
HSBC, Barclays, and UK Gov Databases Compromised
The SOCRadar Dark Web Team has uncovered a series of alarming data breaches and unauthorized access sales affecting major financial institutions, government entities, and a cybersecurity firm. The
The most recent discoveries include leaked databases of HSBC and Barclays, unauthorized network access sale of Zscaler, a significant breach involving the Indian Defence Force, and a leak within the UK Government.
Receive a Free Dark Web Report for Your Organization:
Databases of HSBC and Barclays are Leaked

The SOCRadar Dark Web Team has detected a claim on a hacker forum that databases for both HSBC and Barclays have been leaked. According to the threat actor, the data was uploaded for public access, stating, “Today, I’m uploading the HSBC & Barclays data breach for you to download. Thanks for reading and enjoy!”
The incident reportedly occurred in April 2024, when a direct contractor for the two banks was compromised. The threat actor, who had previously made similar allegations in early April, claims that the breach involved a variety of sensitive data, including database files, certificate files, source code, SQL files, JSON configuration files, and compiled JAR files. A specific file named “notary_request_2024.csv” containing over 512,000 lines was also mentioned.
Alleged Unauthorized Network Access Sale is Detected for a Cyber Security Company
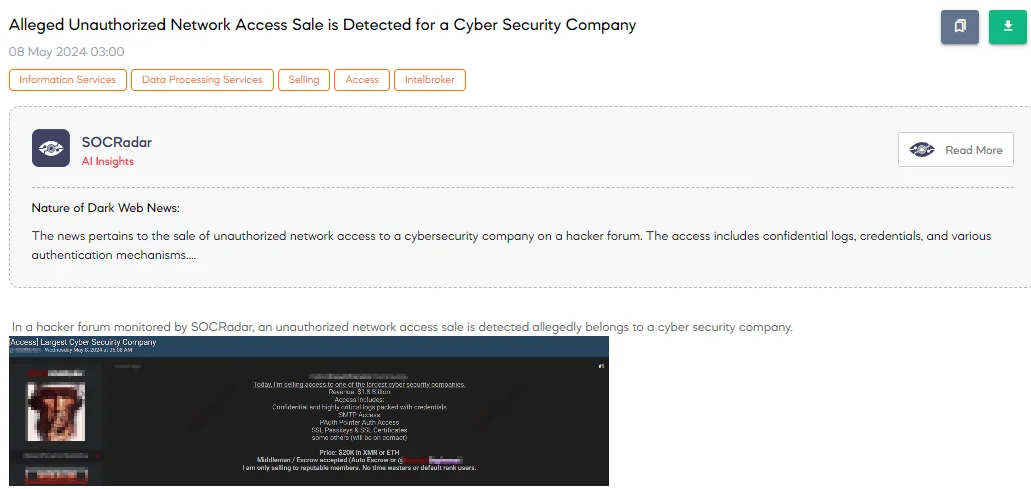
The SOCRadar Dark Web Team has detected a post on a hacker forum claiming unauthorized network access for sale, purportedly belonging to Zscaler, a major cybersecurity company. The threat actor advertised the sale of this access, touting it as entry to “one of the largest cyber security companies” with revenues reported at $1.8 billion. The offered access includes confidential logs filled with credentials, SMTP and Pointer Auth (PAuth) access, as well as SSL passkeys and certificates. The price was set at $20K, payable in Monero (XMR) or Ethereum (ETH), with transactions through a middleman or escrow service.
Shortly after the initial post, the threat actor updated their status, claiming that the access had been sold. This incident has sparked discussions within the security community regarding the integrity of Zscaler’s network security. Zscaler responded promptly, clarifying that the breach was confined to a test environment and assured that their customer, corporate, and production environments were unaffected by this incident.
Database of Indian Defence Force is on Sale
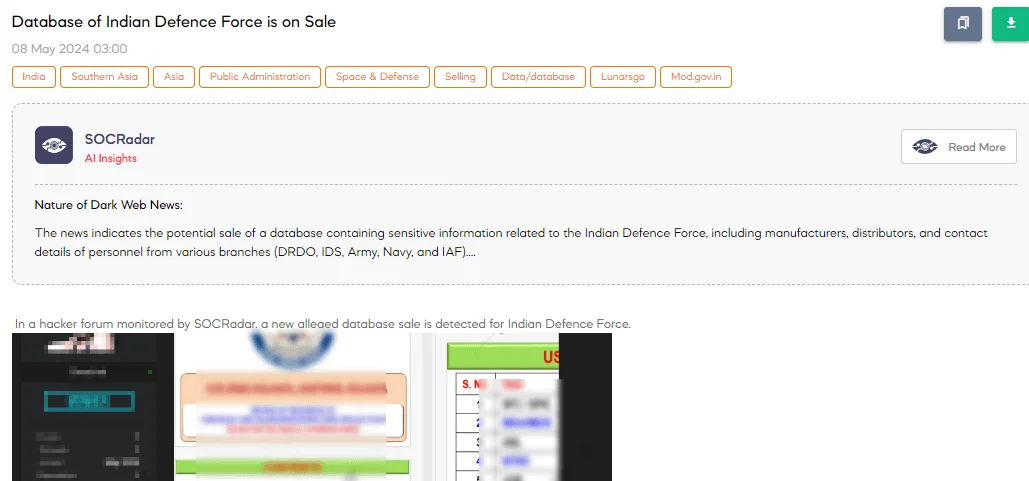
The SOCRadar Dark Web Team has reported detecting a post on a hacker forum where a threat actor is allegedly selling a database related to the Indian Defence Force. The claimed database includes sensitive information concerning manufacturers and distributors of defense-related products, as well as details on various branches such as the DRDO, Indian Defence Services, Army, Navy, and Indian Air Force.
Database of United Kingdom Government is Allegedly Leaked
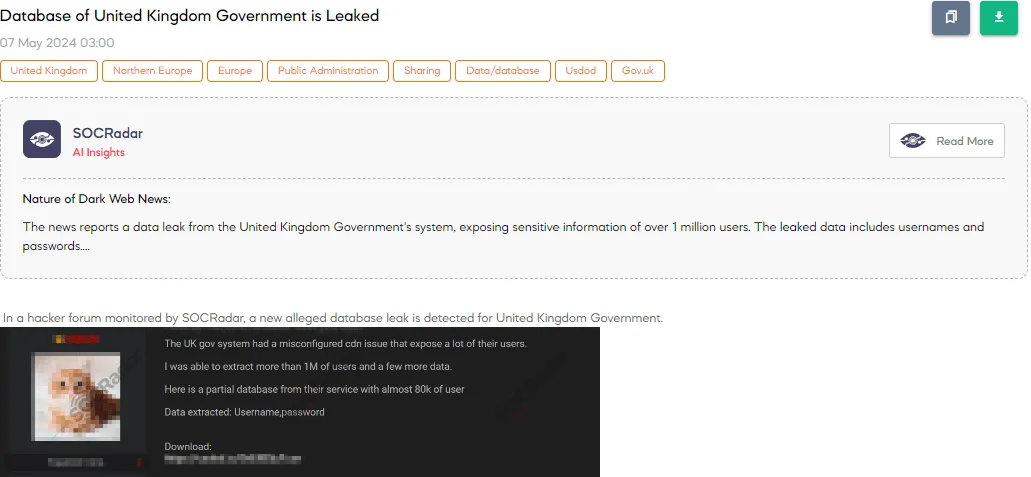
The SOCRadar Dark Web Team has detected a post on a hacker forum where a threat actor claims to have accessed a database from the UK Government due to a misconfigured CDN (Content Delivery Network). According to the threat actor, this security oversight allowed the extraction of data belonging to over 1 million users, with a partial database of nearly 80,000 users being exposed online.
The data allegedly compromised includes usernames and passwords. The threat actor also hinted at possessing more data and plans to release it “at the right moment,” describing this leak as a “friendly warning” and stating they are monitoring actions around the globe.
Powered by DarkMirror™
Gaining visibility into deep and dark web threats can be extremely useful from an actionable threat intelligence and digital risk protection perspective. However, monitoring all sources is simply not feasible, which can be time-consuming and challenging. One click-by-mistake can result in malware bot infection. To tackle these challenges, SOCRadar’s DarkMirror™ screen empowers your SOC team to follow up with the latest posts of threat actors and groups filtered by the targeted country or industry.




































