
Ivanti Zero-Day Exploited in Connect Secure, SonicWall SSL VPN and SSH Vulnerabilities, KerioControl Flaw
[Update] February 17, 2025: “SPAWNCHIMERA Malware Actively Exploiting CVE-2025-0282”
[Update] February 15, 2025: “Active Exploitation of SonicWall CVE-2024-53704”
[Update] January 10, 2025: “Recent Findings Reveal UNC5337 Exploiting Ivanti ICS Vulnerabilities with Advanced Tactics”
Recent vulnerabilities in Ivanti Connect Secure, SonicWall firewalls, and GFI KerioControl have raised serious security concerns.
Ivanti’s CVE-2025-0282, a critical flaw allowing Remote Code Execution (RCE), is currently being exploited as a zero-day, putting systems at immediate risk. In parallel, SonicWall has resolved significant security vulnerabilities in its SSL VPN and SSH management features, which pose serious risks if left unpatched. Additionally, GFI KerioControl’s CVE-2024-52875 opens the door for 1-click RCE attacks, with active exploitation attempts reported.
Organizations using these products must prioritize applying the latest patches, closely monitor for signs of exploitation, and follow recommended mitigation measures to safeguard their systems from these ongoing threats.
Ivanti Warns of Exploitation of Critical Zero-Day in Connect Secure
Ivanti has warned about the exploitation of a critical zero-day vulnerability, CVE-2025-0282, in Ivanti Connect Secure appliances. The company’s Integrity Checker Tool (ICT) detected malicious activity on affected devices, confirming the exploit.
Ivanti has released a patch for Connect Secure appliances to mitigate exploitation, while the patches for the other affected products will be available later in January. Nonetheless, there are mitigative factors in place that reduce the likelihood of exploitation for those products until the patches are released.
Details of CVE-2025-0282 and Affected Products/Versions
CVE-2025-0282 (CVSS 9.0) is a stack-based buffer overflow vulnerability that can allow unauthenticated attackers to perform Remote Code Execution (RCE) across several Ivanti products. The affected products and versions include:
- Ivanti Connect Secure (ICS) before 22.7R2.5
- Ivanti Policy Secure (IPS) before 22.7R1.2
- Ivanti Neurons for ZTA Gateways before 22.7R2.3
While the flaw affects Ivanti’s Connect Secure, Policy Secure, and Neurons for ZTA products, the company confirmed in its official advisory that exploitation has only been observed in Ivanti Connect Secure.
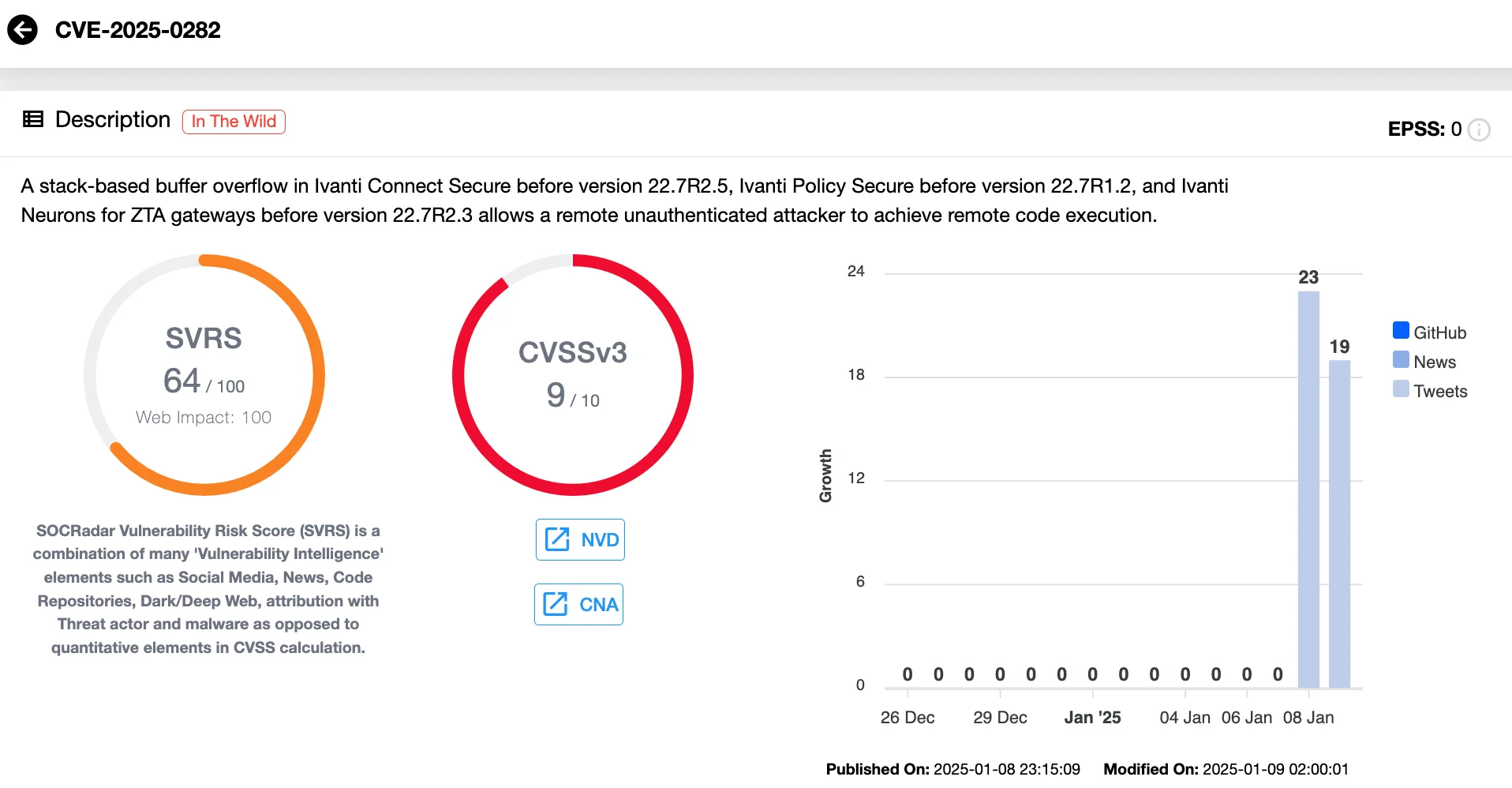
Vulnerability card of CVE-2025-0282 (SOCRadar Vulnerability Intelligence)
High-Severity Flaw Could Lead to Privilege Escalation (CVE-2025-0283)
Alongside CVE-2025-0282, Ivanti also revealed CVE-2025-0283 (CVSS 7.0), a high-severity vulnerability that could allow local authenticated attackers to escalate privileges.
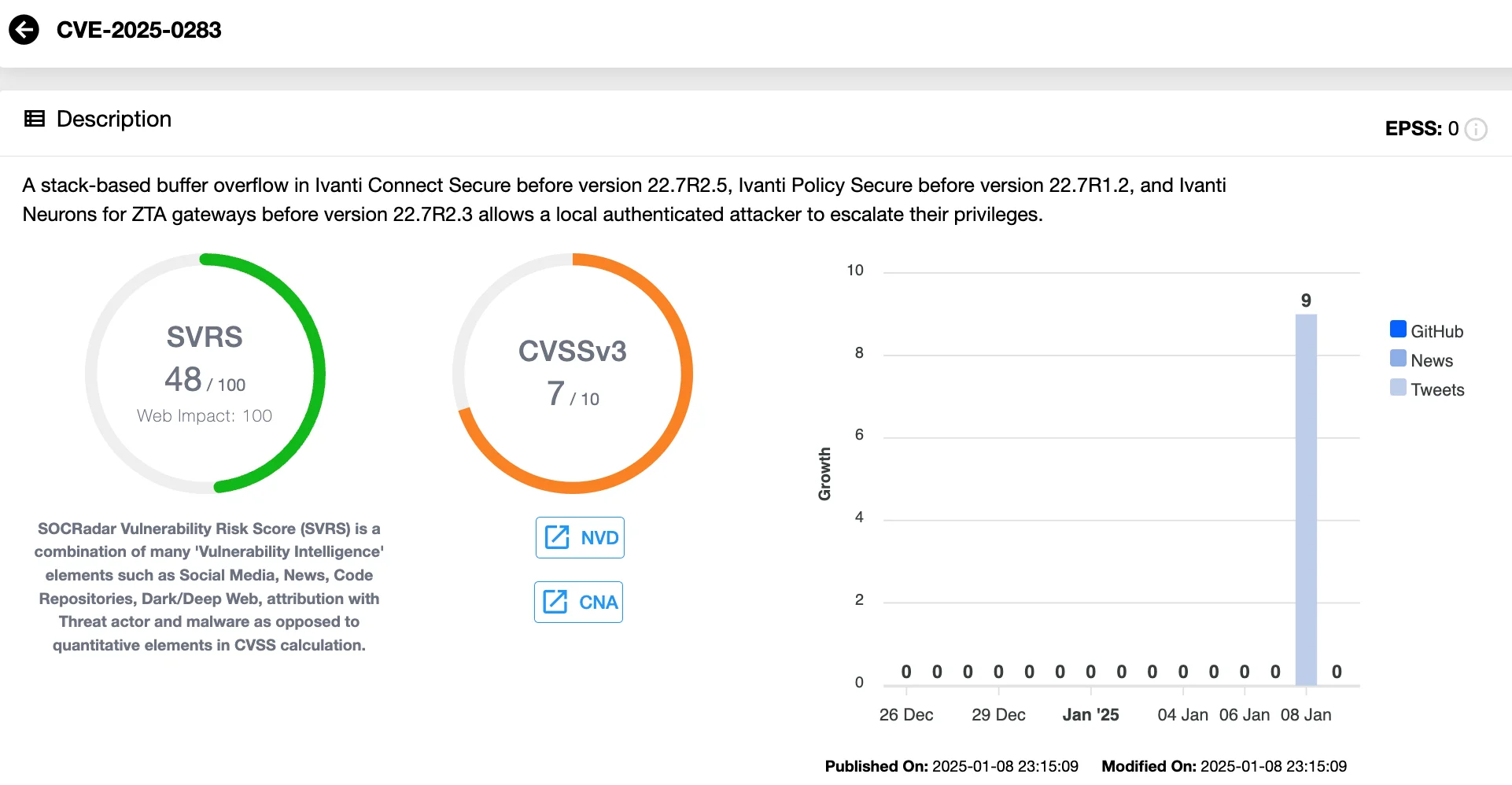
Vulnerability card of CVE-2025-0283 (SOCRadar Vulnerability Intelligence)
This security vulnerability impacts the same Ivanti products and versions, but Ivanti has stated that no exploitation of CVE-2025-0283 has been observed as of the time of disclosure.
Are Patches Available? How Can You Mitigate These Vulnerabilities?
Ivanti has addressed the vulnerability in Ivanti Connect Secure with the release of firmware version 22.7R2.5.
Users of Ivanti Connect Secure should upgrade to version 22.7R2.5 and closely monitor both internal and external scans using security tools. If a compromised ICT scan is detected, Ivanti recommends performing a factory reset before deploying the update and continuing to monitor with additional security solutions.
According to the company’s advisory, patches for Ivanti Policy Secure and Ivanti Neurons for ZTA Gateways will be made available by January 21, 2025. For these products lacking patches, the company has recommendations to reduce risks:
- Since Ivanti Policy Secure is not designed to be internet-facing, the risk of exploitation is lower. Ivanti advises users to ensure proper configuration and avoid exposing the product to the internet.
- Ivanti Neurons for ZTA Gateways is secure when connected to a ZTA controller in production. If unconnected, the product could be vulnerable.
For more information, refer to Ivanti’s security advisory.
Recent Findings Reveal UNC5337 Exploiting Ivanti ICS Vulnerabilities with Advanced Tactics
Latest research points to attackers actively exploiting CVE-2025-0282, a critical vulnerability in Ivanti Connect Secure (ICS) appliances, since December 2024. Ivanti disclosed this flaw on January 8, 2025, alongside CVE-2025-0283, a cross-site scripting (XSS) vulnerability that increases phishing risks.
Mandiant’s analysis reveals a structured exploitation process. Attackers conduct reconnaissance by sending repeated HTTP requests and using the Host Checker Launcher to identify vulnerable ICS versions. Once inside, they disable SELinux, block syslog forwarding, and deploy malicious web shells like PHASEJAM. This Perl-based script embeds itself into legitimate ICS files, providing remote access, preventing system updates, and installing backdoors disguised as system processes.
Researchers have linked these attacks to UNC5337, a China-linked espionage group associated with UNC5221. This group employs advanced malware families such as SPAWNSNAIL, SPAWNMOLE, DRYHOOK, and PHASEJAM to maintain persistence, enable lateral movement, and steal data.
Organizations using ICS appliances must apply patches immediately and monitor for unusual activity. These steps are essential to mitigate the risks posed by these sophisticated and targeted attacks.
SPAWNCHIMERA Malware Actively Exploiting CVE-2025-0282
Researchers at JPCERT/CC have identified SPAWNCHIMERA, a newly evolved malware variant actively exploiting CVE-2025-0282 in Ivanti Connect Secure. This sophisticated malware was detected in attacks even before the vulnerability was publicly disclosed, indicating a well-planned and targeted operation.
SPAWNCHIMERA builds upon previous SPAWN malware variants, integrating advanced stealth and persistence techniques. Notably, it injects itself into system processes while dynamically patching CVE-2025-0282 to prevent competing attackers from exploiting the same flaw. The malware also utilizes UNIX domain sockets for covert communication, making it difficult to detect using traditional network monitoring tools. Additionally, it encrypts sensitive data and eliminates forensic traces, further complicating analysis.
The emergence of SPAWNCHIMERA highlights the growing sophistication of cyber threats targeting enterprise security solutions. Organizations using Ivanti Connect Secure should prioritize patching CVE-2025-0282 and implement strict monitoring to detect unauthorized modifications and covert malware activity.
For details, refer to JPCERT/CC’s official overview.
SonicWall Urges Customers to Upgrade Firmware Following Critical Vulnerability
In other news, SonicWall has released an advisory urging customers to upgrade their firewall’s SonicOS firmware due to a high-severity authentication bypass vulnerability. The flaw, affecting SSL VPN and SSH management functionalities, poses a serious risk of exploitation.
Prior to the update, the company sent an email to its customers, notifying them that the upcoming update (available from January 7, 2025) would address the vulnerability. SonicWall emphasizes the importance of upgrading immediately to prevent potential attacks, particularly for users with SSL VPN or SSH management enabled.
The firmware update also addresses several other less-critical vulnerabilities, further enhancing security.
Details of the Recent SonicWall Vulnerability (CVE-2024-53704)
CVE-2024-53704 (CVSS 8.2) is an improper authentication vulnerability in the SSL VPN authentication mechanism. It enables remote attackers to bypass authentication, potentially gaining unauthorized access to systems.
SOCRadar’s Vulnerability Intelligence platform helps you track and manage vulnerabilities across your environment. It delivers real-time alerts, identifying critical threats as they arise. With our advanced tracking capabilities, you can prioritize vulnerabilities based on severity, exploitability, and relevance to your systems.
Mitigate Risks Early with SOCRadar’s Vulnerability Intelligence
Here are the key features of Vulnerability Intelligence:
- Real-time CVE tracking, risk analysis, and continuous updates
- Detection of available PoC exploits and active exploitation
- Alerts for emerging threats to address before exploit attempts
Get actionable insights and reduce your exposure to cyber risks with SOCRadar’s Vulnerability Intelligence. Protect your organization by addressing vulnerabilities before they can be exploited.
Active Exploitation of SonicWall CVE-2024-53704
Attackers are now actively exploiting CVE-2024-53704, a critical authentication bypass vulnerability in SonicWall firewalls. This flaw, affecting SonicOS 7.1.x and 8.0.0, allows remote attackers to hijack SSL VPN sessions without authentication, granting them unauthorized access to targeted networks.
Cybersecurity firm Arctic Wolf confirmed detecting exploitation attempts shortly after the release of a Proof-of-Concept (PoC) exploit, reinforcing SonicWall’s warnings about the vulnerability’s high risk.
To mitigate the threat, SonicWall is urging users to immediately update their SonicOS firmware. For those unable to patch right away, recommended precautions include restricting VPN access to trusted sources or disabling SSL VPN entirely if not essential.
Additional Vulnerabilities Addressed by SonicWall
The latest security advisory by the company also highlights three other vulnerabilities; though less severe, they still present significant risks:
- CVE-2024-53706 (CVSS 7.8): A privilege escalation vulnerability in the Gen7 SonicOS Cloud platform (AWS and Azure editions) allowing low-privileged attackers to elevate to root and potentially execute code.
- CVE-2024-40762 (CVSS 7.1): A cryptographic weakness in the SSL VPN authentication token generator that could enable attackers to predict tokens and bypass authentication.
- CVE-2024-53705 (CVSS 6.5): A Server-Side Request Forgery (SSRF) vulnerability in the SonicOS SSH management interface, allowing remote attackers to make unauthorized TCP connections while logged in to the firewall.
Recommended Actions for Affected Users
SonicWall urges users to apply the available patch as soon as possible to mitigate security risks. Affected users should upgrade to the following versions:
- Gen 6 / 6.5 Hardware Firewalls: SonicOS 6.5.5.1-6n or later
- Gen 6 / 6.5 NSv Firewalls: SonicOS 6.5.4.v-21s-RC2457 or later
- Gen 7 Firewalls: SonicOS 7.0.1-5165 or later; 7.1.3-7015 and later
- TZ80: SonicOS 8.0.0-8037 or later
SonicWall also advises limiting SSL VPN access to trusted sources and disabling internet access for SSL VPN. Likewise, to mitigate SSH vulnerabilities, restrict firewall management to trusted sources or disable SSH management from the internet.
For more information and detailed mitigation guidance, refer to the security advisory.
Attackers Are Targeting GFI KerioControl Systems with CVE-2024-52875
The exploit of CVE-2024-52875, a significant CRLF injection vulnerability in GFI KerioControl, is another recent urgent news item impacting the vulnerability landscape. The product is defined as a unified threat management firewall that provides a range of features such as intrusion prevention, content filtering, and activity reporting.
What is CVE-2024-52875?
The flaw arises from improper handling of HTTP headers, which allows attackers to inject malicious payloads and potentially gain unauthorized system access. Alarmingly, its exploitation leads to 1-click Remote Code Execution (RCE) attacks.
This vulnerability affects KerioControl versions 9.2.5 through 9.4.5. Organizations using these versions should take immediate action to mitigate the risk.
Technical Details and PoC Exploit Available
In mid-December 2024, a researcher released technical details and a Proof-of-Concept (PoC) exploit for CVE-2024-52875. According to the researcher’s article, the flaw arises from improper sanitization of LF characters in the dest parameter, allowing attackers to manipulate HTTP headers and inject malicious payloads.
This enables the injection of harmful JavaScript, executed in victims’ browsers to steal cookies or CSRF tokens. If an attacker gains an admin’s CSRF token, they can upload a malicious .IMG file with a root-level shell script, triggering a reverse shell via Kerio’s upgrade functionality.
Exploitation Attempts Reported – Patch Now to Prevent Attacks
Recently, Greynoise reported multiple exploitation attempts of CVE-2024-52875, likely leveraging the publicly available PoC exploit. These attempts indicate ongoing malicious activity targeting vulnerable systems.
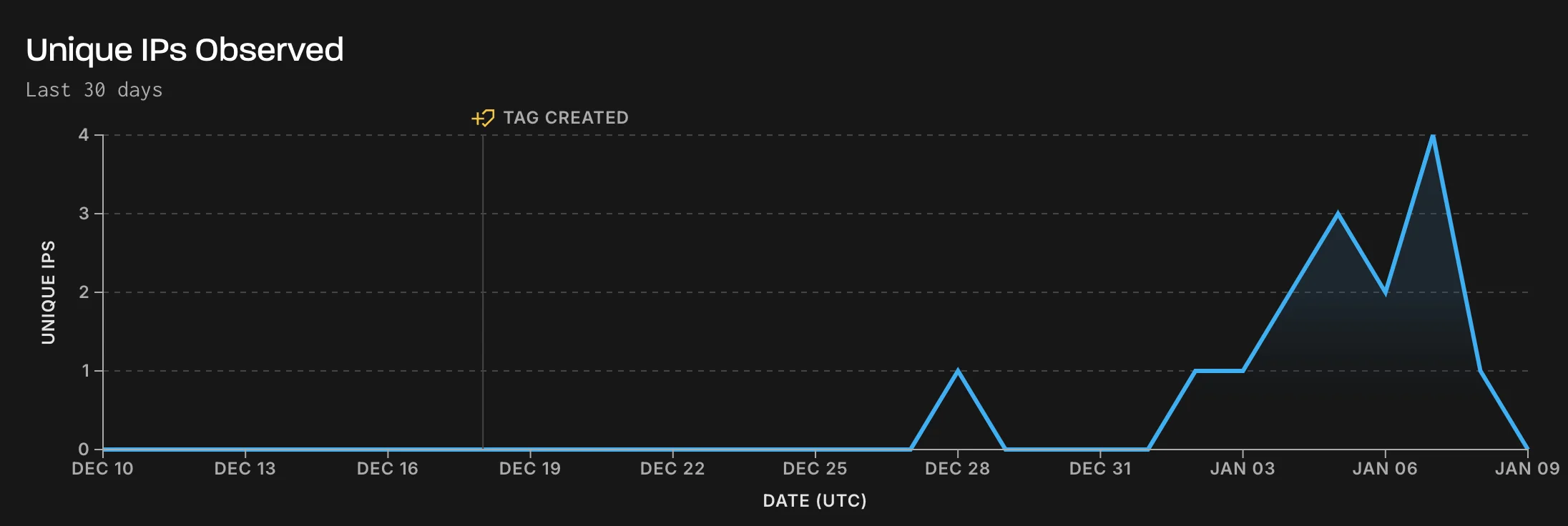
Exploitation attempts targeting KerioControl vulnerability (GreyNoise)
The vulnerability has already been addressed in Version 9.4.5 Patch 1, released last month. Users are urged to apply this patch immediately. For protection, it is advised to restrict access to the web management interface and block vulnerable paths and keep monitoring for exploitation attempts targeting the vulnerable parameter.
Strengthen Your Defenses with SOCRadar’s Attack Surface Management (ASM)
As organizations expand their digital footprint, the risk of unnoticed vulnerabilities increases. Attackers are constantly probing for exposed assets, making it critical to monitor and secure your attack surface proactively. SOCRadar’s Attack Surface Management (ASM) module provides continuous monitoring of all external-facing assets, identifying potential risks before they can be exploited. It helps you detect exposed services, misconfigurations, and vulnerabilities in real time.
Protect your digital infrastructure and stay one step ahead of cyber threats with SOCRadar’s ASM
With actionable insights, real-time alerts, and seamless integration with your existing security tools, SOCRadar ASM helps you reduce your attack surface and prevent data breaches. Proactively manage your vulnerabilities with exposure reports and immediate remediation steps.




































