
Dark Peep #10: The Cold of Russia 2.0
Gear up, digital explorers! You’re about to dive into the latest edition of “Dark Peep #10” where we decode the mysteries of the cyber universe with a sprinkle of fun and a dash of daring. Imagine donning your virtual detective hat as we embark on a journey through the digital jungle, uncovering secrets, dodging cyber traps, and discovering hidden treasures of information.

Fig.1. A scene depicting cyber threat actors sitting around a fire on a snowy day (generated using OpenAI’s DALL-E)
In this action-packed issue, we navigate the twists and turns of the LockBit–Cl0p saga, peek behind the curtains of the dark web’s newest haunts, and unravel the tales of cyber alliances and digital duels. Each story is like a level in the ultimate cybersecurity game, challenging your perceptions and inviting you to solve the puzzle of what’s really happening behind the screen. We’ve got intrigue, we’ve got drama, and yes, we’ve got the inside scoop on the cyber shenanigans that could rival any spy thriller.
The LockBit-Cl0p: The Alleged Attack on Russian Company?
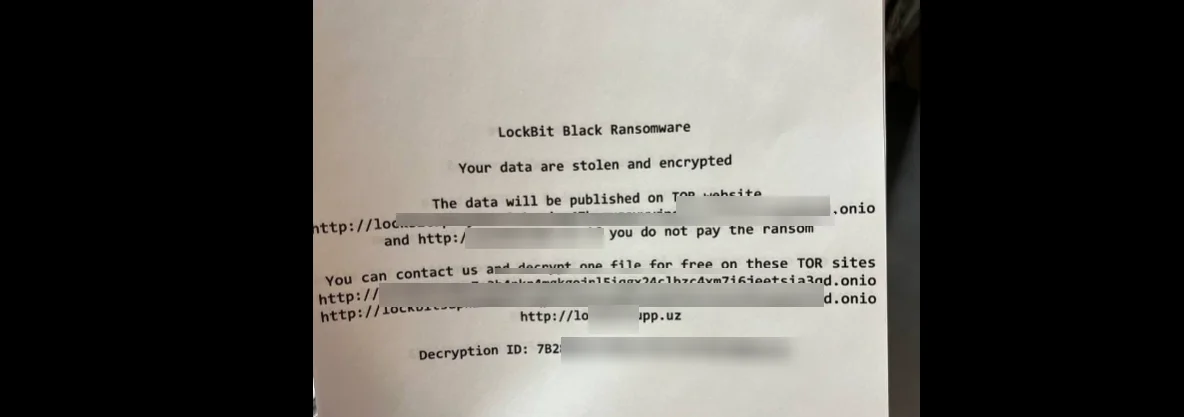
Fig. 2. Ransom note allegedly belonging to LockBit
The cold dawn of January 2023 witnessed a ripple in the cybercrime scene with an alleged ransomware attack on AN-Security, a Russian firm. This incident, attributed to LockBit ransomware, took a twist when the supposed attacker boasted on the RAMP forum, breaking its rule against targeting Russian entities. This breach of conduct led to their immediate ban, sparking debates within the cyber community.
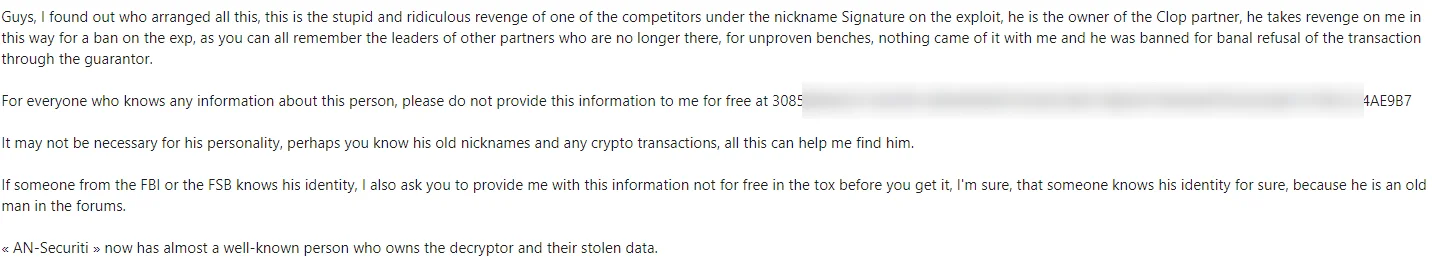
Fig. 3. LockBitSupp’s statement
LockBitSupp, identified as LockBit’s representative on the XSS forum, later claimed that the attack was the work of an individual named Signature, allegedly linked to the Cl0p ransomware group. According to LockBitSupp, Signature used a leaked LockBit builder for the attack, aiming to smear LockBit by falsely implicating them in violating cybercrime’s norms against Russian targets.
A New Dangerous Game from Old Player
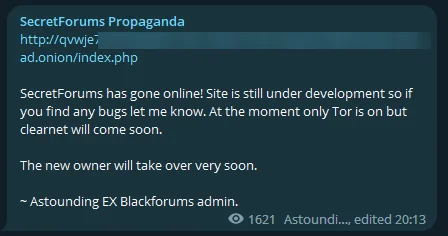
Fig. 4. SecretForums launch announcement
A threat actor known as Astounding, the former admin of Blackforums, has launched a new hacker forum into the dark web’s secretive corridors with SecretForums. Still in its nascent stages and currently only accessible via Tor, the site is a beacon for threat actors and insiders of the cyber underworld. Astounding’s announcement emphasizes the platform’s ongoing development and openness to community feedback, hinting at a future expansion to Clearnet accessibility.
Shared Targets, Shared Methods?
SiegedSec, a threat actor group with a notorious reputation, announced their latest alleged exploit: a breach into a healthcare company, acquiring 80GB of sensitive client and staff data. Despite a seemingly playful tone in their communication, the gravity of their actions underlines a stark reminder of the malicious intent that drives such groups.
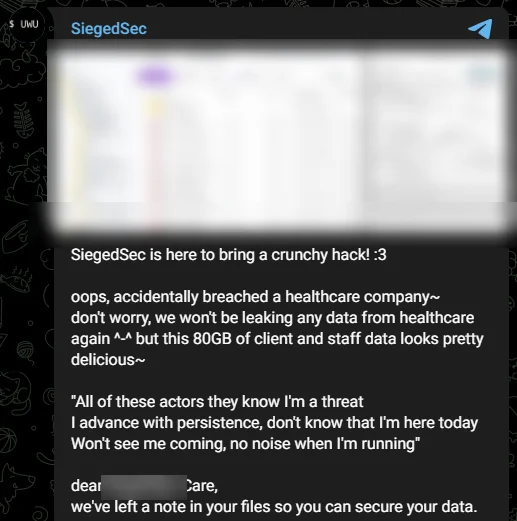
Fig. 5. SiegedSec’s statement
In their message, disseminated via their Telegram channel, SiegedSec articulated a faux pas of ethics, claiming they would abstain from leaking any healthcare data “again.” This assurance, however, does little to mitigate the potential harm and violation of privacy such a breach entails.
The group claimed that they left a note for the healthcare company system, mockingly suggesting they had merely intended to highlight security flaws. On the same day, ALPHV/BlackCat added the healthcare company to its list of victims.
The simultaneous targeting by both ALPHV/BlackCat and SiegedSec could suggest they exploited a shared vulnerability within a healthcare company’s network or utilized similar cyber tools. Trading information on vulnerabilities or direct system access in the dark web’s underground markets might have inadvertently guided both groups to the same target. However, confirming whether both accessed the same data or used overlapping infrastructures is challenging without detailed forensic analysis.
Reshuffling in Pro-Russian Cyber Ranks: KillNet 2.0 and Just Evil
January saw a significant shift among pro-Russian threat actors, leading to the formation of KillNet 2.0 and a new group, Just Evil, by KillMilk. KillNet 2.0 emerged as an international, decentralized threat group, distancing itself from financial motives and focusing on an ideological mission.

Fig. 6. Announcement of KillNet 2.0
This move directly responded to perceptions of the original KillNet becoming too commercially driven under Deanon Club’s leadership. Concurrently, KillMilk launched Just Evil threat group, aiming to maintain influence in the cyber threat landscape while potentially addressing the criticisms of KillNet’s commercialization. These developments signal evolving dynamics within pro-Russian cyber threats, highlighting a blend of ideological and strategic realignments.
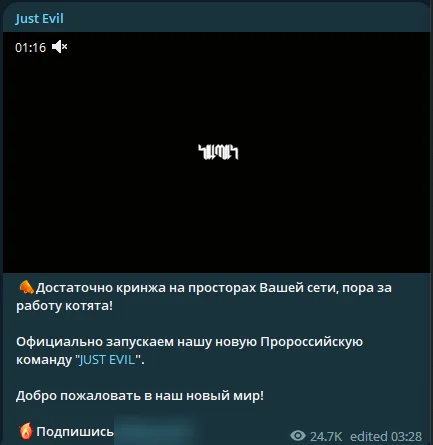
Fig. 7. Announcement of Just Evil
Emergence of a Russian Hacktivist Alliance
A formidable new Russian hacktivist alliance has emerged, signaling a consolidation of cyber forces with a broad and concerning target scope. Initially announcing a united front against Ukraine, the alliance’s ambitions evidently extend beyond a singular focus. Recent allegations include DDoS attacks on Finnish systems, hinting at a broader geopolitical agenda that may encompass additional NATO member states.

Fig. 8. Members of the Alliance
The coalition, comprising groups like NoName057(16), The National Cyber Army, 22C, PHOENIX, Federal Legion, UserSec, CyberDragon, and NETWORK (15), represents a significant escalation in coordinated cyber activities. This alliance underscores the evolving threat landscape and the strategic use of cyber operations in geopolitical conflicts.
LockBitSupp’s Banishment
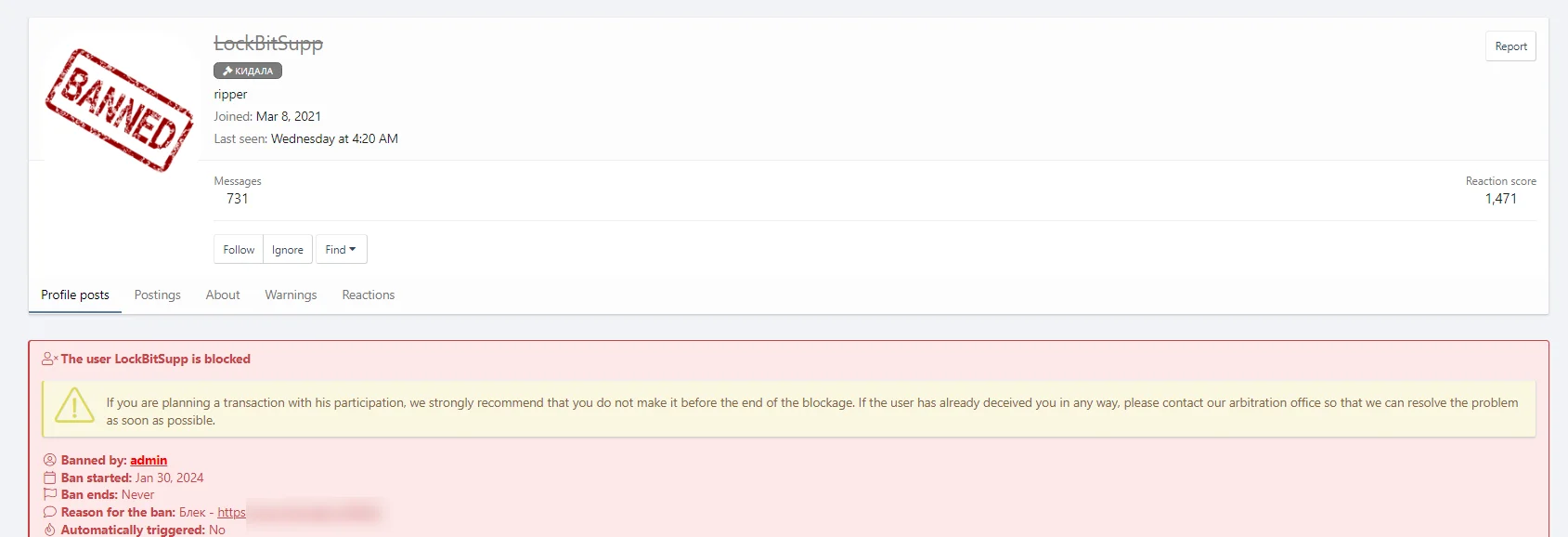
Fig. 9. LockBitSupp’s XSS Profile
LockbitSupp faced a ban from the XSS forum after a breach of trust. Allegations surfaced that LockBit, after obtaining network access for encryption from another threat actor and securing a ransom, sidestepped the agreed commission. Instead, they compensated only for the network access. Following the ban on XSS forum, Lockbit profile has also been banned from Exploit.
Conclusion: Illuminating the Winter Shadows with SOCRadar
As the frosty chapter of this Dark Peep edition closes, we’re reminded that the Dark Web, much like a winter landscape, is ever-changing and full of hidden depths. SOCRadar emerges as the essential guide through this icy realm, not just watching but revealing the intricate patterns beneath the surface.
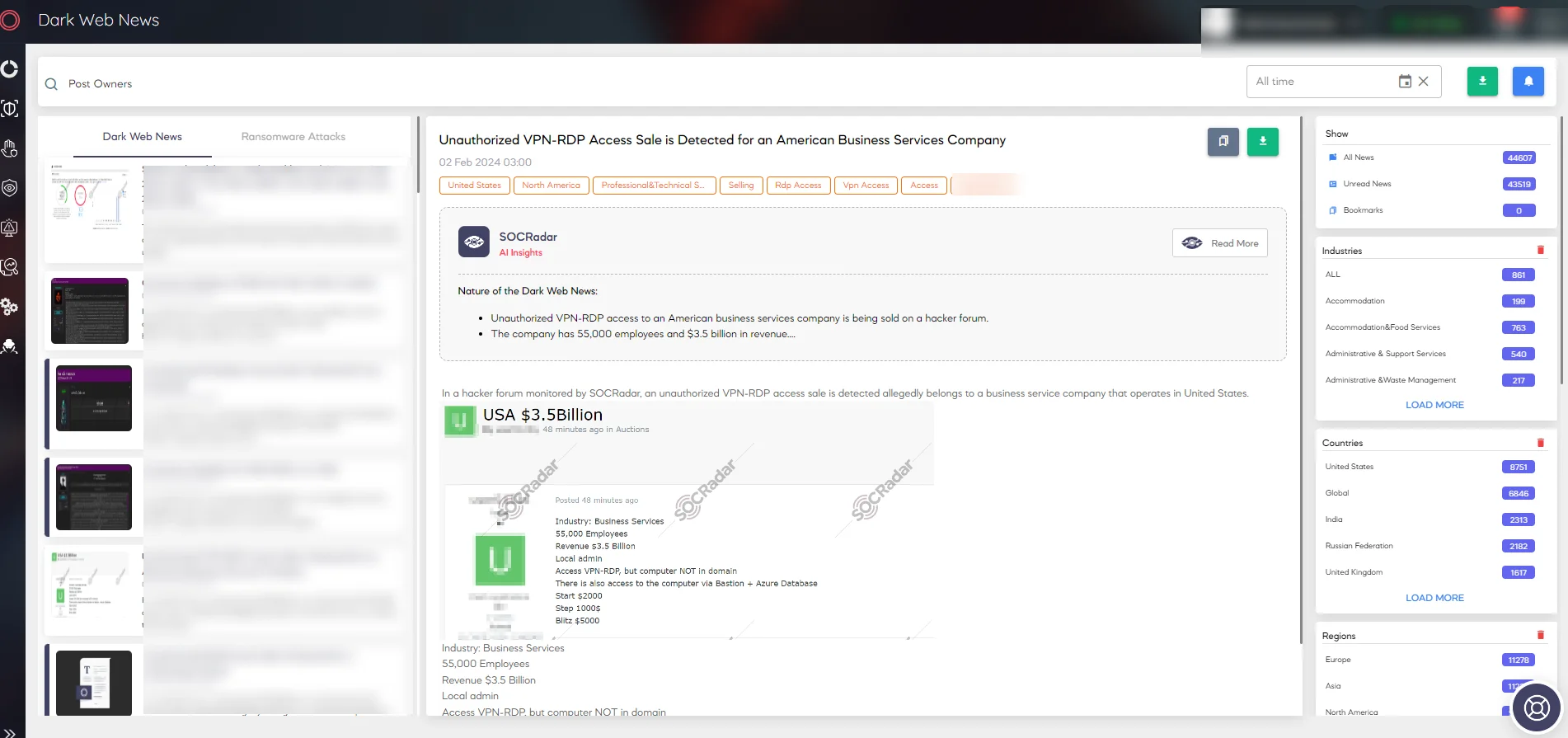
SOCRadar Dark Web News
It’s the warmth of insight in the cold, dark expanse, turning the daunting into the navigable. With SOCRadar, organizations find their path illuminated, ready to face the chill of cyber threats with confidence. In the cold digital winter, SOCRadar is the beacon of knowledge that turns the long night into dawn.


































