
Details On The Largest B2B Leak: BlueBleed
As a cyber threat intelligence company, SOCRadar’s mission is to use every possible piece of information to identify and prevent cyber threats targeting our platform users. SOCRadar has been tireless in expanding its proactive defense capabilities, including a recently developed built-in Cloud Security Module (CSM) that monitors public cloud buckets to detect data leaks. Due to ongoing discussion on the scope and significance of the BlueBleed Leak and Microsoft’s claims about SOCRadar on its blog about the incident, we would like to give more details and answer questions from different channels. We hope that the explanations will make the incident and our intentions clearer.
What is Bluebleed?
SOCRadar’s CSM has so far detected six large cloud buckets that consist of sensitive data belonging to 150,000 companies in 123 countries. SOCRadar platform automatically sent alarms to its affected users whose data was exposed due to misconfigured cloud buckets. While examining a critical level alarm generated by SOCRadar’s cloud security module for more than one of our customers, we detected multiple misconfigured buckets with data belonging to tens of thousands of companies. Due to the size and potential impacts of these public buckets, collectively dubbed BlueBleed, SOCRadar researchers analyzed them to determine potential threats to SOCRadar users.
What is BlueBleed Part I that Impacts 65,000+ Entities?
The largest one of those misconfigured buckets that the SOCRadar platform has detected contains 2.4TB of data that belongs to 65,000 entities in 111 countries. After the initial discovery, SOCRadar automatically started sending alarms to its users. Obviously, this data leak is “not just another one.”
The owner(s) of the buckets did not look like our customers, so we quickly examined the data’s details to find the owner(s). As a result of our investigations and due to the scope of the issue and its probable adverse repercussions, the SOCRadar management team decided to contact Microsoft. Our warning led the cloud service provider to take immediate action and make the bucket private.
How Did We Notify Microsoft?
As a result of the meeting with the Microsoft Security Response Center (MSRC), SOCRadar paused sending alarms after the Microsoft team asked for some time to analyze the data. They expressed their demand to inform the affected customers before SOCRadar, which our leadership team accepted.
SOCRadar has intended to proceed in coordination with Microsoft in every step of the process and had meetings with several members of MSRC and discussed a wide range of issues from the date of publication of the blogs from both sides to how to define the entities potentially affected by the data leak. Both sides stated their concerns and disagreements and reached compromises on some points.
Did We Download any Database from the Misconfigured Public Bucket?
Some publicly available data were automatically crawled by our CSM engine and created critical severity alarms for our customers. Out analysts immediately investigated the alarm due to its scope and criticality to determine the bucket’s owner. But as we promised Microsoft, no data has been shared so far, and all this crawled data was deleted from our systems. We have been redirecting all our customers to MSRC if they want to see the original data.
Why and How did We Create the BlueBleed Search Engine?
One of the main differences between the negotiating parties is the BlueBleed search engine that SOCRadar created for those who are curious if their data was exposed in the bucket. Microsoft demanded the engine’s takedown. From SOCRadar’s perspective, this service has so much in common with “Have I Been Pwned,” where internet users can check whether their data has been compromised in data breaches. This site has been hailed as a valuable source of information for users applying to protect their privacy and online security. The BlueBleed search only shows if a domain name was detected on this leak or not and does not publicly provide any other details about the searched domain names. What we aim with the BlueBleed search engine is basically an enterprise version of Have I Been Pwned where organizations can search if their data was exposed in some of the cloud data leaks CSM has detected so far. As a cyber threat intelligence company, we owe this to the community. BlueBleed search is not our only public service. We also provide account breach searches, dark web reports, and others on publicly available SOCRadar Labs.
Therefore, we do not see any ‘unnecessary risk’ that endangers customer privacy and security. To be more precise, what poses a greater threat is maintaining sensitive data of organizations in a public bucket.
The public BlueBleed search tool only returns results as DETECTED and NOT DETECTED if the searched domain name is detected in the metadata (domain names, company names, email addresses, etc.).
It is important to note that many cyber search tools, such as HaveIBeenPwnd, VirusTotal, Shodan, GrayHat Warfare, etc., provide similar information with more details.
Can Anyone See the Details of BlueBleed Leak?
Using the BlueBleed search engine does not necessarily mean that any user who wishes to get the data belonging to an “entity,” as MSRC advises us to name it, will get the data by just making search queries with a domain name. There is a long and carefully designed process.
After the search with the domain name on our publicly accessible BlueBleed website, visitors can only get information about whether data related to the organization whose domain name is entered exists in the previous public cloud buckets SOCRadar CSM detected. It is as simple as yes or no.
If any related data is detected, we want the users to fill in a ‘Free Edition Submission Form’ to become a SOCRadar Free Edition user to get limited access to our platform. Our analyst team has put immense effort into checking and verifying every single submission with utmost care. It is not a click-and-access procedure. We validate all the requests. In fact, many interested visitors now wait for validation for over a day due to a high number of requests coming. SOCRadar could fairly ensure that we are aware of the risk posed by letting a user into our platform, and this risk is primarily SOCRadar’s risk.
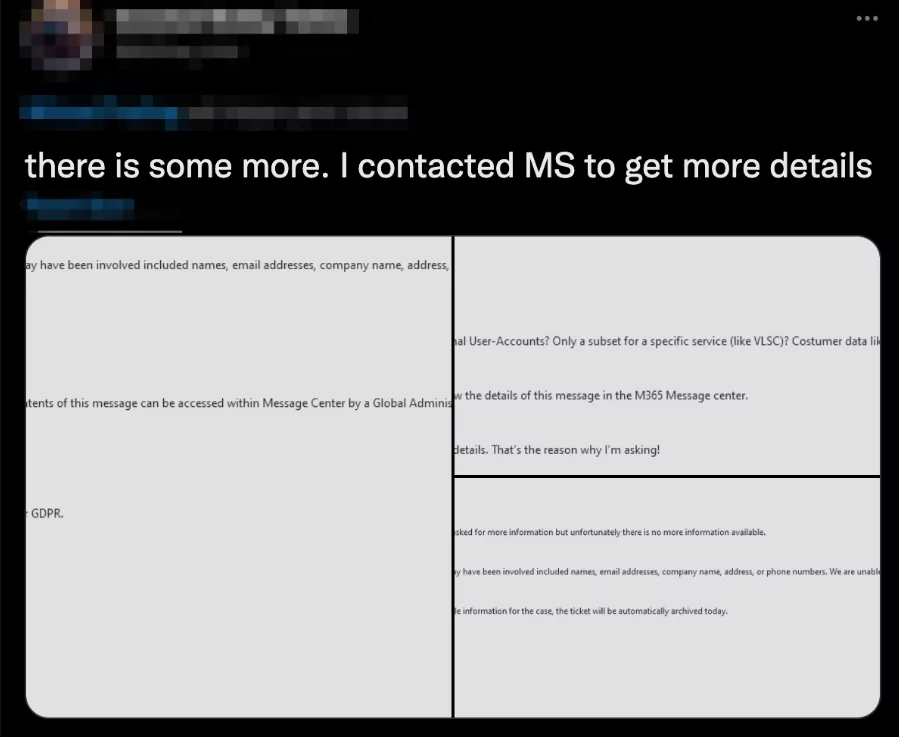
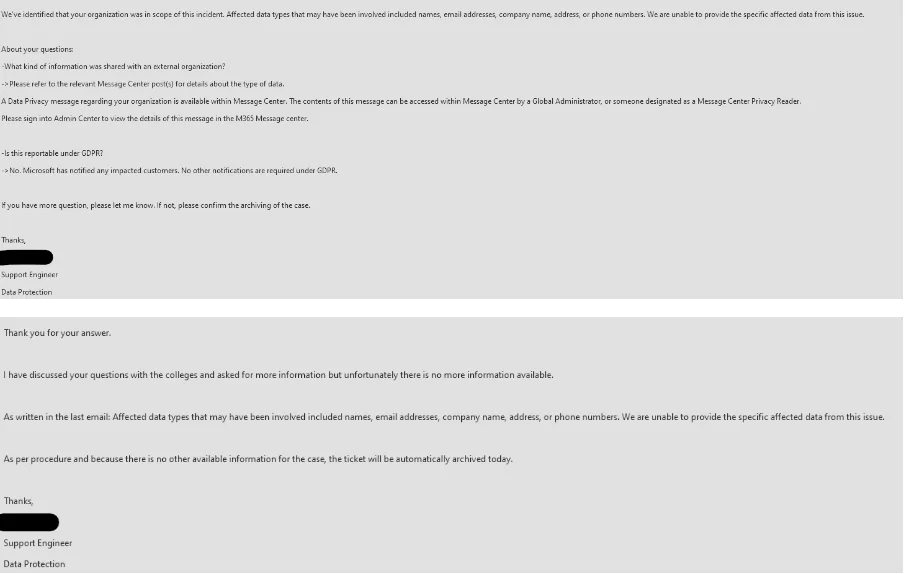
It is important to note that we received much feedback from the customers that the SOCRadar Platform sent alarms encouraging users to contact MSRC for details due to incidents. For those who contacted Microsoft, we were told that Microsoft confirmed the incident but refused to share any details about the contents of the files where our customers’ names were detected.
After our blog post published on October 19, some Microsoft Customers also shared the email exchange with Microsoft about the incident where the email images show that Microsoft is unable to provide any details.
What can a Free Edition User See About BlueBleed?
The Free Edition users (and also the existing SOCRadar users) can do a search in our Threat Hunting module about BlueBleed. What they will get is NOT the data that existed in cloud buckets. It is the METADATA of the data that was exposed due to misconfigured cloud buckets. SOCRadar encourages users to get in contact with the Microsoft team in order to reach the content of the data found in BlueBleed.
However, we would like our users to use SOCRadar services, like BlueBleed, to check and confirm the information they receive from any cloud service provider. We continue to monitor the public buckets, identify the ones which contain sensitive information, and inform the cloud service provider to take the necessary security measures and the affected customers.
SOCRadar finds it an ethical responsibility to announce that the data detected in the public buckets is not stored in BlueBleed’s database. Therefore, we can safely conclude that even if a threat actor can bypass SOCRadar’s verification process, what can be extracted from the search is just the metadata which obviously makes more sense to the owner of this data.
Update: On 19th of October, upon Microsoft’s request, we temporarily suspended any BlueBleed queries in our Threat Hunting Module. All other search queries are still available. We will re-review Microsoft’s request and reconfigure BlueBleed query results if necessary. If you see your company domain name as
How Did We Determine the Number of Entities Detected By BlueBleed?
Another point SOCRadar and Microsoft have not agreed on is the number of affected parties. SOCRadar shared the complete list of entities whose data was found in the bucket. The first discovery showed that the total number of organizations is over 120,000. After objections from the Microsoft team, SOCRadar researchers re-analyzed the data in light of Microsoft’s warnings and came up with a new list that was excluded from duplications. The number difference is also part of the disagreement on the definition of an entity. SOCRadar considers a global company and its subsidiaries as different companies. Regardless of the disagreements, we believe tens of thousands of entities are potentially impacted, making this leak one of the largest B2B data leaks. Microsoft refused to disclose the number they claimed, but SOCRadar analysts worked on the numbers as carefully as possible to understand the real scope of the incident.
Providing true and complete information to affected entities and the public has the utmost importance for a safer digital world. Embracing transparency as a business principle, SOCRadar management takes any criticisms with a solid argumentation into consideration and takes every necessary step to correct any mistake. However, SOCRadar’s expectation from Microsoft to provide the number of affected entities has not been met yet. As discussed above, SOCRadar reconsiders its approach to calculate the number of affected parties and share the new outcome with Microsoft. As a distinguished and leading actor in the cyber security community, what we expect from Microsoft is to go beyond defining our approach as ‘exaggeration’ and provide their version of figures.
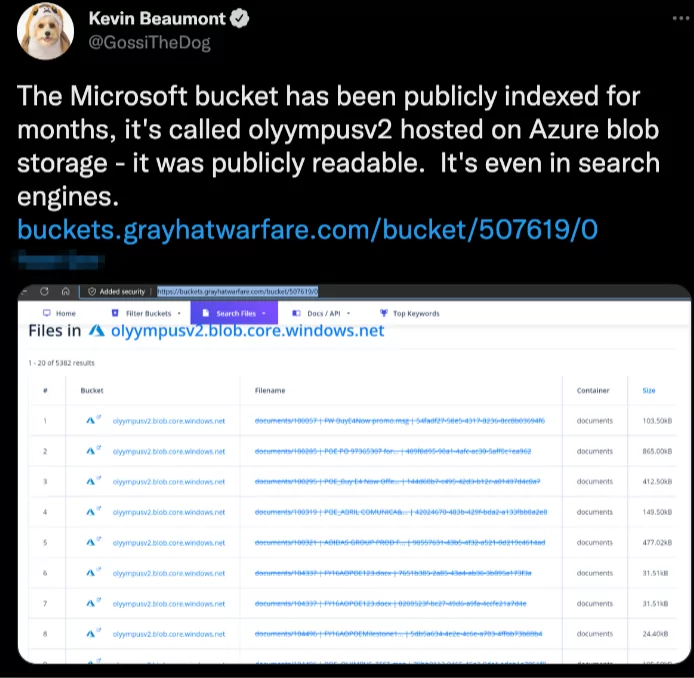
Has the Bucket Ever been Indexed in Any Places?
Kevin Beaumont, a well-known cybersecurity researcher, tweeted on October 20 that “The Microsoft bucket has been publicly indexed for months” and “it was publicly readable. It’s even in search engines.”
We are proud that we were able to catch this problem and inform Microsoft. Thanks to SOCRadar Platform’s capabilities and careful analysis of our researchers, this bucket that consists of sensitive information is no longer accessible.

We are highly disappointed about MSRC’s comments and claims after all the cooperation and support provided by us that absolutely prevented the global cyber disaster.



































