
Security Alert: Critical Flaws in MITRE Caldera and Parallels Desktop (CVE-2025-27364, CVE-2024-34331)
Two critical vulnerabilities, CVE-2025-27364 in MITRE Caldera and CVE-2024-34331 in Parallels Desktop, pose significant security risks, with one allowing Remote Code Execution (RCE) on Caldera servers and the other enabling Local Privilege Escalation (LPE) on macOS systems.
While the MITRE Caldera vulnerability is newly discovered, the Parallels Desktop flaw represents a previously known issue that remains unpatched. These vulnerabilities, if exploited, could grant attackers full control over compromised systems, leading to unauthorized access, data breaches, and even lateral movement within an organization’s network.
MITRE Caldera RCE Vulnerability (CVE-2025-27364)
CVE-2025-27364 (CVSS 10.0) is a critical remote code execution vulnerability in MITRE Caldera. This flaw arises from Caldera’s dynamic agent compilation functionality, which can be manipulated via crafted web requests, allowing attackers to execute arbitrary code remotely on compromised servers.
Given the platform’s extensive use in penetration testing and adversary emulation, this vulnerability poses a severe threat to organizations leveraging Caldera for red teaming and security automation.
Which MITRE Caldera Versions Are Affected?
Versions through 4.2.0 and 5.0.0 before commit 35bc06e are impacted, making it essential for users to upgrade immediately to a patched version.
The Exploitation Process Explained
It was discovered that Caldera’s agent compilation process can be manipulated via its unauthenticated API endpoint, allowing attackers to inject arbitrary commands during compilation. By abusing the -extldflags linker flag in GCC, an attacker can gain full control over the affected system. This issue affects all versions of Caldera predating commit 35bc06e, with most default configurations at risk.
What makes this vulnerability particularly dangerous is its lack of authentication requirements, meaning that an attacker does not need valid credentials to exploit the flaw. By leveraging the affected API, attackers can inject malicious code into the compilation process, resulting in the deployment of rogue Sandcat or Manx agents. These agents could then be used to execute commands on the compromised system, potentially leading to data exfiltration, persistence mechanisms, and even further attacks on connected assets.
Full technical details and a Proof-of-Concept (PoC) exploit are available in this MITRE Caldera documentation.
How to Mitigate the Risk
MITRE has patched the vulnerability in commit 35bc06e and version 5.1.0+. Users should take the following actions to minimize the risk:
- Update immediately to the latest patched version to prevent exploitation.
- Implement network segmentation to limit access to Caldera’s API endpoints.
- Apply strict access control measures to ensure that only authorized users can interact with Caldera’s compilation functionality.
- Monitor for unusual activity, such as unexpected agent compilations or anomalous API requests, to detect exploitation attempts early.
Gain Visibility and Control Over Your External Attack Surface with SOCRadar’s ASM
In today’s connected world, external-facing assets present a growing risk. With SOCRadar’s Attack Surface Management (ASM), you can continuously monitor your external assets, assess vulnerabilities, and gain visibility into your attack surface, including third-party risks and shadow IT.
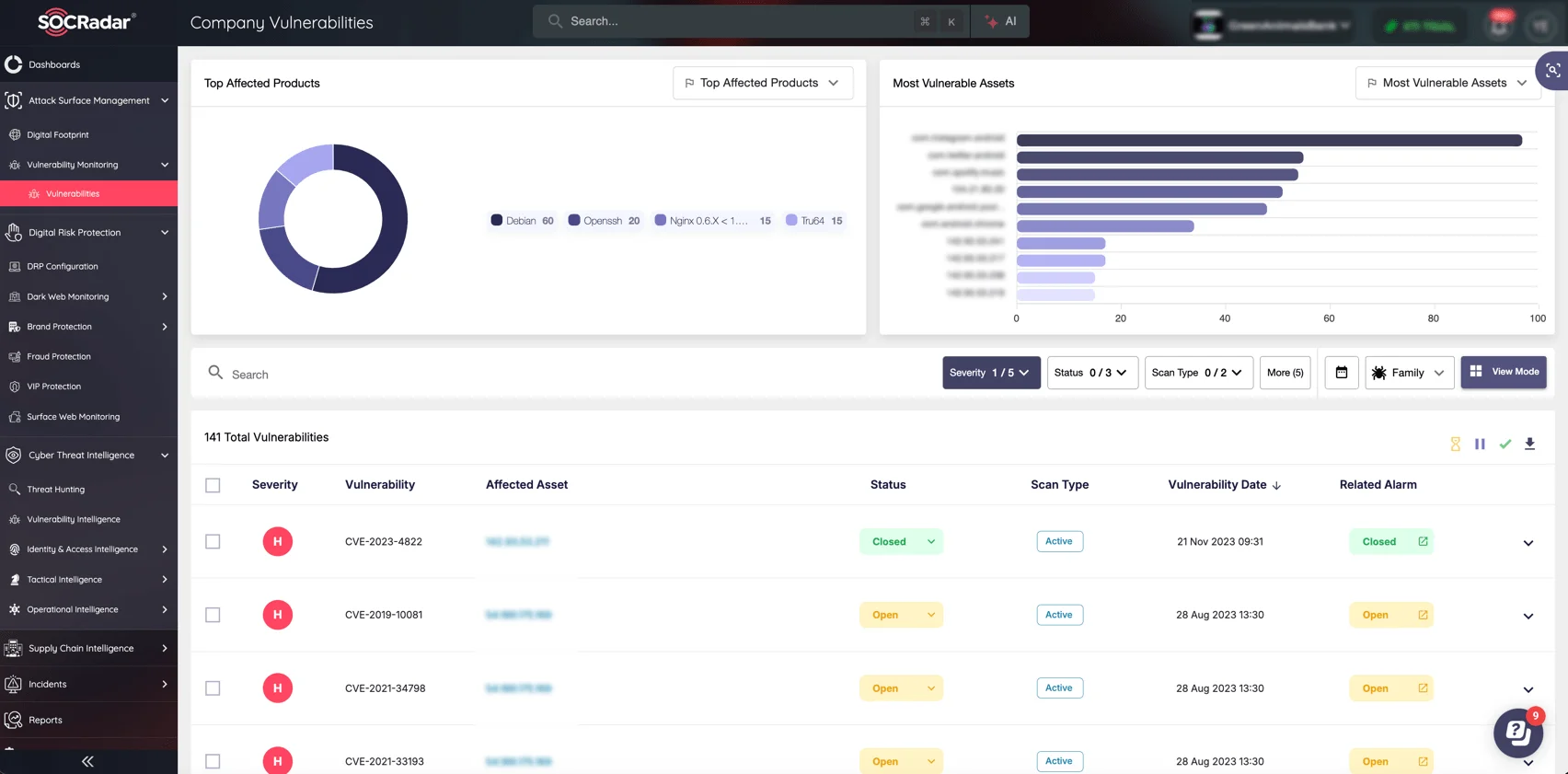
By securing your attack surface with SOCRadar’s ASM, you reduce your exposure to the most likely points of entry for cybercriminals.
SOCRadar’s ASM solution helps you track, analyze, and reduce exposure across your organization’s digital ecosystem, ensuring you’re aware of potential attack vectors before adversaries exploit them.
Parallels Desktop Zero-Day Vulnerability (CVE-2024-34331)
Exploitation methods have been disclosed for CVE-2024-34331 (CVSS 9.8), a critical zero-day privilege escalation vulnerability in Parallels Desktop. This flaw enables local attackers on macOS to gain root-level privileges, significantly increasing security risks for users of the virtualization software.
Parallels Desktop is a tool for running Windows and Linux environments on macOS, making this vulnerability especially worrisome for organizations that depend on its virtualization capabilities for seamless workflows, software development, and secure testing environments.
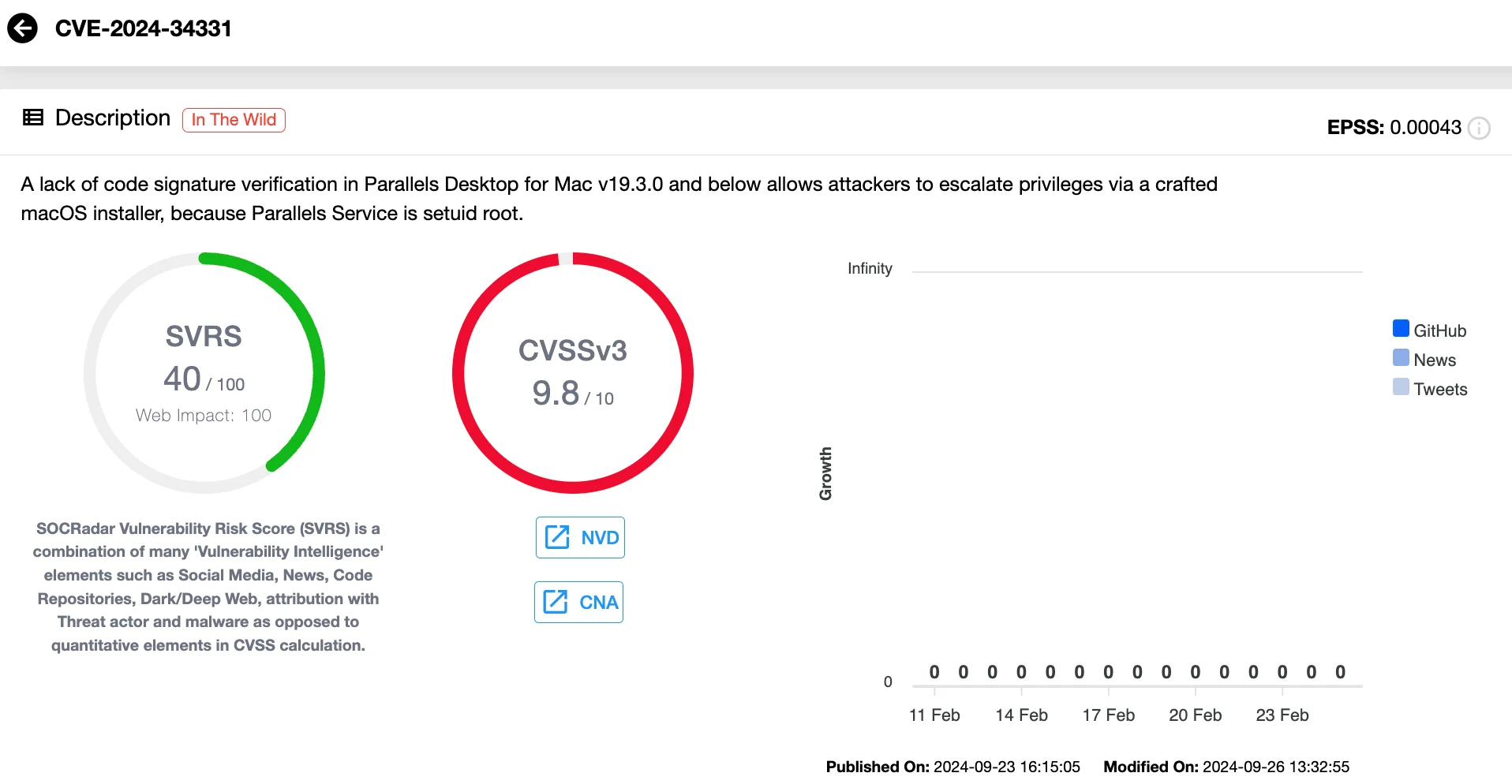
Vulnerability card of CVE-2024-34331 (SOCRadar Vulnerability Intelligence)
All versions of Parallels Desktop, including the latest 20.2.1 (55876), remain vulnerable, as no official patch has been released yet.
Tactics to Exploit This Vulnerability
It was discovered that attackers can take advantage of flaws in Parallels Desktop’s security validation process to gain root privileges on macOS.
One method involves replacing a verified Apple-signed binary with a malicious script just before execution, allowing unauthorized code to run with elevated privileges. Another technique exploits weaknesses in macOS’s code signing mechanism, enabling attackers to bypass security restrictions and inject malicious libraries into trusted processes.
Parallels has attempted to patch the issue, but researchers have found new bypasses for each fix. The persistence of these bypasses indicates a fundamental weakness in Parallels’ approach to security, as each patch attempt has either been ineffective or introduced additional vulnerabilities. As of now, all known versions remain vulnerable, and no official patch has been released.
How to Defend Against CVE-2024-34331
Until a patch is available, security teams should take the following steps to reduce the risk of exploitation:
- Remove SUID permissions from Parallels tools to prevent privilege escalation.
- Segment network access to limit exposure and isolate critical systems.
- Monitor for unauthorized file modifications, particularly in /Library/lpe, where attackers have been observed establishing persistence.
- Implement application whitelisting to block unauthorized binaries from executing with elevated privileges.
Security researcher Mickey Jin has provided further details, including a demo video of the exploit, in a technical write-up.
With the continuous rise of sophisticated exploits, security teams need to be more agile than ever. SOCRadar’s Vulnerability Intelligence enables organizations to stay informed about newly disclosed exploits, assess their risk levels, and gain actionable insights to prioritize their remediation efforts.
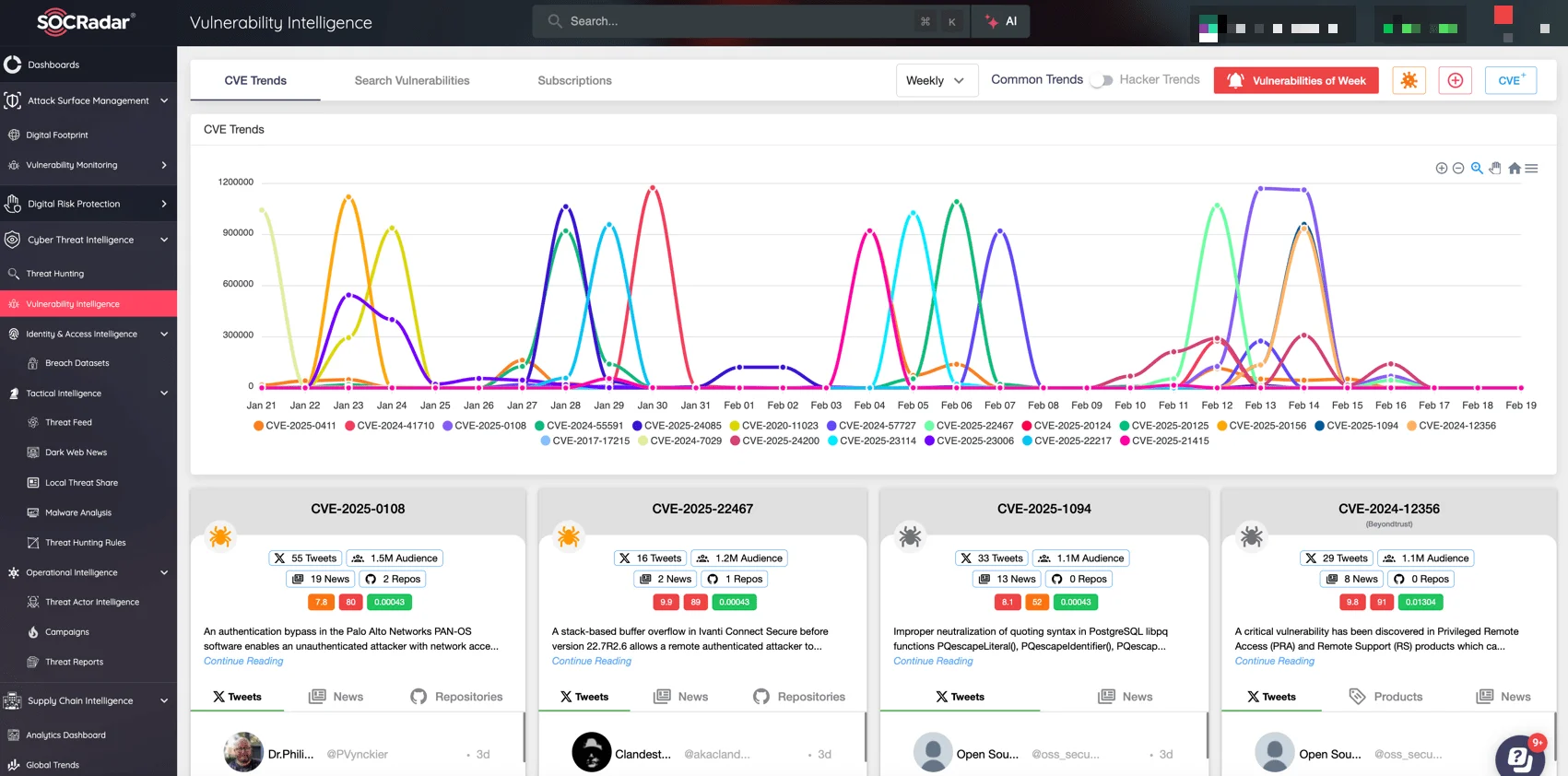
Stay ahead of exploits and minimize your exposure to cybercriminals by adopting SOCRadar’s proactive, intelligence-driven approach. (SOCRadar’s Vulnerability Intelligence)
Our platform goes beyond identifying vulnerabilities by offering a deeper understanding of attacker trends, the likelihood of exploitation, and how threats are evolving. SOCRadar’s intelligence-driven approach helps you focus on vulnerabilities that matter most, allowing you to allocate resources effectively.
SOCRadar’s Vulnerability Intelligence capabilities include:
- Real-time exploit tracking: Stay updated on newly disclosed vulnerabilities.
- Risk assessment: Prioritize vulnerabilities based on real-world threats.
- Actionable insights: Understand how attackers are weaponizing security flaws.
- Proactive alerts: Respond quickly with timely, actionable notifications.




































