
Freely Discover Dark Web Threats of Your Organization: Dark Web Scan Report
The dark web is a hotbed of dangers, a host for various cyber threats due to its nature. Each day, illicit markets overflow with harmful content, forums burst with stolen data, and threat actors eagerly seek profit from every possible chance. They exchange fraud tactics and sell malware and exploits.
The dark web, where anonymity prevails, poses serious risks to individuals, businesses, and governments.
One of the most troubling aspects of the dark web is its bustling illegal marketplaces, where stolen information and hacking tools are easily bought and sold. Cybercriminals exchange stolen credit card details, login credentials, and other sensitive data, which can be exploited for financial gain or used to commit identity theft and fraud.
Moreover, the dark web forums serve as a hub for cybercriminal networks to collaborate and exchange knowledge and resources. Forums and chat rooms abound with discussions on hacking techniques, malware development, and the latest vulnerabilities waiting for a threat actor for exploitation. This collective intelligence enables threat actors to continuously evolve their tactics to evade detection and maximize their impact.
Below you will see a table about the increase in dark web threats. During the last year, dark web activity targeting the most mentioned countries in malicious forums, which are the USA, India, and the UK, accounts for more than 25% of all the activities directed at those states on the dark web. The fact that only one year of malicious activity such as selling data or hacking tools is more than a quarter of the total malicious actions targeting that country shows a clear picture of the rising threats from the dark web in recent years and the importance of monitoring there.
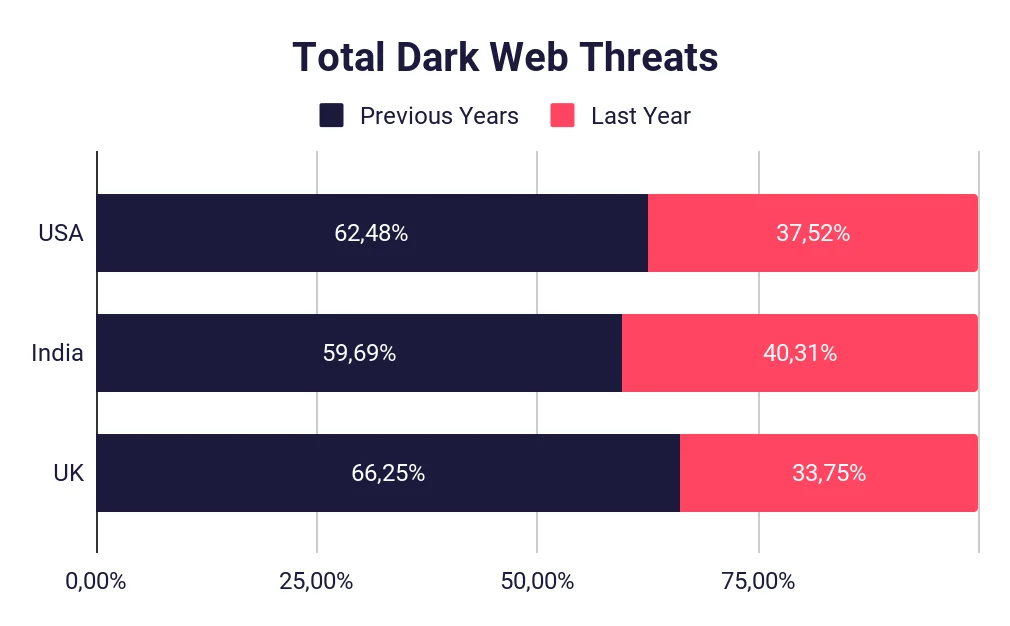
Dark web threats targeting a group of states
Benefits of Dark Web Monitoring
Monitoring dark web threats offers significant advantages for organizations by providing valuable insights into the latest hacking techniques such as malware variants, and exploit kits used by cybercriminals. This intelligence allows organizations to understand the tactics, techniques, and procedures (TTPs) of threat actors, enabling them to fortify their security measures more effectively. In addition to gaining insights into malicious actions, organizations can learn the latest exploitations from discussions in malicious forums and patch vulnerabilities, update security protocols, and implement additional layers of protection.
Furthermore, by identifying compromised credentials or leaked information on the dark web, organizations can take action to mitigate further damage. Actions such as resetting passwords, notifying affected individuals, and scanning stealer logs for further information are especially beneficial in addressing these threats swiftly.

SOCRadar’s whitepaper on Stealer Logs
Check out our report on Stealer Logs, where SOCRadar analysts present their findings obtained by examining 70 million stealer logs. These logs can often include personal information ranging from users’ password usage habits to antivirus software preferences. This whitepaper uses data from SOCRadar to provide insights into what information stealers may contain and what information is being targeted.
SOCRadar’s comprehensive reports leverage the analysis of stealer logs to offer enhanced intelligence to its members. These reports provide valuable intelligence on various aspects of the security landscape, obtained through the analysis of a variety of data points collected from the depths of the dark web. Millions of compromised passwords, emails, and other personally identifiable information (PII) lay exposed, ripe for exploitation by threat actors.
Delving into dark web intelligence extends beyond merely monitoring threat actor posts; it entails obtaining precise details about one’s organization’s structure and gaining actionable insights. You can sign up quickly and explore our in-depth reports for accurate intelligence.
Workings of Dark Web Monitoring Tools
Dark web monitoring tools continuously scan the dark web for specific information, employing web crawling techniques to traverse hidden services, forums, and marketplaces. These tools utilize keyword-based searches to identify sensitive data such as leaked credentials, personal information, or discussions concerning illicit activities.
However, gathering information from the dark web alone is inadequate. In today’s landscape of escalating digital risks and increasingly sophisticated attacks, crafting actionable insights holds greater significance than presenting raw data.
For the necessary insights, you can gain immediate access to information on the dark web about your organization’s assets with SOCRadar’s Free Dark Web Report. What’s in the report?

Threat Severity is an indicator of the dark web risks for your organization. Dark web risks for organizations can encompass a range of threats, from data breaches and intellectual property theft to illegal trade in sensitive information and cybercrime collaboration. With this information, you can see the risk level of your organization.

Dark Web Mentions is a collection of mentions of who and what they are talking about you on the dark web. Discussions related to your organization about hacking, data breaches, and your security vulnerabilities are some of the points you’d like to hear about.

Employee Credentials is a list of information about the credentials of your employees collected from the leaks. It’s crucial to prioritize protecting sensitive information, preventing unauthorized access. Otherwise your organization will be swarmed with threat actors, using passwords from stealer logs as an initial access vector.

Data from Infected Machine will show you that a stealer malware infected a machine in your company. If a machine in the company is infected with malware, it’s essential to respond promptly and effectively to mitigate the impact and prevent further spread. Lack of alerts from your systems doesn’t always mean that your organization is secure. You might want to check if threat actors are exploiting your computers.

Latest Exposure is the last time your sensitive data was exposed. To determine the last time sensitive data was exposed, you might have to conduct a thorough investigation, analyzing systems, identifying if the data is accessed or compromised, and determine the timeline of the breach. Or, you can check our Free Dark Web Report.

Data for sale in Blackmarket will tell you if anyone is selling your data on the blackmarket. This data can include personally identifiable information (PII), financial records, login credentials, intellectual property, and more. They are not supposed to be on the dark web, but it is essential to search within that domain to make sure whether anyone is exploiting your vulnerabilities and extracting sensitive information.
Don’t be intimidated by what you see in our Free Dark Web report! You can use SOCRadar for free for 1 year and get relevant intelligence that will keep you one step ahead of threat actors.



































