Fortinet 0-Day, Spotify Checker Shared, and STX Leak Campaign
SOCRadar’s Dark Web Team has uncovered a new round of malicious activity across hacker forums this week. Threat actors are auctioning off 80,000 credit card records and claiming to sell a zero-day exploit affecting Fortinet FortiGate firewalls. A broader campaign, dubbed “STX Database Collection,” appears to be targeting multiple email service providers beyond SendGrid, with over 10 million records allegedly compromised. Additional posts include the leak of password manager exports from two separate companies, as well as a new Spotify account checker tool being shared to enable credential stuffing attacks.
Receive a Free Dark Web Report for Your Organization:
Alleged 80K Credit Cards are on Sale
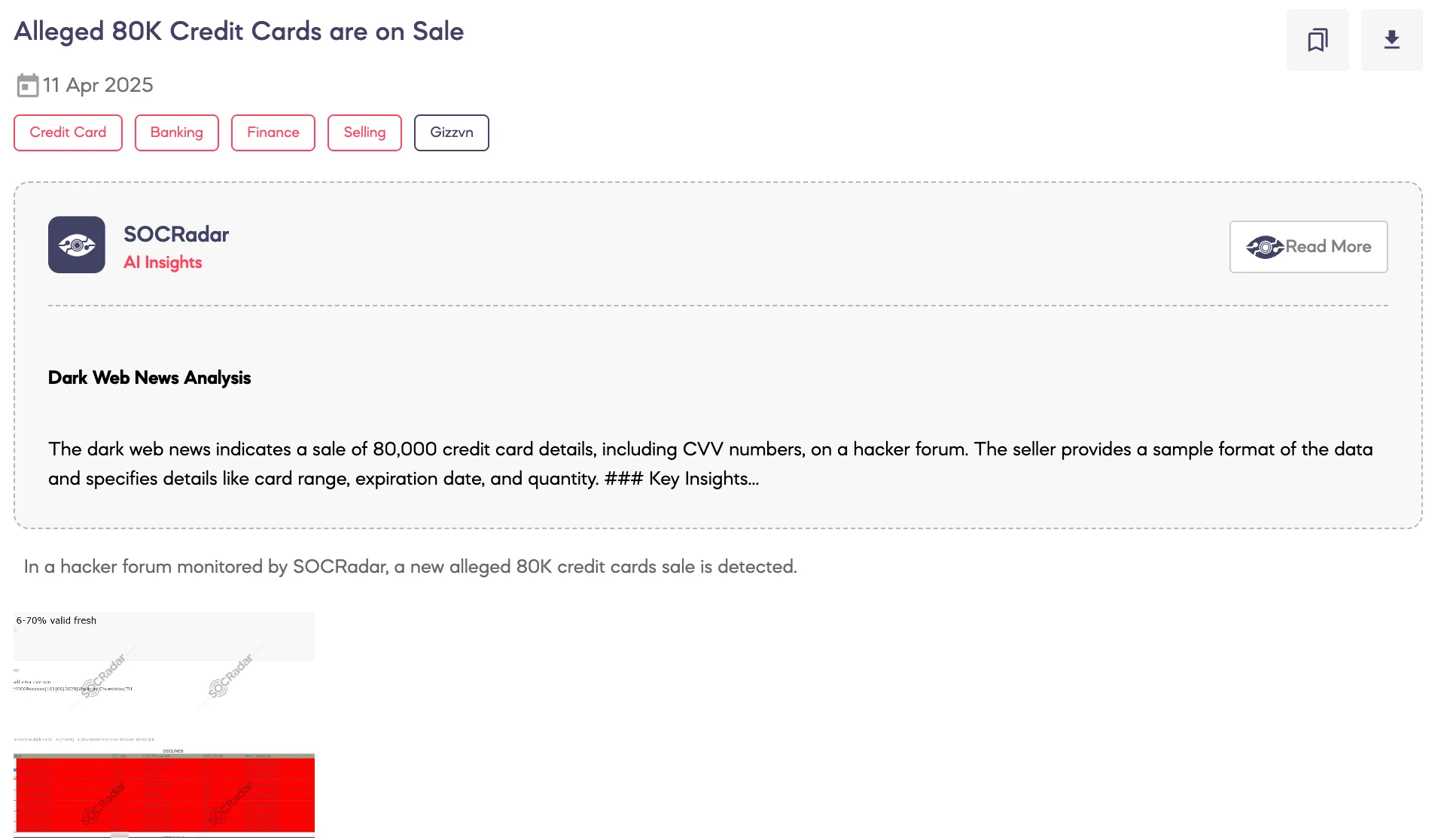
SOCRadar Dark Web Team has detected a new post on a dark web forum in which a threat actor claims to be selling a set of 80,000 credit card records.
According to the threat actor, the dataset contains full card details, including the card number, CVC code, expiration date, and cardholder name. The sample format aligns with CVV dumps commonly traded in underground fraud markets.
The threat actor notes that the auction starts at 400,000, with 30,000 increments. A blitz price of 500,000 is also set – this refers to a direct purchase option that bypasses the bidding process entirely. The listing is said to be available for 24 hours, possibly to pressure potential buyers with limited-time urgency.
While the authenticity of the dataset remains unconfirmed, if legitimate, the scale and nature of the offer could pose serious risks in terms of financial fraud and cardholder security.
0-Day Exploit Sale Is Detected for Fortinet
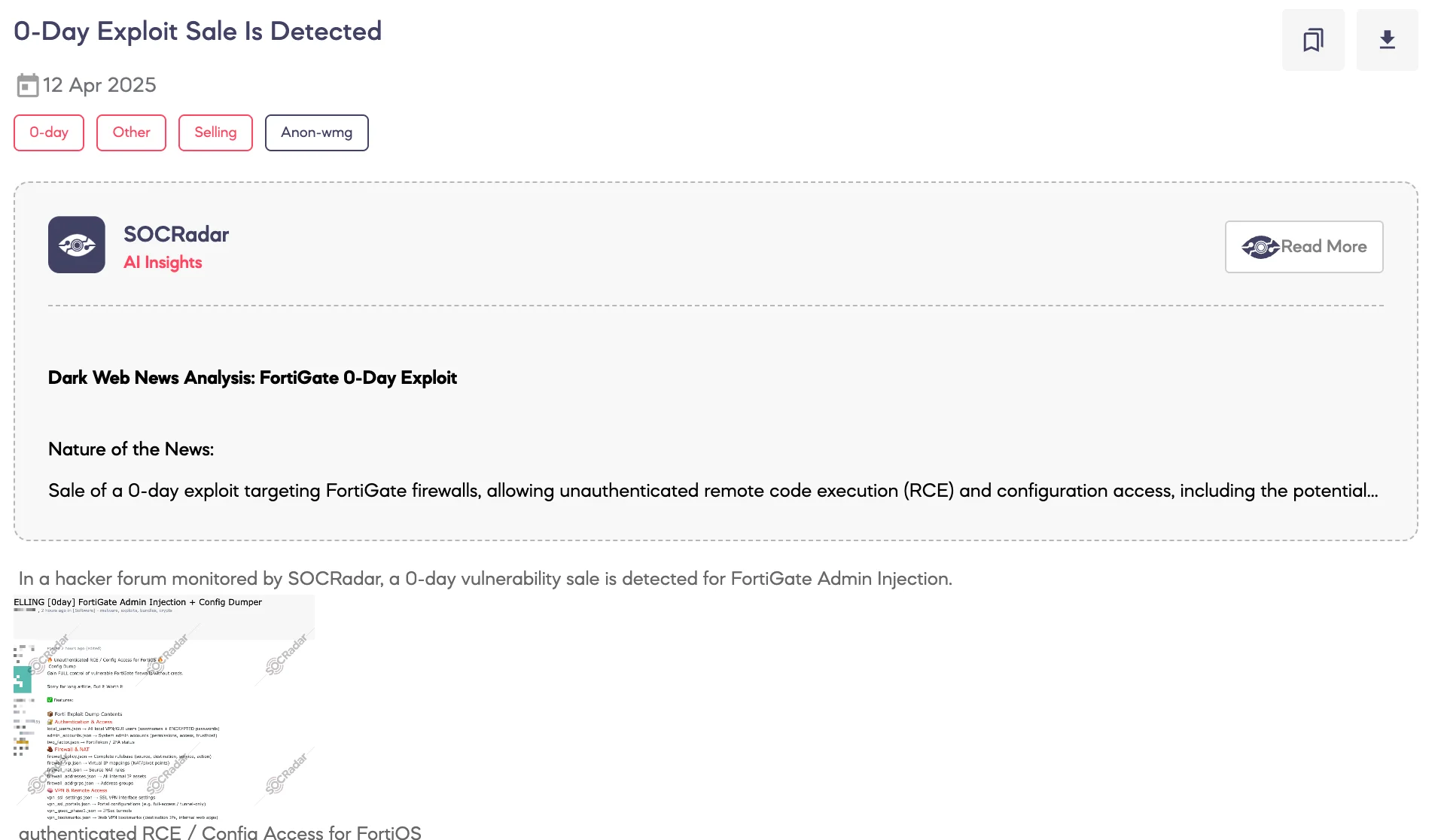
SOCRadar Dark Web Team has identified a post on a dark web forum in which a threat actor claims to be selling a zero-day vulnerability affecting Fortinet FortiGate firewalls. The exploit reportedly allows authenticated remote code execution and full configuration access on systems running FortiOS.
According to the threat actor, the vulnerability enables complete administrative control of vulnerable FortiGate devices without requiring valid credentials. The exploit package is described as providing access to configuration files, user data, firewall rules, VPN settings, logs, certificates, and other critical system components.
The threat actor is offering the full exploit and data dump for $6,500. While the validity of the exploit remains unverified, the level of access described suggests potentially critical implications for organizations using unpatched FortiGate devices.
Alleged Email Service Data Breach Expands Beyond SendGrid
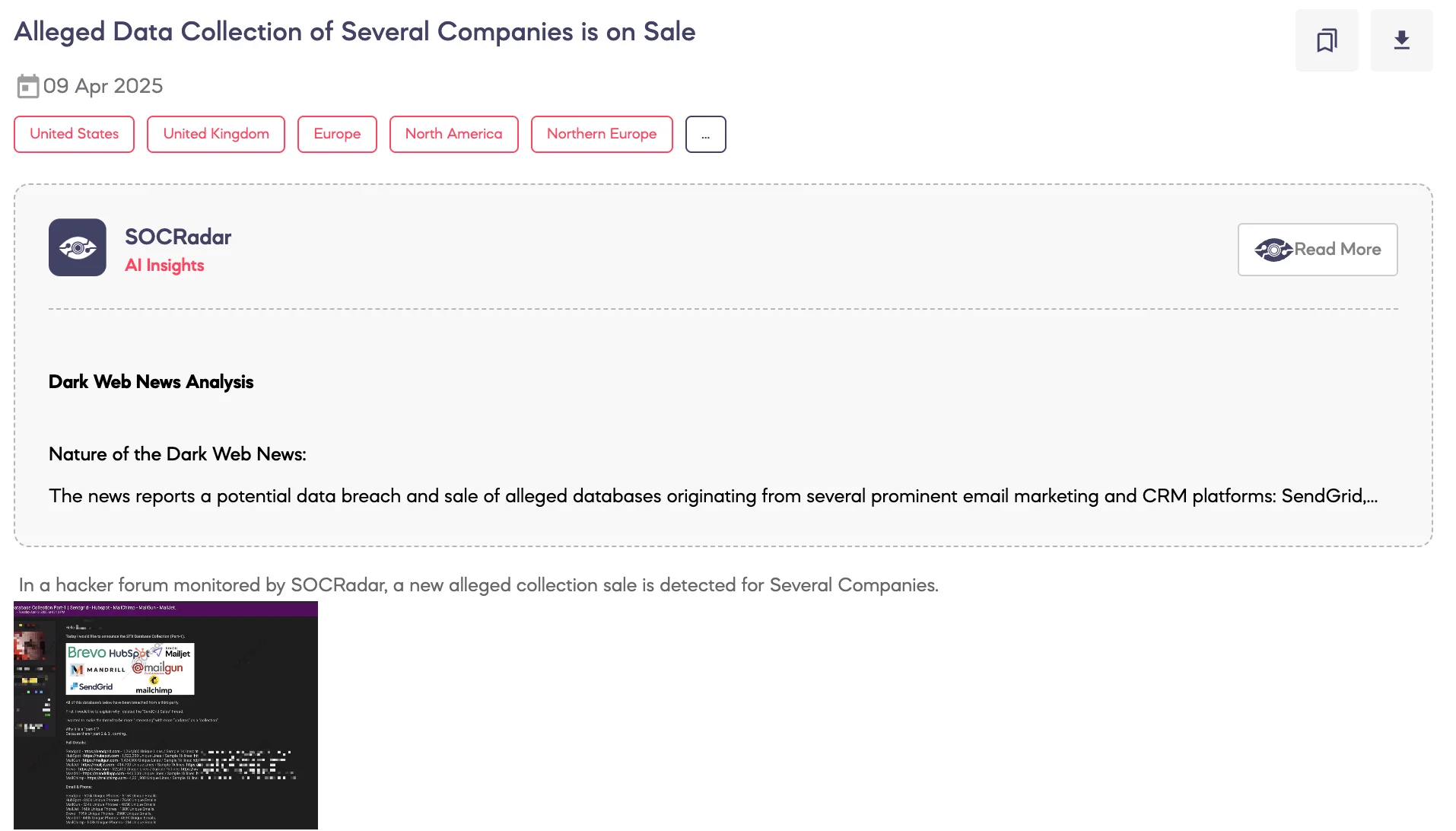
SOCRadar Dark Web Team has identified a new post on BreachForums where a threat actor using the alias “Satanic” has restructured a previously shared leak into a broader campaign under the name “STX Database Collection (Part-1)” – a label explicitly created by the threat actor.
Published on April 8, 2025, the updated post now claims to include data from several major email platforms: MailChimp, HubSpot, MailGun, MailJet, Mandrill, and Brevo. According to the threat actor, the total dataset contains more than 10 million records, allegedly exposing sensitive contact and business information.
The threat actor asserts that the compromised data includes email addresses, phone numbers, and company-level metadata, which may indicate a widespread compromise of platforms widely used for marketing and communication.
In the same post, the threat actor also mentioned that Part-2 and Part-3 of the so-called STX collection will follow soon, implying an ongoing campaign targeting email service providers.
While the authenticity of the data remains unverified, the scale of the claim – if confirmed – could pose a serious risk to both the affected platforms and their users.
Alleged Password Manager Exports of 2 Companies are Leaked
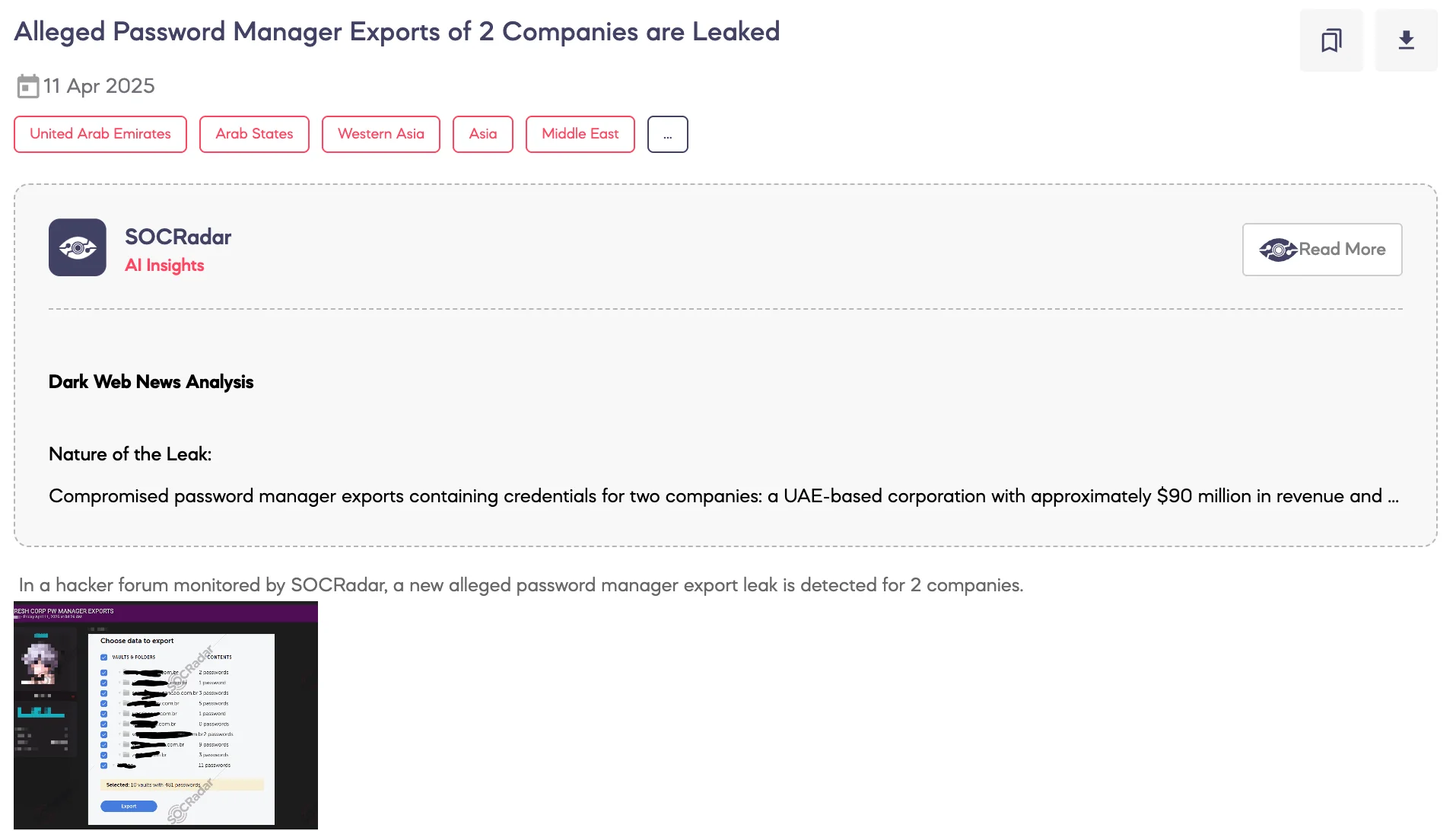
SOCRadar Dark Web Team has identified a new dark web post in which a threat actor claims to be selling password manager exports belonging to two separate companies.
According to the threat actor, the first target is a UAE-based corporation with $90 million in revenue, allegedly exposing access to sensitive infrastructure such as an ESET business panel, AWS credentials with two-factor authentication, Fortinet systems, and RDP configurations.
The second entity is said to be a Brazilian corporate group generating $10 million in revenue, with similar sensitive access reportedly exposed – including AWS credentials (2FA-enabled), Docker environments via Portainer, and other internal services.
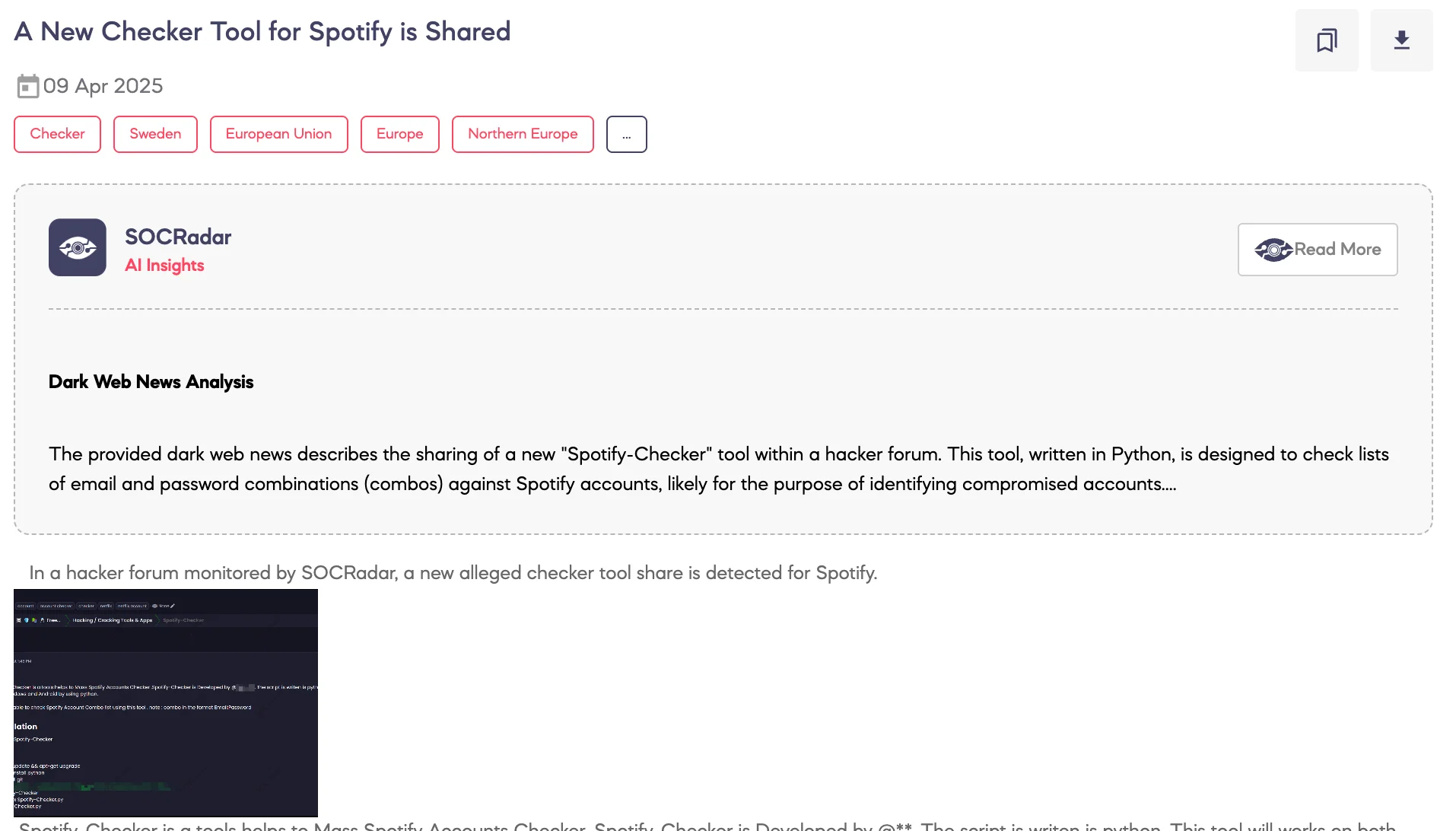
A New Checker Tool for Spotify is Shared
SOCRadar Dark Web Team has detected a new post on a dark web forum in which a threat actor claims to have shared a custom-built tool designed to perform mass Spotify account checks.
According to the threat actor, the tool – referred to as “Spotify-Checker” – is written in Python and is compatible with Linux, Windows, and Android systems. It is allegedly capable of testing large Spotify credential lists (combo lists) formatted as email:password pairs.
The threat actor has shared step-by-step installation instructions for all major platforms, including the use of Git to clone the tool from a GitHub repository and run it directly using Python.
Although the tool’s functionality has not been independently verified, such tools are often used by threat actors to automate credential stuffing attacks against popular platforms. If effective, this checker could enable unauthorized access to large volumes of Spotify accounts using previously leaked credentials.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.