone a shift in nomenclature. The new nomenclature includes the following:
CVSS-B (CVSS Base Score): This represents the traditional Base Score, which assesses the severity of a vulnerability based on its intrinsic characteristics.
CVSS-BT (CVSS Base + Threat Score): This incorporates the Base Score along with additional metrics related to the threat landscape. By considering real-time threat information, the CVSS-BT score provides a more comprehensive assessment of the risk posed by a vulnerability.
CVSS-BE (CVSS Base + Environmental Score): This combines the Base Score with metrics that allow customization based on the organization’s specific environment. The CVSS-BE score considers factors such as the presence of security controls and the importance of Confidentiality, Integrity, and Availability to the organization.
CVSS-BTE (CVSS Base + Threat + Environmental Score): The CVSS-BTE score encompasses all available metrics, including the Base Score, threat-related metrics, and environmental metrics. By incorporating a comprehensive set of factors, the CVSS-BTE score provides the highest level of quality in vulnerability assessments.
The inclusion of additional metrics in the scoring process allows for a more thorough and refined assessment of vulnerabilities. The more metrics used, the higher the quality of the assessment, as it captures a broader range of information and contextual factors. This shift in nomenclature highlights the importance of leveraging multiple metrics to enhance the accuracy and effectiveness of CVSS scoring.
Attack Requirements (AT), A New Base Metric
A new Base Metric called Attack Requirements (AT) has been introduced in response to the problem with the existing Attack Complexity (AC) values. The current AC in version 3.x values of “low” and “high” fail to capture the significant differences between various conditions that are currently categorized as “high” complexity.
To address this issue, the AC definition is split into two separate metrics:
Attack Complexity: This metric reflects the complexity involved in engineering an exploit to evade or circumvent defensive or security-enhancing technologies.
Attack Requirements: This metric reflects the prerequisite conditions of the vulnerable component that enable the attack to occur.
By introducing these two distinct metrics, the revised approach aims to provide a more accurate assessment of the exploit complexity and the specific requirements for an attack.
Finer Granularity
The CVSS v4.0 introduces an update to the Base Metric “User Interaction (UI)” that provides greater precision in evaluating the interaction between a user and a vulnerable component. The metric includes three specific values:
None (N): The vulnerability can be exploited without any user interaction except for the attacker’s involvement.
Passive (P): Successful exploitation requires limited, involuntary interaction by the targeted user with the vulnerable component and the attacker’s payload.
Active (A): Successful exploitation necessitates specific, conscious interactions by the targeted user with the vulnerable component and the attacker’s payload or the active subversion of protection mechanisms.
These specific value descriptions aim to enable a more accurate assessment of the user’s involvement in the exploit process.
The Scope is Retired
CVSS v4.0 retires the Scope (S) metric due to issues of inconsistent scoring and lack of understanding. To address this, the Impact Metrics have been expanded into two sets: Vulnerable System Confidentiality (VC), Integrity (VI), Availability (VA), and Subsequent System(s) Confidentiality (SC), Integrity (SI), Availability (SA). This change aims to improve the assessment of impacts on the vulnerable system and subsequent systems, providing a more precise and comprehensive evaluation in CVSS v4.0.
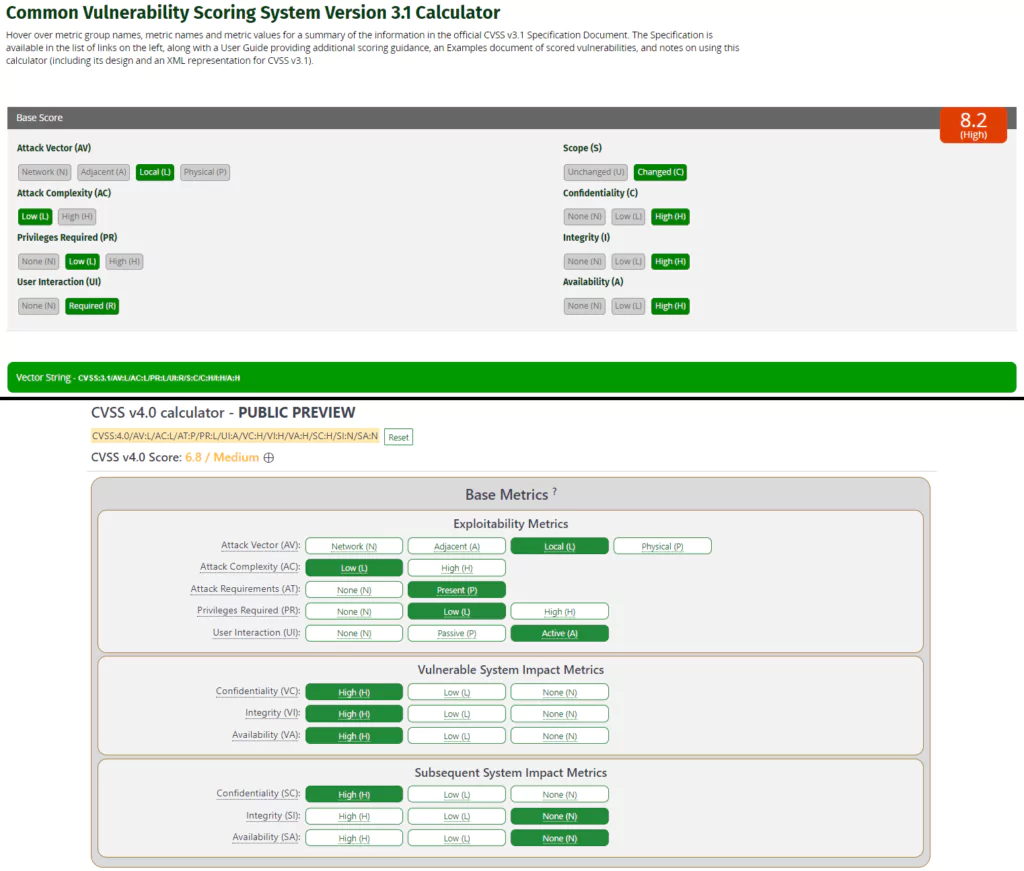
Above, we look at a hypothetical vulnerability in the most barebones terms. Here are the vector strings:
CVSS:3.1/AV:L/AC:L/PR:L/UI:R/S:C/C:H/I:H/A:H
CVSS:4.0/AV:L/AC:L/AT:P/PR:L/UI:A/VC:H/VI:H/VA:H/SC:H/SI:N/SA:N
In the scoring of the hypothetical vulnerability, the difference between them is the scope and its correspondence in the CVSS v4.0. According to the scoring of the CVSS v3.1, the vulnerability comes to a high score of 8.2. However, thanks to the retiring and expansion of the Scope metric, we can see that a vulnerability with the Subsequent System Impact of Confidentiality comes to a medium score of 6.8. Before, it was not possible to set these metrics separately within the context of Scope.
Temporal Metric to Threat Metric, A Renaming
In the CVSS v4.0, there are simplifications made to the Threat Metric Group. The “Temporal” Metric Group has been renamed to “Threat,” while the metrics Remediation Level (RL) and Report Confidence (RC) have been retired. Additionally, the metric “Exploit Code Maturity” is now called “Exploit Maturity” and has the following options to consider:
- Not Defined (X) – the metric has not set
- Unreported (U) – no known available exploit or PoC
- PoC (P) – PoC is available but no exploit used in real-world scenarios
- Attacked (A) – real-world attacks have been observed
These changes to the metric highlight that the importance of official patches or workarounds has dropped. This can be due to the rise of social media usage, in which news of a vulnerability sprawls rapidly and reduces the time for confirmation and patches.
Supplemental Metric Group
One of the biggest changes in the CVSS v4.0 is the introduction of the Supplemental Metric Group. It brings the ability to define new metrics that describe and measure additional extrinsic attributes of a vulnerability. These Supplemental Metrics are optional and allow the consumer the flexibility to assign locally significant importance to the metrics and their values.
It’s important to note that no metric within the Supplemental Metric Group will have a numerical impact on the final calculated CVSS score. Instead, organizations have the discretion to assign importance and effective impact to each metric or combination of metrics, determining their influence on the final risk analysis. The metrics and values in the Supplemental Metric Group simply convey additional extrinsic characteristics of the vulnerability itself.
Supplemental Metrics introduced in CVSS v4.0 include Automatable, Recovery, Safety, Value Density, Vulnerability Response Effort, and Provider Urgency. These metrics provide further context and information to aid in decision-making and additional actions related to the vulnerability. For a detailed explanation, you can visit the specification document here.
FIRST Has Released CVSS v4.0: The Next Generation of Vulnerability Scoring
The Forum of Incident Response and Security Teams (FIRST) has officially announced the release of CVSS v4.0, marking the next generation of its Common Vulnerability Scoring System standard. This significant development comes eight years after the introduction of CVSS v3.0 – which was released precisely in June 2015 – and introduces several notable improvements.

CVSS v4.0 offers enhanced granularity in base metrics, eliminating ambiguity in downstream scoring and simplifying threat metrics. FIRST states that these enhancements make it more effective in assessing security requirements tailored to specific environments and evaluating compensating controls.
The latest standard incorporates new supplemental metrics for vulnerability assessment. Here’s the new Supplemental Metric Group:
- S- Safety
- A – Automatable (Wormable)
- R – Recovery (Resilience)
- V – Value Density
- RE – Vulnerability Response Effort
- U – Provider Urgency
Additionally, the introduction of fresh nomenclature, including CVSS-B (Base), CVSS-BT (Base + Threat), CVSS-BE (Base + Environmental), and CVSS-BTE (Base + Threat + Environmental), underscores that CVSS encompasses not just the Base score but various combinations of metrics.
To explore the complete set of changes and features within CVSS v4.0, visit FIRST’s website.
Conclusion
The CVSS v4.0 introduces significant enhancements to overcome the limitations and criticisms of its previous version. These improvements result in improved clarity, flexibility, and a more precise representation of real-world risk, empowering security professionals to prioritize vulnerabilities and allocate resources for mitigation more effectively.
While CVSS is widely adapted and will be in the future, organizations should consider alternative options that elaborate on the CVSS. SOCRadar Extended Threat Intelligence, with its Vulnerability Intelligence module, provides an extensive view of the vulnerability landscape. With its proprietary features like SVRS, which builds on the CVSS, you can stay ahead of the curve.