
Ivanti Security Update Addresses Severe Vulnerabilities in ICS, IPS, and ISAC (CVE-2025-22467, CVE-2024-38657, CVE-2024-10644)
In response to newly identified vulnerabilities, Ivanti has released security updates addressing flaws in Ivanti Connect Secure (ICS), Ivanti Policy Secure (IPS), and Ivanti Secure Access Client (ISAC). Among the identified issues, three have been classified as critical, posing significant security risks. While Ivanti has reported no known active exploitation of these vulnerabilities, users are strongly urged to apply patches immediately to secure their systems.
In this blog, we will outline the latest Ivanti vulnerabilities and explore the steps you can take to stay protected.
What Are Ivanti’s Latest Critical Vulnerabilities and How Could They Impact Your Systems?
The three critical vulnerabilities affect different security solutions of Ivanti, with potential consequences such as Remote Code Execution (RCE) and arbitrary file writing.
- CVE-2025-22467 (CVSS 9.9) – Stack-Based Buffer Overflow
A flaw in Ivanti Connect Secure allows a remote authenticated attacker to achieve remote code execution. Due to the high impact on confidentiality, integrity, and availability, this is the most severe vulnerability in this update.
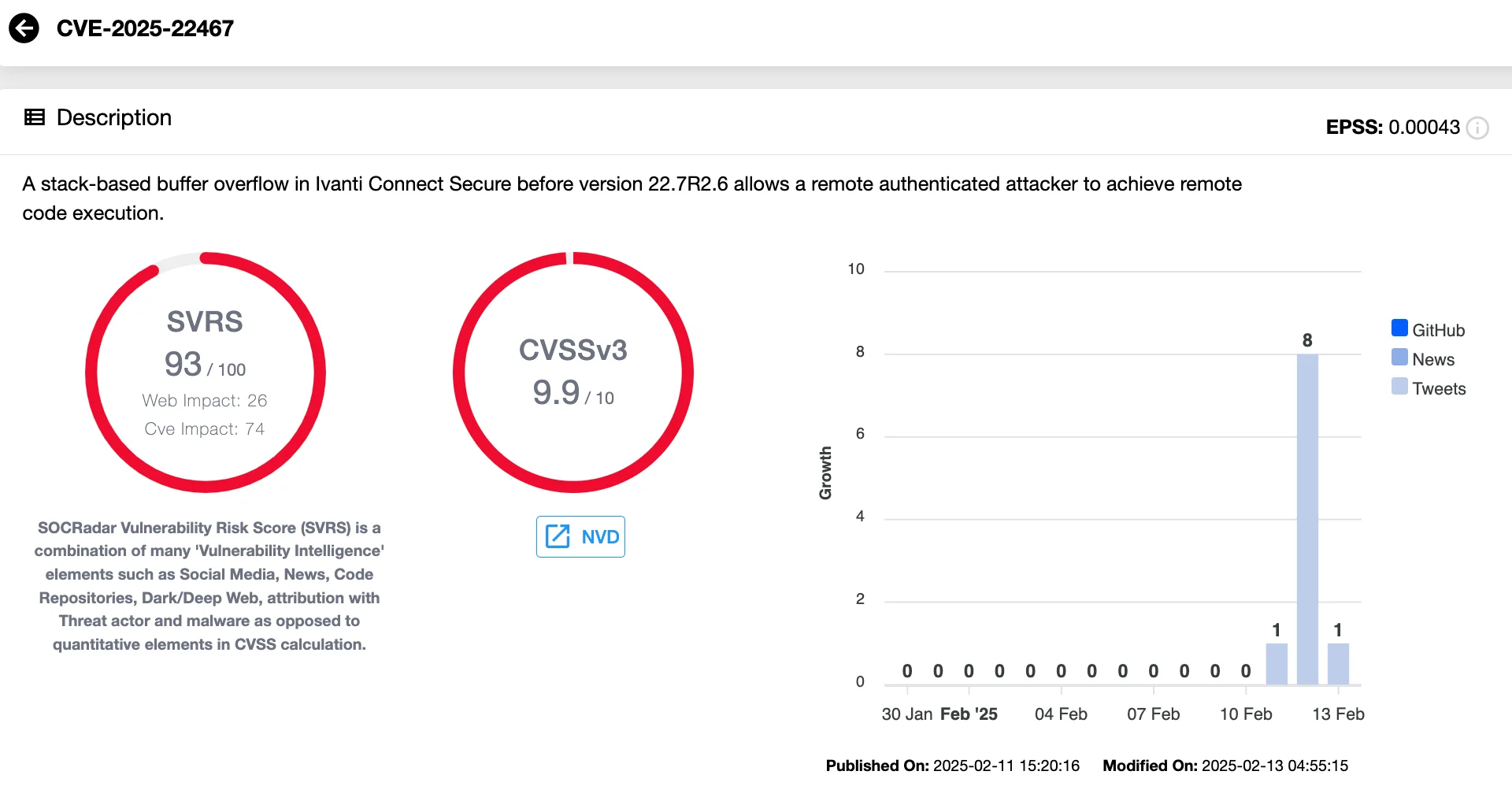
Vulnerability card of CVE-2025-22467 (SOCRadar Vulnerability Intelligence)
- CVE-2024-10644 (CVSS 9.1) – Code Injection
Another high-impact flaw affecting Ivanti Connect Secure and Policy Secure, this issue allows remote code execution when exploited by an authenticated attacker with admin privileges.
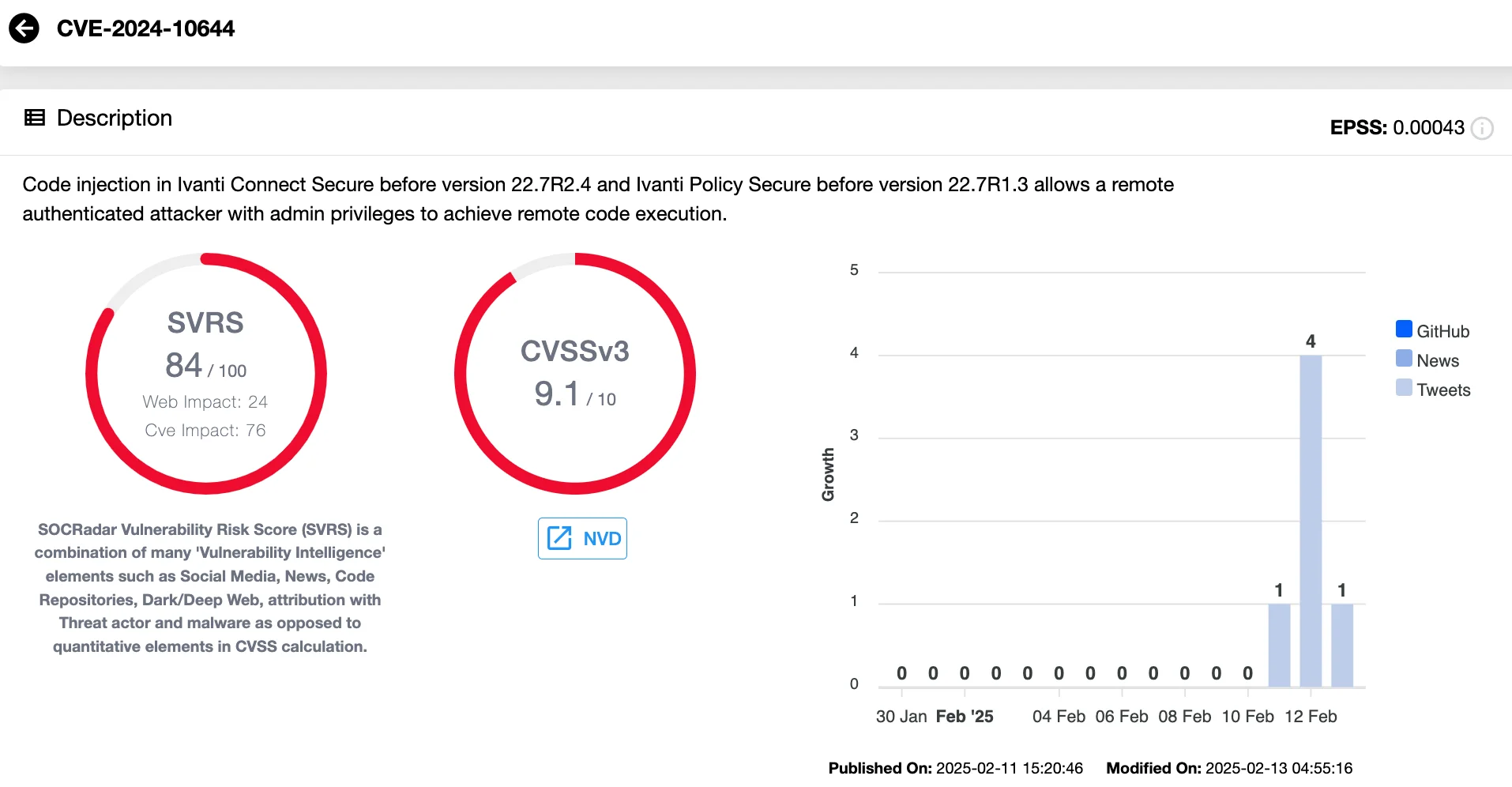
Vulnerability card of CVE-2024-10644 (SOCRadar Vulnerability Intelligence)
- CVE-2024-38657 (CVSS 9.1) – Arbitrary File Write
Found in Ivanti Connect Secure and Policy Secure, this vulnerability enables a remote authenticated attacker with admin privileges to write arbitrary files, potentially leading to full system compromise.
SOCRadar’s Vulnerability Intelligence module provides real-time alerts, comprehensive vulnerability analysis, and detailed insights into risks like those in Ivanti’s products. By integrating with industry-standard vulnerability databases, SOCRadar helps you track critical CVEs, assess potential impacts, and prioritize patches before threats can be exploited.
Additional Security Flaws That Require Attention
Although these vulnerabilities are considered less severe than the previously mentioned ones, they still present significant risks if left unpatched. Attackers could exploit them to gain unauthorized access, leak sensitive information, or disrupt system operations.
- CVE-2024-12058 (CVSS 6.8) – Arbitrary file read (authenticated attackers).
- CVE-2024-13830 (CVSS 6.1) – Reflected XSS vulnerability (user interaction required).
- CVE-2024-13842 (CVSS 6.0) – Hardcoded key exposure.
- CVE-2024-13843 (CVSS 6.0) – Cleartext storage of sensitive data.
- CVE-2024-13813 (CVSS 7.1) – Insufficient permissions, allowing arbitrary file deletion.
Which Ivanti ICS, IPS, and ISAC Versions Are Affected?
The vulnerabilities impact multiple versions of Ivanti products, including:
- Ivanti Connect Secure (ICS) – Versions 22.7R2.5 and older
- Ivanti Policy Secure (IPS) – Versions 22.7R1.2 and older
- Ivanti Secure Access Client (ISAC) – Versions 22.7R4 and older
Ivanti has also stated that Pulse Connect Secure 9.x is affected, but it will not receive patches as its support ended on December 31, 2024.
How Can You Protect Your Systems from These Ivanti Vulnerabilities?
To protect systems from potential exploitation, Ivanti urges administrators to immediately update to the latest available versions:
- ICS: Upgrade to 22.7R2.6
- IPS: Upgrade to 22.7R1.3
- ISAC: Upgrade to 22.8R1
As Ivanti has not provided any specific mitigations for these vulnerabilities, applying the latest patches remains the most effective security measure. Organizations should also enforce strict access controls, regularly audit system configurations, and follow best practices to minimize the risk of exploitation.
For further details and to download the updates, refer to Ivanti’s official security advisory.
By staying proactive with patch management, organizations can mitigate the risks posed by these newly discovered vulnerabilities and secure their critical network infrastructure.
Monitor and Secure Your Digital Footprint with SOCRadar’s ASM
As cyber threats evolve, so should your defense strategies. SOCRadar’s Attack Surface Management (ASM) module continuously monitors your digital footprint, providing complete visibility into your systems, applications, and third-party dependencies.
Strengthen your security posture with proactive risk management and automated remediation using SOCRadar’s ASM, designed to keep your digital assets secure.
With the rapid rise of vulnerabilities, like CVE-2025-22467, ASM allows you to identify risks across your entire attack surface. It tracks vulnerabilities and provides timely insights to help you reduce exposure and take swift action.




































