
Enter the BlackLotus: Analysis of the Latest UEFI Bootkit
The world of cybercrime is constantly evolving, and one of the latest threats to emerge is the BlackLotus bootkit. This malware is the first known bootkit capable of bypassing Secure Boot on Microsoft Windows 11 systems, making it a dangerous threat in the cyber world. The malware has been sold on various hacker forums for $5,000, while upgrading to a new version only costs $200. The 80 kB-sized BlackLotus bootkit has been available on hacker forums since October 2022.
Secure Boot Features and Bootkit Malware

Secure boot is a BIOS software that comes with UEFI version 2.3.1. Secure boot ensures that only trusted software, as determined by the manufacturer, is allowed to run when the machine is started. When Secure Boot is enabled, the computer will verify the digital signature of any executable files before allowing them to run. This feature reduces the impact of bootkits.
Bootkit malware is malicious software designed to gain access to and take control of a computer’s operating system. Bootkit malware differs from other types of malware because it embeds itself in a computer’s boot sector or master boot record (MBR). Therefore, it runs during the computer’s startup process and takes control of the system before the operating system starts. After infecting a machine, bootkits have full control over the system. They can disable security mechanisms and deploy their own kernel-mode or user-mode payloads in early operating system startup stages. In this way, they work in the system with high authority and confidentiality. In particular, groups such as the Russia-backed APT28 (Fancy Bear) and China-backed APT41 (Double Dragon) have carried out bootkit-based cyberattacks to maintain persistence in victim systems. These APT groups, renowned for their bootkit expertise, have been responsible for significant cyberattacks worldwide.
Features of BlackLotus
The most important feature of BlackLotus, mentioned in hacker forums, is its ability to bypass secure boot. Additionally, it can bypass Windows security protections. The malware has Ring0/Kernel protection against removal. The purpose of the malware is to act as an HTTP downloader running under the SYSTEM account. It also has features such as anti-VM, anti-debug, and code obfuscation to prevent malware analysis.
Machines Still at Risk
BlackLotus uses the CVE-2022-21894 vulnerability to bypass the secure boot feature. Microsoft released a patch for this vulnerability in January 2022, but the vulnerable signed binaries have yet to be added to the UEFI revocation list. This list identifies boot files that should no longer be trusted and marks them as untrusted. Therefore, even fully updated devices still appear vulnerable.
ESET malware researcher Martin Smolár states that the following three Microsoft-signed files were abused for malicious purposes:
Anatomy of the BlackLotus Bootkit Attack
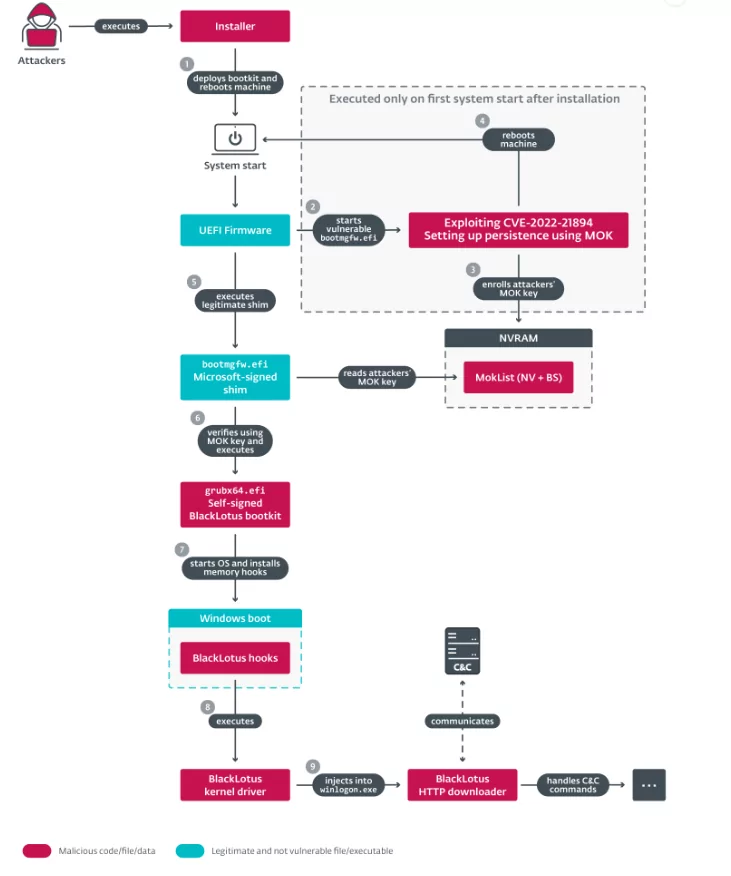
Martin Smolár, a malware researcher at ESET, explains the attack in his blog, stating that the attack starts with running an installer. The installer first checks whether it has the necessary privileges to execute processes. If it does not have sufficient privileges, it attempts to elevate privileges by using the UAC bypass method. UAC is a security feature that asks users if they want to approve high-privileged processes that can cause certain changes on their computers.
Once the installer has the necessary privileges, it deploys bootkit files to the EFI system partition. Malicious binary files are deployed to the EFI system partition along with Microsoft-signed files that have the CVE-2022-21894 vulnerability. The EFI system partition is a section that contains files necessary for booting in EFI-based systems and includes the essential EFI components that will be used during the boot process.
The installer disables the BitLocker and HVCI security systems. The HVCI security system must be disabled to run unsigned kernel code. Kernel code runs in the operating system kernel and interacts directly with the operating system and hardware. The HVCI system ensures the integrity of kernel code, which is critical for security.
The installer restarts the computer. The restarted computer runs through the modified files in the EFI system partition. The machine loads the modified BCD (Boot Configuration Data) boot options that were previously modified by the installer. BCD is a database that contains configuration data used for booting in Windows operating systems.
During the computer restart, the attacker’s MOK key is also saved, ensuring continuity even in systems with UEFI secure boot enabled. MOK allows users to install their own boot or driver software despite the blocking by UEFI secure boot. This is useful when users need to install their own software, but it also allows the malware to bypass UEFI secure boot using the same method.
The purpose of the bootkit is to distribute an HTTP downloader consisting of a kernel driver and a user-mode component. If instructed by the HTTP downloader, the bootkit removes itself or runs additional kernel loads. It also prevents the deletion of bootkit files from the ESP. The HTTP downloader communicates with the C&C to execute received commands and download and run payloads.
Mitigations and Remediation

According to Martin Smolár, the remediation method for a persistent BlackLotus bootkit infection involves reinstalling Windows and using the mokutil utility to remove the attacker’s registered MOK key. The most critical mitigation measure against the BlackLotus bootkit is to disable vulnerable UEFI binary files that are used to bypass UEFI Secure Boot.
Using security products and keeping them and your system up-to-date will help prevent BlackLotus infections and reduce their impact. Closely monitoring threat actors also raises awareness of current threats, enabling you to optimize security measures and minimize risks from BlackLotus and other malware. The campaign page prepared by the SOCRadar research team, which closely tracks and analyzes threat actors and cyber incidents, will be helpful in this regard.




































