Exploitation Attempts Observed for Critical ownCloud Vulnerability (CVE-2023-49103)
Exploitation activity targeting ownCloud with the CVE-2023-49103 vulnerability has been observed, raising concerns within the cybersecurity community.
ownCloud, renowned as an open-source file server facilitating secure storage, file-sharing, and collaboration, recently drew attention due to the disclosure of three critical vulnerabilities, including CVE-2023-49103.
In parallel, CISA’s weekly vulnerability summary features these recent ownCloud vulnerabilities, currently categorized as “Severity Not Yet Assigned.” While official severity ratings await assignment, MITRE rates them as critical. Notably, CVE-2023-49103 is actively exploited, boasting a maximum CVSS score of 10. If successfully exploited, the vulnerability could result in unauthorized access to admin passwords, mail server credentials, and license keys, potentially leading to the escalation of malicious activities through the compromised information.
Vulnerability Overview
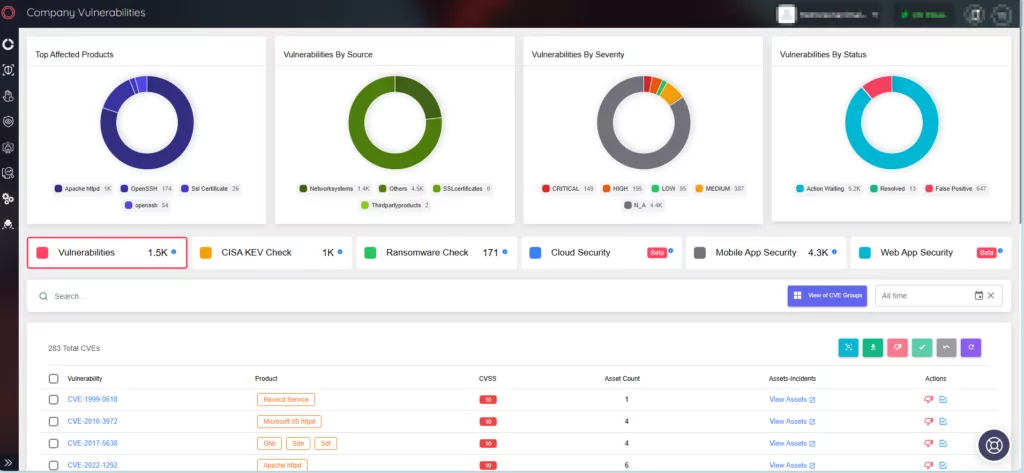
The CVE-2023-49103 vulnerability, with a maximum CVSS severity rating of 10, impacts ownCloud versions 0.2.0 to 0.3.0, residing within the “graphapi” app. The graphapi app, employing a third-party library (GetPhpInfo.php), exposes critical PHP environment configurations, unveiling passwords and keys.
This is because the library generates a URL that, when accessed, reveals the PHP environment’s configuration details (phpinfo). It includes all webserver environment variables; in containerized deployments, these variables may contain sensitive data such as admin passwords, mail server credentials, and license keys.
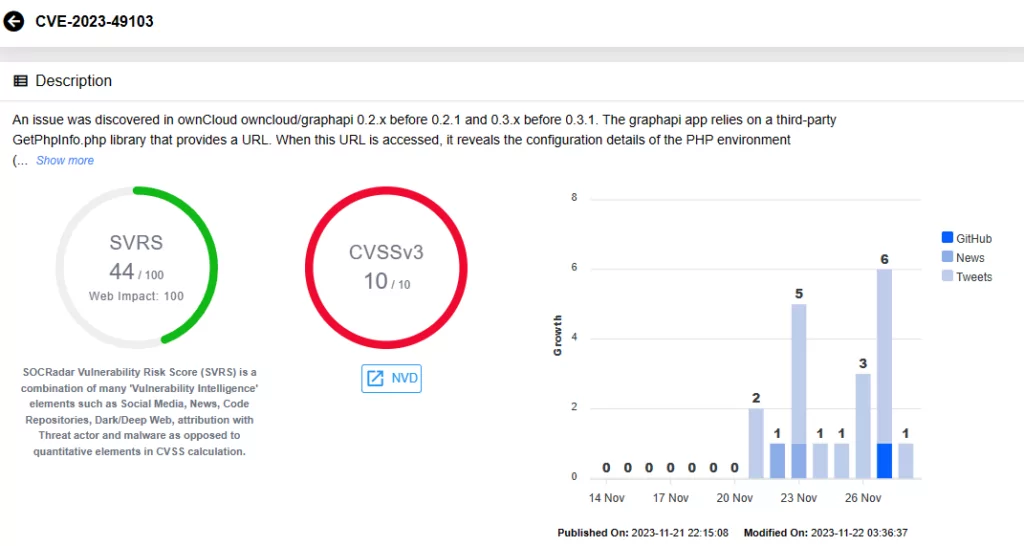
The Severity of the Situation: Observed Exploitation Attempts Targeting CVE-2023-49103 in ownCloud
GreyNoise has reported widespread exploitation of the CVE-2023-49103 vulnerability in real-world scenarios, starting as early as November 25, 2023.
The consistent targeting of software related to file-sharing represents an enduring trend. This trend underscores the possibility that threat actors’ attention may soon shift to ownCloud. This concern is exemplified by the impactful ransomware attacks on Progress’ MOVEit Transfer product by Clop Ransomware. Preceding the MOVEit incident, threat actors similarly exploited the GoAnywhere MFT vulnerability (CVE-2023-0669), resulting in a notable 91% increase in ransomware incidents.
A recent tweet from Shadowserver underscores the threat posed by the vulnerability, stating, “Not surprisingly given the ease of exploitation we have started seeing OwnCloud CVE-2023-49103 attempts.” The tweet serves as a warning, urging users to review the ownCloud advisory. Additionally, Shadowserver reports instances of ownCloud in scans, highlighting over 11,000 IPs currently accessible.

SANS, in their observations, has detected scans specifically targeting a URL affected by the CVE-2023-49103 vulnerability. The article outlines details about five IP addresses engaged in these scans, providing insights into their origin and activities.
These IPs, originating from Oracle’s cloud, a Tor exit node, H4Y in the US, and Portlane in the Netherlands, have scanned files within ownCloud instances. This pattern can suggest potential coordinated efforts by threat actors or botnets aiming to exploit the disclosed security flaw.
The SANS article also notes that attacks against ownCloud are not uncommon, with a consistent flow of attempts frequently targeting outdated vulnerabilities or exploiting weak passwords.
How to Fix the CVE-2023-40103 Vulnerability in ownCloud?
To address the CVE-2023-40103 vulnerability in ownCloud, disabling the graphapi app, as stated by ownCloud, is not an effective resolution. Due to the exposure of various potentially sensitive configuration details through phpinfo, even non-containerized ownCloud instances remain susceptible to exploitation by attackers. However, Docker-Containers before February 2023 remain unaffected.
ownCloud has outlined several mitigation methods in the advisory to address the exploitation of CVE-2023-49103. These methods include deleting a specific directory and changing compromised secrets.
About the Other Critical Vulnerabilities Disclosed by ownCloud (CVE-2023-49104, CVE-2023-49105)
Regarding the additional critical vulnerabilities disclosed by ownCloud, namely CVE-2023-49104 and CVE-2023-49105:
CVE-2023-49104, with a CVSS score of 8.7, is identified as a Subdomain Validation Bypass vulnerability.
An attacker can utilize a crafted redirect-url to bypass validation, allowing them to redirect callbacks to a Top-Level Domain (TLD) controlled by the attacker. This vulnerability is present in the oauth2 app before version 0.6.1 when the “Allow Subdomains” option is enabled.
As a workaround, ownCloud recommends that users disable the “Allow Subdomains” option, which disables the vulnerability, and harden the validation code in the oauth2 app.
CVE-2023-49105, with a CVSS score of 9.8, is an Authentication Bypass vulnerability. This flaw enables unauthorized access, modification, or deletion of any file without authentication, provided the username of the victim is known and the victim has no signing-key configured (by default behavior).
This vulnerability arises because pre-signed URLs can be accepted even when no signing-key is configured for the owner of the files. The vulnerability affects WebDAV API in ownCloud versions 10.6.0 to 10.13.0.
ownCloud advises denying the use of pre-signed URLs if no signing-key is configured for the owner of the files as a preventive measure against this vulnerability.
Enhance Security with SOCRadar’s Vulnerability Intelligence and Attack Surface Management
SOCRadar offers continuous monitoring of emerging security threats, regularly updating the platform with essential information about vulnerabilities. This includes details, mentions, Proof of Concept (PoC) exploits, lifecycle data, and the proprietary SOCRadar Vulnerability Risk Score (SVRS).
To access a wealth of information on the latest vulnerabilities, simply navigate to the Vulnerability Intelligence tab within the Cyber Threat Intelligence module of the SOCRadar XTI platform.
Furthermore, you can leverage the capabilities of the Attack Surface Management (ASM) module to actively monitor emerging vulnerabilities across your digital assets. This enables you to receive timely threat alerts and efficiently manage patching efforts, mitigating the potential impact on your organization.