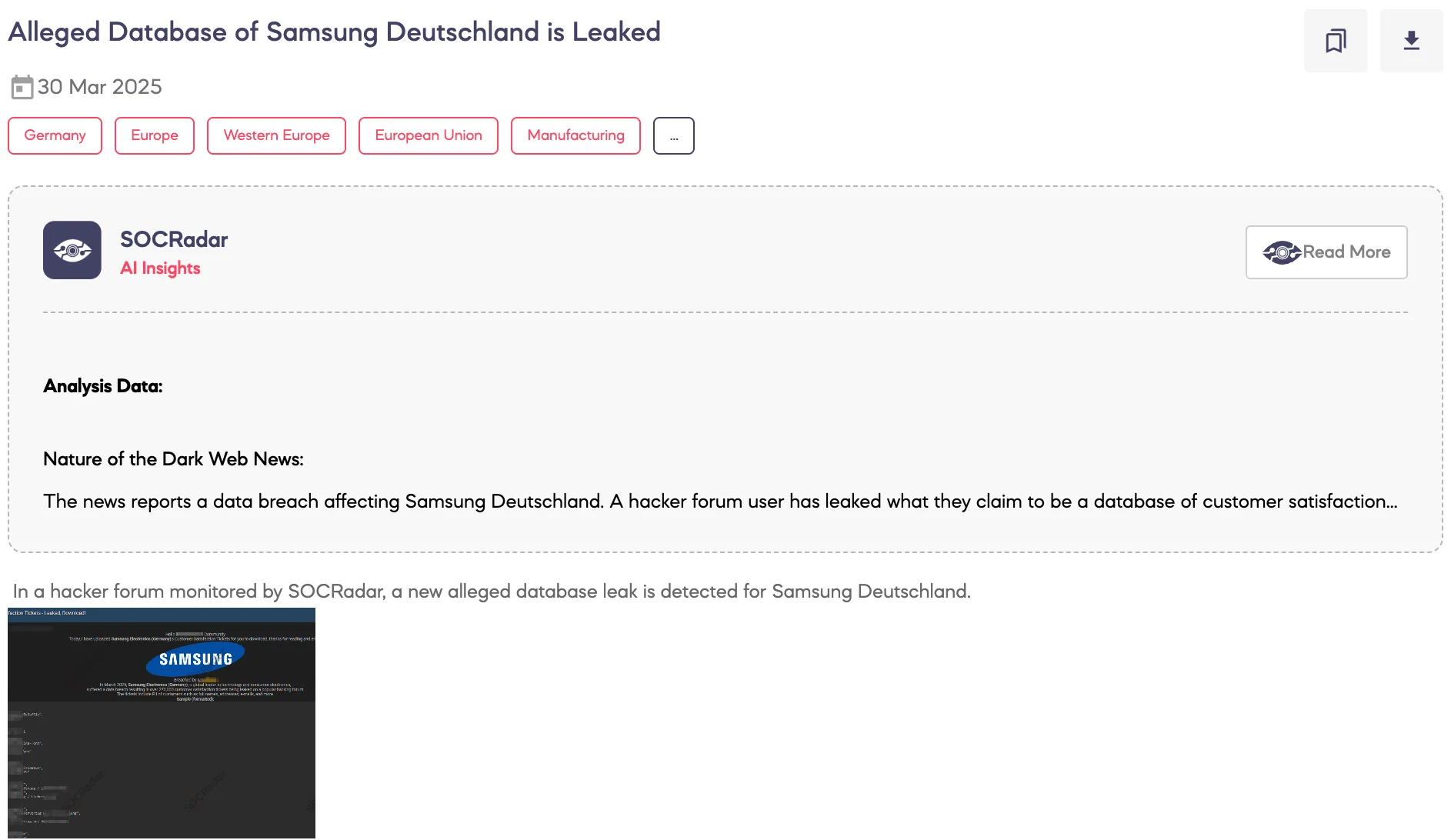
Dark Web Sees New Market Launch, Credit Card and VPN Access Sales
SOCRadar’s Dark Web Team has identified several new threats emerging on hacker forums in the last week. Highlights include the promotion of a newly launched illicit database market covering a broad range of sectors, and the alleged sale of sensitive data tied to Spanish fintech firm Aplazame. Additional discoveries include unauthorized VPN access linked to a U.S. telecom equipment company, leaked source code from the University of Sydney, and the sale of 1,400 South Korean credit card records.
Receive a Free Dark Web Report for Your Organization:
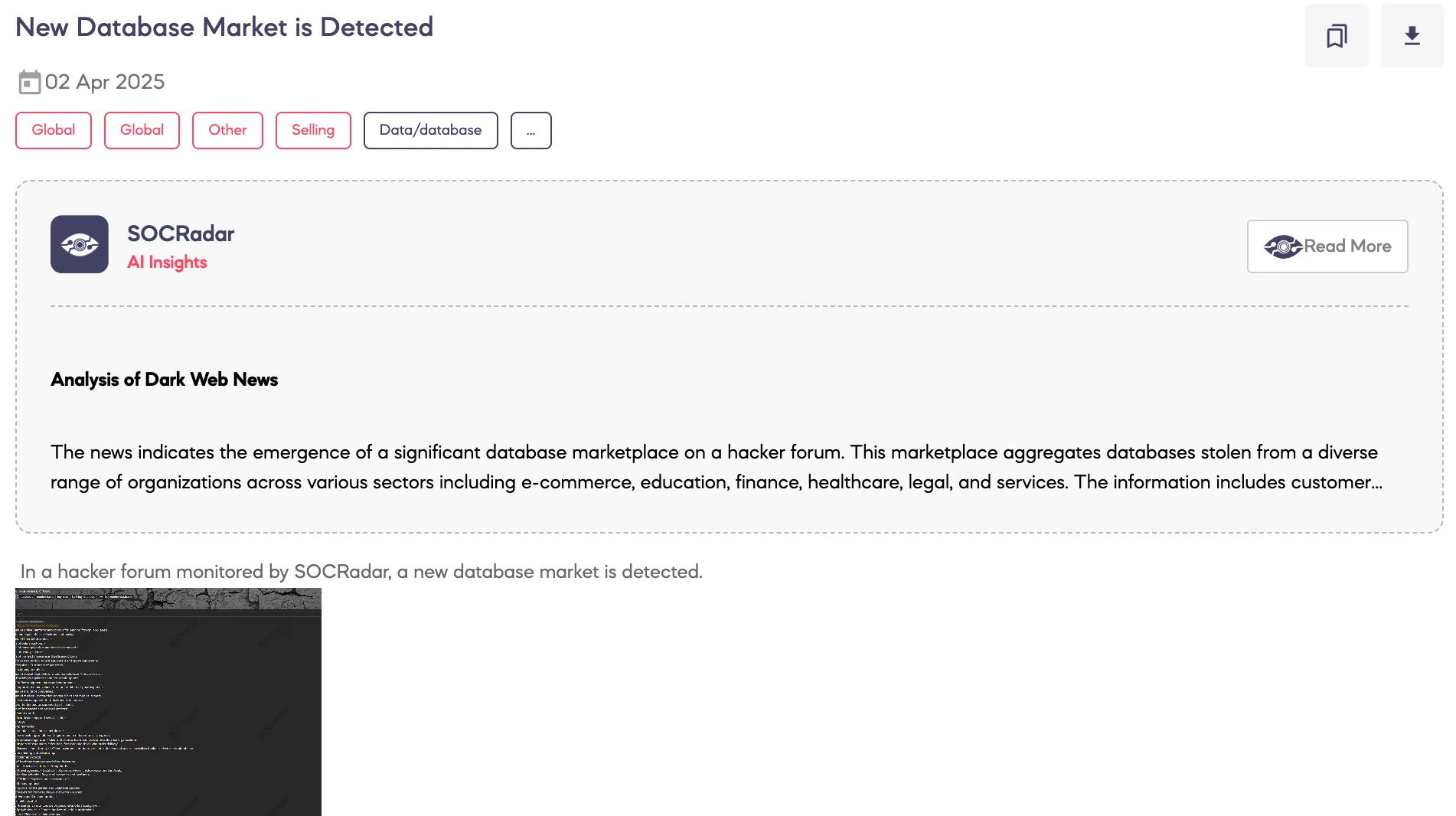
New Database Market is Detected
SOCRadar Dark Web Team detected a post on a hacker forum where a new illegal database market is being promoted. According to the threat actor’s statements, the market offers a wide range of consumer and client data covering individuals and businesses from multiple industries and sectors.
The datasets allegedly include information on customers of banks, internet providers, online learning platforms, beauty salons, healthcare providers, insurance companies, real estate agencies, e-commerce platforms, travel agencies, and more. The actor also lists data from freelancers, job seekers, online shoppers, and users of delivery, marketing, and financial services.
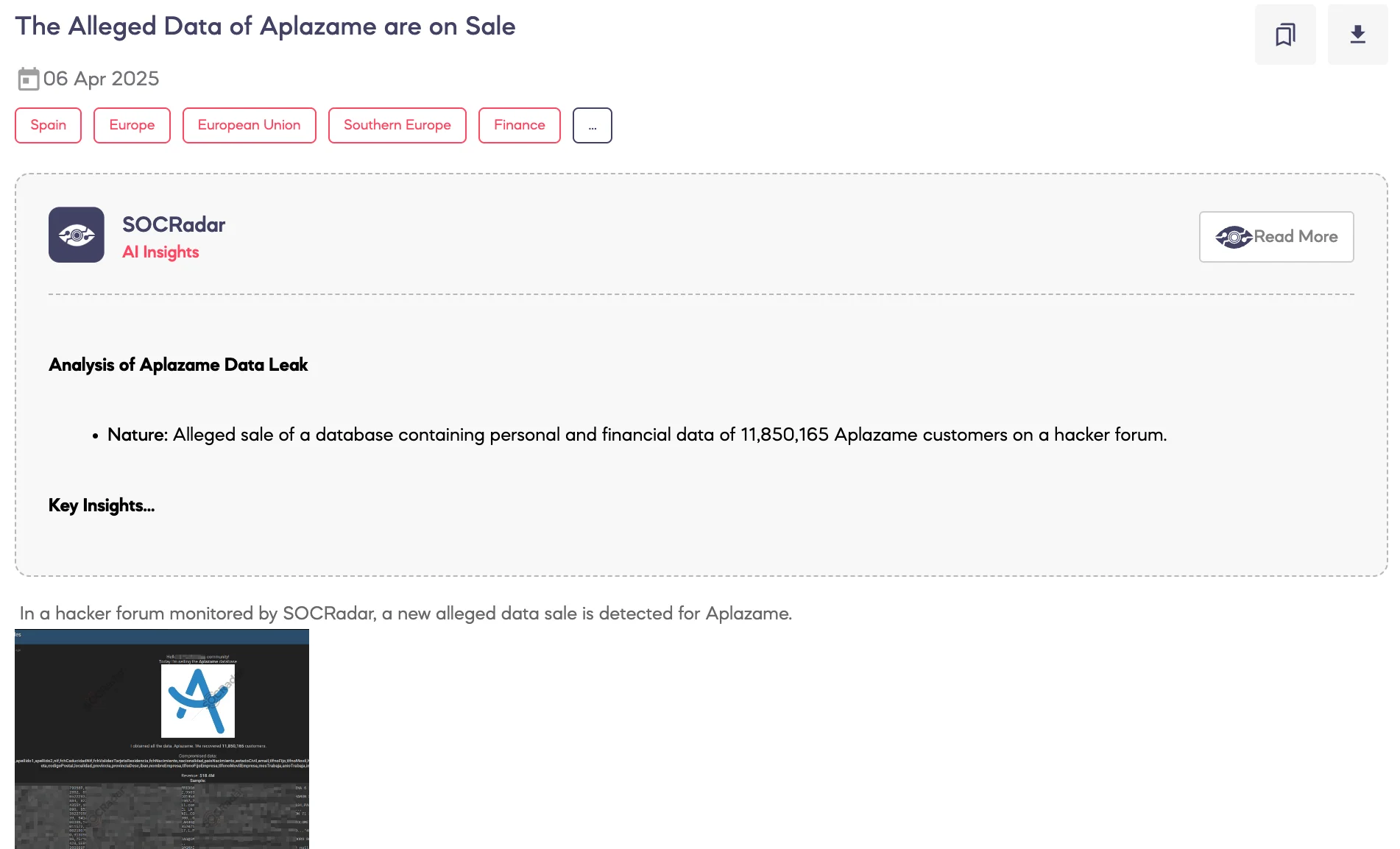
Alleged Data of Aplazame are on Sale
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling a database allegedly belonging to Aplazame, a Spanish consumer financing company. According to the threat actor’s statements, the dataset contains information on 11,850,165 individuals.
The exposed data reportedly includes extensive Personally Identifiable Information (PII) such as full names, NIF (Número de Identificación Fiscal), dates of birth, nationality, marital status, contact information, residential and employment details, IBANs, income levels, and social security records.
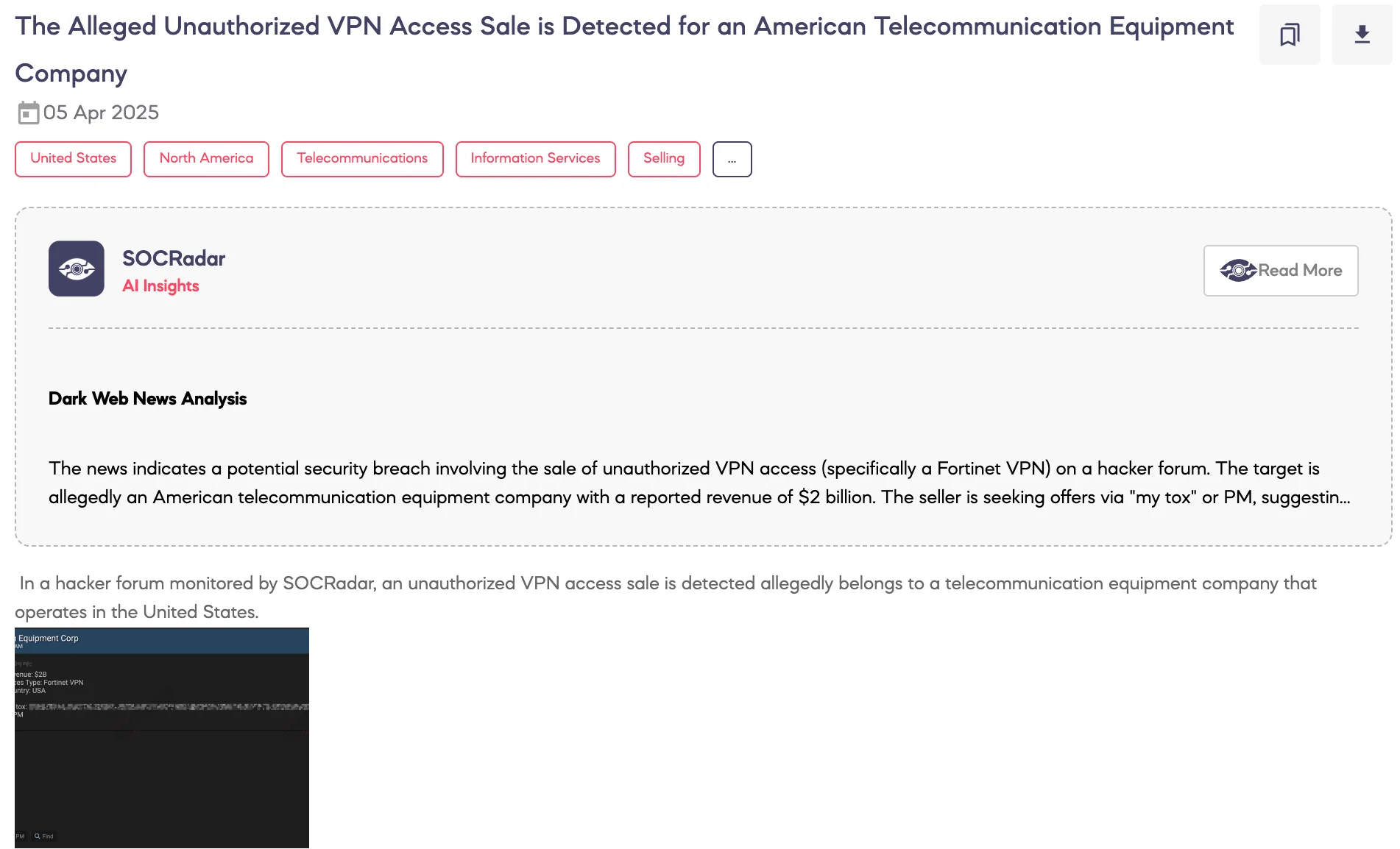
Alleged Unauthorized VPN Access Sale is Detected for an American Telecommunication Equipment Company
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling unauthorized VPN access allegedly belonging to a U.S.-based telecommunications equipment company with an estimated annual revenue of $2 billion. According to the threat actor’s statements, the access is through a Fortinet VPN, and the sale is being facilitated via Tox or private messaging.
Alleged Data of The University of Sydney are Leaked
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to have leaked source code and repository data allegedly associated with the University of Sydney. According to the threat actor’s statements, the data was obtained through access to a GitHub token linked to the university’s domain. The post references various internal repositories and includes partial file names suggesting the presence of PHP scripts, login pages, server configuration files, and version details.
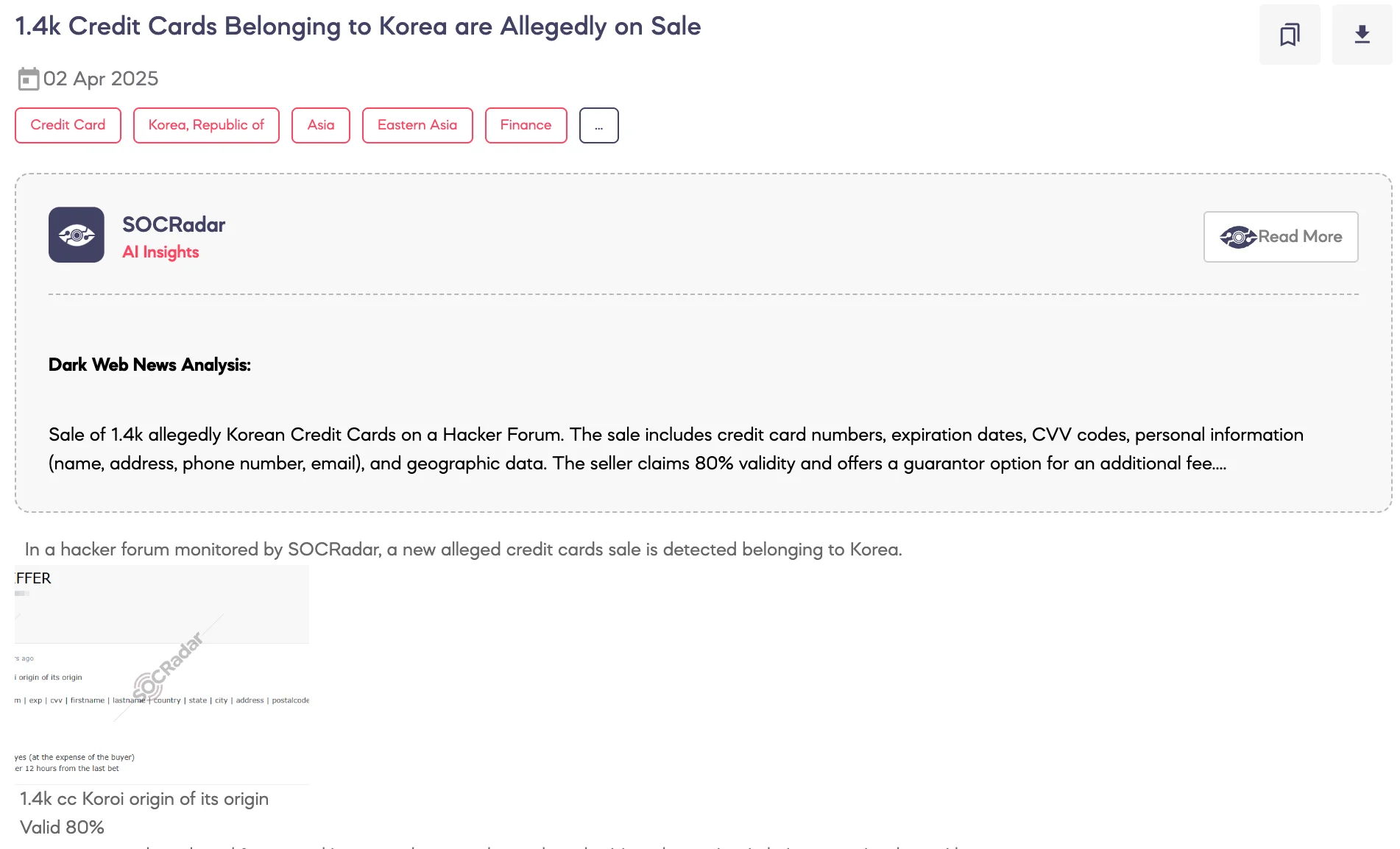
1.4K Credit Cards Belonging to Korea are Allegedly on Sale
SOCRadar Dark Web Team detected a post on a hacker forum where a threat actor claims to be selling 1,400 credit card records allegedly originating from South Korea. According to the threat actor’s statements, the dataset includes full cardholder details with an 80% validity rate, and is formatted to include card numbers, expiration dates, CVV codes, personal names, addresses, contact information, and emails.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.