
December 2024 Patch Tuesday Update – One Actively Exploited Zero-Day, Multiple Critical RCEs; SAP Updates
[Update] January 2, 2025: “PoC Exploit Available for Critical CVE-2024-49112 “LDAP Nightmare” Vulnerability”
Microsoft’s latest updates in the December 2024 Patch Tuesday bring fixes for 72 security vulnerabilities. This month’s highlights include 16 critical vulnerabilities and one actively exploited zero-day that demands immediate attention. Notably, the zero-day was publicly disclosed and exploited in the wild before Microsoft released its patch, as noted in the advisories.
Here’s a quick categorization of the vulnerabilities addressed this month:
- 31 Remote Code Execution (RCE) Vulnerabilities
- 27 Elevation of Privilege (EoP) Vulnerabilities
- 7 Information Disclosure Vulnerabilities
- 5 Denial of Service (DoS) Vulnerabilities
- 2 Spoofing Vulnerabilities
Let’s look at the most critical vulnerabilities in this month’s update, discuss their potential impact, and outline steps you can take to protect your systems.
Microsoft Patches One Actively Exploited Zero-Day
This month’s Patch Tuesday includes only one actively exploited zero-day vulnerability, CVE-2024-49138 (CVSS 7.8), a privilege escalation flaw in the Windows Common Log File System (CLFS) Driver.
Rated as important, this vulnerability has been observed in real-world attacks, although specific details about its exploitation remain undisclosed at the time of writing.
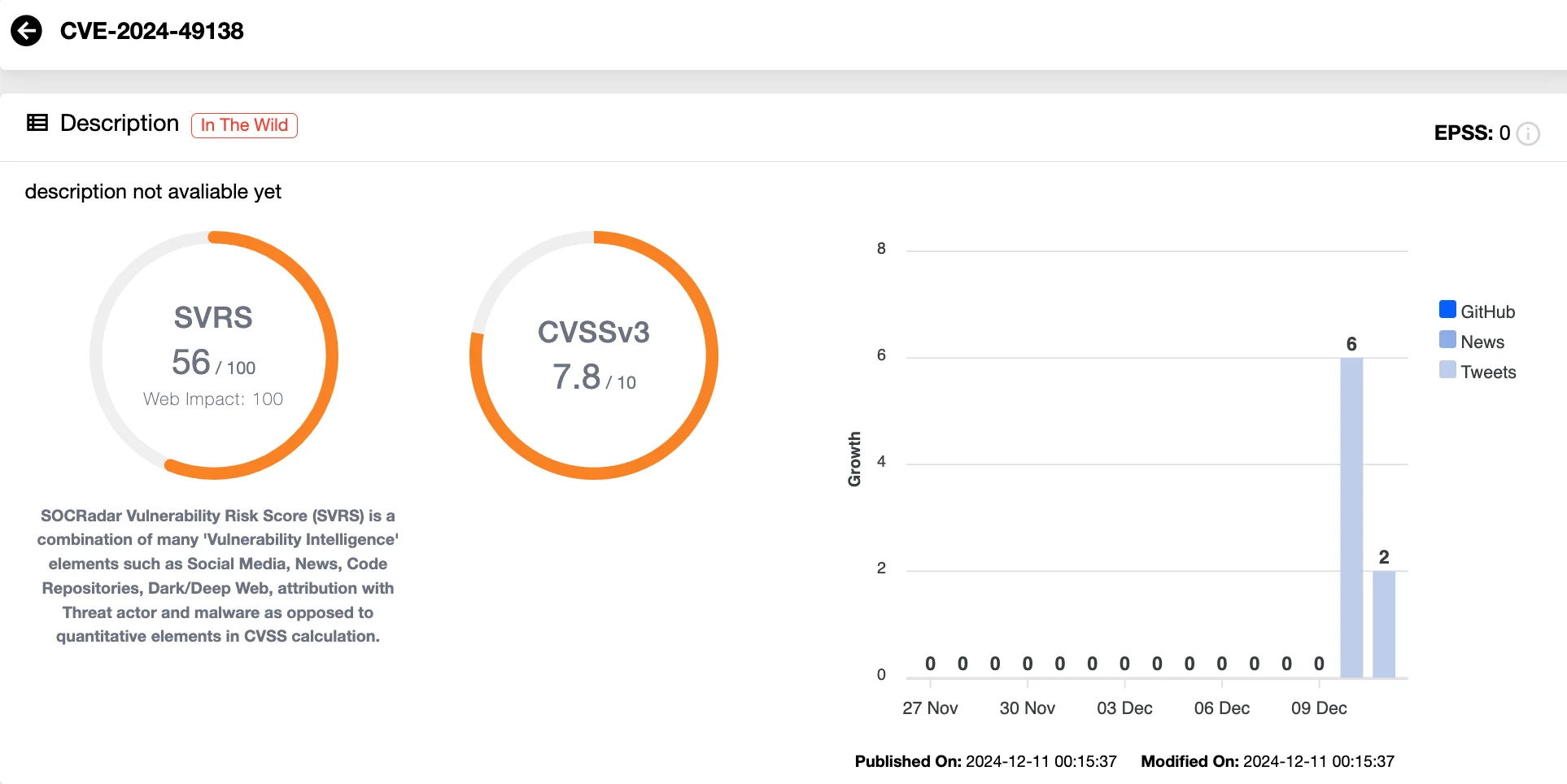
Vulnerability card of CVE-2024-49138 (SOCRadar Vulnerability Intelligence)
According to Microsoft, successful exploitation of CVE-2024-49138 could allow an attacker to gain SYSTEM privileges, providing them with complete control over the targeted system. While the exact method of exploitation has not been revealed, the fact that it has been weaponized highlights the urgency of applying the available patch.
Organizations are strongly advised to prioritize this update to mitigate potential risks, especially as attackers continue to target unpatched systems. For more information, refer to Microsoft’s official advisory on this zero-day vulnerability.
Critical Vulnerabilities in Microsoft’s December 2024 Updates
Microsoft’s December 2024 advisories highlighted 16 vulnerabilities as ‘critical’ in maximum severity, each carrying significant risks of Remote Code Execution (RCE). Here’s a closer look at the most severe vulnerabilities and their potential impact:
Key Vulnerabilities
CVE-2024-49112 and CVE-2024-49117 stand out as the most severe among Microsoft’s December 2024 critical vulnerabilities. Their potential to enable arbitrary code execution or compromise host servers poses significant risks, particularly in environments with interconnected systems.
- CVE-2024-49112 (CVSS 9.8) – Windows Lightweight Directory Access Protocol (LDAP)
This vulnerability allows an unauthenticated attacker to exploit the LDAP service by sending specially crafted requests. Successful exploitation can lead to arbitrary code execution within the context of the service, enabling attackers to compromise the system remotely without prior access. - CVE-2024-49117 (CVSS 8.8) – Windows Hyper-V
Exploitable by an authenticated attacker on a guest VM, this flaw involves sending malicious file operation requests to access underlying hardware resources. If exploited, it could lead to remote code execution on the host server, potentially enabling cross-VM attacks.Notably, the vulnerability does not require elevated privileges, significantly increasing its risk.
PoC Exploit Available for Critical CVE-2024-49112 “LDAP Nightmare” Vulnerability
SafeBreach Labs has released a detailed analysis and Proof-of-Concept (PoC) exploit for CVE-2024-49112, coined “LDAP Nightmare.”
The flaw allows unauthenticated attackers to exploit the vulnerability remotely, leading to a crash of unpatched Windows Servers, including Active Directory Domain Controllers (DCs). SafeBreach researchers demonstrated how the vulnerability could be used to trigger an LSASS crash via LDAP queries, potentially taking down critical infrastructure and elevating privileges within the network.
The researchers’ PoC exploit shows how attackers can exploit the vulnerability by sending a DCE/RPC request to the victim server, redirecting traffic to a malicious LDAP server. Once exploited, the vulnerability forces the victim’s LSASS to crash, causing a reboot.
Organizations are urged to apply this patch immediately and monitor for signs of exploitation, such as unusual CLDAP responses or DNS SRV queries.
For more information, refer to the research, and see the exploit on GitHub to test for exposure.
Additional Critical Vulnerabilities
- CVE-2024-49124 (CVSS 8.1) – Lightweight Directory Access Protocol (LDAP) Client
- CVE-2024-49127 (CVSS 8.1) – Windows Lightweight Directory Access Protocol (LDAP)
- CVE-2024-49126(CVSS 8.1) – Windows Local Security Authority Subsystem Service (LSASS)
- CVE-2024-49118 (CVSS 8.1) – Microsoft Message Queuing (MSMQ)
- CVE-2024-49122 (CVSS 8.1) – Microsoft Message Queuing (MSMQ)
- CVE-2024-49132 (CVSS 8.1) – Windows Remote Desktop Services (RDS)
- CVE-2024-49115 (CVSS 8.1) – Windows Remote Desktop Services (RDS)
- CVE-2024-49116 (CVSS 8.1) – Windows Remote Desktop Services (RDS)
- CVE-2024-49123 (CVSS 8.1) – Windows Remote Desktop Services (RDS)
- CVE-2024-49128 (CVSS 8.1) – Windows Remote Desktop Services (RDS)
- CVE-2024-49106 (CVSS 8.1) – Windows Remote Desktop Services (RDS)
- CVE-2024-49108 (CVSS 8.1) – Windows Remote Desktop Services (RDS)
- CVE-2024-49119 (CVSS 8.1) – Windows Remote Desktop Services (RDS)
- CVE-2024-49120 (CVSS 8.1) – Windows Remote Desktop Services (RDS)
Cybersecurity threats are evolving faster than ever, leaving organizations struggling to keep up. Zero-day vulnerabilities and advanced exploits can quickly expose your systems to attacks, resulting in data breaches, financial losses, or workflow disruptions. Understanding which vulnerabilities pose the greatest risk, and acting fast, is important to stay secure.
SOCRadar’s Vulnerability Intelligence module equips you with the necessary tools, such as:
- Real-time alerts for newly discovered vulnerabilities.
- Insights into active exploit trends.
- Prioritization guidance to address critical risks first.
SOCRadar’s Vulnerability Intelligence module page
With this approach, your team can focus on mitigating the most pressing threats before they escalate. Combined with SOCRadar’s proactive monitoring, you’ll be better prepared to defend against cyber attacks and secure your digital environment.
High-Risk Microsoft Vulnerabilities Demand Immediate Attention
Microsoft’s December 2024 Patch Tuesday update includes several vulnerabilities flagged as “Exploitation More Likely.” This label indicates a high probability of these flaws being actively targeted by attackers.
With no available workarounds for these vulnerabilities, applying the patches is the only viable mitigation strategy. Below are the details of the affected products and vulnerabilities in this category:
- CVE-2024-49093 (CVSS 8.8) – Windows Resilient File System (ReFS)
- CVE-2024-49122 (CVSS 8.1) – Windows Message Queuing
- CVE-2024-49088 (CVSS 7.8) – Windows Common Log File System Driver
- CVE-2024-49090 (CVSS 7.8) – Windows Common Log File System Driver
- CVE-2024-49114 (CVSS 7.8) – Windows Cloud Files Mini Filter Driver
- CVE-2024-49070 (CVSS 7.4) – Microsoft Office SharePoint
For additional information, refer to Microsoft’s December 2024 Patch Tuesday Release Notes.
SAP December 2024 Security Patch Day Addresses Critical Vulnerabilities in NetWeaver and Web Dispatcher
In addition to Microsoft, SAP has also recently released its monthly updates. SAP’s December 2024 Security Patch Day updates feature ten new Security Notes and updates to three previously disclosed notes. The most critical vulnerabilities addressed this month are highlighted below.
- Security Note #3536965 – CVE-2024-47578 (CVSS 9.1):
This vulnerability affects SAP NetWeaver AS for JAVA, its Adobe Document Services component. When combined with two lower-severity vulnerabilities disclosed in the same security note – CVE-2024-47579 and CVE-2024-47580, both classified as Information Disclosure flaws – it creates significant risks, including unauthorized actions that could compromise the system’s confidentiality, integrity, and availability.
- Security Note #3520281 – CVE-2024-47590 (CVSS 8.8):
An update to a Security Note released during the November 2024 Patch Day, this vulnerability involves Cross-Site Scripting (XSS) in SAP Web Dispatcher. It affects versions 7.77 through 9.13 and could allow attackers to inject malicious scripts, potentially jeopardizing the security of trusted web applications.
- Security Note #3469791 – CVE-2024-54198 (CVSS 8.5):
This Information Disclosure vulnerability in SAP NetWeaver Application Server ABAP could enable unauthorized access to sensitive data through Remote Function Calls (RFC).
SAP emphasizes the importance of addressing these vulnerabilities promptly to protect systems from potential risks. Full details on the vulnerabilities can be found in SAP’s December 2024 Patch Day release note.
Cybersecurity threats frequently escalate when vulnerabilities in your systems go unresolved, allowing attackers to exploit critical systems. To avoid serious risks like data breaches or operational disruptions, you must remain on guard and address these gaps as soon as possible.
With SOCRadar’s Attack Surface Management (ASM), you gain continuous visibility into your digital environment. This solution helps you identify exposed assets and risks in real time, enabling your security team to take proactive measures and minimize your attack surface effectively.
Easily monitor Company Vulnerabilities and take quick action via SOCRadar ASM module
At the same time, SOCRadar’s Dark Web Monitoring searches deep into hidden channels such as Dark Web forums and underground markets, flagging any mentions of your company or its vulnerabilities. These modules enable organizations to address risks early on and strengthen their defenses against emerging threats by providing actionable intelligence.


































