
Everything You Need to Know About TIBER-EU Framework
TIBER-EU (Threat Intelligence-Based Ethical Red Teaming) is widely recognized as a leading framework for simulating cyberattacks against critical financial infrastructure across the EU. Unlike traditional pen testing, it replicates the tactics of real-world threat actors to uncover how far adversaries could go if they truly came after you.
It’s not just about defense, it’s about understanding your actual exposure from the attacker’s perspective.
Why was it Created?
Before TIBER-EU, each country had its own testing method. For example, the UK had CBEST, and the Netherlands had TIBER-NL. TIBER-EU combines these efforts into one standard. It helps companies and regulators work together to improve cyber resilience across Europe.
Who has used TIBER-EU?
Many European banks and regulators have used it. De Nederlandsche Bank (DNB) was one of the first. The European Central Bank (ECB) also did a TIBER test on its systems. Over 100 tests have been done in countries like Germany, France, Ireland, and Belgium.
What value does TIBER-EU provide?
TIBER-EU helps companies find gaps in their detection and response. It shows what works and what needs fixing. It also gives the board clear insights into cyber risks. After the test, companies get better at handling real attacks.
Is it safe and legal?
Yes, but only with strict rules. The company must approve the test in writing. All actions are controlled. Red teams must avoid harming systems. If anything risky happens, the test can be stopped. Data protection rules also apply, especially around personal data.
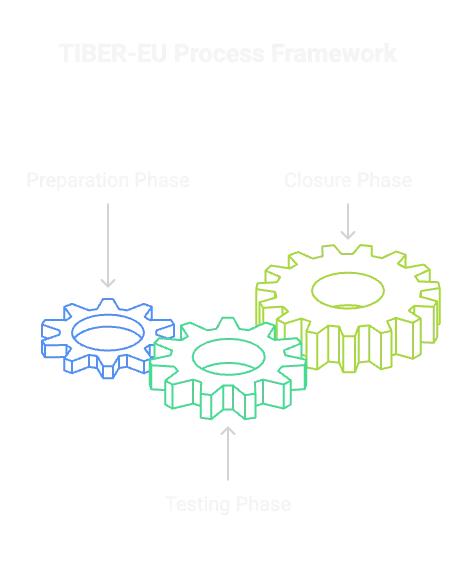
How Does the TIBER-EU Process Work?
What is TIBER-EU and Why Does It Matter?
The TIBER-EU framework unfolds across three structured phases, each designed to simulate real-world cyber threats while maintaining control and oversight:
- Preparation Phase:
In this phase, the organization defines the scope of the engagement, identifies critical functions and systems, and ensures alignment with National Competent Authorities (NCAs) and regulators. Threat intelligence providers play a key role here, delivering sector-specific intelligence to shape realistic attack scenarios. - Testing Phase:
Guided by the threat intelligence collected earlier, a red team mimics the Tactics, Techniques, and Procedures (TTPs) of real-world threat actors. The goal is to compromise agreed-upon critical systems without tipping off defenders. Throughout this phase, blue teams remain unaware, making detection and response evaluations highly authentic. - Closure Phase:
Post-exercise, findings are reviewed collaboratively among all stakeholders, including red and blue teams, intelligence partners, and regulators. The results are used to identify systemic vulnerabilities, recommend mitigations, and improve detection and response capabilities. In some cases, a replay or “purple teaming” session is performed to validate improvements.
What is TIBER-EU?
TIBER-EU (Threat Intelligence-Based Ethical Red Teaming) is widely recognized as a leading framework for simulating cyberattacks against critical financial infrastructure across the EU. Unlike traditional pen testing, it replicates the tactics of real-world threat actors to uncover how far adversaries could go if they truly came after you.
It’s not just about defense, it’s about understanding your actual exposure from the attacker’s perspective.
How long does a typical TIBER-EU engagement last?
A full TIBER-EU engagement usually spans several months. The preparation phase alone can take several weeks, followed by 6–8 weeks of active testing, and an additional period for reporting and closure activities. Timelines may vary depending on the organization’s size and the complexity of the agreed-upon scenarios.
What happens if defenders detect the red team early?
If defenders detect the red team too early, the test is not necessarily failed. Instead, the detection is noted as a success point. The red team may pivot to alternative attack paths, or the test plan may be adjusted to continue assessing resilience without compromising the learning objectives.
What makes TIBER-EU different from a standard test?
TIBER-EU goes beyond traditional red teaming. It’s a comprehensive, intelligence-led security validation framework that reflects the complexity of today’s evolving threat landscape. Rooted in real-world threat actor behaviors and tactics, TIBER-EU assessments are closely monitored by national authorities to ensure safety and control throughout the process.
With active involvement from executive leadership, the program emphasizes learning and improving resilience, rather than simply passing or failing a test.
If you want to explore how dark web intelligence can further enhance TIBER-EU exercises and similar intelligence-led testing programs, check out our blog post, or dive deeper by downloading our full whitepaper here.
Who runs the Test?
Two external teams are hired:
- Threat Intelligence (TI) provider: Finds out how real attackers might target the company.
- Red Team (RT) provider: Simulates the attack using that intelligence.
They work together but stay independent. The company’s white team coordinates everything.
Why TIBER-EU fails without real threat intelligence
TIBER-EU isn’t effective without relevant, timely, and tailored threat intelligence. Here’s what threat intelligence brings to the table:
- Maps adversary TTPs to the organization’s attack surface using frameworks like MITRE ATT&CK
- Identifies threat actors that have historically targeted similar institutions
- Uncovers asset exposure on the surface, deep, and dark web
- Correlates regional threats and campaign trends with your digital footprint
Without real intelligence, it’s just guesswork. TIBER-EU demands precision, not assumption.
How SOCRadar Adds Value to Your TIBER-EU Engagement
SOCRadar is uniquely positioned to supercharge your TIBER-EU or TLPT program:
| Capability | SOCRadar Value |
| Threat Actor Intelligence | Monitor and profile threat actors targeting your industry or region through real-time actor cards and campaign tracking. |
| Digital Footprint Discovery | Automatically discover exposed digital assets—domains, subdomains, IPs, certificates—to define your real attack surface. |
| Attack Surface Monitoring | Continuously track changes to your infrastructure, detect misconfigurations, and prioritize risk with asset-level visibility. |
| Dark Web Intelligence | Detect leaked credentials, data breaches, and insider threat indicators across underground forums, marketplaces, and Telegram channels. |
| Threat Campaign Correlation | Map sector-specific APT campaigns, malware activity, and IOCs to inform scenario selection and red team focus areas. |
TIBER-EU starts with knowing who might target you. SOCRadar shows you exactly that, and more.
Is TIBER-EU Compliance Mandatory for All?
Not across the board, but in countries like the Netherlands (where the Dutch Central Bank (DNB) has implemented the TIBER-NL program for financial institutions), Germany, Ireland, and others, TIBER-EU (or national versions like TIBER-NL) is increasingly being required for systemically important institutions.
Even where it’s not required, it’s quickly becoming a cybersecurity maturity benchmark.
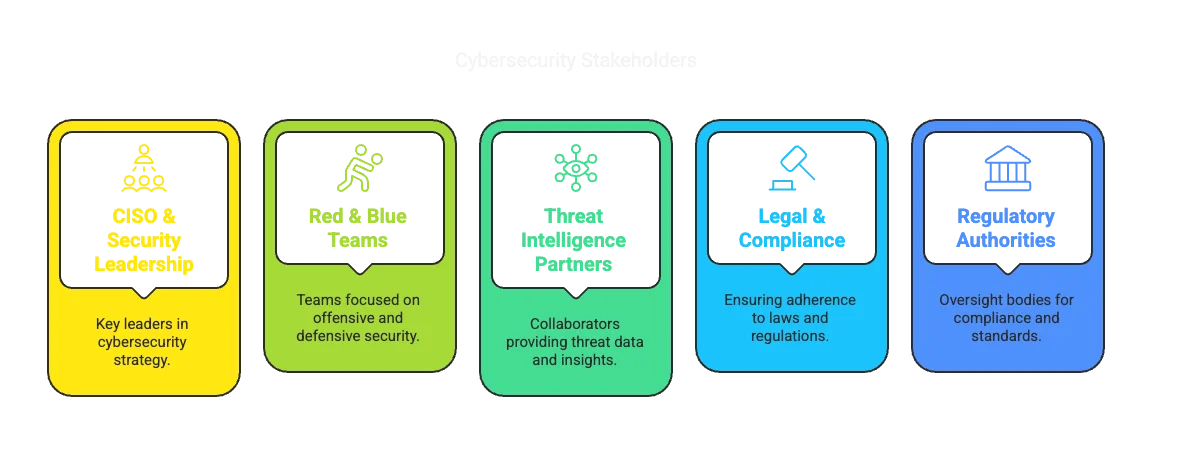
Who Should Lead and Be Involved in a TIBER-EU Project?
A successful TIBER-EU exercise requires collaboration between:
- CISO / Cybersecurity Leadership
- Red & Blue Teams
- Threat Intelligence Partners
- Legal, Compliance & Executive Stakeholders
- Regulatory Authorities (when applicable)
Who Should Lead and Be Involved in a TIBER-EU Project?
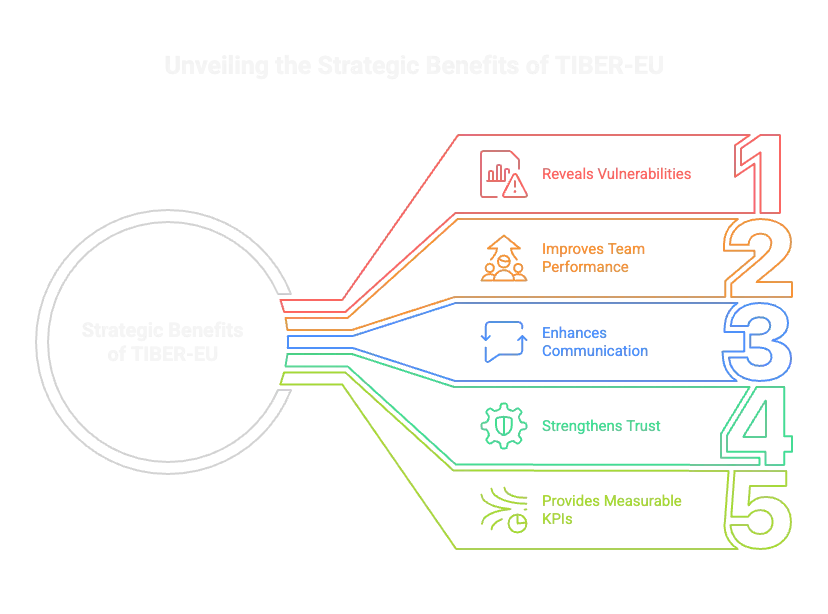
What Are the Strategic Benefits of TIBER-EU?
- Reveals real vulnerabilities threat actors could exploit
- Improves SOC and IR team performance under pressure
- Enhances cross-functional communication and response
- Strengthens regulatory posture and stakeholder trust
- Provides measurable KPIs for cyber resilience
- E.G. MTTD (mean time to detect), MTTR (mean time to respond), red team detection rates, and effectiveness of containment actions
What are the strategic benefits of TIBER-EU?
The outcome? Resilience that’s tested, proven, and regulator-ready.
Final Thoughts: Don’t Just Prepare. Simulate, Learn, Evolve
Financial institutions can no more afford to wait for an attack to discover their weaknesses. TIBER-EU offers a realistic lens into your defenses, and threat intelligence ensures it’s laser-focused on what matters most.
With SOCRadar as your trusted threat intelligence partner, you’re not just running a test, you’re building a strategic advantage.
For more on how real-world threat intelligence, especially from dark web sources, can elevate red teaming and penetration testing, explore our whitepaper and accompanying blog post.
Ready to align your organization with TIBER-EU standards and go beyond compliance? [Book a Demo] to see how SOCRadar can guide your journey.



































