
How Private is Your VPN?
The term “Virtual Private Network” (VPN) refers to the ability to create a secure network connection while using public networks. VPNs encrypt your internet traffic and hide your true identity on the internet. Third parties will have a more challenging time tracking your online activities and stealing data due to this. The encryption is performed in real-time.
Why Should You Use a VPN Connection?
When you connect to the internet, your ISP sets typically up to your connection. It uses your IP address to track you. Your network traffic is routed through the servers of your Internet service provider, who can log and display everything you do online.
Although your Internet service provider may appear trustworthy, it may disclose your surfing history with advertising, the police or government, and other third parties. Cybercriminals might also target Internet service providers: Your personal and confidential information may be compromised if they are hacked.
This situation is especially critical if you use public Wi-Fi networks frequently. You never know who is watching your online activities or what they might steal from you, such as passwords, personal information, financial information, or even your complete identity.
How Does VPN Work?
VPN tunneling establishes a secure point-to-point connection that is impenetrable to unauthorized users. A tunneling protocol is used to create the tunnel over existing networks. Different tunneling protocols, such as OpenVPN or Secure Socket Tunneling Protocol (SSTP), will be used by other VPNs.
The tunneling protocol utilized will vary depending on the VPN’s platform, such as SSTP on Windows OS, and provide variable data encryption levels. A VPN client (software application) must be installed locally or in the cloud on the endpoint device. In the background, the client will be running. Unless it causes performance concerns, the VPN client is invisible to the end-user.
A VPN tunnel connects a user’s device to another network, masking its IP address and encrypting data. This is how attackers or others attempting to obtain access to an individual’s actions will be able to see private information.
The tunnel will connect a user’s device to an exit node in a different place, giving the impression that the user is there.
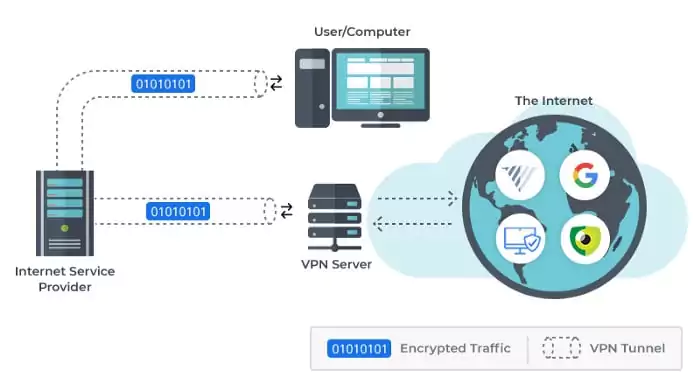
VPNs link a user’s search history to the IP address of the VPN server. VPN services will have servers in many geographical areas, making it appear as if the user is from any of those locations.
VPNs can impact performance in a variety of ways, including the speed of customers’ internet connections, the protocol types that a VPN provider can utilize, and the type of encryption used. Poor quality of service (QoS) outside the control of an organization’s information technology (IT) department can also impair performance in the enterprise.
In some VPN products, a kill switch is a last-resort security mechanism.
If the VPN connection is lost, the kill switch will unplug the device from the internet, preventing the device’s IP address from being exposed.
Kill switches come in two varieties:
1- Active Kill Switch Protocols: When a device is linked to a VPN, active kill-switch protocols prohibit it from connecting to insecure networks. It is disabled when not connected to the VPN, aside from server outages.
2- Passive Kill Switch Protocols: Protocols with a passive kill switch are more secure. Even when the device is unplugged from the VPN server, they prevent it from connecting to non-VPN connections.
Pros and Cons of VPN
Pros:
– Security
– Privacy
– No ISP bandwidth throttling
– Lower support costs
– Geo-blocked content access
Cons:
– Slower internet
– Activity logs
– Low-quality options that undermine the security
– Shared IPs
After considering all the advantages and disadvantages, you’ve probably concluded that a VPN is required for active internet users.
VPN services improve your online experience in various ways, from securing your personal information to avoiding content censorship. However, before you purchase a VPN, you should analyze the top VPN services available and select the one that best meets your needs.
Discover SOCRadar® Free Edition
With SOCRadar® Free Edition, you’ll be able to:
- Discover your unknown hacker-exposed assets
- Check if your IP addresses tagged as malicious
- Monitor your domain name on hacked websites and phishing databases
- Get notified when a critical zero-day vulnerability is disclosed
Free for 12 months for 1 corporate domain and 100 auto-discovered digital assets.
Try for free


































