Exploring MegaMedusa: The Streamlined DDoS Tool
Distributed Denial of Service (DDoS) attacks continue to pose significant challenges in cybersecurity. Tools like MegaMedusa have made it easier for individuals, regardless of their technical expertise, to launch potent DDoS attacks.
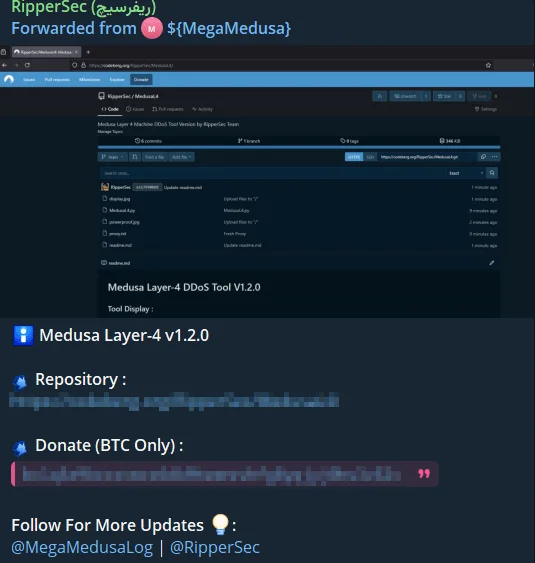
MegaMedusa ad in RipperSec’s Telegram channel
The Genesis of MegaMedusa
MegaMedusa is a Node.js-based DDoS tool developed by RipperSec, a pro-Palestinian hacktivist group. Established in June 2023, RipperSec has rapidly grown, accumulating over 5.000 subscribers on its Telegram channel by March 2025. The group engages in various cyber activities, including data breaches, website defacements, and DDoS attacks. MegaMedusa, their publicly available web DDoS attack tool, simplifies launching large-scale Layer 7 (application layer) DDoS attacks, making it accessible to a broader audience.

Telegram logo of RipperSec
Key Features of MegaMedusa
MegaMedusa incorporates several techniques to enhance the effectiveness of its attacks:
- Randomized Headers: The tool varies headers such as User-Agent, Accept-Language, and Referrer to mimic legitimate traffic from diverse sources.
- Dynamic Request Paths: Appending random query parameters and path segments creates unique URLs, complicating detection efforts.
- Variable HTTP Methods: The tool randomly selects HTTP methods (GET, POST, HEAD, etc.), adding unpredictability to the attack patterns.
- IP Spoofing: MegaMedusa utilizes headers like X-Forwarded-For to obscure the true origin of requests, making mitigation more challenging.
These features collectively make MegaMedusa a formidable tool for executing sophisticated DDoS attacks.
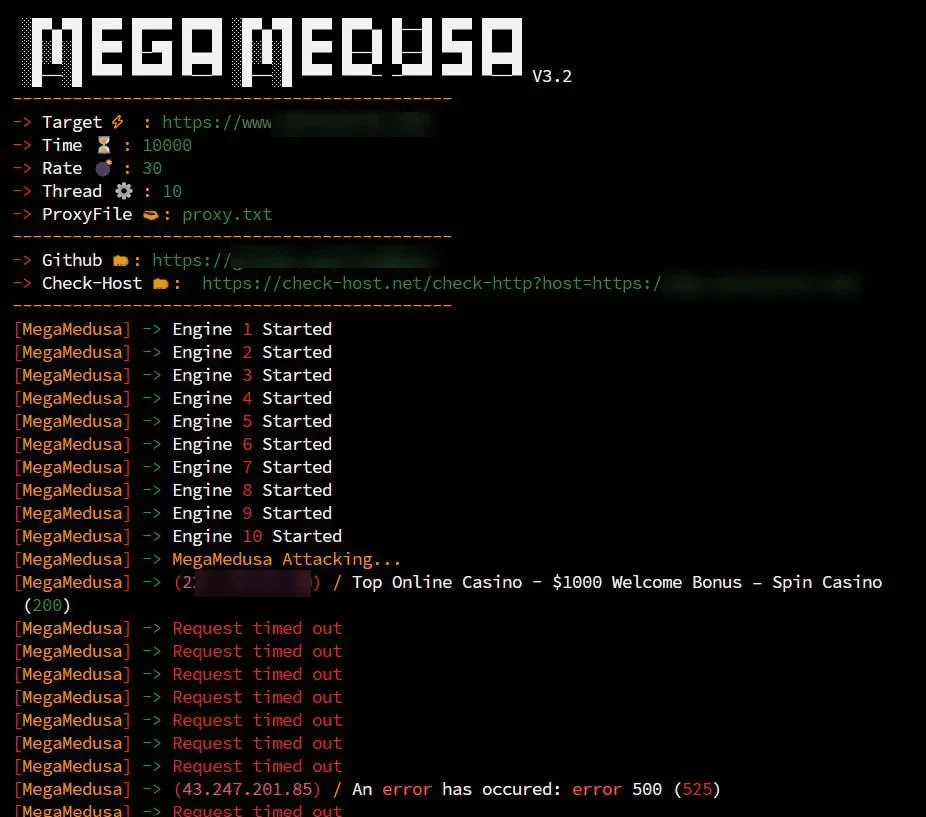
MegaMedusa’s control panel (Source: GitHub)
What is Layer-7 DDoS?
A Layer 7 DDoS attack is a type of Distributed Denial of Service (DDoS) attack that targets the application layer of the OSI model—the layer responsible for handling web requests. Instead of overwhelming a server with raw traffic like traditional network-layer attacks, Layer 7 attacks focus on exhausting a website’s resources by mimicking real user behavior. This makes them particularly difficult to detect and mitigate.
These attacks typically work by flooding web servers with requests that require significant processing power, such as accessing dynamic pages, querying databases, or loading heavy scripts. Attackers often disguise their traffic by rotating IP addresses, modifying headers, and using botnets to make the attack appear like legitimate user activity. Common techniques include HTTP floods, where attackers send massive numbers of GET or POST requests, and Slowloris attacks, which keep connections open for long periods to exhaust server resources.
Introducing MiniMedusa
MiniMedusa is a configuration package and via a parser it easily showcases a look into MegaMedusa.
Notable Features of MiniMedusa
MiniMedusa has several core features while optimizing for simplicity:
- User-Agent Management: The default User-Agent is set to axios/1.8.1, but users can customize it to suit specific attack scenarios.
- Target Restrictions: To prevent misuse, MiniMedusa includes safeguards against targeting specific top-level domains (TLDs), such as “.my” (Malaysia) and “.id” (Indonesia). Attempting to target these TLDs may cause the script to self-delete and reboot, especially if configured with sudo privileges without a password.
- Configuration Access: Users can browse various configurations and access current IP lists, facilitating tailored attack strategies.
Parsing the MiniMedusa
A parser developed by cudeso can read and interpret MiniMedusa’s output. You can specify a file for the output by enabling json_prettified_output and setting the file name, such as write_to_mini_medusa.json. This helps with configuration:
json
CopyEdit
{
“write_to_mini_medusa_json”: “mini_medusa_output.json”,
“json_prettified_output”: true
}
Passive DNS Lookup
To enable Passive DNS lookups, update the parser configuration to include DNS data. This allows MiniMedusa to retrieve historical DNS information:
json
CopyEdit
{
“db_json”: “True”
}
Reverse DNS Lookup
The parser also provides an option to perform Reverse DNS lookups. To enable this feature, add the following setting to the parser configuration file:
json
CopyEdit
{
“rdns_server”: “True”
}
Top-Level Domain (TLD) Check
For more refined results, you can implement domain filtering with specific TLDs. To filter for a particular TLD, such as .onion, add the following rule in the parser configuration file:
json
CopyEdit
{
“tld_check”: “.onion”
}
Example Output: Analyzing the Results
Once it’s configured, you can parse IPs and gather detailed data about network connections. Below is a sample of the output generated by the tool:
MegaMedusa config: Parsed 38307 IPs (2025-03-13)
Records
————
IP|ASN|CC|AS Name|RDNS|Domains
72.10.160.170|36666|CA|GTCOMM, CA|None|[]
154.236.177.101|36992|EG|ETISALAT-MISR, EG|HOST-101-177.236.154.nile-online.net.|[]
203.190.44.225|45317|ID|JATARA-AS-ID Jaringan Lintas Utara, PT, ID|None|[]
72.10.160.174|36666|CA|GTCOMM, CA|None|[]
115.127.5.146|24342|BD|BRAC-BDMAIL-AS-BD BRACNet Limited, BD|host-146.bracnet.net.|[]
…
Mitigation Strategies
The accessibility and user-friendly nature of tools like MegaMedusa lower the barrier to entry for conducting DDoS attacks, potentially increasing their prevalence.
To protect against DDoS attacks facilitated by these tools, organizations should consider the following measures:
- Deploy Web Application Firewalls (WAFs): WAFs can filter out malicious traffic and block common attack patterns associated with DDoS tools.
- Implement Rate Limiting: Limiting the number of requests from a single IP address can help mitigate the impact of volumetric attacks.
- Utilize Content Delivery Networks (CDNs): CDNs distribute traffic across multiple servers, absorbing and mitigating DDoS attacks more effectively.
- Engage DDoS Protection Services: Specialized services can provide real-time monitoring and automatic mitigation of DDoS attacks.
In Summary
MegaMedusa is yet another reminder of how easy it has become to launch powerful DDoS attacks with minimal effort. With tools like this becoming more accessible, organizations need to stay ahead with strong security measures. Investing in firewalls, rate limiting, and DDoS protection isn’t optional anymore—it’s a necessity. Cybercriminals aren’t slowing down, so neither should cybersecurity defenses.
IP Addresses without Privates IPs for MiniMedusa: Click Here
How Can SOCRadar Help?
SOCRadar offers advanced tools and services designed to help organizations enhance their security posture and effectively manage DDoS threats. With solutions like SOCRadar Labs’ DoS Resiliency and SOCRadar’s Threat Hunting, organizations can gain proactive protection against a range of cyber threats, including those posed by DDoS attacks.
- SOCRadar Labs DoS Resiliency: This tool helps businesses assess their vulnerabilities to DDoS attacks and provides critical insights into potential attack vectors. By leveraging this tool, organizations can fortify their systems, ensuring they are resilient against large-scale DDoS campaigns.
- SOCRadar’s Threat Hunting: With SOCRadar’s Threat Hunting capabilities, security teams can detect and mitigate potential threats before they escalate. The platform actively searches for signs of malicious activity, including DDoS threats, ensuring early detection and rapid response to attacks.