FortiGate Devices Compromised by Stealthy Backdoor Technique
A backdoor discovered in Fortinet FortiGate devices has drawn attention due to its ability to persist even after patches are applied. The mechanism enables attackers to maintain read-only access to system files, potentially exposing sensitive configuration data.
The situation has raised serious concerns within the cybersecurity community about lingering vulnerabilities and the potential for long-term exploitation of seemingly secured systems.
How Was the Fortinet Symlink Backdoor Implemented?
The technique used in this case involves a symbolic link, commonly referred to as a “symlink.” A symlink is a type of file system pointer that functions much like a shortcut, redirecting access from one file location to another.
In FortiGate devices, the attackers created a symlink between publicly accessible language files and the device’s root directory. This allowed them to view sensitive system files through the SSL-VPN web interface, which is typically used for secure remote access.
Rather than exploiting a brand-new vulnerability, the attackers made use of known issues from previous years – particularly those documented in 2023 and early 2024. Once they gained access, they created the symlink within the user file system. This is a strategic location because it isn’t typically overwritten during firmware updates, allowing the backdoor to persist even after patches were applied.
Since the backdoor offered read-only access, it was less likely to trigger standard alerts or be detected through normal traffic analysis. This made detection difficult and gave the attackers a quiet way to maintain access.
Who Is Affected?
Based on telemetry from The Shadowserver Foundation, the number of compromised devices has surpassed 17,000. These affected systems span multiple industries and geographies, indicating a broad and opportunistic campaign rather than one that is narrowly targeted.
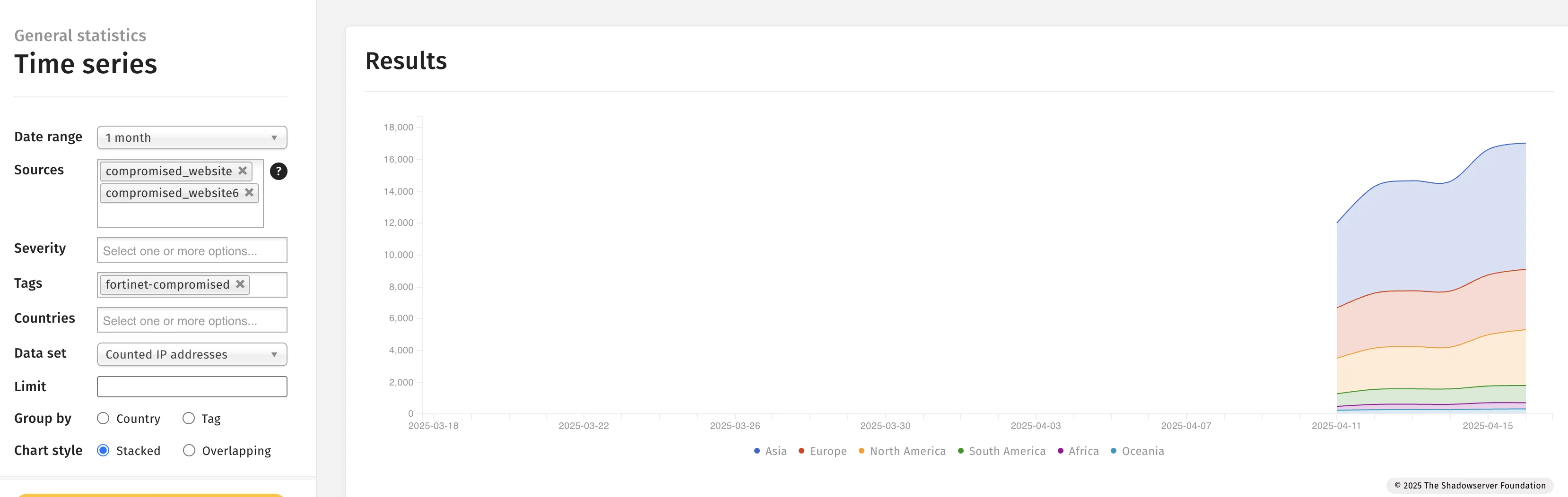
Number of compromised Fortinet devices (Shadowserver)
Devices with the SSL-VPN feature enabled are most at risk, as this is the gateway through which the attackers gain visibility into system files. On the other hand, organizations that never activated SSL-VPN on their FortiGate devices can consider themselves safe from this specific threat, though they should remain alert for related tactics.
Compromised systems may expose internal configurations, network details, and potentially even stored credentials. While attackers can’t directly modify files through this backdoor, access to sensitive data can facilitate future breaches, phishing campaigns, or more targeted intrusions.
Fortinet’s Response: Detection, Patching, and Customer Guidance
Fortinet responded promptly once the technique was identified. The company’s multi-pronged response includes:
- Developing AV/IPS signatures capable of detecting and eliminating the malicious symlink.
- Issuing firmware updates (versions 7.6.2, 7.4.7, 7.2.11, 7.0.17, and 6.4.16) that actively remove the backdoor upon installation.
- Updating the SSL-VPN web interface to block the serving of files outside expected directories.
- Privately notifying customers with affected devices and providing direct support for remediation.
The company emphasized responsible disclosure and collaborated with third-party threat monitoring organizations to enhance detection and response capabilities across the board.
Mitigation Steps for Organizations Using FortiGate Devices
If your enterprise relies on FortiGate devices, immediate action is essential. Fortinet recommends the following steps:
- Upgrade to the latest supported FortiOS version that includes the security enhancements and symbolic link removal features.
- Reset all user and administrative credentials stored on impacted systems to mitigate the risk of unauthorized access.
- Thoroughly audit system configurations to identify any potential tampering or unusual changes that may have been made during the compromise window.
- Consult Fortinet’s official technical recovery guide for a structured response process tailored to this specific threat.
Link: Fortinet Recovery Guide
To gain better visibility over assets exposed to the internet, including misconfigured VPN portals or outdated firmware, organizations can benefit from leveraging SOCRadar’s Attack Surface Management (ASM) module.
ASM helps security teams identify exposed services, unauthorized changes, and vulnerabilities like those exploited in this case, before attackers do. When used in conjunction with SOCRadar’s Vulnerability Intelligence, organizations gain contextual insights into emerging threats, enabling faster prioritization and response.
By actively monitoring your external footprint and correlating threat data, these tools help reduce the attack surface and strengthen your proactive defense strategy.
To learn more about Fortinet’s analysis of this activity and their ongoing response, you can read their official blog post here.