Fortinet Reveals Critical Vulnerability in FortiSIEM Report Server (CVE-2023-36553): Patch Now
Fortinet, a leading cybersecurity provider, has recently issued an advisory for a critical vulnerability impacting its FortiSIEM Report Server. The vulnerability poses a serious risk, potentially allowing remote and unauthenticated attackers to execute malicious commands on vulnerable instances.
The FortiSIEM Report Server, an optional component of the Fortinet’s Security Information and Event Management (SIEM) solution, serves as a centralized repository for storing and managing FortiSIEM reports.
About the Vulnerability Affecting FortiSIEM Report Server
Fortinet characterizes the vulnerability, designated as CVE-2023-36553 with a critical CVSS rating of 9.8 (on NVD), as an OS Command Injection vulnerability resulting from improper neutralization of special elements.
CVE-2023-36553 allows remote, unauthenticated attackers to execute unauthorized commands by sending specially crafted API requests to the FortiSIEM report server.
Researchers state that this vulnerability is a variant of a previously patched security issue, namely CVE-2023-34992. This earlier critical OS Command Injection vulnerability affecting FortiSIEM was addressed by Fortinet in October 2023.
Are There Any Reports of Exploitation?
As of now, there are no known instances of exploitation regarding the CVE-2023-36553 vulnerability in FortiSIEM Report Server.
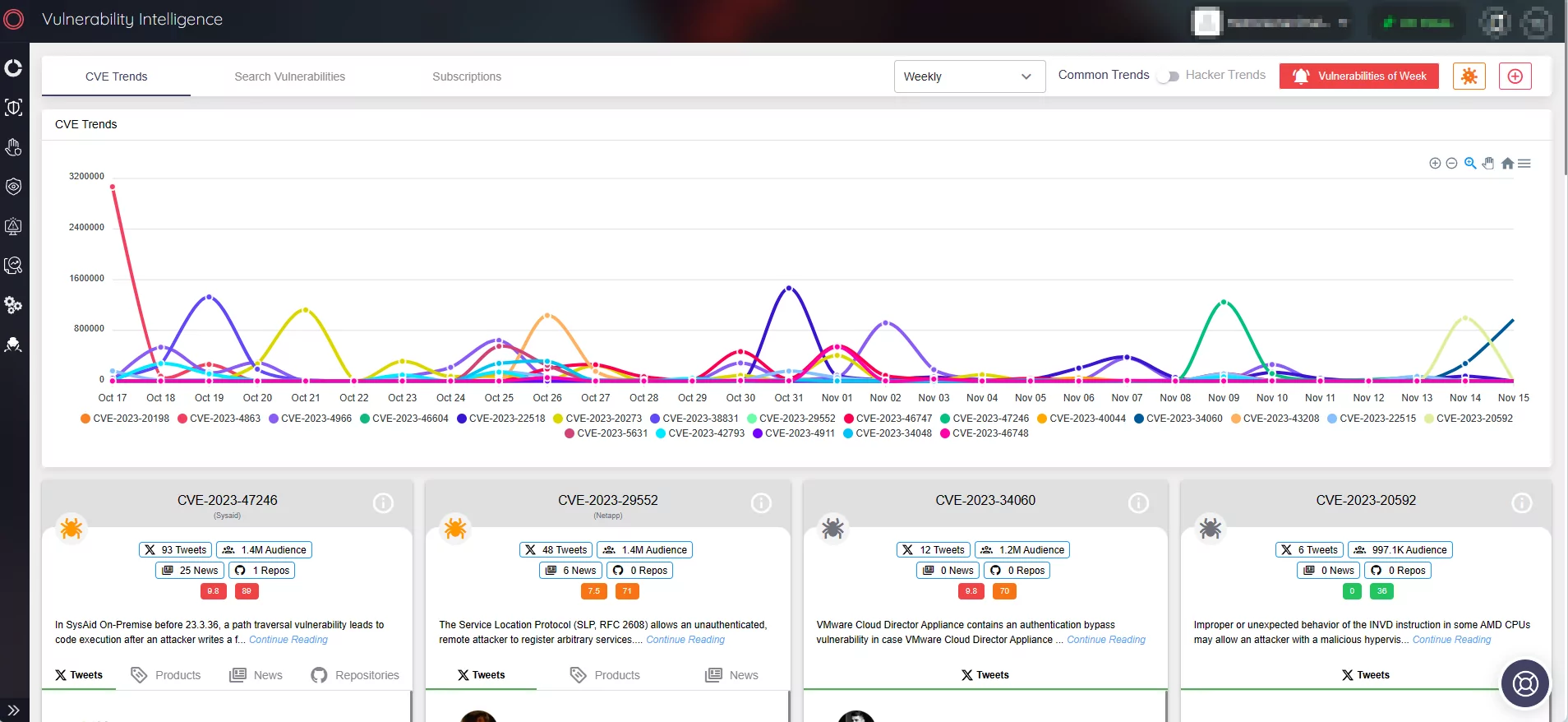
To monitor the timeline of the vulnerability, you can view the vulnerability card on SOCRadar’s platform, through Vulnerability Intelligence.
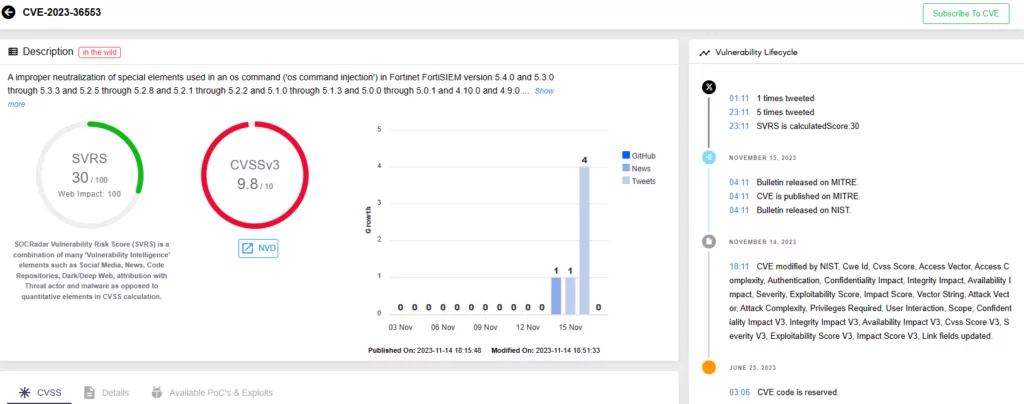
With the vulnerability lifecycle section, you can view all the updates and mentions related to the CVE. This way, you can stay informed and know precisely when exploitation occurs or if there are any changes to its information.
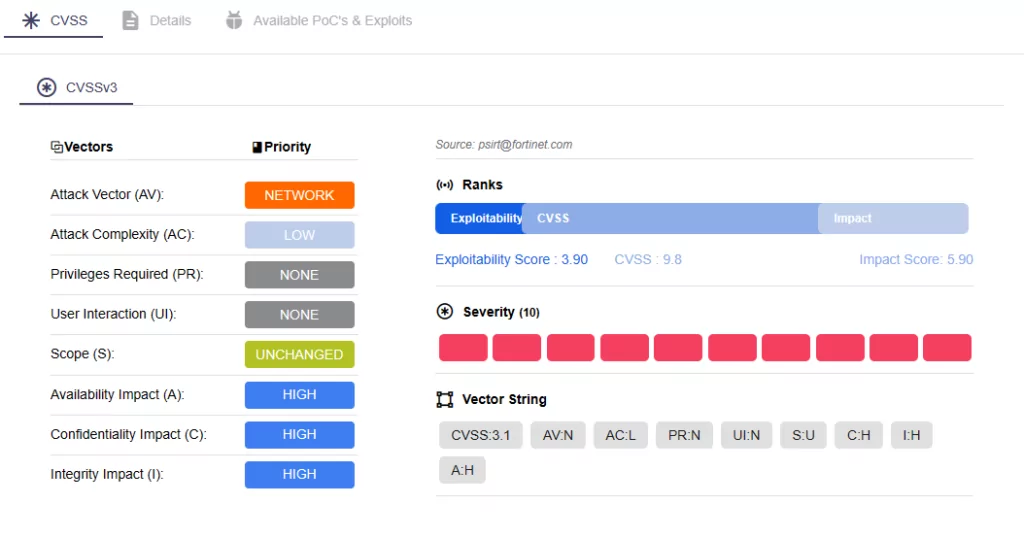
Additionally, the vulnerability card offers a glimpse into the CVSS metrics and the CVE’s exploitability, and it receives updates whenever Proof-of-Concept exploits become publicly available.
How to Fix the CVE-2023-36553 Vulnerability?
Fortinet has issued patches for the vulnerability and recommends that customers update their FortiSIEM versions to the following versions, or later, to avoid security risks:
- 7.1.0
- 7.0.1
- 6.7.6
- 6.6.4
- 6.5.2
- 6.4.3
How Can SOCRadar Help?
Every discovery of a vulnerability serves as a solid reminder for organizations to stay vigilant and address vulnerabilities promptly.
You can leverage SOCRadar’s Attack Surface Management (ASM) module for constant monitoring of digital assets. The solution ensures that you are aware of emerging security issues in your organization’s environment and provides real-time alerts.
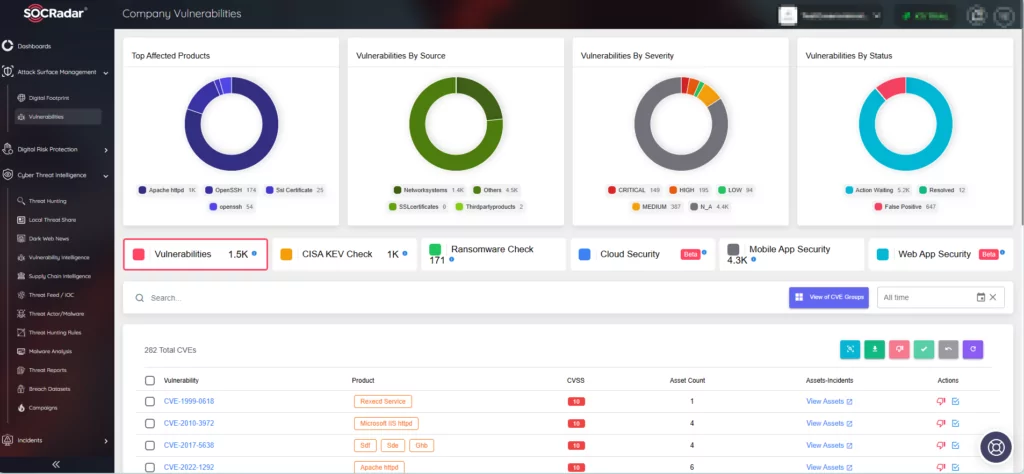
Moreover, with Vulnerability Intelligence, you can gain access to detailed insights into threat severity, affected systems, and exploitation activity. This helps in making informed decisions and enhancing your cybersecurity posture.