
Hacktivist Group Black Reward Leaked Iran’s Nuclear Program Secrets
Iran’s Atomic Energy Organization announced on Sunday, October 23, that foreign country-backed hackers had hacked an email system belonging to the organization’s subsidiaries. On the other hand, the Iranian hacktivist group Black Reward claimed responsibility for the attack even before the announcement. They threatened to release documents on Tehran’s nuclear program unless all “political prisoners, prisoners of conscience, and people arrested in the recent protests” were released within 24 hours.
The Iranian government remained silent about the threat, but when the time expired, the hacktivist group began to publish the leaked data in pieces on the Anonymous File Upload site.
Who is Black Reward?
Before we delve into the latest hack & leak operation by Black Reward, we should identify the group and its previous activities.
We witnessed the birth of the Black Reward group as they initiated their hacktivism acts against the Iranian government to support the protests that spread throughout the state after the death of Mahsa Amini. According to their statements, they are against the theocratic government and describe the government as criminal. They also declare they will continue their actions until the Iranian government is overthrown.
The group claims to be part of the Iranian hacker community. This claim also indicates that they deny being foreign state-sponsored hackers, as the Iranian Atomic Energy Organization alleges.
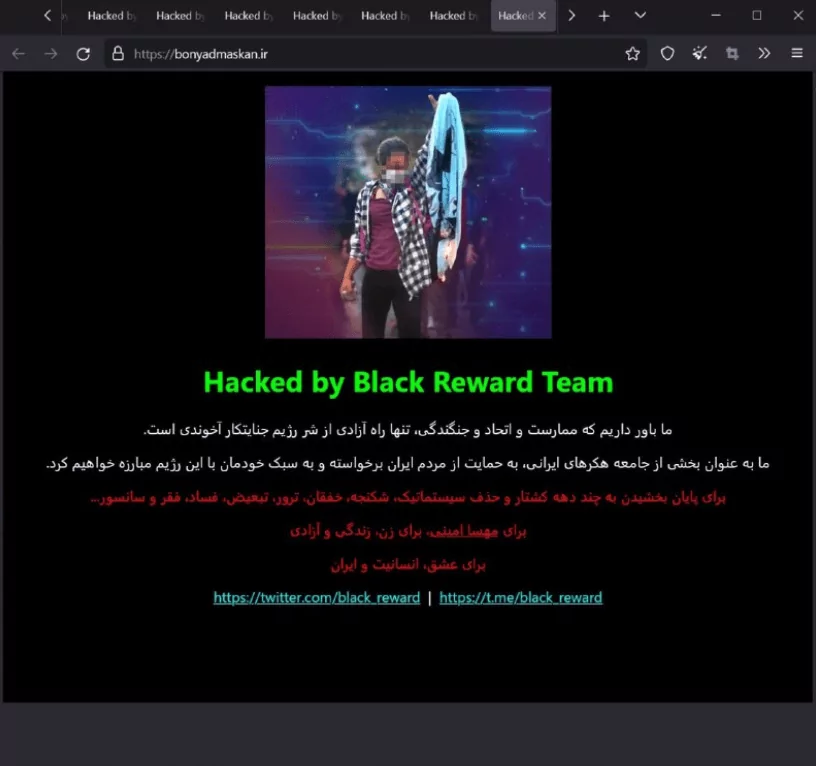
The first target of the group was the Islamic Revolution Housing Foundation. According to the group’s claim, the foundation’s servers and affiliated websites were hacked, and all their data was deleted.
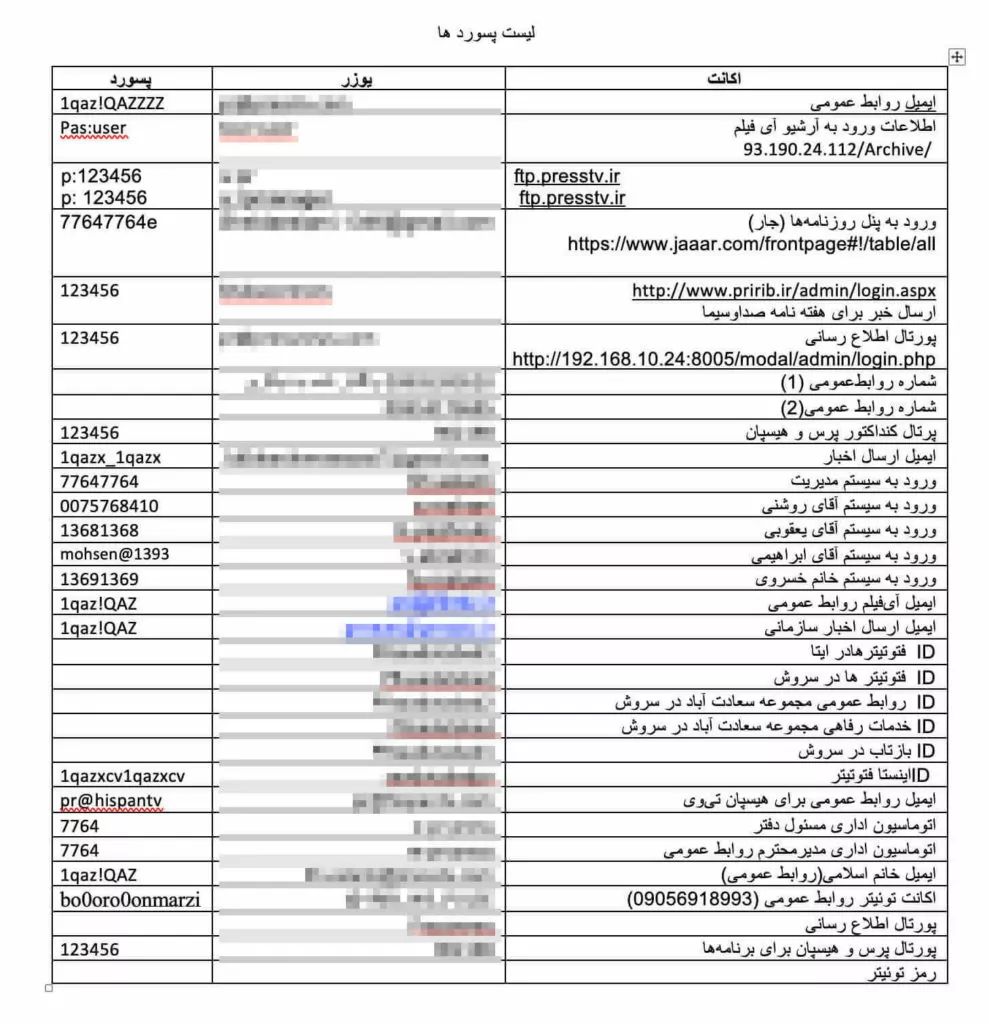
The group performed the other cyber-attack against the official website of Press TV, which is state-owned and the first Iranian international news network broadcasting in English and French.
Apart from the above attacks against government institutions, they were also engaged in another protest action. On October 7, they claimed that they sent 5 million SMS to Iranian citizens as an invitation to protests.
The Black Reward group, which opened its social media accounts on September 22 and shared its first posts on September 25, seems to have been operating under this name for more than a month. Considering their previous statement, they seem like a collective group of hackers and hacktivists who came together, especially against the Iranian government during the protests.
What was the Purpose of the Latest Attack?
The introduction of the Black Reward Group’s manifesto about the latest attack in their words as follows:
“As a part of the Iranian hacker community and born from among you, unlike Westerners, we are not flirting with criminal mullahs, and if we say something, we follow it 100%.”
Similar to their other activities, the hacktivist group carried out this attack to represent the ongoing protests in Iran in the cyber field. On Friday, October 21, 2022, they threatened the Iranian government to leak, in their words, “dirty nuclear projects.” This threatening message stated they would spread the data if the government won’t release the political prisoners and arrested protesters within 24 hours.
There was no response from the government over the weekend, and the group began leaking 50GB of data on their Telegram channel. On Sunday, October 23, authorities announced that an email server from Iran’s Atomic Energy Organization subsidiaries was hacked. Thus, the authorities made the first official statement on the subject.
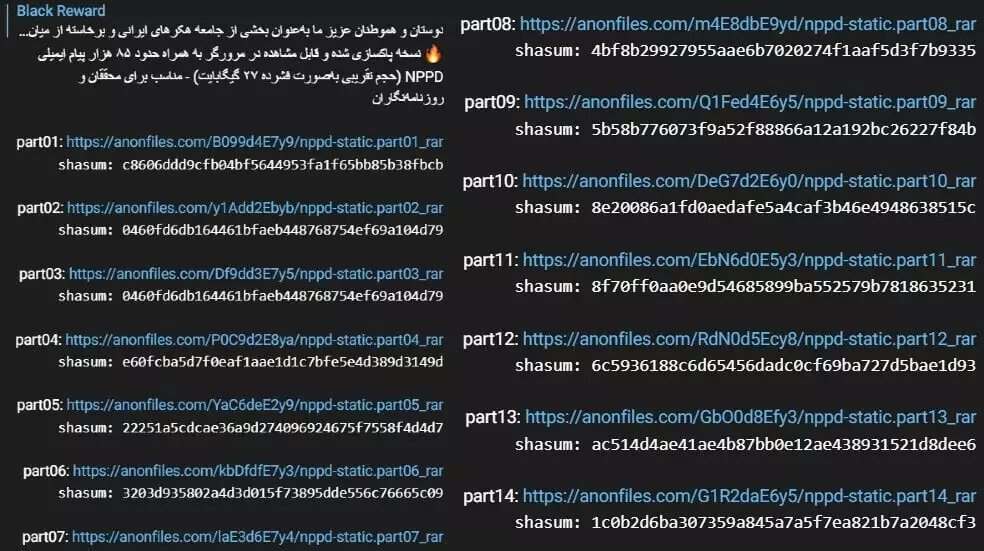
Figure 7, Black Reward leaked 50GB of data on their Telegram channel. The whole leak consists of 14 parts.
Details of Leaked Documents
According to Black Reward’s statement, the data they leaked includes the following:
- Iran’s public and private conversations with the International Atomic Energy Agency,
- Atomic development contracts and agreements with domestic and foreign partners,
- Construction plans, logistics, and strategic plans related to nuclear industries,
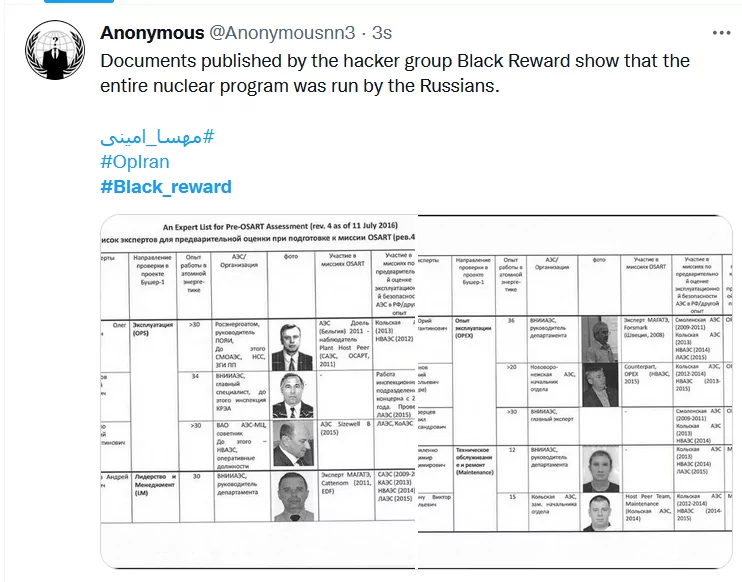
- Management and operational schedules of different parts of the Bushehr power plant,
- Identity specifications and legal forms of engineers and employees of Iran Atomic Energy Production and Development Company,
- Passports and visas of Iranian and Russian specialists working in the Bushehr power plant, along with details of trips and missions,
- Details of Bushehr Nuclear Power Plant’s cross-sectional performance status,
- Technical and specialized reports and documentation, and more.
What’s Next?
While the Black Reward group’s next step is currently unknown, the hacktivism activities against the Iranian government, which regained momentum with the people deceased during protests, are snowballing. In this context, cyber attack support of hacktivist groups like Black Reward is expected to continue.
As we mentioned in our previous article, attacks are carried out on state institutions and many government-related organizations. In addition to many hacktivist collectives, we can say that even organizations and legal entities are participating in protests in cyberspace. While famous figures such as Elon Musk post messages of support, platforms considered “libertarian,” such as The Tor Project and Signal, are also publishing guides to the Iranian people against censorship and restriction measures.
Lessons Learnt
We saw the power of social media in mass movements like the Arab Spring, and the ever-expanding cyberspace seems to be one step ahead of this phenomenon. The cost of an attack in cyberspace can be very cheap, but the impact can be very high. Every community that can be physically suppressed in such social events can and does choose cyber-attack as an action vector. It appears that the support of hackers may even be the most crucial part of the ongoing protests.
SOCRadar analysts continue to work on the leaked files and will continue to inform their customers and the public when a threatening case is detected.




































