Dark Web Profile: Flax Typhoon
Intelligence reports confirm that Flax Typhoon (also tracked as RedJuliett and Ethereal Panda) is a sophisticated Chinese state-sponsored Advanced Persistent Threat (APT) group, operational since at least mid-2021. The group demonstrates a strategic focus aligned with Chinese government intelligence priorities.
Flax Typhoon’s primary operational focus centers on cyber espionage activities targeting a diverse range of sectors, including government agencies, educational institutions, critical manufacturing facilities, and information technology organizations. While Taiwan remains the group’s predominant target, intelligence reports indicate expanded operations across North America, Africa, and Southeast Asia, demonstrating an evolution in their geographic targeting strategy.
The group’s suspected base of operations in Fuzhou, China, provides strategic positioning for its persistent focus on Taiwanese entities. This geographic location aligns with the assessment that Flax Typhoon’s activities support Beijing’s intelligence requirements regarding Taiwan’s economic partnerships, diplomatic engagements, and technological developments.
What are the Countries and Industries Targeted by Flax Typhoon?
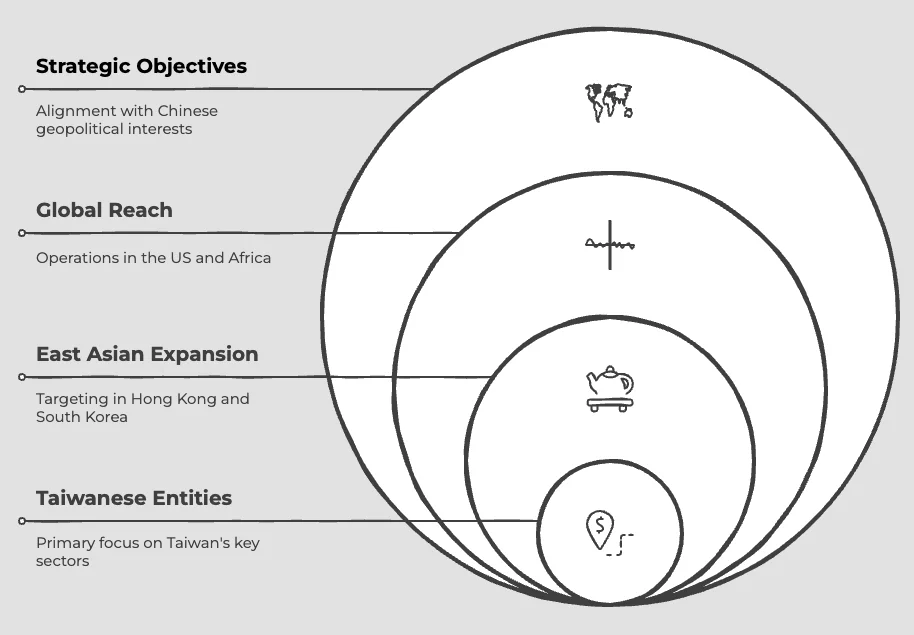
Intelligence sources confirm that the Chinese state-sponsored threat actor has maintained its primary operational focus on Taiwanese entities while significantly expanding its global reach. This expansion represents a strategic evolution in the group’s targeting methodology, suggesting broader intelligence collection objectives aligned with Chinese geopolitical interests.
The group has demonstrated a consistent pattern of targeting government, academic, technology, diplomatic, and telecommunications organizations in Taiwan. This targeting aligns with traditional Chinese intelligence priorities regarding Taiwan. However, Insikt Group’s findings reveal a notable expansion of operations beyond this traditional theater, now encompassing organizations across Hong Kong, Malaysia, Laos, South Korea, the United States, and extending into African nations including Djibouti, Kenya, and Rwanda.
This geographic diversification indicates an evolution in the threat actor’s strategic objectives. The inclusion of targets in East Africa is particularly noteworthy, as it coincides with increased Chinese economic and political engagement in these regions. The targeting of organizations in the United States further suggests interest in collecting intelligence on Western policy positions and technological capabilities.
What Are Flax Typhoon’s Techniques?
The operational profile of Flax Typhoon further focuses on establishing and maintaining extended network access with minimal malware deployment. Their tactical approach includes exploiting vulnerabilities in public-facing servers, deploying VPN connections for persistent access, and executing lateral movement within compromised environments.
Initial access
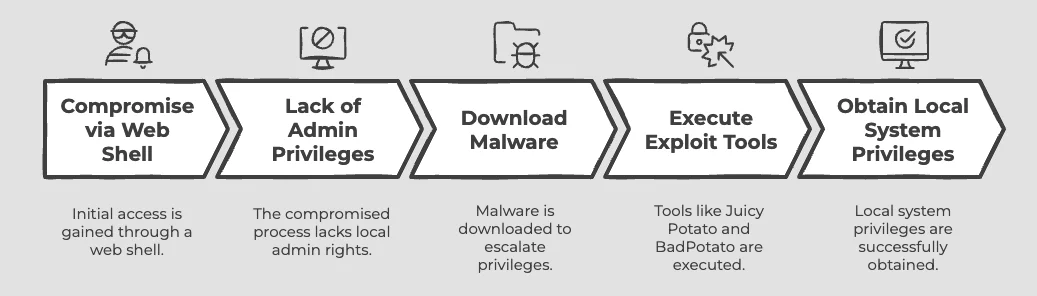
According to Microsoft, Flax Typhoon’s attack chain typically begins with the exploitation of known vulnerabilities in public-facing servers, providing an initial foothold in target networks. The services they target vary but reportedly include VPN, Java, and web applications. The group leveraged threat actor-controlled SoftEther VPN servers to conduct reconnaissance and attempted exploitation activities, primarily against Taiwanese organizations. These servers, also configured as Acunetix Web Application Security Scanners, scanned and attacked web servers in the government, education, and technology sectors. Once access is obtained, Flax Typhoon deploys web shells such as China Chopper, devilzShell, and AntSword to enable remote code execution while maintaining a minimal footprint.
Privilege escalation
In cases where the process compromised via web shell does not have local administrator privileges, the group downloads and runs a piece of malware that exploits one or more known vulnerabilities to obtain local system privileges. Microsoft has observed that the actor use Juicy Potato, BadPotato, and other open-source tools to exploit these vulnerabilities.
Persistence
The group employs a sophisticated persistence method once it gains local administrator privileges through tools such as WMIC, PowerShell, or Windows Terminal.
After gaining access, the actor disables network-level authentication for RDP, which normally forces a user to authenticate before a remote session begins, thereby exposing the Windows sign-in screen to unauthorized interactions.
To capitalize on this vulnerability, the threat actor alters a registry key to disable NLA and replaces the Sticky Keys binary. This manipulation leverages the Sticky Keys accessibility feature, where pressing the Shift key five times launches sethc.exe.
By modifying the registry, the group ensures that when the Sticky Keys shortcut is activated, the Windows Task Manager is launched as a debugger for sethc.exe, granting local system privileges.
With these elevated privileges, the actor can use Task Manager to access the Terminal, create memory dumps, and perform nearly any other action on the compromised system.
Recognizing that RDP typically operates on an internal-facing network interface, the actor further establishes a VPN connection to link the compromised system to its own network infrastructure, ensuring persistent and remote access.
Command and control
The threat actor group establishes a resilient command and control infrastructure by deploying a VPN connection using SoftEther VPN. The actor downloads the necessary executable from their network infrastructure through common Windows tools such as PowerShell’s Invoke-WebRequest, certutil, or bitsadmin.
They then leverage the Service Control Manager to create a Windows service that automatically launches the VPN connection on system startup, enabling continuous monitoring of the compromised system and facilitating RDP access.
To obscure the VPN connection, the actor takes several deliberate measures. They use a legitimate VPN application often found in enterprise environments, which minimizes detection by antivirus solutions, and they rename the executable—typically from vpnbridge.exe to names like conhost.exe or dllhost.exe—to mimic standard Windows components.
Additionally, they employ SoftEther’s VPN-over-HTTPS mode, encapsulating Ethernet packets within compliant HTTPS packets on TCP port 443, making the traffic appear as legitimate HTTPS communications.
For lateral movement within the compromised network, threat actors utilize other legitimate tools such as Windows Remote Management and WMIC, and have been observed routing network traffic through the installed VPN bridge to perform network and vulnerability scans along with exploitation attempts on other systems.
Credential access
Once established on the target system, they conduct credential access operations using well-known techniques and tools.
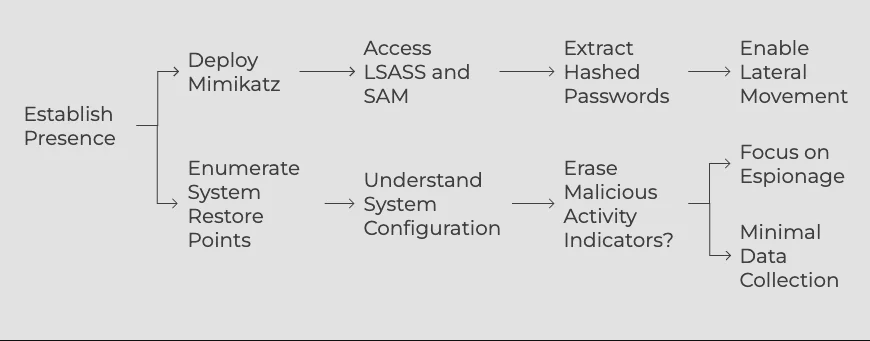
The actor targets both the Local Security Authority Subsystem Service (LSASS) process memory and the Security Account Manager (SAM) registry hive to extract hashed passwords of local users. By deploying Mimikatz, the actor can automatically dump these stores, enabling offline password cracking or pass-the-hash attacks to move laterally within the network.
Additionally, they enumerate System Restore points to gain insights into the operating system’s configuration, potentially using this information to better understand the compromised system or to erase indicators of malicious activity.
According to intelligence reports, despite these credential access and reconnaissance efforts, there is minimal subsequent activity, suggesting that while the actor is focused on espionage and maintaining persistent access, they don’t move towards large-scale data collection or exfiltration.
What are Flax Typhoon’s Relations with Raptor Train Botnet
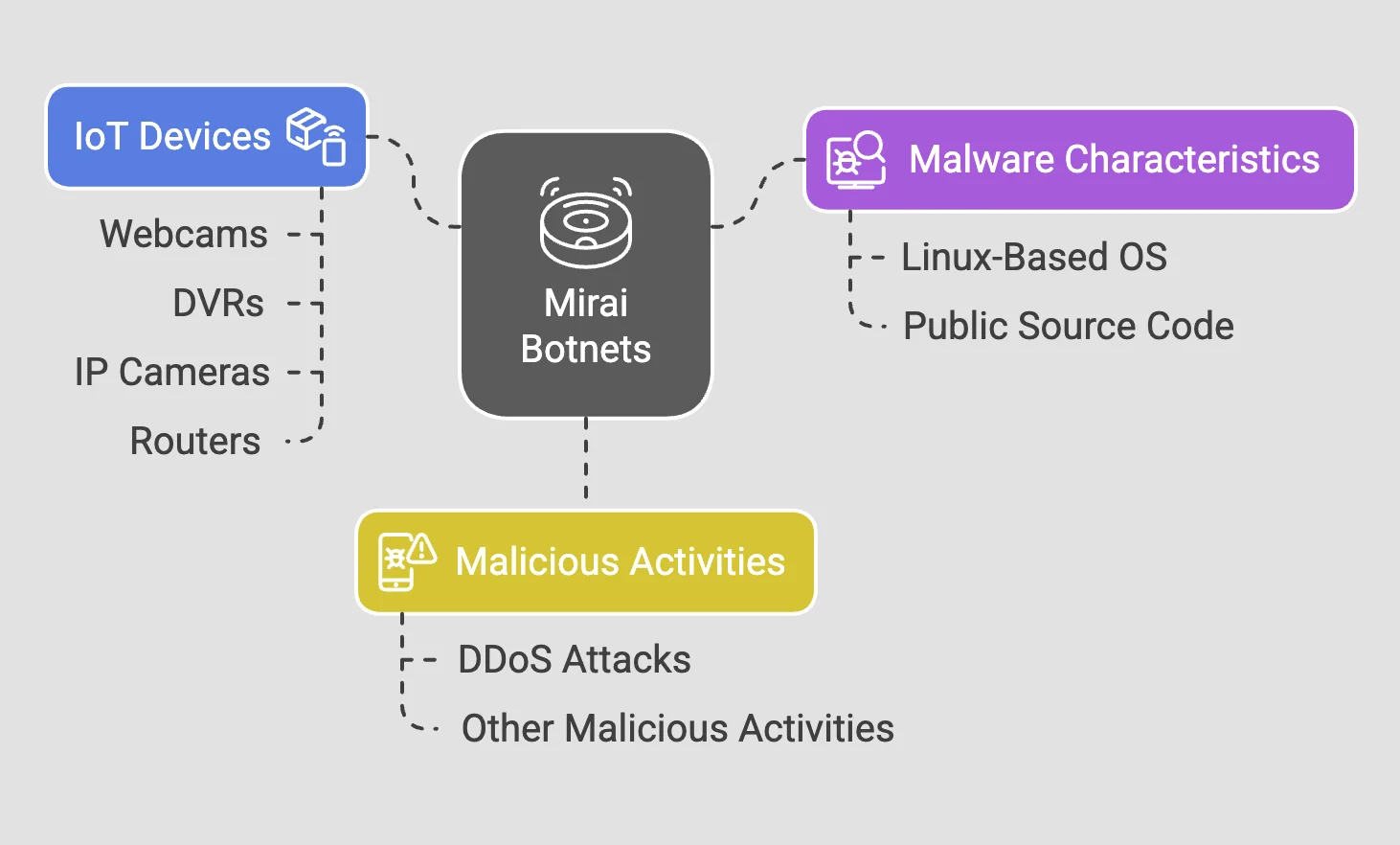
CISA reports indicate that the Raptor Train botnet, operated by the China-based Integrity Technology Group, represents one of the largest and most persistent botnet operations linked to Chinese state-sponsored cyber activities. First identified in mid-2021, the botnet has undergone significant expansion, with its reach growing from 60,000 compromised devices in 2023 to over 260,000 by mid-2024. Its rapid proliferation underscores both the scale and adaptability of the infrastructure supporting it.
A notable aspect of the botnet’s operation is its connection to previously identified Chinese cyber espionage actors, particularly Flax Typhoon. The presence of IP addresses historically linked to these groups within Raptor Train’s operational framework suggests a broader, state-backed initiative that integrates cyber intrusion capabilities with botnet operations. This linkage is reinforced by FBI investigations into U.S. victims, which have found activity consistent with Flax Typhoon’s known tactics, techniques, and procedures (TTPs).
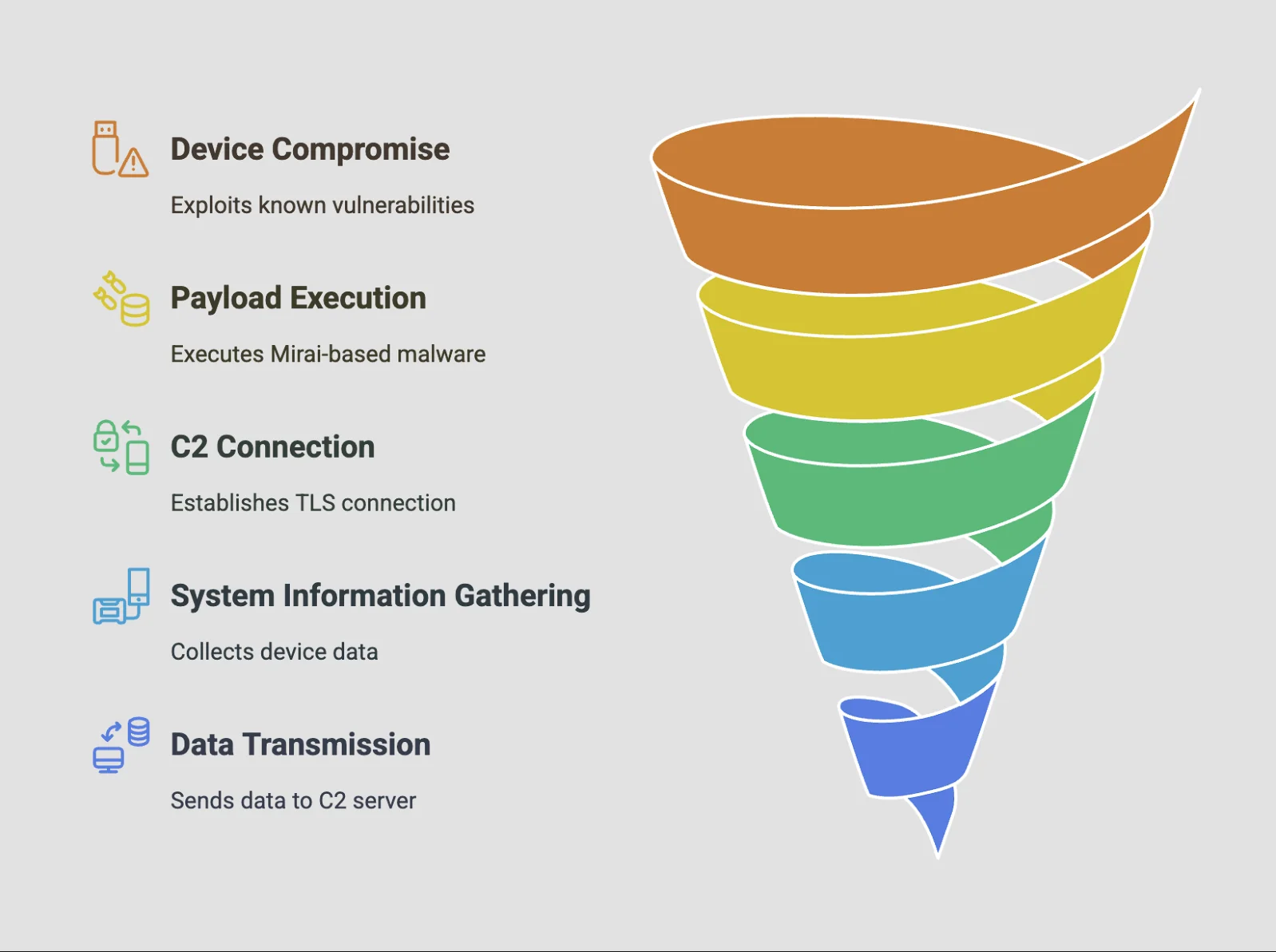
Unlike traditional botnets that rely heavily on malware, Raptor Train prioritizes stealth by exploiting legitimate software tools for persistence. However, it does incorporate a customized version of Mirai malware, a widely abused strain known for targeting IoT devices such as routers, IP cameras, and DVRs.
The infrastructure supporting Raptor Train extends beyond the botnet itself. China Unicom Beijing Province Network IP addresses, which have been observed managing the botnet, were also linked to cyber intrusions targeting U.S. entities.
The botnet’s C2 activity was traced to multiple subdomains of “w8510.com,” with over 80 subdomains identified by September 2024, which was used to collect system information from the victim device. Some malware payloads used by the botnet also exhibit self-deleting properties, further complicating detection and forensic analysis.
The global footprint of Raptor Train is another concerning factor. While Chinese state-sponsored cyber operations have historically focused on strategic targets in the U.S. and Taiwan, this botnet has compromised devices across North America, South America, Europe, Africa, Southeast Asia, and Australia.
For more detailed analysis of the botnet, you can visit our blog post.
How to Mitigate?
- Mitigate the group’s techniques by maintaining robust patch management for public-facing systems and applying proper system hardening. Implement multi-factor authentication and least privilege principles to protect against credential theft and unauthorized access.
- Ensure continuous monitoring of all external-facing services. Look out for post-exploitation activities like web shells, backdoors, or lateral movement within internal networks. Utilize SIEM and EDR tools to detect and respond to threats promptly.
- Implement network segmentation by placing internet-facing services in a DMZ, and control access between network segments. This reduces the impact of any breach and limits lateral movement within the network.
- Adopt a risk-based approach to patching, prioritizing high-risk vulnerabilities and those actively exploited in the wild. Use SOCRadar Vulnerability Intelligence to guide patching efforts and reduce potential threats.
MITRE ATT&CK TTPs of Flax Typhoon
| Tactics | Technique | ID |
| Reconnaissance | Active Scanning: Vulnerability Scanning | T1595.002 |
| Resource Development | Acquire Infrastructure: Virtual Private Server | T1583.003 |
| Resource Development | Compromise Infrastructure: Server | T1584.004 |
| Initial Access | Exploit Public: Facing Application | T1190 |
| Execution | Command and Scripting Interpreter | T1059 |
| Persistence | External Remote Services | T1133 |
| Persistence | Server Software Component: Web Shell | T1505.003 |
| Persistence | Accessibility Features: Event Triggered Execution | T1546.008 |
| Persistence | Create or Modify System Process: Windows Service | T1543.003 |
| Privilege Escalation | Exploitation for Privilege Escalation | T1068 |
| Defense Evasion | Masquerading: Match Legitimate Name or Location | T1036.005 |
| Defense Evasion | Use Alternate Authentication Material: Pass the Hash | T1550.002 |
| Credential Access | OS Credential Dumping: LSASS Memory | T1003.001 |
| Credential Access | OS Credential Dumping: Security Account Manager | T1003.002 |
| Command and Control | Ingress Tool Transfer | T1105 |
| Command and Control | Protocol Tunneling | T1572 |