How Can OpenAI Assistant Feature Help in Vulnerability Management?
The integration of artificial intelligence has become instrumental in fortifying defenses against evolving threats. One particularly intriguing facet is the application of OpenAI assistants in vulnerability management. These digital aides, powered by advanced natural language processing, offer a promising avenue for automating critical aspects of threat assessment.
Vulnerability management, a pivotal component of cybersecurity strategy, involves continuously identifying, prioritizing, and mitigating potential vulnerabilities in a system or network. The efficacy of vulnerability management directly impacts an organization’s resilience against cyber threats.
In a previous blog post, we delved into custom GPTs and their potential in vulnerability management. We explored how every stage of the management process – identifying, prioritizing, and mitigating vulnerabilities – could be elevated through the integration of GPTs, especially when paired with our robust Attack Surface Management solutions. If you missed that discussion, you can catch up here.
Let’s focus on OpenAI Assistant—a powerful AI tool designed to simplify assistant development and enable natural language user interactions. OpenAI Assistant allows developers to create unique assistants and threads for each user, offering a personalized and dynamic conversational experience. The Assistant could also help fulfill the requirements of your organizational vulnerability management policy, as it can be fed with domain-specific data.
In this blog post, we dive into the capabilities of OpenAI assistants, specifically focusing on their role in vulnerability management. From defining their responsibilities to setting up customized tasks, we’ll explore how these assistants can be harnessed to streamline and enhance your organization’s response to emerging threats.
The Problem: Complexity of the Vulnerability Landscape
Amidst the ever-changing cybersecurity landscape, organizations grapple with formidable challenges in identifying and addressing vulnerabilities. Managing many vulnerabilities across diverse systems adds complexity to maintaining robust cybersecurity measures.
The Solution: Automation in Vulnerability Management
In the era of expansive cyber threats, automation emerges as a pivotal player in handling the scale and complexity of vulnerability management. Automation streamlines the identification, prioritization, and remediation of vulnerabilities, empowering organizations to fortify their defenses efficiently and effectively. Automating the critical process of vulnerability management is possible with OpenAI Assistant.
SOCRadar’s Approach to Automated Vulnerability Management
In tandem with OpenAI Assistant, SOCRadar’s Attack Surface Management (ASM) module is also a valuable, automated solution, adept at handling the intricate scale and complexity of vulnerability management scenarios.
The ASM module continuously monitors an organization’s digital footprint, scanning and cataloging external-facing assets like domains, IP addresses, and web applications. This proactive approach provides real-time insights into emerging vulnerabilities.
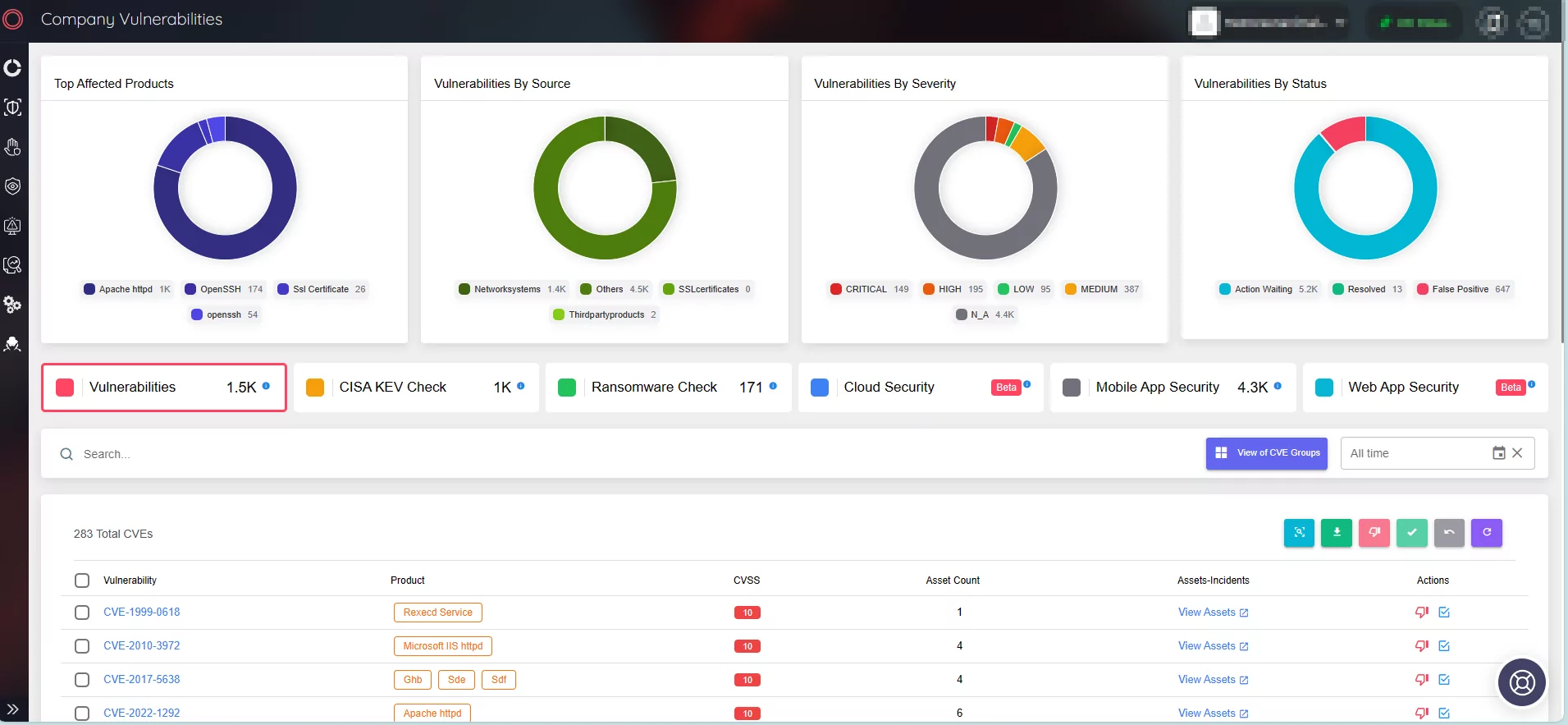
View vulnerabilities affecting your organizational assets on SOCRadar ASM Module
What is OpenAI Assistant? How Is It Different from GPTs?
OpenAI Assistant is an AI tool developed by OpenAI, specifically designed for the creation of conversational agents or chatbots. It streamlines AI assistant development and facilitates natural language interactions with users. The accompanying OpenAI Assistants API provides developers with access to the latest models and safety best practices, allowing integration into applications.
According to its official documentation, the OpenAI Assistant can:
- Customize OpenAI’s models with specific instructions.
- Utilize persistent Threads that store message history and automatically truncate as the conversation progresses, simplifying AI application development.
- Manage Files in various formats during their creation or within Threads. When using tools, Assistants can create files (such as images, and spreadsheets) and cite them in the Messages they generate.
- Access multiple tools simultaneously, including OpenAI-hosted tools (such as Code interpreter and Retrieval) or tools built/hosted independently (via Functions).
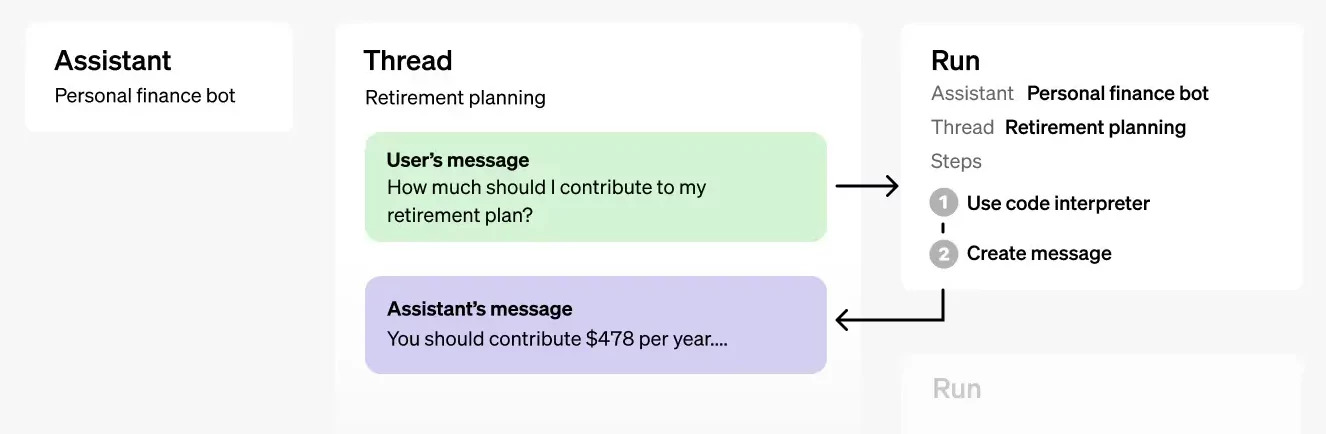
The basic workflow of an OpenAI Assistant – a personal finance bot (Source: OpenAI)
In its approach to AI, OpenAI Assistant introduces a set of tools, namely “Functions,” “Code Interpreter,” and “Retrieval,” augmenting the assistant’s capabilities significantly.
- Function Calling for Customization:
Developers can use function calling to define custom functions for their applications or external APIs. This enables the assistant to intelligently execute these functions, generating a JSON object with relevant arguments.
- Dynamic Code Execution:
The Code Interpreter enables the assistant to write and execute code. It processes files with diverse data and formatting, generating outputs such as graphs.
- Knowledge Retrieval from Uploaded Files:
Retrieval equips the assistant with knowledge from user files. The assistant autonomously decides when to retrieve content based on user requests. You can upload domain-specific files to train the Assistant for certain scenarios.
- Seamless File Integration:
Uploading files enhances the assistant’s capabilities. It enables the assistant to use content for both retrieval and code interpretation, given these tools are enabled through the Assistant’s settings.
Training and incorporating such a tool into cybersecurity workflows simplifies tasks and contributes to building a proactive and resilient defense against cyber threats.
How Can OpenAI Assistant Enhance Vulnerability Management?
The OpenAI Assistant introduces several key advantages that can streamline the processes in vulnerability management and empower security professionals. Let’s explore the benefits of integrating OpenAI Assistant into the workflows.
A standout feature of OpenAI Assistant lies in its capacity to generate and summarize comprehensive reports. The Assistant efficiently extracts relevant information from extensive datasets in a field inundated with data. This accelerates the analysis process and enables security teams to derive actionable insights swiftly.
The capability to distill complex information into concise summaries is a valuable asset in staying ahead of evolving threats and could greatly assist in prioritizing vulnerabilities. This is why, harnessing the power of AI, SOCRadar delivers clear and concise reports for every identified vulnerability through its Vulnerability Intelligence feature.
The Vulnerability Intelligence feature provides detailed information on each vulnerability, encompassing its lifecycle, including updates and exploitation. It also details mentions, available PoC exploits, and related repositories. By utilizing the AI Insights feature on a vulnerability page on the SOCRadar platform, users can access a brief report on its key insights and mitigation strategies.
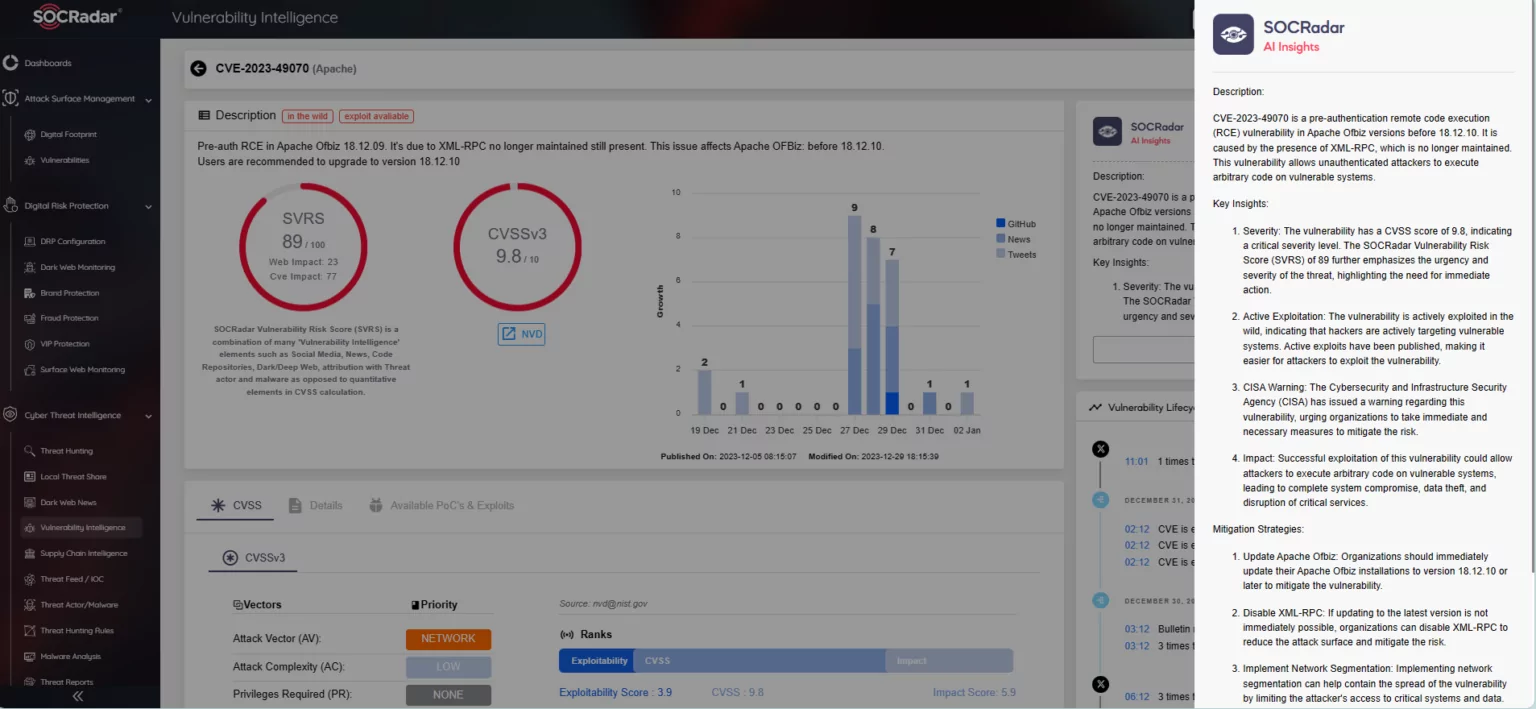
SOCRadar Vulnerability Intelligence, AI Insights
Similarly, by leveraging contextual information and considering risk factors, the OpenAI Assistant can also contribute to a more informed decision-making process. This ensures that security teams can direct their efforts toward addressing vulnerabilities with the highest risks, thereby enhancing the overall resilience of the organization’s cybersecurity posture.
To illustrate the practical application of OpenAI Assistant, let’s envision security professionals employing the Assistant to automate the analysis and reporting of new Common Vulnerabilities and Exposures (CVEs).
Like Custom GPTs, you have the capability to feed the Assistant on a specific domain or other datasets and invoke it through the API. With a simple script, you can collect CVE data, for example, from an RSS feed.
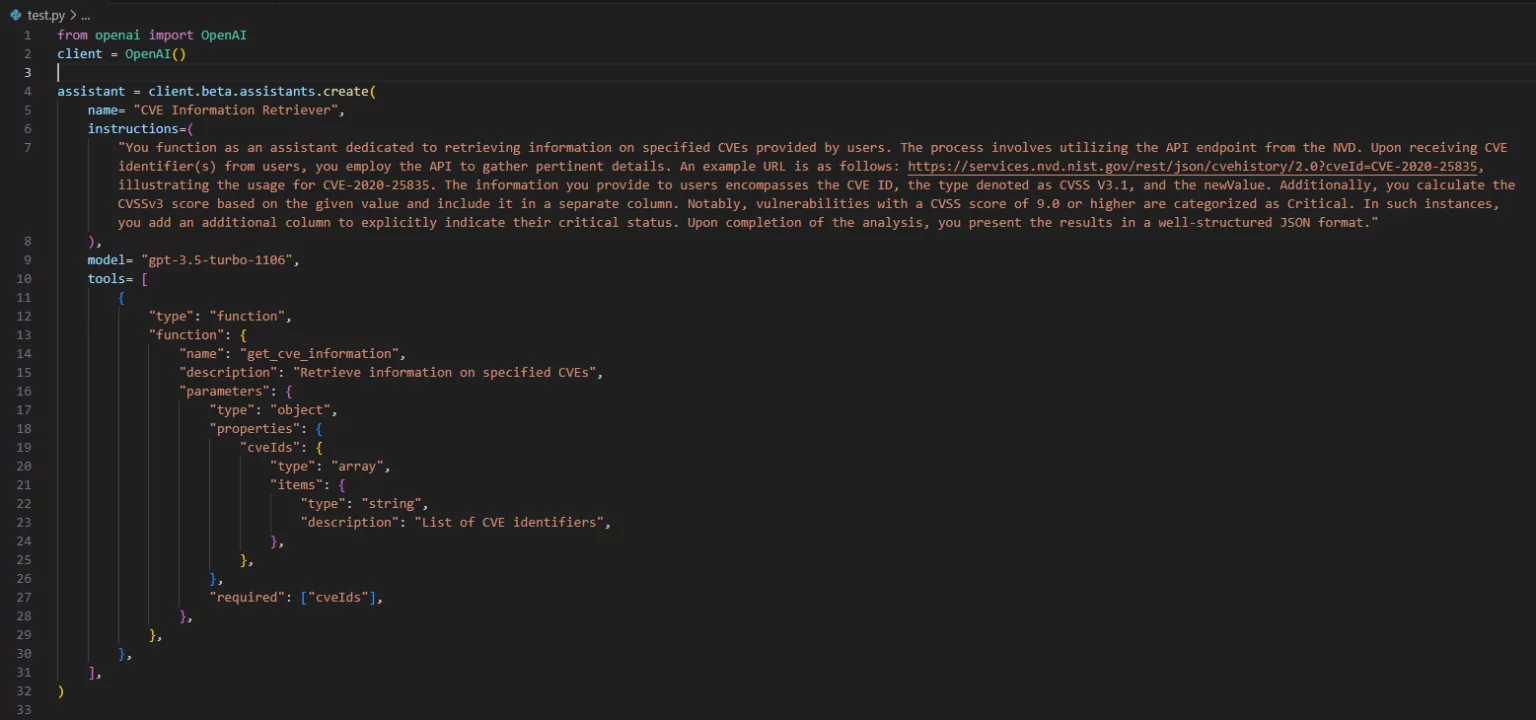
Generating an assistant to retrieve specific vulnerability details.
This Assistant would excel in generating concise reports, summarizing critical details of identified vulnerabilities – after submitting the data to OpenAI Assistant, you can instruct it to generate analysis results in a JSON file and examine the values.
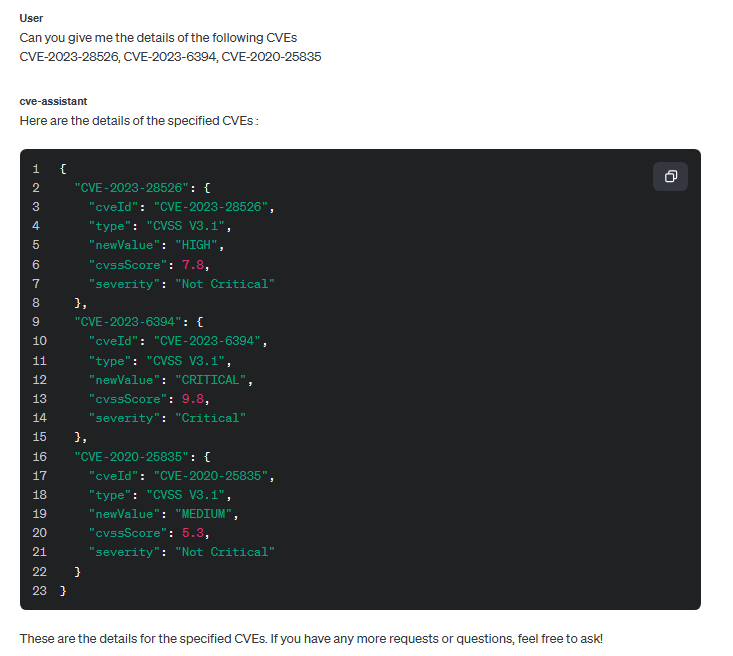
The assistant provided CVE details. You can retrieve more details as needed.
It is highly valuable that users can input domain-specific data into the system. Consider a scenario where a company has a predefined workflow in its vulnerability management policy.
For instance, if a vulnerability’s CVSS score surpasses 8.0, the policy mandates either opening a Jira ticket or emailing a designated recipient. By uploading this policy document to the OpenAI Assistant and presenting it as a prompt when a new vulnerability arises, the Assistant can seamlessly instruct the organization to adhere to the established policies.
Additionally, organizations often set specific timelines for resolving vulnerabilities in vulnerability management guidelines. The Assistant can determine the required timeframe for taking action and enter it accordingly in the tickets opened in Jira.

The Assistant can instruct users on what to do according to their policy – using other API or tools; you can automate the ticket opening process as well.
This example showcases how OpenAI Assistant can be used to automate vulnerability management processes, enhancing efficiency and effectiveness.
However, attempting to automate processes through the ChatGPT web UI can be quite challenging; effective automation is achievable exclusively through the OpenAI API. As emphasized by Sam Altman during OpenAI DevDay on October 6, the data transmitted via the API is not used in training. This assurance holds significant importance for organizations concerned about data privacy and security.
Expanding on the Assistant’s capabilities and considering the role of vulnerability management in Software Development Life Cycle (SDLC) pipelines, it can play a role in ensuring the integrity of builds. For instance, if a vulnerability with a severity score exceeding 8 is detected, it can trigger a build failure. Leveraging the Assistant’s Functions feature, organizations can intelligently integrate this capability into their SDLC pipelines, ensuring a proactive response to security concerns.
In essence, OpenAI Assistant acts as a catalyst, transforming the vulnerability management landscape with an easy way to automate specific processes, its report generation prowess, and valuable assistance in prioritizing security efforts.
Integration with Existing Security Infrastructure
During the integration of OpenAI Assistant with existing security tools and platforms to enhance vulnerability management, it is crucial to be aware of the following:
- Organization Scope: Remember that assistants, threads, messages, and files created via the API are organization-scoped. Individuals with API key access can read or write these components.
- Authorization Measures: Ensure secure data access by implementing authorization measures. Verify the end-user’s authorization before performing reads or writes on assistants, threads, messages, and files. Store accessible object IDs in your database and check them before fetching the object ID with the API.
- Restrict API Key Access: API keys grant extensive operational capabilities, including reading and modifying sensitive information like messages and files. It is strongly recommended to regularly audit the list of individuals within your organization with API keys.
- Create Separate Accounts: Consider creating separate accounts or organizations for different applications. This practice helps isolate data across multiple applications, creating a more organized and secure integration.
Conclusion
As organizations grapple with the complexity of identifying and addressing vulnerabilities, integrating OpenAI Assistant into vulnerability management practices offers a potent solution.
This AI tool, equipped with a natural language interface and proficient report generation, can offer a dynamic solution for security professionals. By facilitating seamless communication with vulnerability databases and intelligently extracting relevant information, OpenAI Assistant can enhance the workflow of security teams.
The capabilities of OpenAI Assistant are further extended with the introduction of tools like Functions, Code Interpreter, and Retrieval. Developers can define custom functions through function calls, allowing intelligent execution by the assistant when configured for specific tasks. The Code Interpreter facilitates coding and its execution, processing diverse data for valuable outputs. Retrieval equips the assistant with knowledge from uploaded files, contributing to enhanced contextual understanding when tailored for specific requirements.
However, it is crucial to carefully consider integrating this innovative AI tool into security infrastructure. This ensures alignment with specific needs and tasks when configuring the assistant accordingly.
OpenAI Assistant can be a valuable tool in a proactive defense against cyber threats. Its user-friendly interface and capabilities offer a flexible solution for the intricate challenges of vulnerability management, contingent upon its appropriate configuration for such tasks.
In parallel, SOCRadar can provide organizations with even more comprehensive security. You can access reports for each identified vulnerability by leveraging the AI Insights feature in SOCRadar’s Vulnerability Intelligence. These reports provide key insights and mitigation strategies for each vulnerability. With SOCRadar’s advanced CTI solutions like Vulnerability Intelligence, Attack Surface Management, and the AI Insights feature, you can easily identify and mitigate vulnerabilities, improving the overall effectiveness of your organization’s vulnerability management practices.



































