
What is Red Teaming and How Does It Work?
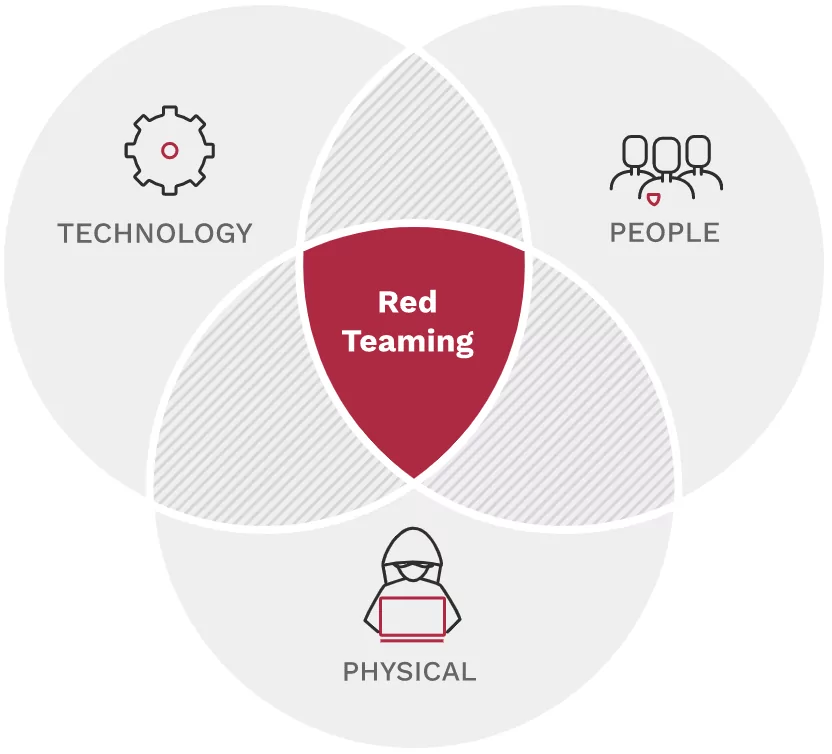
Red Teaming is a multi-layered attack simulation that assesses how well a company’s people, networks, applications, and physical security controls can survive an attack from a real-world opponent.
A red teaming assessment aims to show how real-world attackers can combine seemingly unrelated exploits to accomplish their objectives. It’s an excellent method to demonstrate that even the most advanced firewall is useless if an attacker can walk out of the data center with an unencrypted hard disk. Rather than relying on a single network appliance to protect sensitive data, employ a defense-in-depth approach and continually enhance your people, processes, and technology.
What Does Red Teaming Do?
A comprehensive red team examination will reveal weaknesses and dangers in the following areas:
- Networks, applications, routers, switches, appliances, sensitive data, phishing, and other aspects of technology and information security
- Personnel, independent contractors, departments, commercial partners, and so on are all examples of people.
- Offices, warehouses, substations, data centers, buildings, and other physical structures
By leveraging social engineering and physical, application, and network penetration testing to uncover ways to shore up your defenses, red teaming helps a corporation stay competitive while securing its business interests.
During a red team engagement, highly skilled security professionals simulate attack scenarios to reveal the potential physical, hardware, software, and human vulnerabilities. Bad actors and malevolent insiders can use red team engagements to infiltrate enterprise systems and networks and facilitate data breaches.
Red Teaming in Business
In today’s cyberthreat landscape, businesses must have the proper protocols, policies, and processes to keep their data safe, infrastructure strong, and, ultimately, make them resilient.
The 2013 Yahoo data breach was recently revised to have compromised close to 3 billion user accounts. The Equifax data breach surpassed the greatest publicly acknowledged intrusions ever revealed, with 145.5 million customers affected.
These hacks and the WannaCry and Petya intrusions are harbingers of things to come in the cyber world. With this in mind, businesses should test their systems and networks to see how vulnerable they are to a successful attack before an attacker does.
As we all learned in elementary school, you can’t grade your homework. You’ll need another pair of eyes on your ideas and plans if you want to stress-test them. A red team provides that. This type of independent evaluation is performed by a group separate from your usual planning staff.
Why Do You Need a Red Team?
Red teaming isn’t a superior planning method; it’s a method that improves your plans. There are numerous approaches to incorporating red teaming into your organization’s planning process. You can form a permanent or ad hoc red team in-house or employ an outside facilitator to conduct a red teaming review.
Regardless of which method you use, red teaming employs a variety of analytical, inventive, and contrarian tactics to test your planning assumptions, evaluate alternate viewpoints, and examine the potential for failure so that you may avoid it. These tools force you to look at your business as a competitor or newcomer, which can help you become a disruptor rather than a disruption in your sector.
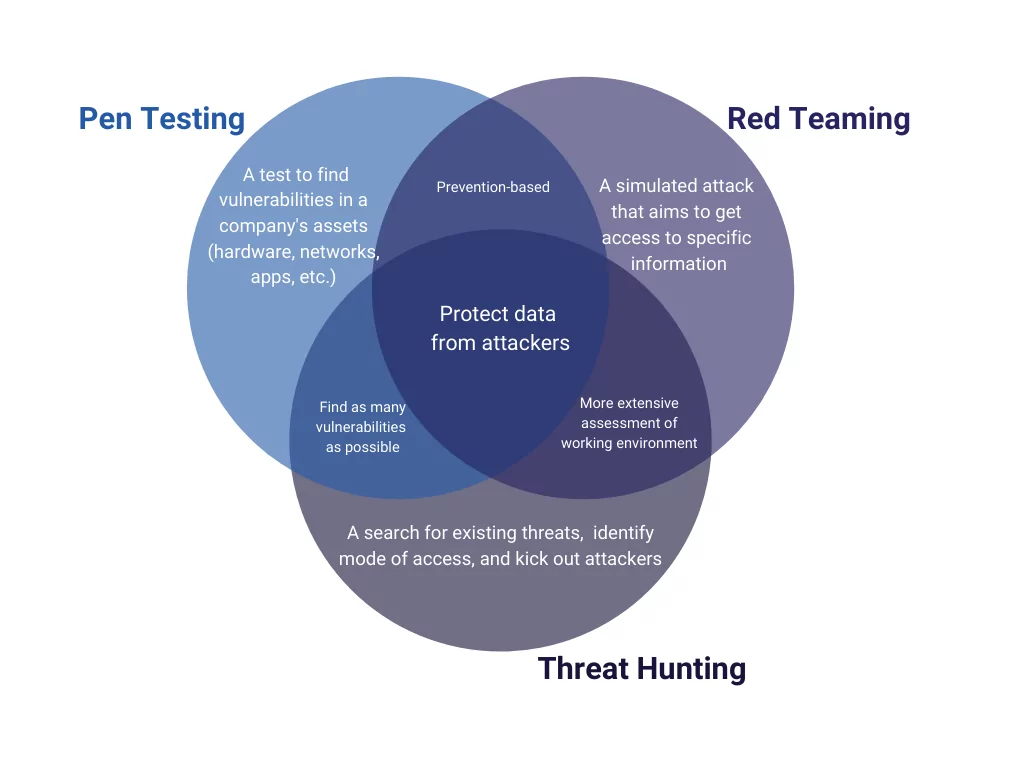
Difference Between Red Teaming and Penetration Testing
Penetration testing has long been used as a primary security precaution by companies worldwide. Due to time restrictions, however, a strategy with a more technical perspective may be necessary. Red teaming overcomes some of penetration testing’s constraints, allowing for a more realistic simulation of real-world threat scenarios.
Pen testing is crucial, but it is only one aspect of a Red Team’s work. Pen testers’ goal is to access a network frequently, whereas red team activities have broader objectives. Red Team drills simulate a more realistic APT scenario, complete with defensive techniques and risk analysis.
Red Teaming includes a minor amount of penetration testing. Evasion and persistence, privilege escalation, and exfiltration are all part of red teaming. The first step in the cyber death chain is penetration testing. The whole cyber death chain would be included in red teaming exercises.
How SOCRadar Can Help on Red Teaming
The Red team needs expanded threat intelligence to create realistic attack scenarios. With intelligence from dark web forums and hacker channels, IoCs, digital asset discovery, and many more modules, SOCRadar supports the establishment of a solid security posture for the known techniques, tactics, and procedures (TTPs) of threat actors.
With SOCRadar’s unique Extended Threat Intelligence (XTI):
- Discover your attack surface and have better visibility into external facing assets
- Protect your digital assets and have monitoring capabilities across all environments
- Prevent cyber attacks by gathering and processing the data extracted from various sources.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Get free access.

































