Google Switches Email Authentication Method Following Exploitation by Scammers
Google has patched a vulnerability that allowed a threat actor to pose as UPS on Gmail. The email was falsely labeled as authentic by the tech giant.
According to Google, what caused the issue was a third-party security vulnerability in an authentication program’s Sender Policy Framework (SPF). The standard, Brand Indicators for Message Identification (BIMI), is intended to protect email users from brand spoofing and phishing attacks. Threat actors utilized BIMI in the attack to appear more trustworthy.
How Does the SPF Vulnerability in BIMI Work?
BIMI safeguards brands’ reputations by granting them control over their representation in messaging services through logo display and authenticated emails. Google adopted BIMI support in July 2021 and recently introduced blue checkmarks for verified senders.
BIMI uses email authentication standards like SPF, Domain-based Message Authentication, Reporting, and Conformance (DMARC), and DomainKeys Identified Mail (DKIM), utilized by email providers, including Google. BIMI necessitates brands to implement DMARC along with SPF or DKIM; previously, Google enforced this necessity.
Google transitioned to DKIM after security architect Chris Plummer discovered the vulnerability in Gmail’s SPF in late May. Due to the vulnerability, SPF authenticated a non-authenticated email by mistake, allowing a fraudulent email from a supposedly verified UPS sender.
SPF is an email authentication method that determines whether the server sending an email is authorized to send messages on behalf of the sender’s domain. The DKIM method, on the other hand, prevents email spoofing by adding a digital signature to outgoing emails, allowing recipients to verify if the domain owner authorizes the email.
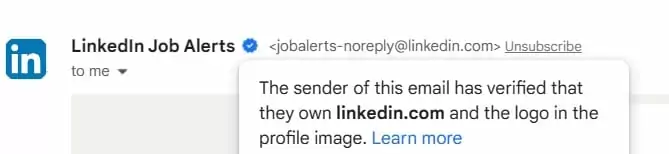
The attacker appeared more trustworthy by exploiting the vulnerability because they could display the UPS logo and blue checkmark, making it look like Google verified them.
To attain the BIMI blue checkmark, Gmail users now need to adopt the more reliable DKIM authentication standard, according to Google.
Bug in Gmail Delivery Allows Malicious Sender to Impersonate UPS
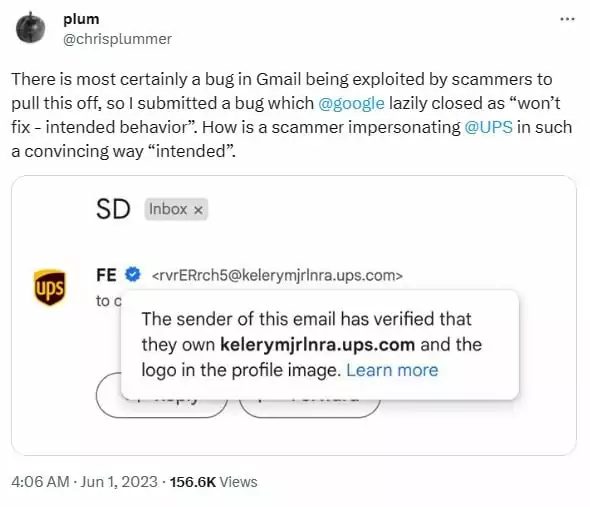
There was a problem with Gmail’s delivery. Plummer reported the bug to Google. He explained that a malicious sender tricked Gmail into thinking the email was from UPS, but it actually went through other sources before reaching Gmail.
The message came from a Facebook account and went through third-party infrastructure (fa83.windbound.org.uk) before reaching Gmail via O365. It’s highly unlikely that UPS actually sent this message.
The spoof email didn’t contain a harmful payload, but if it had, it would have looked authentic to users. Initially, Google ignored the bug report, claiming it was intended behavior. But after media attention, they seemed to change their stance.
The extent of malicious use and victimization is unknown. BIMI acknowledged the issue and attributed it to a known problem with SPF.
They stated that the program is functioning correctly but highlighted the need to fix long-standing issues with authentication protocols.
Email Security: Protect Against Phishing and Malicious Threats with SOCRadar
Protecting against phishing threats is crucial in today’s digital landscape. Phishing attacks and malware threats pose significant risks to users and organizations alike. SOCRadar Labs’ Email Threat Analyzer can help to identify and block phishing emails before they reach users.