
IntelBroker’s Alleged Cisco Breach: A Deep Dive into the Claims and Responses
[Update] December 31, 2024: “Cisco Confirms Data Leak by IntelBroker and Provides Update”
[Update] December 25, 2024: “IntelBroker Releases More Data from Alleged Cisco Breach: 4.5TB Leak Update”
[Update] December 17, 2024: “IntelBroker Shares Partial Cisco Data to Prove Legitimacy”
[Update] November 7, 2024: “IntelBroker Raises Stakes, Claims Cisco Breach Tops 800GB”
On October 14, 2024, IntelBroker, the notorious threat actor and current admin of popular hacker forum, BreachForums, claimed to have breached Cisco Systems. The actor, well-known for targeting high-profile organizations, shared details of the breach, asserting access to sensitive data, including source codes and internal documents.
Cisco promptly responded, denying any compromise of their core systems and attributing the exposed data to a public-facing DevHub resource. Despite these reassurances, IntelBroker insisted they maintained access until October 18, when Cisco reportedly revoked all remaining access. The details of the Cisco breach, the company’s investigation, and IntelBroker’s claims will be examined further in this blog.
IntelBroker Claims to Have Breached Cisco
On October 14, IntelBroker, the notorious admin of BreachForums, announced a breach of Cisco Systems, Inc. on the popular hacker forum. IntelBroker asserted that the Cisco breach took place on October 6, offering the stolen data for sale.
In the forum post, IntelBroker detailed the types of data they claim to have obtained:
- GitHub and GitLab projects
- SonarQube projects
- Source code and hard-coded credentials
- Certificates and customer Secure Remote Connections (SRCs)
- Cisco confidential documents, Jira tickets, API tokens, AWS private buckets
- Docker builds, Azure Storage buckets, private & public keys
- SSL certificates, Cisco premium products
The actor also claimed to have accessed data linked to major companies, listing names like Microsoft, AT&T, Barclays, British Telecom, Bank of America, Verizon, Vodafone, BT, SAP, and T-Mobile. To support these claims, IntelBroker shared several screenshots, purportedly showing access to management interfaces, internal documents, databases, and even customer information.
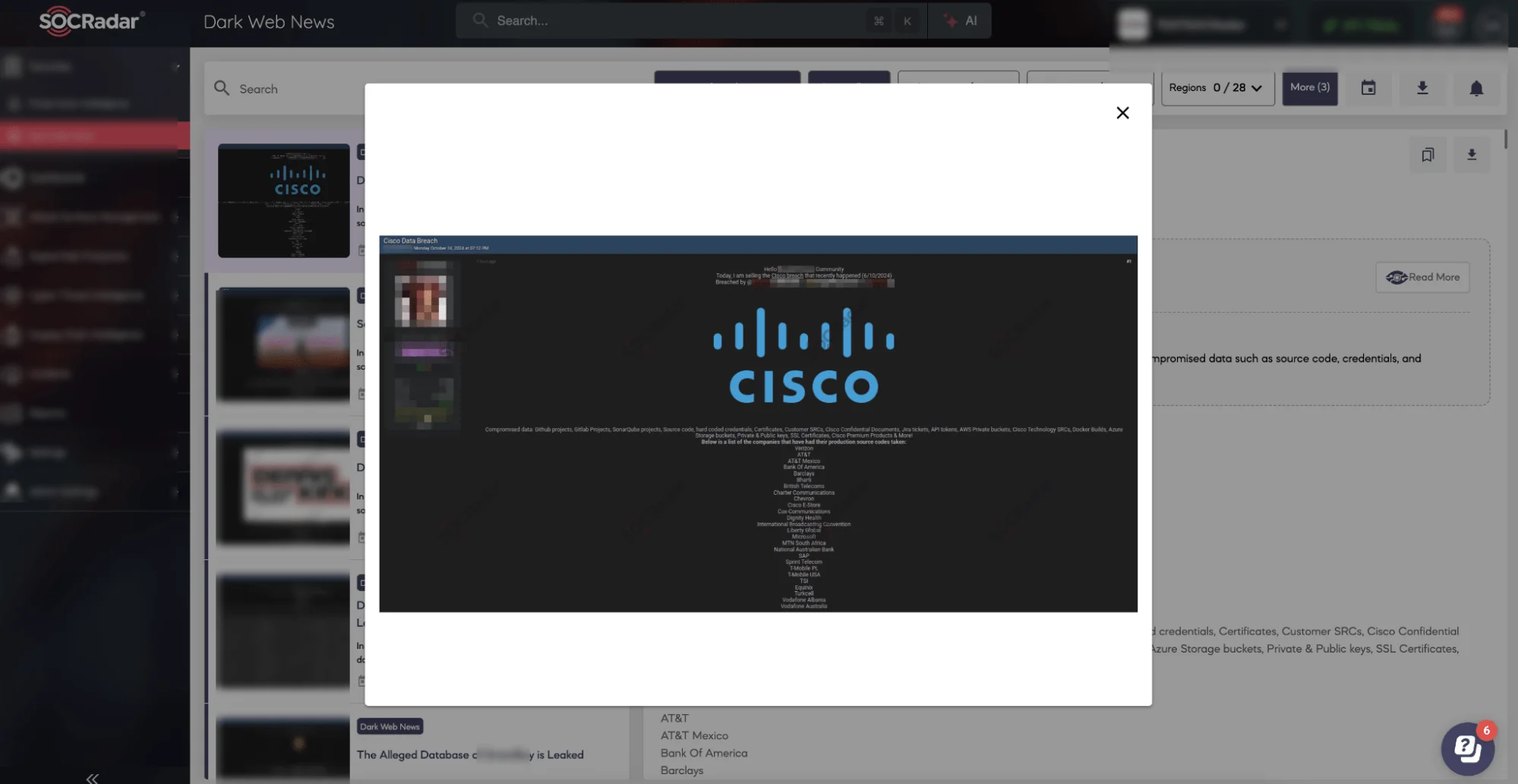
On October 14, Intelbroker claims to have breached Cisco (SOCRadar Dark Web News)
SOCRadar’s Advanced Dark Web Monitoring is an essential cybersecurity module that tracks potential risks in the Dark Web. It offers real-time alerts for PII exposures, stealer logs, and underground chatter, enabling proactive measures before incidents escalate.
The platform also includes fraud and VIP protection, safeguarding financial assets and executives’ digital identities. The integrated Dark Web Search Engine provides keyword searches for deep threat analysis.
Additionally, SOCRadar Dark Web News delivers curated intelligence on Dark Web activities, keeping users informed about emerging threats specific to their industry or region. This comprehensive approach allows organizations to detect and respond swiftly to evolving cyber risks.
Response to the Alleged Cisco Breach
Cisco quickly responded to IntelBroker’s claims, issuing an initial statement on October 15, 2024, titled “Cisco Event Response: Reports of Security Incident.” In this response, Cisco stated:
“Cisco is investigating reports that an unauthorized actor is alleging to have gained access to certain Cisco data and data of our customers. Cisco takes this allegation seriously and we have engaged law enforcement as part of this investigation. To date, our investigation has found no evidence of our systems being impacted. We will notify customers if we confirm that the actor has obtained their confidential information.”
In a follow-up statement released on October 18, 2024, Cisco reiterated that there was no breach of their core systems:
“We have determined that the data in question is on a public-facing DevHub environment. As of now, we have not observed any confidential information such as sensitive PII or financial data.”
The statement emphasized that Cisco had engaged law enforcement and was conducting a thorough investigation. The company confirmed that no sensitive information, such as Personally Identifiable Information (PII) or financial data, was detected among the exposed files. Cisco clarified that the data in question originated from DevHub, a public-facing resource center designed to support the community by sharing software code and scripts. To mitigate potential risks, Cisco temporarily disabled access to DevHub.
IntelBroker’s Social Media Reactions: Claiming 12 Days of Access to Cisco Systems
IntelBroker used Twitter to amplify their breach claims and criticize Cisco’s response, while also attempting to highlight their own persistence. In their initial BreachForums post, IntelBroker stated that the Cisco breach occurred on October 6, though the exact entry date remains unclear. Despite this uncertainty, IntelBroker asserted on social media that they maintained access to Cisco’s systems until October 18, claiming a total of 12 days inside.
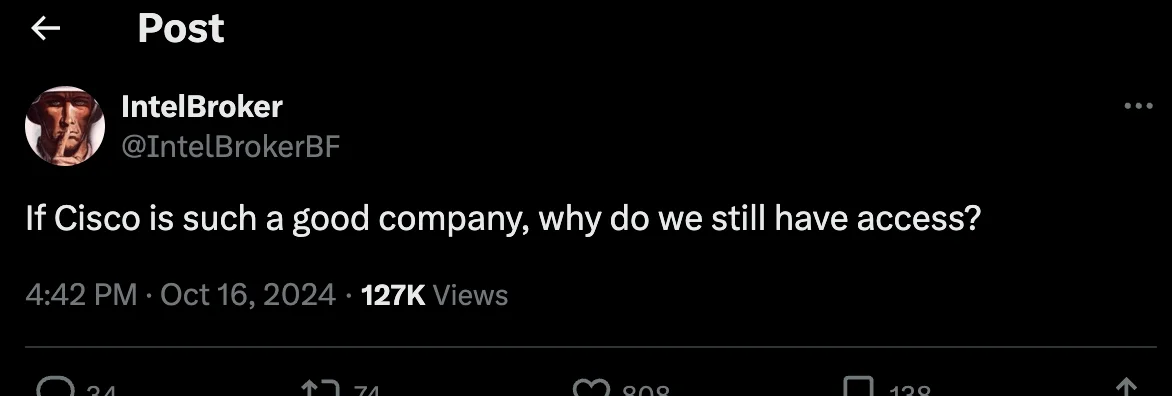
IntelBroker claimed in an October 16 tweet that they still had access to Cisco’s systems
The first Twitter post from IntelBroker came on October 16, suggesting that they still had ongoing access to Cisco’s systems, thereby casting doubt on the effectiveness of Cisco’s containment measures.
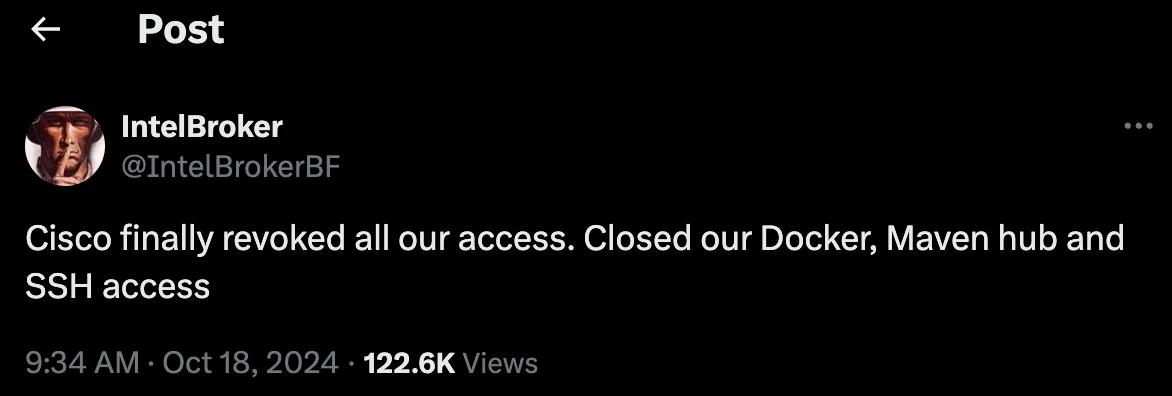
On October 18, they claimed Cisco had finally revoked all access
On October 18, IntelBroker announced that Cisco had successfully revoked all access, citing the shutdown of Docker, Maven Hub, and SSH entry points. By framing this as a delayed action, IntelBroker aimed to publicly undermine Cisco’s response, positioning themselves as a resilient threat capable of sustaining access against one of the largest tech firms. The social media posts were part of a broader strategy to enhance IntelBroker’s reputation among cybercriminals while creating doubts about Cisco’s transparency and incident response management.
IntelBroker Raises Stakes, Claims Cisco Breach Tops 800GB
IntelBroker continues to dispute Cisco’s statements, with recent updates adding new dimensions to the alleged breach. On November 3, IntelBroker claimed on their X (formerly Twitter) account that Cisco had proposed a payment to have the data deleted and the sale thread closed, describing the offer as unexpected.
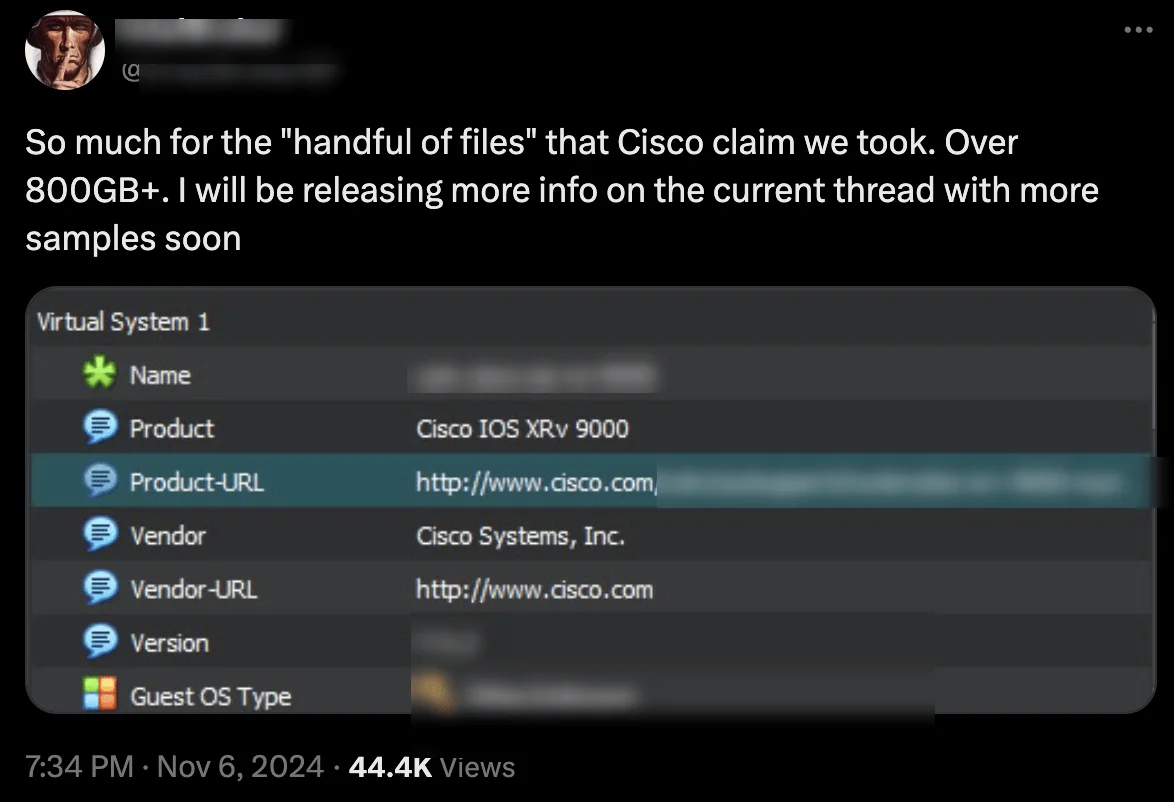
IntelBroker’s November 6 post on X, alleging that the Cisco breach exposed over 800GB of data, with plans to share additional samples to support their claim
Then, in a November 6 post, IntelBroker suggested that the volume of data accessed was significantly larger than what Cisco had reported, with a total size exceeding 800GB. The threat actor indicated plans to release more samples and details soon, sharing a screenshot as supporting evidence.
IntelBroker Shares Partial Cisco Data to Prove Legitimacy
IntelBroker has intensified their claims by releasing a 2.9GB partial sample of the stolen data on December 16. The leak allegedly includes files like Cisco IOS XE, Cisco ISE, Cisco SASE, Umbrella, and Webex, making it the first publicly shared portion of the claimed 4.5TB dataset. This release appears to be a move to validate the breach and attract potential buyers for the full data.

IntelBroker shares a partial 2.9GB sample of the alleged Cisco DevHub breach on a hacker forum, claiming it as proof of the 4.5TB data leak.
IntelBroker Releases More Data from Alleged Cisco Breach: 4.5TB Leak Update
IntelBroker continues to push forward with the claimed 4.5TB Cisco data breach from October, now claiming another free data leak for Christmas. The latest post, dated December 25, 2024, introduces new files that help validate the size and scope of the breach. Notably, these files in the leak involve testing environments and network configurations, and more.
IntelBroker has released Cisco Partial Breach v2 on the Dark Web forum
Cisco Confirms Data Leak by IntelBroker and Provides Update
Cisco has confirmed the authenticity of the recent data leak by hacker IntelBroker. Previously, the company clarified that while much of the exposed data was already public, some files were not intended for release. After the initial claims, on Christmas Day, the hacker leaked around 4 GB of this data, following an earlier release of 3 GB.
On December 26, Cisco acknowledged the new leak and confirmed the released data matched what had already been identified during the company’s investigation in October 2024. Cisco reiterated that no breach of core systems occurred, and there has been no evidence suggesting that the leaked data could be used to access production or enterprise environments.
Although Cisco initially denied any risk to personal or financial data, the company has since removed this statement from its reports and continues to investigate the full scope of the breach.
Who is IntelBroker: From Notorious Breacher to BreachForums Admin
IntelBroker’s claim to have accessed Cisco’s systems isn’t an isolated event; it’s part of a long history of breaches targeting high-profile organizations. Initially, IntelBroker gained recognition as one of the most active members on BreachForums, associated with other notorious cybercriminals like ShinyHunters and USDoD. Emerging in late 2022, IntelBroker became widely known in 2023 after alleged breaches of Weee Grocery Service, Europol, Autotrader, Volvo, Hilton Hotels, and AT&T. While not all breaches could be independently verified, many were confirmed leaks, boosting IntelBroker’s reputation within the cybercriminal community.

For a deeper look into IntelBroker’s history and activities, check out the Dark Web Profile: IntelBroker
In May 2024, IntelBroker rose to admin status on BreachForums, following significant events that disrupted the forum’s leadership. Law enforcement captured Baphomet, the former admin, leading to a power vacuum within the community. ShinyHunters, another prominent figure, stepped down, leaving IntelBroker to fill the gap. This transition marked a new phase for IntelBroker, positioning them as both a key figure in the forum’s operations and one of the most active participants in its illicit activities.
Beyond BreachForums, IntelBroker’s involvement extends to the racist cybercrime group CyberNiggers. The group gained notoriety in 2023 for its coordinated cyberattacks. Though IntelBroker initially joined as a member, they soon became a driving force behind the group’s most significant breaches, distinguishing themselves within its ranks. The group’s activities ceased for a time, but IntelBroker revived it on August 9, 2024, uniting some of BreachForums’ most active threat actors under a new banner.

For more insights into the CyberNiggers’ history and IntelBroker’s role, visit the Dark Web Profile: CyberNiggers blog
The Cisco incident is the latest chapter in IntelBroker’s evolving tactics and targets. The actor’s ability to consistently breach prominent organizations and maintain public visibility, even on platforms like Twitter, highlights a strategic approach that combines technical skill with psychological pressure. IntelBroker’s pattern of targeting organizations like Cisco suggests a broader agenda: not just data theft, but a reputation built on high-profile intrusions that challenge corporate security measures and reveal potential vulnerabilities.



































