
Dark Web Data Breaches: PT Nap Info Lintas Nusa, LocalPlace, Opensoft Affected
The SOCRadar Dark Web Team has detected multiple new posts on hacker forums, alleging significant data breaches across various industries. These incidents involve telecommunications, online reservation, technology, e-commerce, and media companies, including PT Nap Info Lintas Nusa, LocalPlace, Opensoft, an Amazon partner, and a company in Uruguay.
Sensitive data, system access, and credentials are being offered for sale, highlighting severe cybersecurity vulnerabilities and raising concerns about the potential misuse of compromised information.
Receive a Free Dark Web Report for Your Organization:
Alleged Database of PT Nap Info Lintas Nusa is on Sale
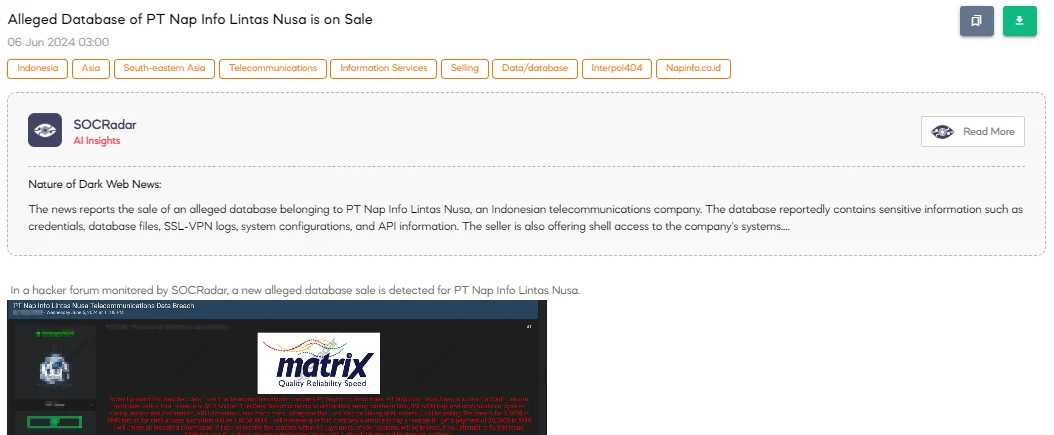
The SOCRadar Dark Web team detected in a hacker forum that a threat actor claims to be selling an alleged database of PT Nap Info Lintas Nusa, a telecommunications company located in Jakarta, Indonesia. The threat actor claims the breach includes credentials, various database files, SSL-VPN logs and configurations, system configurations and information, API information, and more.
Additionally, shell access is also being sold. The threat actor demands $1,300 in XMR (Monero) for the database and $1,800 in XMR for shell access alone. They have also issued a ransom demand of $20,000 in XMR
Alleged Database of LocalPlace Leaked
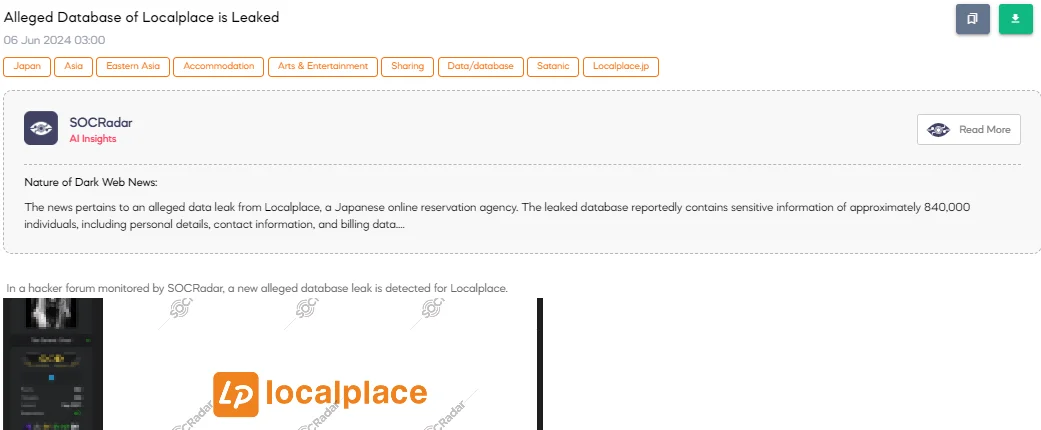
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have leaked a database of LocalPlace, a Japanese online reservation agency. The alleged leak includes 839,999 lines of compromised data from May 2024.
The compromised data purportedly contains client IDs, company forms, company names, full company info, phone numbers, full names, email addresses, billing information, and other sensitive details.
Database of Opensoft is Allegedly Leaked
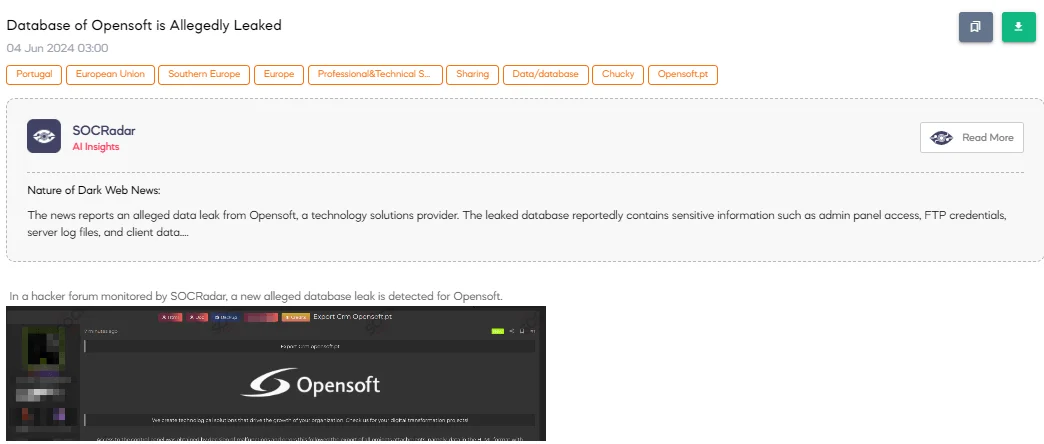
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor claims to have leaked a database of Opensoft, a Portuguese tech company established in 2001, specializing in software engineering and technological consultancy. The alleged leak includes access to various admin panels, FTP access, server log files, and project attachments in HTML format with screenshots.
The threat actor claims that access was obtained due to malfunctions and errors, allowing the export of extensive data. This information could potentially be used to find admin panels of clients, databases, and other sensitive information.
Alleged Data of Amazon Partner on Sale
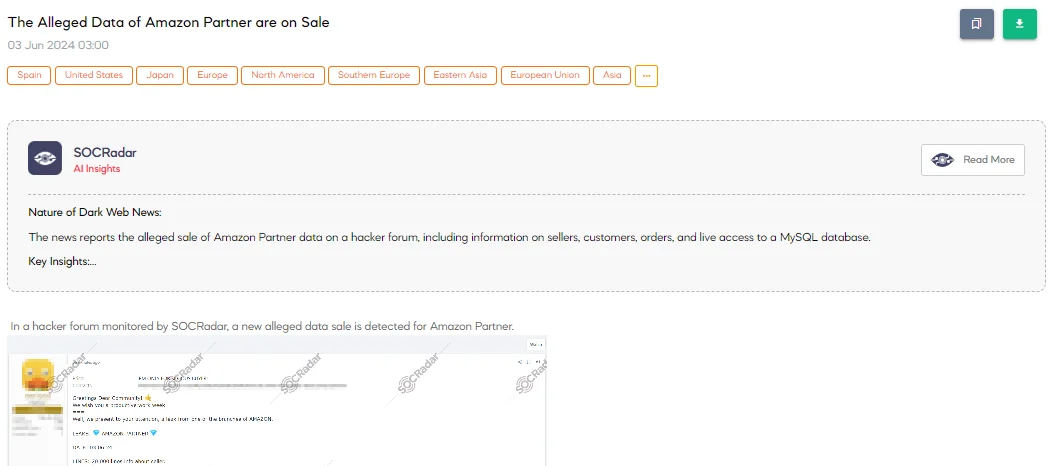
The SOCRadar Dark Web Team uncovered a post in a hacker forum that a threat actor claims to be selling data allegedly leaked from an Amazon partner.
The threat actor’s post advertised the data with the following details:
- Price available via private message for serious buyers
- Leak includes 20,000 lines of seller information
- Data includes over 1 million records of customers, shipment orders, live orders, and sellers
- Live access to a MySQL database if needed
- Data spans multiple countries, including the USA, Japan, and Spain
According to the post, the exposed data contains sensitive information such as Amazon order IDs, recipient names, shipping addresses, phone numbers, account codes, product details, and financial information, including prices, shipping costs, and estimated profits. Additionally, it includes seller information and conditions.
Unauthorized RDP Access Sale is Detected for a Uruguayan Media & Internet Company
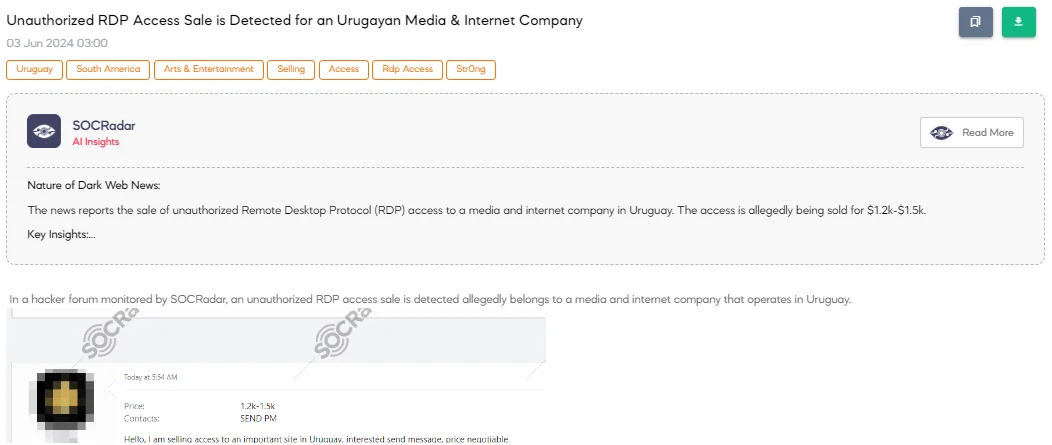
The SOCRadar Dark Web Team detected a post in a hacker forum that a threat actor is selling unauthorized RDP access allegedly belonging to a media and internet company operating in Uruguay.
The threat actor claims the access is to an important site in Uruguay and is selling it for a negotiable price between $1.2k and $1.5k. The access type is Remote Desktop Protocol (RDP) Windows, and the company’s revenue is stated to be $15 million. The seller is offering DA (Domain Administrator) credentials and accepts escrow for the transaction.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































