
Navigating the Assets Discovery Journey with SOCRadar XTI EASM
The attack surface is the sum of all potential entry points an attacker can use to gain unauthorized access to an organization’s assets and is likely to affect one or more of the CIA (Confidentiality-Integrity-Availability) triads. The attack surface includes anything connected to the internet, such as websites, applications, and cloud services. Numerous factors contribute to the attack surface in today’s digital landscape, from cloud environmentsto IoT devices.
The challenge of the attack surface is that it is not a static entity and constantly changing and growing. As organizations adopt new technologies and work practices, such as the increased migration of workloads to the cloud and the growing use of personal devices for work purposes, evolving threats and emerging attack vectors continuously contribute to the growth and evolution of the attack surface.
SOCRadar XTI External Attack Surface Management
External Attack Surface Management (EASM) helps organizations identify and manage risks associated with Internet-facing assets and systems by continuously discovering, monitoring, evaluating, and prioritizing. The goal is to uncover vulnerabilities that are difficult to detect and provide a better understanding of the organizations’ actual external attack surface.
SOCRadarXTI’s External Attack Surface Management solution;
- Scans the entire internet and determines all external-facing assets associated with the organization’s domains, IP addresses, websites, SSL/TLS certificates, and other related infrastructure.
- Identifies and understands the potential risks associated with an organization’s external-facing digital assets.
- Provides comprehensive information that can be used to diagnose possible security risks and take precautions about each identified asset, including its location, configuration, and vulnerabilities.
- Also identifies assets that are not known by the organization, and this allows it to generate alerts to guide the organization on how to act upon those unknown assets.
SOCRadar XTI External Attack Surface Management (EASM) has two main sections: Digital Footprint and Company Vulnerabilities.
The digital footprint is also known as digital shadow can be described as the traces left behind after scrolling through the Internet. It includes all the traceable digital activities, actions, contributions, and communications.
The Digital Footprint section includes all the digital assets associated with the organization, such as domains, IP addresses, IP blocks, SSL/TLS certificates, websites, mobile applications, and so on. This section provides all the necessary information related to each digital asset.
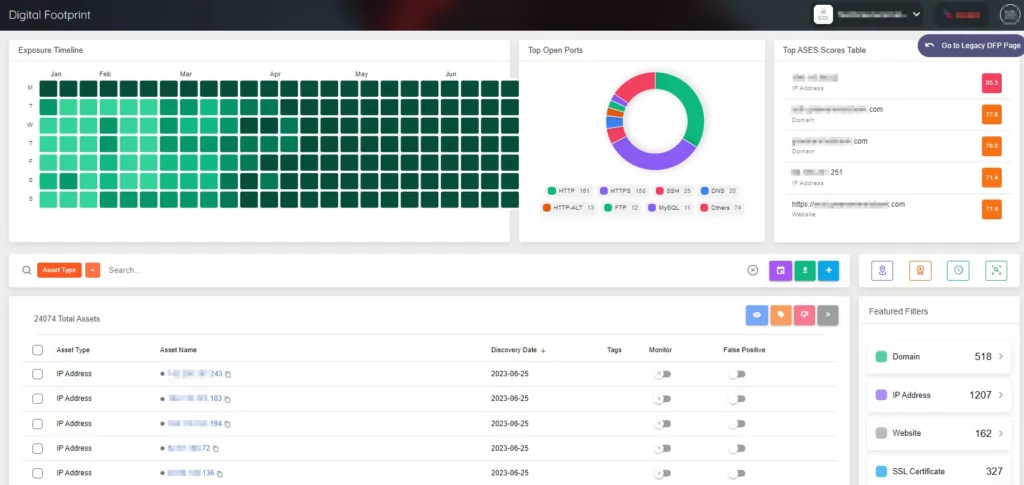
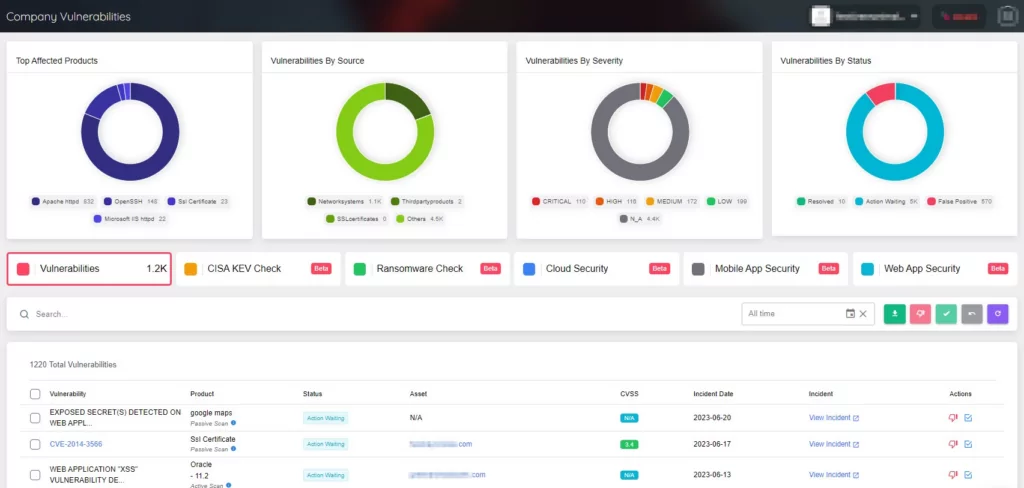
The Company Vulnerabilities section includes all the vulnerabilities associated with the organization’s digital assets. It presents comprehensive information about each vulnerability, including its severity, CVSS score, and related assets. It enables the management of vulnerabilities associated with assets and generates alerts to guide how to act upon those vulnerabilities.
Assets Discovery Process
The motto of the Attack Surface Management approach is: effective asset management is only possible when the existence of assets is known. That philosophy highlights the significance of asset discovery and visibility and the critical nature of asset awareness.
Assets that remain unknown, unprotected, or unrecognized are the most exploitable. Therefore, gaining insight into what attackers can perceive when assessing an organization’s digital assets is imperative to establish a robust defense system.
The attack surface management approach begins with asset discovery as the essential step. This process entails systematically scanning and identifying all the assets in an organization’s digital landscape, ranging from systems and applications to devices and networks.
The primary objective of digital assets discovery is to achieve comprehensive visibility into an organization’s online presence and gain a thorough understanding of the extent of its digital footprint.
After identifying the assets, comprehensive information is furnished for each asset, encompassing its location, configuration, and vulnerabilities. Among the details provided for the assets, one crucial aspect is the discovery path.
Assets Discovery Path
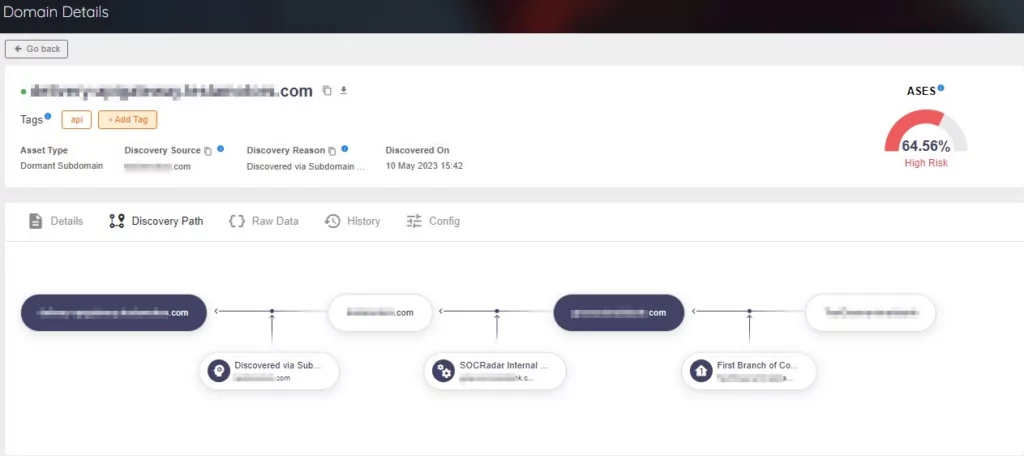
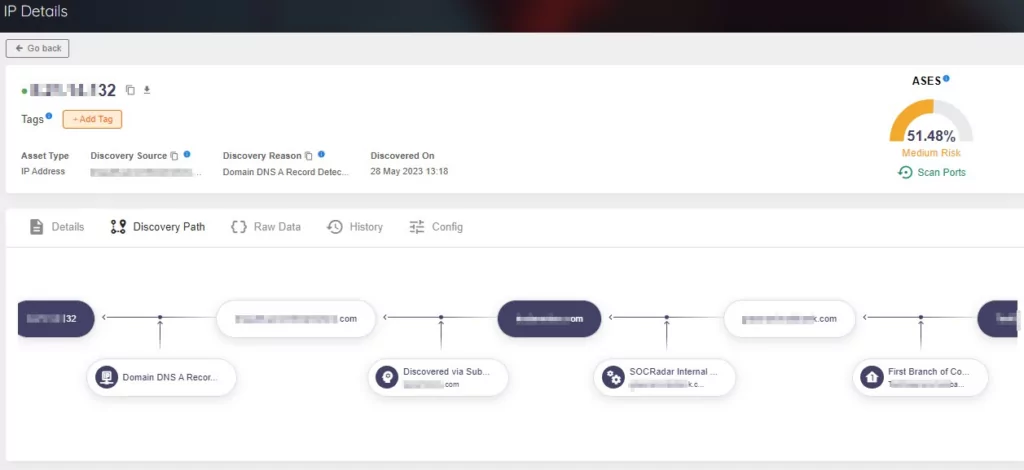
The discovery path within the assets details section was designed to enhance understanding of the relationship between assets and their discovery process.
Understanding the complete picture and how various elements contribute to an asset can be challenging. Therefore, the Discovery Path feature emphasizes the specific path to uncover each item, providing clarity and insight into the discovery process. This valuable information enables users to visualize the connections between assets and gain a deeper understanding of why a particular asset has been identified as belonging to their organization.
The Discovery Path can be utilized as a jumping-off point and guidance for conducting the user’s investigation while discovering and monitoring the attack surface.
The Discovery Path feature lets users quickly access their inventory when their data is refreshing, and additional assets and current context are added to their Attack Surface. So, in case of an unwanted digital asset is in the inventory, it is possible to detect and exclude it.
SOCRadar XTI EASM already provides Discovery Path for domains and IP addresses.
It is now time to focus on Websites and SSL/TLS Certificates. SOCRadar XTI EASM enables you to gain insights into where and how your Websites and SSL/TLS Certificates are identified.
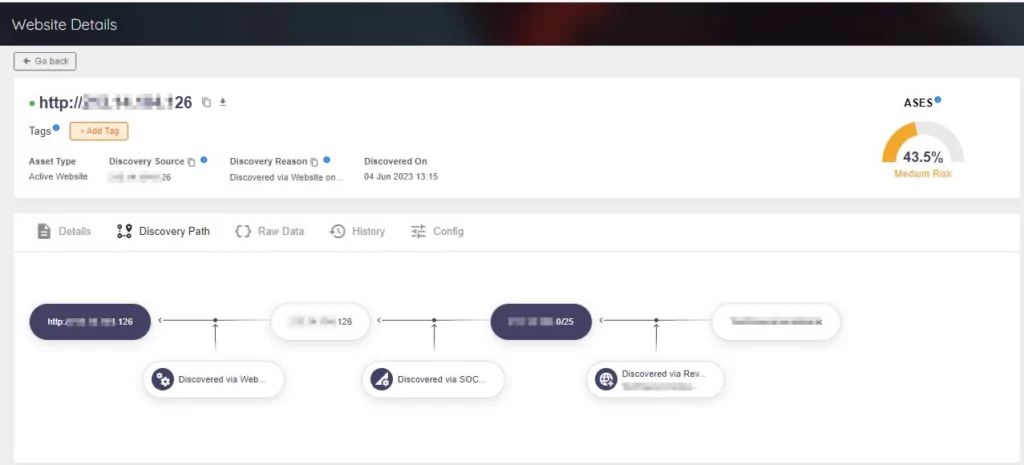
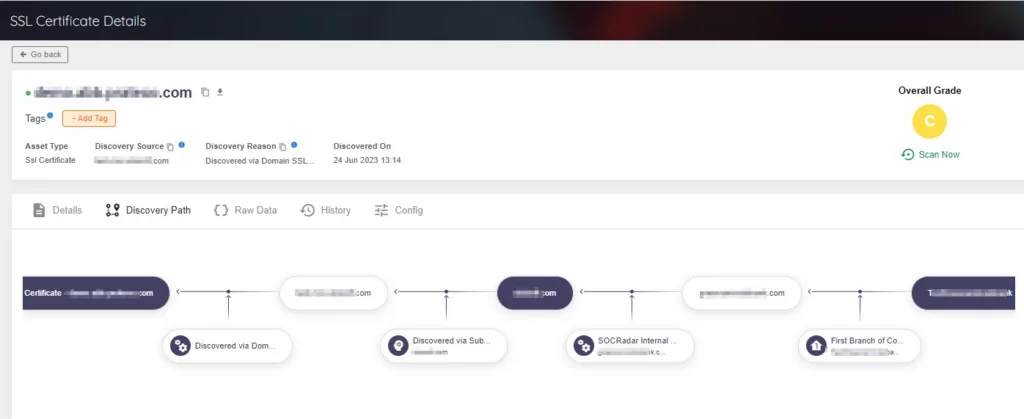
Furthermore, the Discovery Path feature provides users with visibility into how potential attackers can detect digital assets. By offering crucial insights into the asset discovery process, as well as Discovery Source and Discovery Reason data, it empowers users to proactively address the security of their assets.
All types of asset details include Discovery Source and Discovery Reason along with Discovery Path. Also, these details can be tracked on the Discovery Path.
Conclusion
External Attack Surface Management solutions help organizations gain visibility and context of their digital assets, specify and prioritize potential security risks, and make more knowledgeable decisions to strengthen them against threats.
Through SOCRadar XTI’s advanced internet-wide monitoring algorithms, EASM gives users direct visibility into all internet-facing digital assets in use as well as assets such as IP, DNS, Domain, Websites, and SSL/TLS Certificates.
Modern IT environments are often complex, comprising various interconnected systems, applications, and data repositories. The Discovery Path feature empowers organizations to navigate the complexities and visualize their asset discovery journey. This approach allows a clear understanding of the relationships and dependencies between different components, helping identify potential vulnerabilities and security gaps.



































