
Dark Web Sales: A New RCE Exploit, US Credit Cards, and 19M Japanese Emails
In recent discoveries within the cyber threat landscape, the SOCRadar Dark Web Team has identified the sale of access to a cloud company, a financial organization, and a software company. Additionally, a new seed phrase scanner tool has emerged, presenting a critical risk to cryptocurrency security. The team also uncovered a sale of a new Remote Code Execution (RCE) exploit. Furthermore, credit cards from the United States were leaked, and a particularly alarming discovery was made regarding the sale of 19 million Japanese email addresses.
Unauthorized Shell Access Sale is Detected for a German Cloud Company
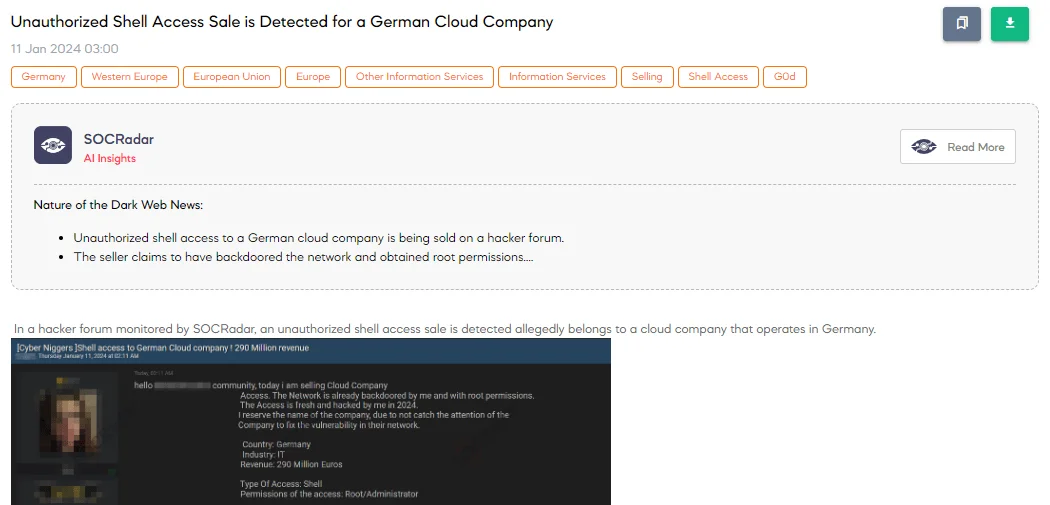
On January 11, the SOCRadar Dark Web Team discovered a hacker forum post offering unauthorized shell access for sale, allegedly from a German cloud company with 290 million Euros in revenue. The threat actor asserts it has personally backdoored the network, gaining root or administrator-level permissions. Emphasizing the freshness of the hack, carried out in 2024, they deliberately withheld the company’s name to avoid alerting them and prompting a fix for the vulnerability.
A New RCE Exploit Sale is Detected for Popular IoT Product
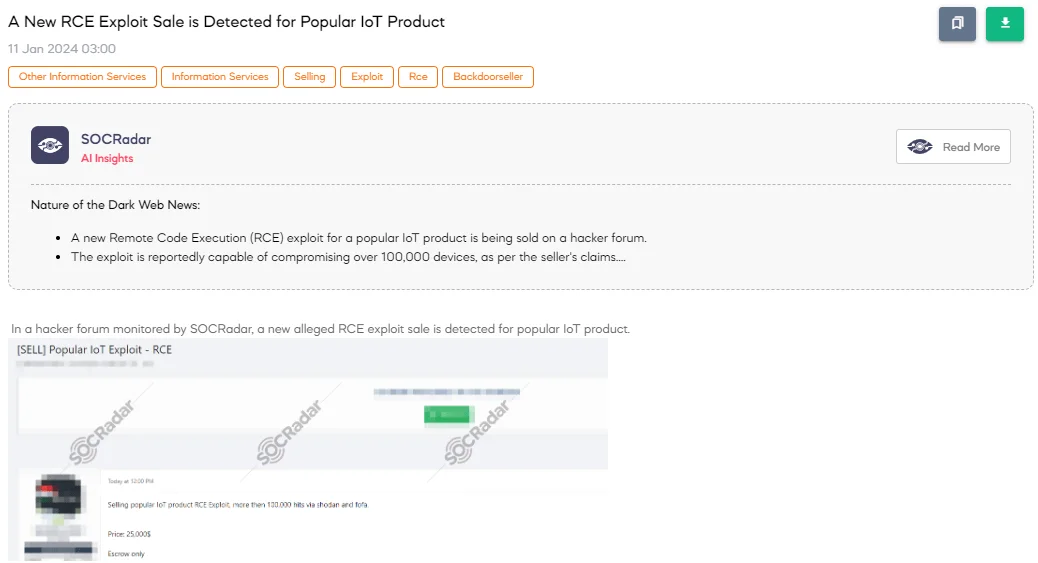
A hacker forum post revealing a sale of a new Remote Code Execution (RCE) exploit for a popular IoT (Internet of Things) product has been detected by the SOCRadar Dark Web Team. The threat actor offers this exploit, claiming it has over 100,000 hits on Shodan and Fofa. These are search engines that specialize in identifying internet-connected devices. The price set for this exploit is $25,000, and the seller requires using an Escrow service for the transaction, ensuring secure fund handling until the deal is complete.
Sale of 19 Million Japanese Email Addresses Detected
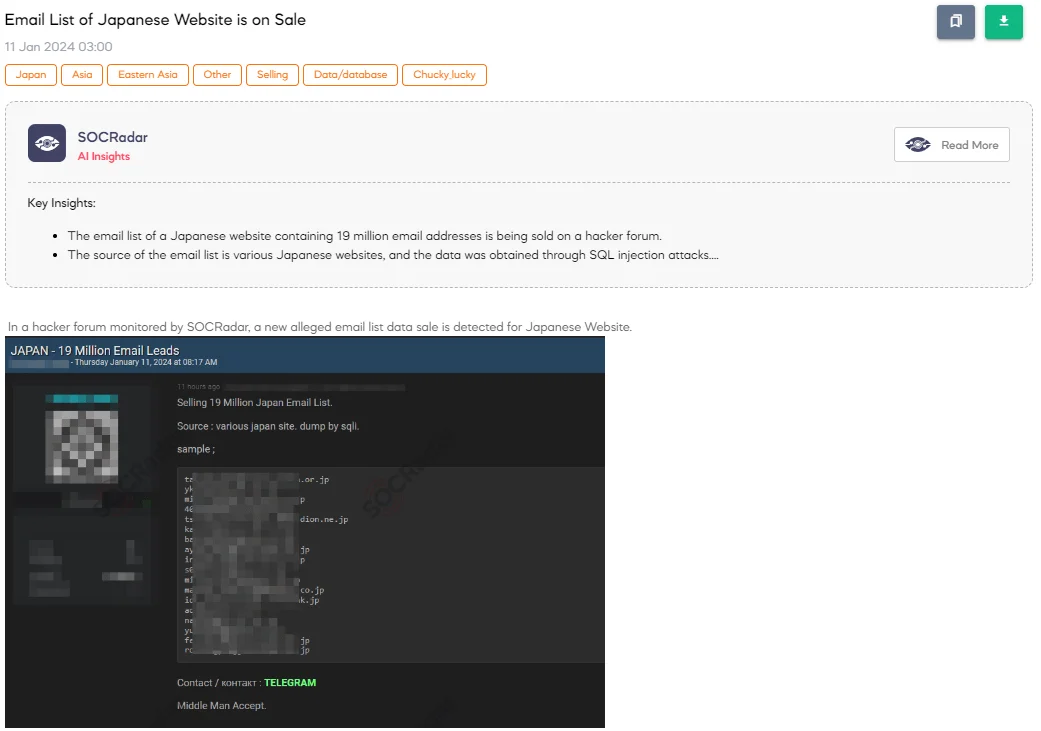
A SOCRadar Dark Web Analyst has detected a post on a hacker forum advertising the sale of an email list allegedly sourced from various Japanese websites. The threat actor claims to be selling a list comprising 19 million Japanese email addresses obtained through SQL injection (SQLi) techniques. They also provide a sample to showcase the data’s authenticity. The seller mentions the availability of contact through Telegram and is open to transactions involving a middleman (Escrow). Such data is often compiled into combo lists, which are used for malicious activities like phishing or credential-stuffing attacks.
Unauthorized VNC Access Sale is Detected for BMO Bank
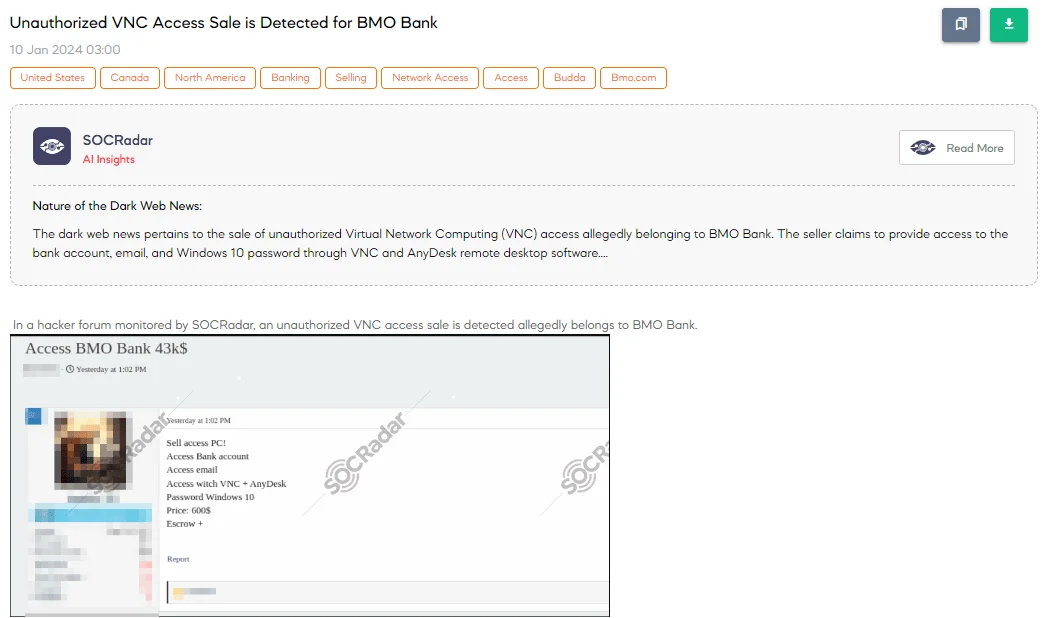
SOCRadar has discovered a post on a hacker forum advertising the sale of unauthorized access, purportedly to the BMO Bank.
BMO Bank, N.A., headquartered in Chicago, Illinois, is an American national bank and a subsidiary of the Toronto-based Bank of Montreal, owned through BMO Financial Corporation.
The threat actor claims that it has access to a PC, bank accounts, and emails, utilizing VNC (Virtual Network Computing) and AnyDesk, which are remote desktop software that allows for control over a computer from a distant location. The sale includes Windows 10 passwords, with a price set at $600, insisting on an escrow service for the transaction.
Unauthorized VPN Access Sale is Detected for an Indian Software Company
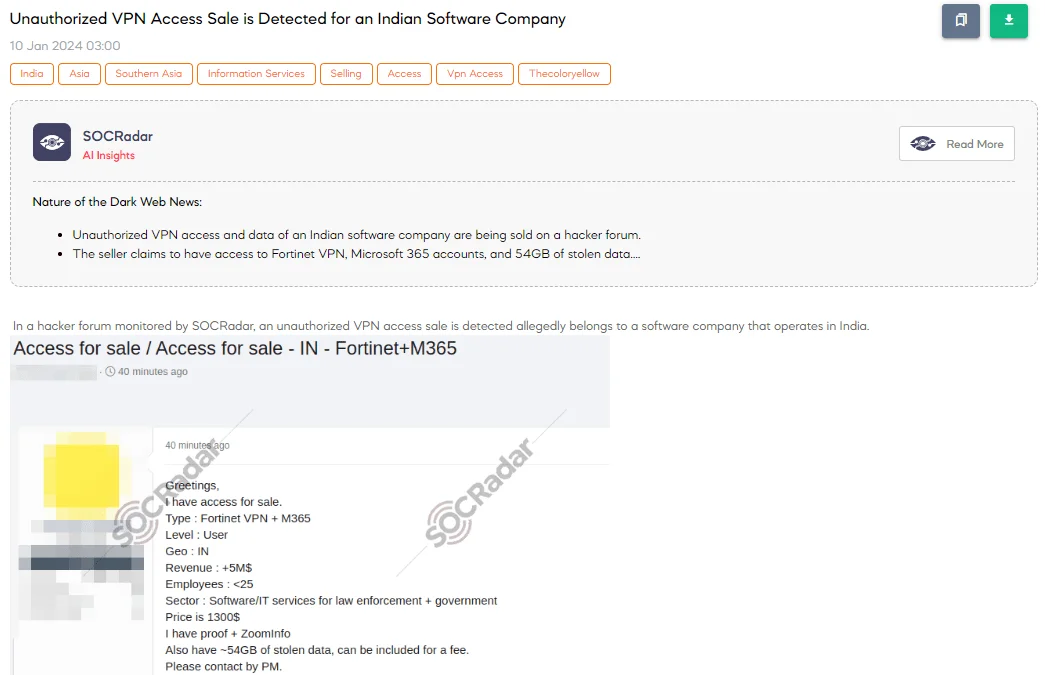
The SOCRadar Dark Web Team has discovered a forum post where a threat actor is selling unauthorized VPN access, purportedly to a software company in India specializing in IT services for law enforcement and government. The actor offers access via Fortinet VPN and M365, at a user level, for a company with over $5M in revenue and fewer than 25 employees. The price is set at $1,300, with the seller claiming to have proof and ZoomInfo details. Additionally, the actor mentions possessing approximately 54GB of stolen data, available for an extra fee. Contact is encouraged through private messaging. ZoomInfo is a platform that provides information about businesses and professionals for sales and marketing purposes.
400 Credit Cards Belonging to the United States are on Sale
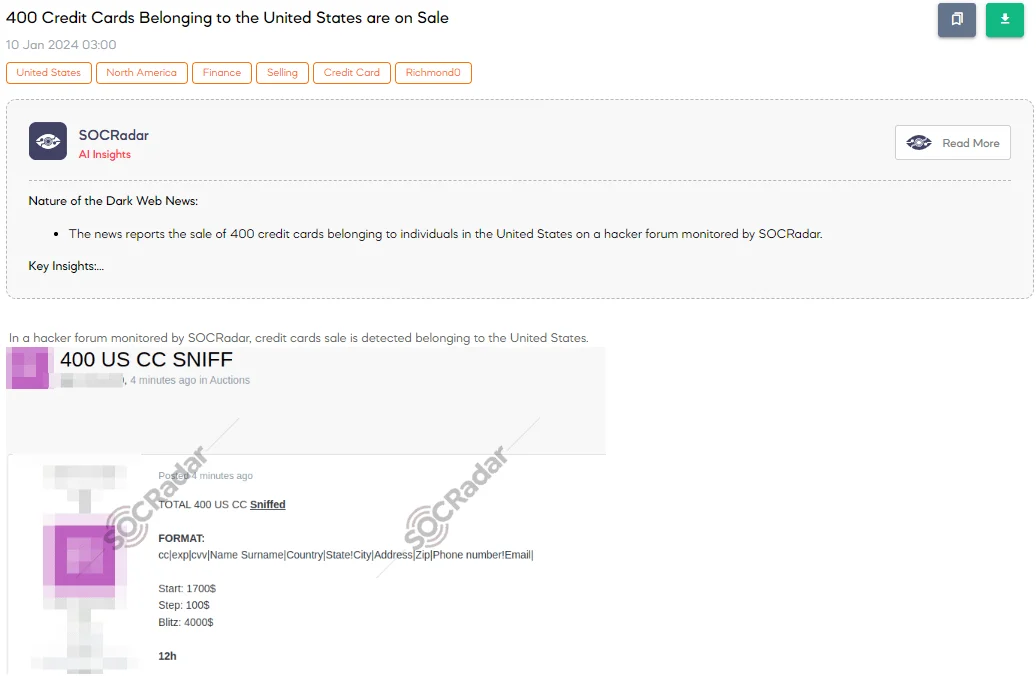
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor claims to be selling information of 400 US credit cards. The threat actor details the data format, including information like the card number, expiration date, CVV, cardholder’s name, country, state, city, address, zip code, phone number, and email. They have set the starting bid at $1,700 with increments of $100, and an option for an instant buy (Blitz) at $4,000, with the auction lasting 12 hours. This situation highlights a significant cybersecurity breach impacting financial data.
A New Seed Phrase Scanner Tool is Shared
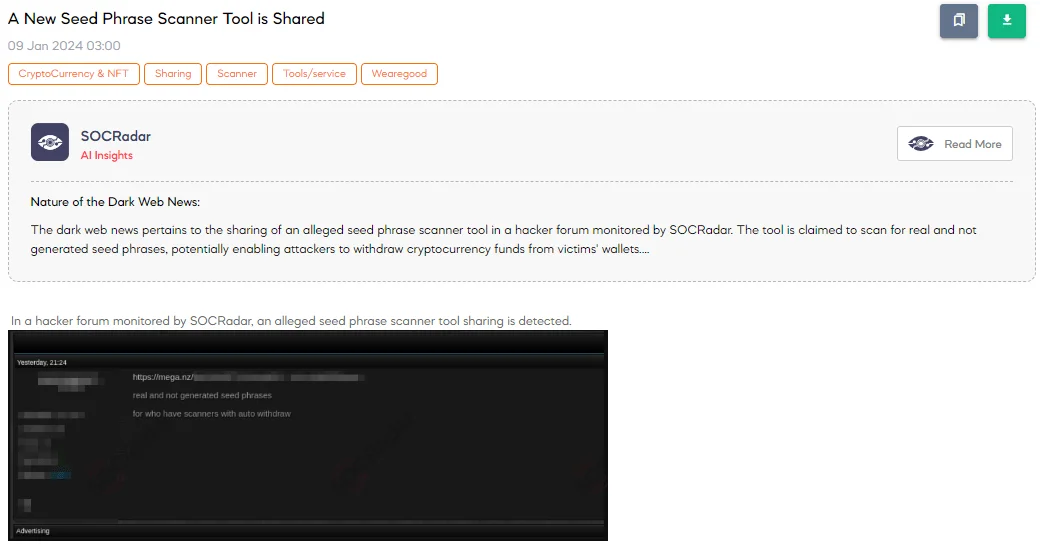
On January 9, SOCRadar identified a new seed phrase scanner tool being shared on a hacker forum, posing a significant threat to cryptocurrency security. The tool claims to access real seed phrases, crucial for wallet security, and features an auto-withdrawal function, allowing attackers to quickly and automatically transfer funds from compromised wallets.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































