
Comprehensive Guide to IoC Enrichment and SOCRadar’s New IoC Enrichment Module
The ability to quickly and accurately identify potential threats is crucial. Indicator of Compromise (IoC) enrichment is a vital process that transforms raw indicators into actionable intelligence. Let’s dive deep into what IoC enrichment is, why it matters, and how to utilize SOCRadar’s new module.
What is IoC Enrichment?
IoC enrichment is the process of augmenting basic indicators (like IP addresses, domains, file hashes, or URLs) with additional context and metadata. This supplementary information helps security teams better understand the nature, severity, and potential impact of threats.
Why is IoC Enrichment Important?
Raw IoCs alone provide limited value. For instance, an IP address by itself tells you very little about potential threats. However, when enriched with additional data points such as:
– Geographic location
– Associated ASN information
– Historical malicious activities
– Connection to known threat actors
– Presence on reputation blacklists
– Recent DNS resolution history
This context becomes invaluable for threat assessment and incident response.
Common Types of IoC Enrichment
Domain enrichment provides valuable additional context about a domain, enabling a better assessment of its legitimacy or identifying suspicious activity. Key information includes WHOIS data, which details the domain’s registration, such as the registrar, owner, and creation date. DNS resolution history offers insights into past mappings of the domain to IP addresses, while SSL certificate data reveals information about certificates used by the domain, which can help detect impersonation attempts. Associated subdomains, connected IP addresses, and domain reputation scores further enhance understanding by providing a comprehensive view of subdomains tied to the domain, IPs historically linked to it, and ratings indicating its potential maliciousness based on threat intelligence.
IP address enrichment adds a layer of geographical, organizational, and behavioral data to analyze IP addresses more effectively. Geolocation data reveals the physical location of the IP, and ASN (Autonomous System Number) details provide information about the ISP or organization that owns the IP. Insights into known services running on the IP, such as web or mail servers, add further context. Historical records of malicious activity, such as involvement in DDoS attacks or spamming, are particularly useful for threat analysis. Additionally, associated domains linked to the IP and correlation with firewall logs offer indicators of potential threats.
File hash enrichment provides detailed insights into specific files identified by their cryptographic hash (e.g., MD5 or SHA256). This includes information about the file type and characteristics, such as whether it is an executable or document, along with its attributes. The dataset also includes the first seen and last seen dates, indicating when the file was first and most recently observed. Prevalence data shows how often the file has been encountered, while antivirus detection results highlight whether the file is flagged as malicious. Code signing information, including the file’s digital signature, and behavioral analysis results from sandbox or dynamic analysis reveal the file’s behavior when executed, aiding in the assessment of its potential threat level.
The Power of a Dedicated IoC Enrichment Module
Our new module serves as a centralized hub for security teams, offering detailed threat intelligence focused on IoCs. Beyond simple indicator lookup, it provides deep insights into connections with threat actors, malware, and critical infrastructure components—all organized in an intuitive, dedicated interface.
The ability to quickly understand and contextualize Indicators of Compromise (IoCs) is crucial for effective threat detection and response. The IoC Enrichment module stands out with several powerful capabilities that transform raw indicators into actionable intelligence.
At its core, the module delivers comprehensive IoC analysis, enabling security teams to deep dive into the intricate connections between threat actors, malware strains, and associated infrastructure. This holistic approach ensures that analysts can quickly understand the full scope of potential threats and their implications.
The module’s thoughtfully designed multi-tab structure serves as an intuitive command center for investigators. Each tab provides a focused lens through which to examine different aspects of an IoC – from associated threat actors and malware families to detailed IP and subdomain information. This structured approach streamlines the investigation process, allowing analysts to quickly pivot between different contexts while maintaining a clear investigative thread.
One of the module’s most valuable attributes is its fusion of real-time and historical data. This temporal intelligence gives security teams crucial context about how threats evolve over time, enabling them to better predict and prepare for future attack patterns. The live update capability ensures that analysts always work with the most current threat intelligence available.
Perhaps most impressively, the module transforms complex data relationships into intuitive visualizations. Interactive graphs make it possible to immediately grasp the connections between different IoCs and their associated entities, dramatically accelerating the decision-making process. These visual representations help security teams quickly identify patterns and relationships that might be missed in traditional data formats.
Core Functionalities
In today’s rapidly evolving threat landscape, Cyber Threat Intelligence (CTI) platforms must offer robust Indicator of Compromise (IoC) enrichment capabilities. The core functionalities of an effective IoC enrichment module can be broken down into three primary components, each serving a crucial role in threat analysis and response.
Comprehensive IoC Dashboard
At the heart of the enrichment module lies a sophisticated IoC dashboard that serves as the first line of insight for analysts. This dashboard provides critical metrics at a glance, including severity assessments that help prioritize threats, comprehensive source feed tracking to maintain intelligence provenance, and temporal data through the first and last reported dates. The dashboard categorizes IoCs by type – whether they’re IPs, hashes, domains, or URLs – enabling analysts to quickly filter and focus on relevant indicators.
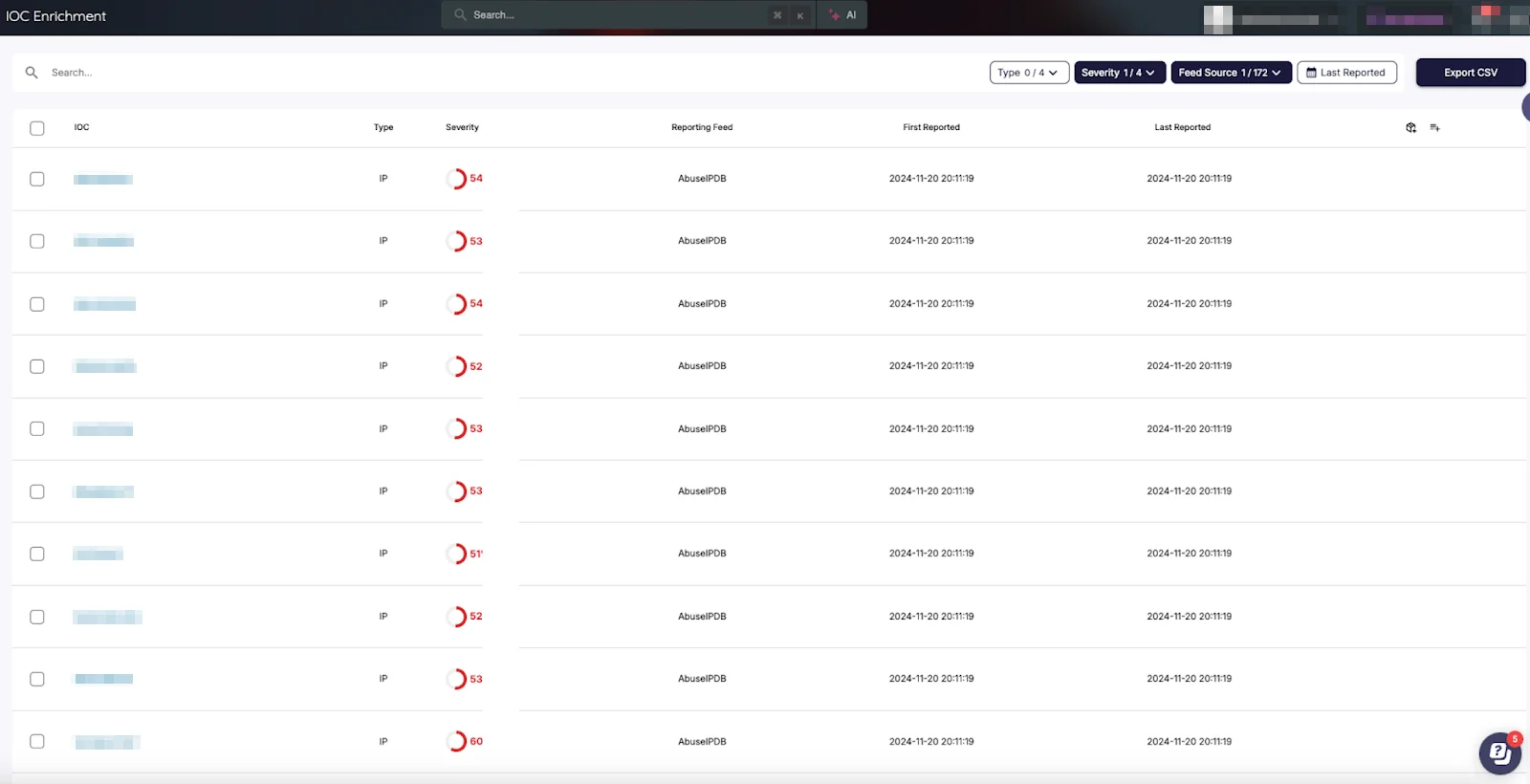
IoC Dashboard
Multi-layered Enrichment Interface
The enrichment interface employs a tab-based structure that progressively reveals deeper layers of intelligence:
The Overview tab acts as a command center, presenting consolidated insights and severity levels that enable quick decision-making. It provides a birds-eye view of the threat landscape while highlighting critical associations that warrant immediate attention.
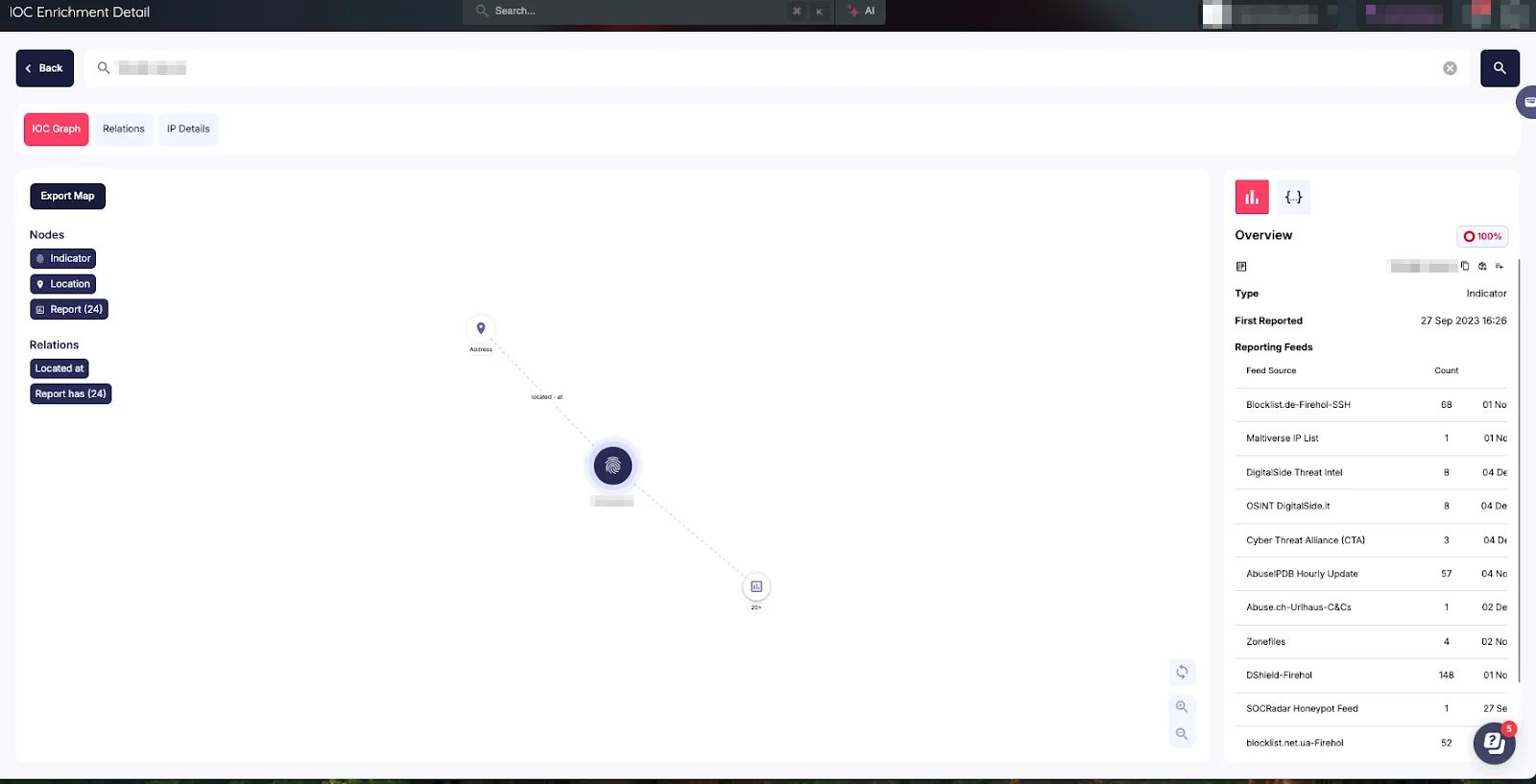
Overview Tab
Moving deeper, the Relations tab unfolds a complex web of connections between various IoCs, threat actors, and malware families. This relational mapping is crucial for understanding the broader context of threats and identifying potential attack campaigns.
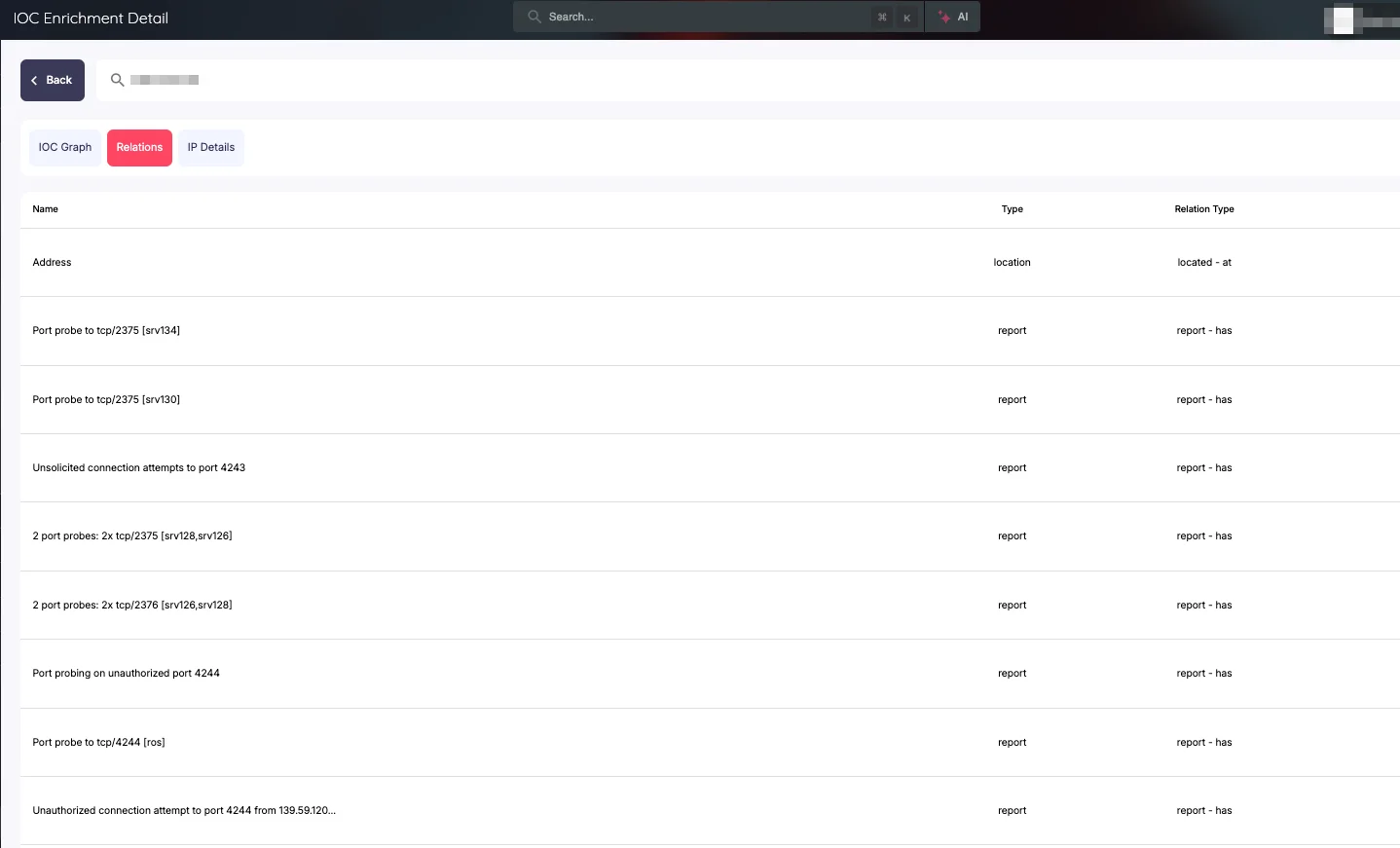
Relations Tab
The IoC Details tab serves as the analytical backbone, offering granular information specific to each indicator type. For instance, IP-related data includes ASN details, CIDR ranges, and geolocation information, while domain analysis encompasses WHOIS records and associated IPs. This depth of detail is essential for thorough threat investigation and validation.
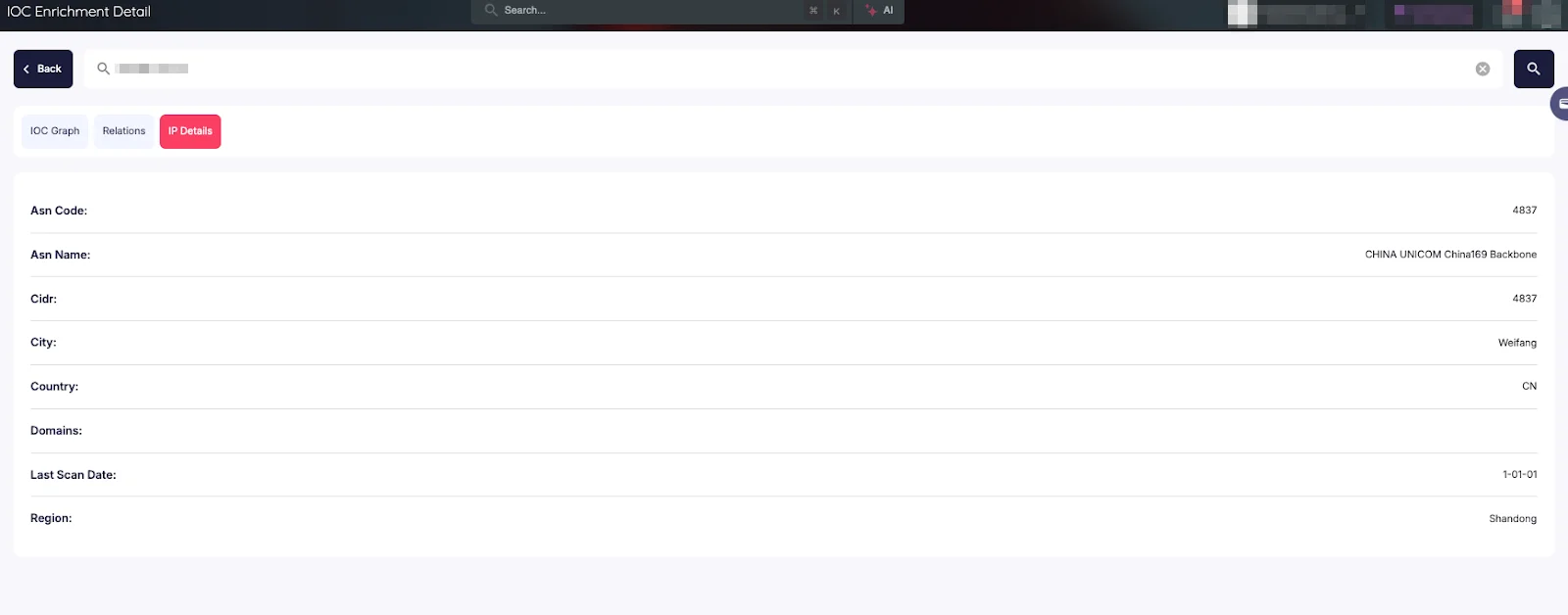
IP/Domains Details Tab
Visual Analytics Through Interactive Graphs
The module’s visual analytics component transforms complex data relationships into intuitive, interactive graphs. These visualizations map out the interconnections between various IoCs, associated malware, and threat actors, providing security teams with immediate visual insights into attack vectors and infrastructure patterns. This graphical representation significantly reduces the time needed to understand threat contexts and make informed decisions about potential security risks.
The interactive nature of these graphs allows analysts to navigate through different layers of relationships, helping them uncover hidden patterns and connections that might not be immediately apparent in traditional data presentations.
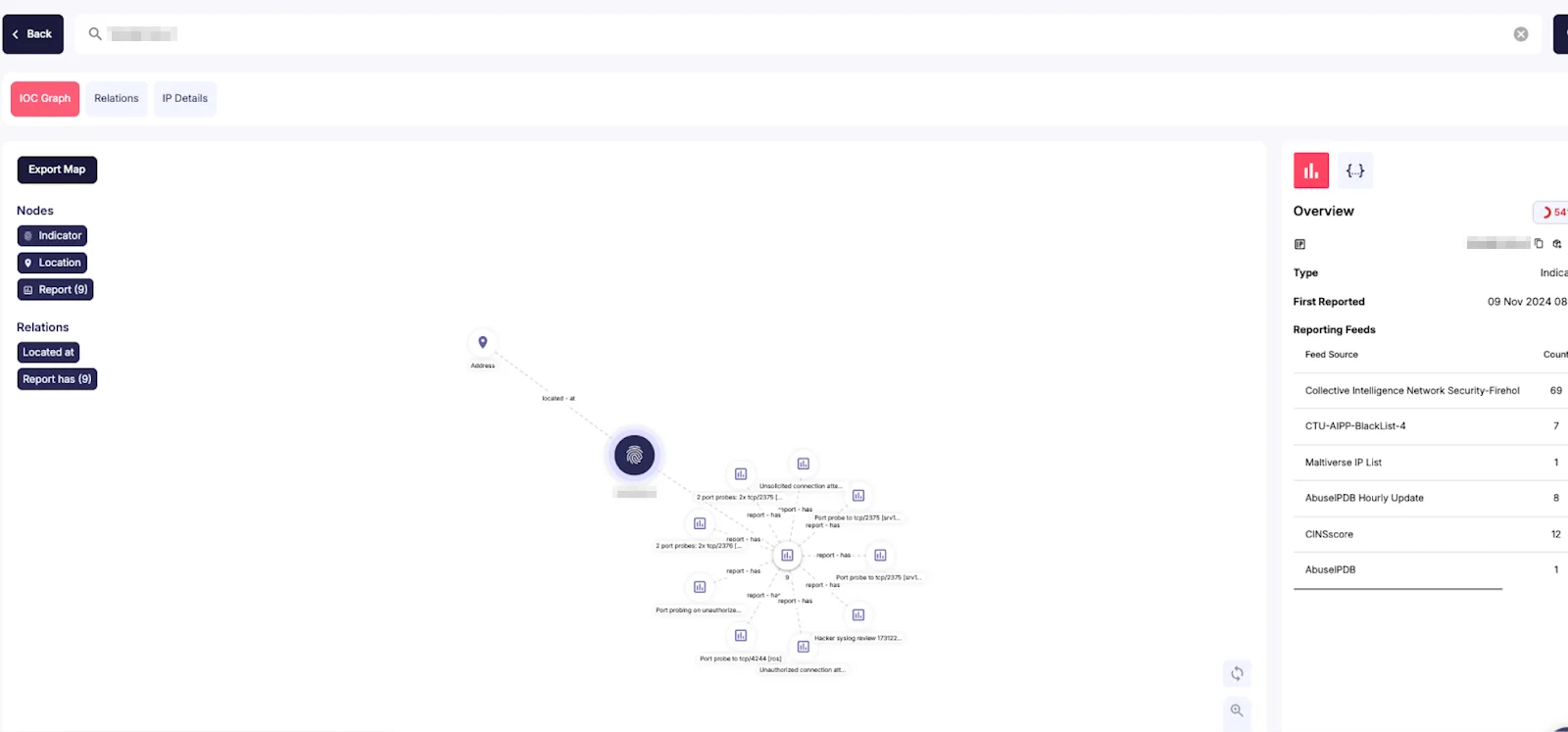
Visual Relationship Mapping
Key Benefits of IoC Enrichment Module
The IoC Enrichment module brings several key benefits to security teams in their daily operations.
Enhanced Threat Visibility
The IoC Enrichment module empowers cybersecurity professionals with unparalleled visibility into the threat landscape. The module enables teams to act swiftly and decisively by offering comprehensive intelligence focused on threat actors, malware, and their associated infrastructures. With high-quality, contextual data at their fingertips, analysts and incident responders can uncover hidden patterns and connections, facilitating a deeper understanding of threats. This enhanced visibility ensures that no critical detail goes unnoticed.
Faster Investigations
Efficiency is the cornerstone of effective threat mitigation, and the IoC Enrichment module delivers on this front. Its multi-tabbed design and detailed data organization streamline the investigative process. This way, teams can quickly locate relevant information about threat actors, malware, and infrastructures. Teams can conduct investigations with precision and speed with easy access to enriched data points such as subdomains, IP addresses, DNS records, and assets. This acceleration in the workflow translates into timely threat responses, reducing the potential impact of incidents.
Proactive Defense
The IoC Enrichment module not only enhances visibility and speeds up investigations but also equips organizations with the tools needed for a proactive defense. By leveraging real-time tracking alongside enriched historical data, users can anticipate emerging threats and take preemptive measures. This capability shifts the focus from reactive threat management to anticipatory defense, enabling security teams to stay one step ahead of adversaries.
Designed for High-Impact Sectors
The IoC Enrichment module is particularly beneficial for high-risk industries such as finance, healthcare, government, and energy. These sectors face constant threats from sophisticated adversaries, making the need for advanced threat intelligence tools paramount. The module equips security teams in these industries with the resources needed to protect their critical assets effectively by providing in-depth data, real-time insights, and intuitive visualizations.
Conclusion
Our IoC Enrichment module represents a significant advancement in threat intelligence analysis. By combining comprehensive data enrichment, intuitive visualization, and powerful analysis capabilities, we’re providing security teams with the tools they need to stay ahead of emerging threats.
The module’s focus on usability, combined with its depth of analysis, makes it an invaluable asset for any organization serious about its cybersecurity posture. Whether you’re conducting incident response, threat hunting, or proactive threat intelligence gathering, our IoC Enrichment module provides the insights and capabilities you need to make informed decisions quickly.
Ready to enhance your threat intelligence capabilities? Contact our team to learn more about implementing the IoC Enrichment module in your security infrastructure.



































