
Disney Data Leak, Meduza Stealer Sale, Nissan Australia and The Economist Targeted in Cyberattacks
Last week’s findings by the SOCRadar Dark Web Team include a substantial 1.9 million credit card data breach by Bidencash, the sale of the Meduza Stealer malware, an unauthorized access sale for a Brazilian government company registry, and a new Android botnet service.
Furthermore, known names are involved in some incidents: a DDoS attack on The Economist by The Anonymous BD, a data leak from Disney MyID Self Service, and a claim by the Akira ransomware group stating that Nissan Australia is their latest victim, with access to sensitive documents and personal information.
Let’s explore these incidents in the latest edition of The Week in the Dark Web.
Get your free Dark Web Report and find out if your data has been compromised.
1.9M Credit Cards are Leaked

On December 23, the SOCRadar Dark Web Team identified a significant data breach involving the leak of 1.9 million credit card details. The breach was disclosed on a hacker forum by a threat actor known as Bidencash.
See our blog for further information and detailed insights about this breach.
Meduza Stealer is on Sale
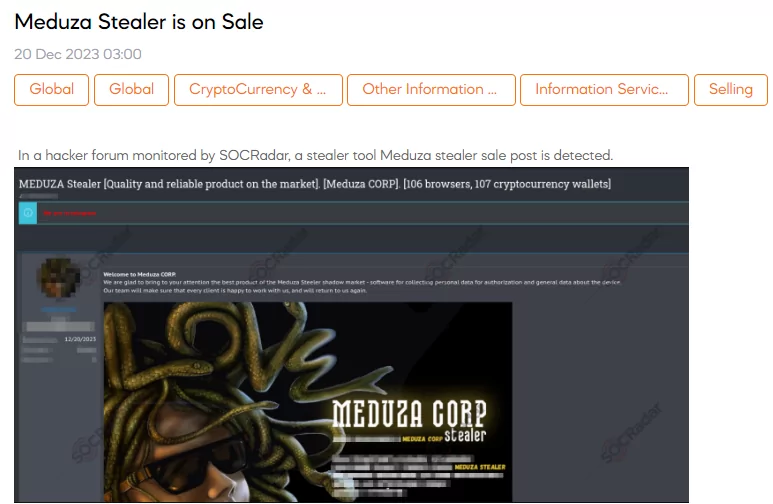
The SOCRadar Dark Web Team has detected a sale post for Meduza Stealer, a personal data collection malware, on a hacker forum. The threat actor, representing Meduza CORP, touts it as a leading product in the shadow market, designed for harvesting authorization and device data. The actor highlights its features, including a web panel for on-the-fly file encryption, minimalistic design, a clear log structure, and a lightweight build.
According to the post, It boasts capabilities like server-side log decryption, a unique protocol for C2 server communication, and extensive collection targeting 100 browsers, 107 crypto wallets, Steam files, Telegram, Discord, and various password managers. The service promises reliability, efficiency, and a focus on client satisfaction, indicating a high level of sophistication and broad potential in cybercrime.
A New Android Botnet Service is Detected
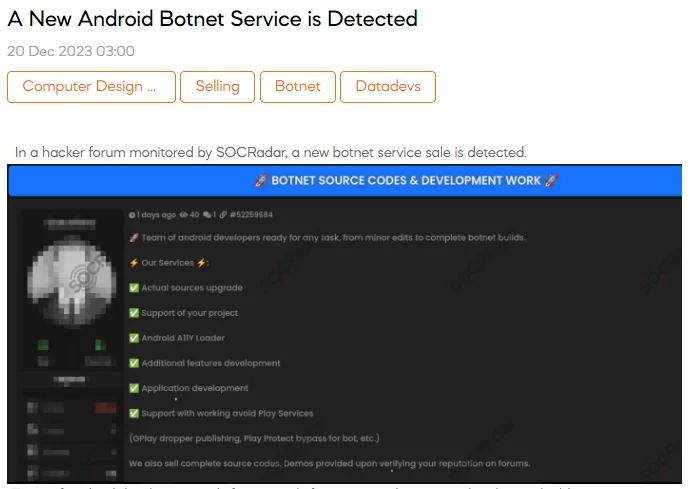
We identified a new Android botnet service being advertised on a hacker forum. The threat actor asserts they have a team of Android developers prepared to undertake tasks ranging from minor edits to complete botnet builds. They offer services such as upgrading current sources, supporting projects, developing additional features, and creating applications. Notably, they claim proficiency in avoiding Google Play Services, including publishing droppers on Google Play and bypassing Play Protect for bots. They also mention selling total source codes and providing demos after verifying a buyer’s reputation on forums.
The Anonymous BD Conducted DDoS Attack on The Economist
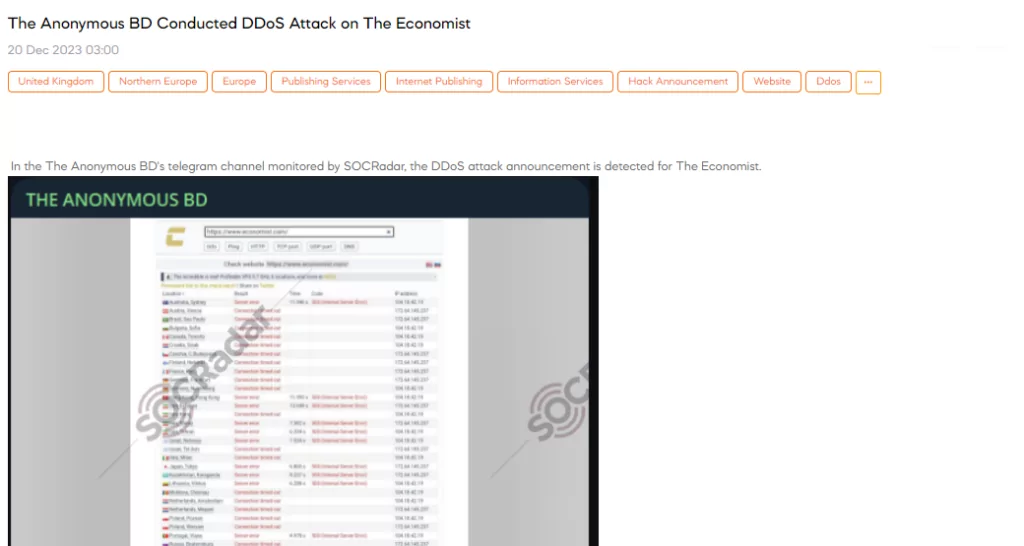
On December 20, the SOCRadar Dark Web Team identified a post on The Anonymous BD’s Telegram channel, where they claim to have conducted a DDoS attack on The Economist, a major UK-based news website.
Unauthorized Access Sale is Detected for Brazilian Government Company Registry
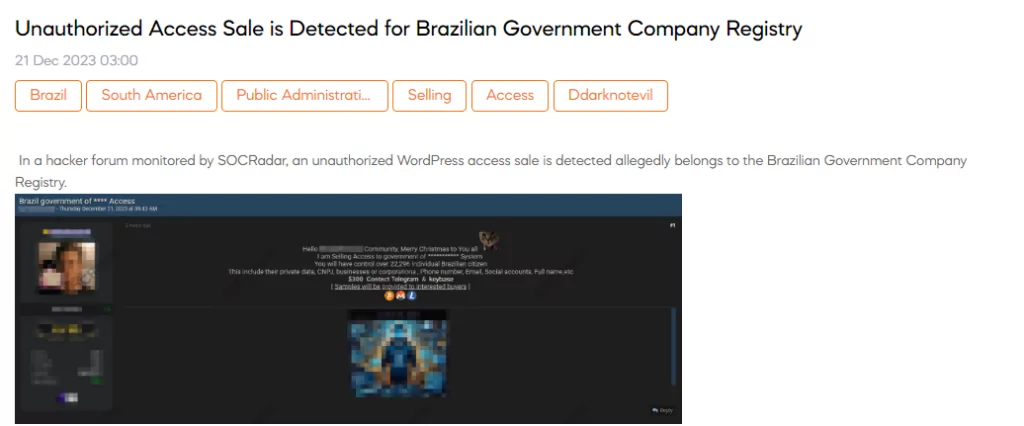
The SOCRadar Dark Web Team has uncovered a post on a hacker forum advertising the sale of unauthorized access to a Brazilian government company’s WordPress system. The threat actor claims to provide control over the personal data of 22,296 Brazilian citizens, including sensitive information like CNPJ (business or corporation tax ID), phone numbers, e-mails, social accounts, and full names. Priced at $300, the actor offers to provide samples to interested buyers and lists contact details for transactions.
Data of Disney MyID Self Service are Leaked
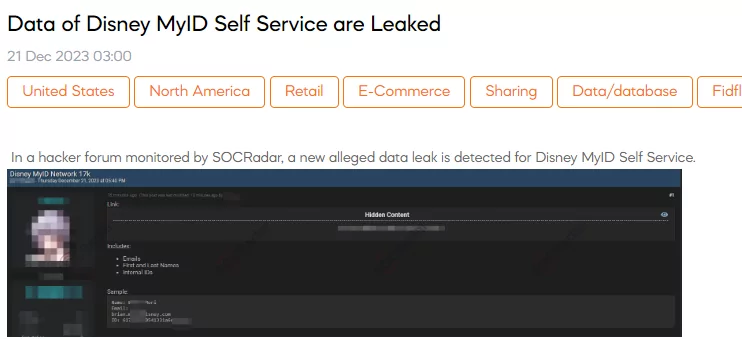
The SOCRadar Dark Web Team has detected a post on a hacker forum that allegedly details a data leak from Disney’s MyID Self Service. The threat actor claims the leak includes e-mails, first and last names, and internal IDs.
The New Ransomware Victim of Akira: Nissan Australia
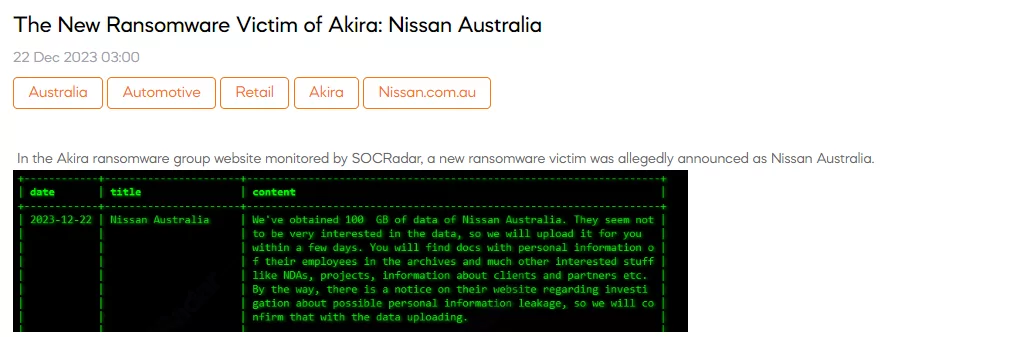
On December 22, the SOCRadar Dark Web Team uncovered a claim on the Akira ransomware group’s website stating that Nissan Australia is the latest victim of their ransomware attack. The threat actor asserts they have obtained 100 GB of data from Nissan Australia, including sensitive documents with employees’ personal information, NDAs, project details, client and partner information, and more.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































